CAST-128
Encyclopedia
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, CAST-128 (alternatively CAST5) is a block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
used in a number of products, notably as the default cipher
Cipher
In cryptography, a cipher is an algorithm for performing encryption or decryption — a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. In non-technical usage, a “cipher” is the same thing as a “code”; however, the concepts...
in some versions of GPG
GNU Privacy Guard
GNU Privacy Guard is a GPL Licensed alternative to the PGP suite of cryptographic software. GnuPG is compliant with RFC 4880, which is the current IETF standards track specification of OpenPGP...
and PGP
Pretty Good Privacy
Pretty Good Privacy is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security...
. It has also been approved for Canadian
Canada
Canada is a North American country consisting of ten provinces and three territories. Located in the northern part of the continent, it extends from the Atlantic Ocean in the east to the Pacific Ocean in the west, and northward into the Arctic Ocean...
government use by the Communications Security Establishment
Communications Security Establishment
The Communications Security Establishment Canada is the Canadian government's national cryptologic agency. Administered under the Department of National Defence , it is charged with the duty of keeping track of foreign signals intelligence , and protecting Canadian government electronic...
. The algorithm was created in 1996 by Carlisle Adams
Carlisle Adams
Carlisle M. Adams is a cryptographer and computer security researcher. Formerly senior cryptographer at Entrust, he is currently a professor at the University of Ottawa. His notable work includes the design of the block ciphers CAST-128 and CAST-256. He also helped organize the first Selected...
and Stafford Tavares
Stafford Tavares
Stafford Emanuel Tavares is a cryptographer, professor emeritus at Queen's University.His notable work includes the design of the block ciphers CAST-128 and CAST-256. He also helped organize the first Selected Areas in Cryptography workshop in 1994...
using the CAST design procedure; another member of the CAST family of ciphers, CAST-256
CAST-256
In cryptography, CAST-256 is a block cipher published in June 1998. It was submitted as a candidate for the Advanced Encryption Standard ; however, it was not among the five AES finalists. It is an extension of an earlier cipher, CAST-128; both were designed according to the "CAST" design...
(a former AES candidate) was derived from CAST-128. According to some sources, the CAST name is based on the initials of its inventors, though Bruce Schneier
Bruce Schneier
Bruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
reports the authors' claim that "the name should conjure up images of randomness" (Schneier, 1996).
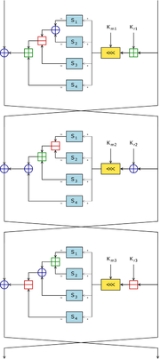
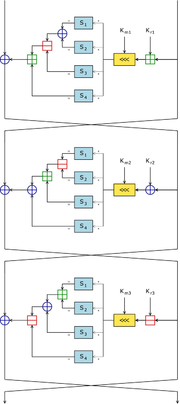
CAST-128 is a 12- or 16-round Feistel network with a 64-bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
block size
Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
and a key size
Key size
In cryptography, key size or key length is the size measured in bits of the key used in a cryptographic algorithm . An algorithm's key length is distinct from its cryptographic security, which is a logarithmic measure of the fastest known computational attack on the algorithm, also measured in bits...
of between 40 to 128 bits (but only in 8-bit increments). The full 16 rounds are used when the key size
Key size
In cryptography, key size or key length is the size measured in bits of the key used in a cryptographic algorithm . An algorithm's key length is distinct from its cryptographic security, which is a logarithmic measure of the fastest known computational attack on the algorithm, also measured in bits...
is longer than 80 bits.
Components include large 8×32-bit S-boxes based on bent function
Bent function
In the mathematical field of combinatorics, a bent function is a special type of Boolean function. Defined and named in the 1960s by Oscar Rothaus in research not published until 1976, bent functions are so called because they are as different as possible from all linear and affine functions...
s, key-dependent rotations, modular
Modular arithmetic
In mathematics, modular arithmetic is a system of arithmetic for integers, where numbers "wrap around" after they reach a certain value—the modulus....
addition and subtraction, and XOR operations. There are three alternating types of round function, but they are similar in structure and differ only in the choice of the exact operation (addition, subtraction or XOR) at various points.
