
3-Way
Encyclopedia
In cryptography
, 3-Way is a block cipher
designed in 1994 by Joan Daemen
, who also (with Vincent Rijmen
) designed Rijndael, the winner of NIST's Advanced Encryption Standard
(AES) contest.
3-Way has a block size
of 96 bit
s, notably not a power of two
such as the more common 64 or 128 bits. The key length is also 96 bits. The figure 96 arises from the use of three 32 bit words in the algorithm, from which also is derived the cipher
's name. When 3-Way was invented, 96-bit keys and blocks were quite strong, but more recent ciphers have a 128-bit block, and few now have keys shorter than 128 bits. 3-Way is an 11-round substitution-permutation network
.
3-Way is designed to be very efficient in a wide range of platforms from 8-bit processors to specialized hardware
, and has some elegant mathematical features which enable nearly all the decryption to be done in exactly the same circuits as did the encryption.
3-Way is vulnerable to related key
cryptanalysis
. John Kelsey
, Bruce Schneier
, and David Wagner showed how it can be broken with one related key query and about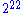 chosen plaintexts
chosen plaintexts
.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, 3-Way is a block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
designed in 1994 by Joan Daemen
Joan Daemen
Joan Daemen |Limburg]], Belgium) is a Belgian cryptographer and one of the designers of Rijndael, the Advanced Encryption Standard , together with Vincent Rijmen. He has also designed or co-designed the MMB, Square, SHARK, NOEKEON, 3-Way, and BaseKing block ciphers...
, who also (with Vincent Rijmen
Vincent Rijmen
Vincent Rijmen is a Belgian cryptographer and one of the two designers of the Rijndael, the Advanced Encryption Standard. Rijmen is also the co-designer of the WHIRLPOOL cryptographic hash function, and the block ciphers Anubis, KHAZAD, Square, NOEKEON and SHARK.In 1993, Rijmen obtained a degree...
) designed Rijndael, the winner of NIST's Advanced Encryption Standard
Advanced Encryption Standard
Advanced Encryption Standard is a specification for the encryption of electronic data. It has been adopted by the U.S. government and is now used worldwide. It supersedes DES...
(AES) contest.
3-Way has a block size
Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
of 96 bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
s, notably not a power of two
Power of two
In mathematics, a power of two means a number of the form 2n where n is an integer, i.e. the result of exponentiation with as base the number two and as exponent the integer n....
such as the more common 64 or 128 bits. The key length is also 96 bits. The figure 96 arises from the use of three 32 bit words in the algorithm, from which also is derived the cipher
Cipher
In cryptography, a cipher is an algorithm for performing encryption or decryption — a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. In non-technical usage, a “cipher” is the same thing as a “code”; however, the concepts...
's name. When 3-Way was invented, 96-bit keys and blocks were quite strong, but more recent ciphers have a 128-bit block, and few now have keys shorter than 128 bits. 3-Way is an 11-round substitution-permutation network
Substitution-permutation network
In cryptography, an SP-network, or substitution-permutation network , is a series of linked mathematical operations used in block cipher algorithms such as AES .Other ciphers that use SPNs are 3-Way, SAFER, SHARK, and Square....
.
3-Way is designed to be very efficient in a wide range of platforms from 8-bit processors to specialized hardware
Computer hardware
Personal computer hardware are component devices which are typically installed into or peripheral to a computer case to create a personal computer upon which system software is installed including a firmware interface such as a BIOS and an operating system which supports application software that...
, and has some elegant mathematical features which enable nearly all the decryption to be done in exactly the same circuits as did the encryption.
3-Way is vulnerable to related key
Related-key attack
In cryptography, a related-key attack is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker...
cryptanalysis
Cryptanalysis
Cryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key...
. John Kelsey
John Kelsey (cryptanalyst)
John Kelsey is a cryptographer currently working at NIST. His research interests include cryptanalysis and design of symmetric cryptography primitives , analysis and design of cryptographic protocols, cryptographic random number generation, electronic voting, side-channel attacks on cryptography...
, Bruce Schneier
Bruce Schneier
Bruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
, and David Wagner showed how it can be broken with one related key query and about
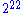 chosen plaintexts
chosen plaintextsChosen-plaintext attack
A chosen-plaintext attack is an attack model for cryptanalysis which presumes that the attacker has the capability to choose arbitrary plaintexts to be encrypted and obtain the corresponding ciphertexts. The goal of the attack is to gain some further information which reduces the security of the...
.
External links
- SCAN's entry for 3-Way
- Chapter 7 of Daemen's thesis (gzipGzipGzip is any of several software applications used for file compression and decompression. The term usually refers to the GNU Project's implementation, "gzip" standing for GNU zip. It is based on the DEFLATE algorithm, which is a combination of Lempel-Ziv and Huffman coding...
ped Postscript)