Although Entrust
Entrust
Entrust Inc. is a $100 million privately-owned software company with 350 employees. It provides identity-based security software and services in the areas of public key infrastructure , multifactor authentication, Secure Socket Layer certificates, fraud detection, digital certificates and mobile...
holds a patent
Patent
A patent is a form of intellectual property. It consists of a set of exclusive rights granted by a sovereign state to an inventor or their assignee for a limited period of time in exchange for the public disclosure of an invention....
on the CAST design procedure, CAST-128 is available worldwide on a royalty-free basis for commercial and non-commercial uses.
Test vectors :
Below is a sample test vector, providing the input and the expected output for the above algorithm. Even, the values of Key Schedule, Km and Kr is provided for both encryption and decryption.
Encryption :
128-bit key = 01 23 45 67 12 34 56 78 23 45 67 89 34 56 78 9A
plaintext = 01 23 45 67 89 AB CD EF
ciphertext = 23 8B 4F E5 84 7E 44 B2
| i | K[i] | Km[i] | Kr[i] |
|---|---|---|---|
| 1 | BC173E26 | BC173E26 | 00000015 |
| 2 | 78A207EF | 78A207EF | 0000001B |
| 3 | ECE0A7F5 | ECE0A7F5 | 00000001 |
| 4 | 7CB0FB6B | 7CB0FB6B | 00000005 |
| 5 | A5D2D636 | A5D2D636 | 00000003 |
| 6 | D78B9407 | D78B9407 | 0000001F |
| 7 | 56C069D3 | 56C069D3 | 0000001F |
| 8 | 82E8240C | 82E8240C | 0000001C |
| 9 | 33543749 | 33543749 | 00000010 |
| 10 | 8813D5C7 | 8813D5C7 | 0000001F |
| 11 | B9FCD732 | B9FCD732 | 00000012 |
| 12 | 59106B36 | 59106B36 | 00000001 |
| 13 | 496AF1A9 | 496AF1A9 | 0000001D |
| 14 | 18F8DC43 | 18F8DC43 | 00000019 |
| 15 | 8D9DEF0F | 8D9DEF0F | 00000001 |
| 16 | 83EDA384 | 83EDA384 | 0000000F |
Decryption :
128-bit key = 01 23 45 67 12 34 56 78 23 45 67 89 34 56 78 9A
plaintext = 23 8B 4F E5 84 7E 44 B2
ciphertext = 01 23 45 67 89 AB CD EF
| i | K[i] | Km[i] | Kr[i] |
|---|---|---|---|
| 1 | BC173E26 | BC173E26 | 00000015 |
| 2 | 78A207EF | 78A207EF | 0000001B |
| 3 | ECE0A7F5 | ECE0A7F5 | 00000001 |
| 4 | 7CB0FB6B | 7CB0FB6B | 00000005 |
| 5 | A5D2D636 | A5D2D636 | 00000003 |
| 6 | D78B9407 | D78B9407 | 0000001F |
| 7 | 56C069D3 | 56C069D3 | 0000001F |
| 8 | 82E8240C | 82E8240C | 0000001C |
| 9 | 33543749 | 33543749 | 00000010 |
| 10 | 8813D5C7 | 8813D5C7 | 0000001F |
| 11 | B9FCD732 | B9FCD732 | 00000012 |
| 12 | 59106B36 | 59106B36 | 00000001 |
| 13 | 496AF1A9 | 496AF1A9 | 0000001D |
| 14 | 18F8DC43 | 18F8DC43 | 00000019 |
| 15 | 8D9DEF0F | 8D9DEF0F | 00000001 |
| 16 | 83EDA384 | 83EDA384 | 0000000F |
See also
- PGPPretty Good PrivacyPretty Good Privacy is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security...
- GPGGNU Privacy GuardGNU Privacy Guard is a GPL Licensed alternative to the PGP suite of cryptographic software. GnuPG is compliant with RFC 4880, which is the current IETF standards track specification of OpenPGP...
- AESAdvanced Encryption StandardAdvanced Encryption Standard is a specification for the encryption of electronic data. It has been adopted by the U.S. government and is now used worldwide. It supersedes DES...
External links
- RFC 2144 — The CAST-128 Encryption Algorithm
- CAST related publications
- SCAN's entry for CAST-128
- List of algorithms approved for Canadian government use

