
ACE Encrypt
Encyclopedia
ACE — the collection of units, implementing both a public key encryption scheme and a digital signature scheme. Corresponding names for these schemes — «ACE Encrypt» and «ACE Sign». Schemes are based on Cramer-Shoup public key encryption scheme and Cramer-Shoup signature scheme. Introduced variants of these schemes are intended to achieve a good balance between performance and security of the whole encryption system.
Ronald Cramer currently stays in the university of Aarhus, Denmark
. He worked on the project of ACE Encrypt while his staying in ETH in Zürich
, Switzerland
.
Mehdi Nassehi and Thomas Schweinberger worked on ACE project in the IBM research lab in Zürich
, Switzerland
.
Victor Shoup works in the IBM research lab in Zürich
, Switzerland
..
intractability assumptions.
These four assumptions are:
 — The set of integers.
— The set of integers.
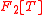 — The set of univariate polynomials with coefficients in the finite field
— The set of univariate polynomials with coefficients in the finite field 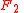 of cardinality 2.
of cardinality 2.
 — integer
— integer  such that
such that  for integer
for integer  and
and  .
.
 — polynomial
— polynomial 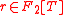 with
with 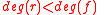 such that
such that  with
with 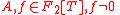 .
.
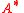 — The set of all strings.
— The set of all strings.
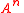 — The set of all strings with length n.
— The set of all strings with length n.
For — length of string
— length of string  . The string of length zero is denoted
. The string of length zero is denoted 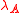 .
.
For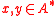
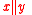 — the result of
— the result of  and
and  concatenation.
concatenation.
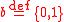 — The set of bits.
— The set of bits.
Let us take all sets of form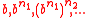 . For such a set A we define the "zero element":
. For such a set A we define the "zero element":
We define as a set of bytes, and
as a set of bytes, and  as a set of words.
as a set of words.
For with
with 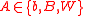 and
and  we define a padding operator:
we define a padding operator:
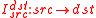 makes a conversion between elements
makes a conversion between elements 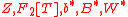 .
.
ACE public key: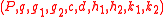 .
.
ACE private key: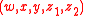 .
.
For a given size parameter m , such that
, such that 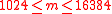 , key components are defined as:
, key components are defined as:
 — a 256-bit prime number.
— a 256-bit prime number.
 — a m-bit prime number, such that
— a m-bit prime number, such that  .
.
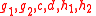 — elements
— elements 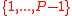 (whose multiplicative order modulo
(whose multiplicative order modulo  divides
divides  ).
).
 — elements
— elements  .
.
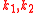 — elements
— elements 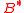 with
with 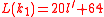 and
and  , where
, where  and
and 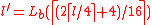 .
.
Input: a size parameter m , such that
, such that 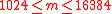 .
.
Output: a public/private key pair.
where the components are defined as:
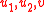 — integers from
— integers from 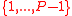 (whose multiplicative order modulo
(whose multiplicative order modulo  divides
divides  ).
).
 — element
— element 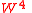 .
.
 — element
— element 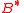 .
.
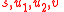 we call the preamble, and
we call the preamble, and  — the cryptogram. If a cleartext is a string consisting of
— the cryptogram. If a cleartext is a string consisting of  байт, then the length of
байт, then the length of  is equal to
is equal to 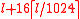 .
.
We need to introduce the function , which maps a ciphertext to its byte-string
, which maps a ciphertext to its byte-string
representation, and the corresponding inverse function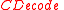 . For the integer
. For the integer  , word string
, word string  , integers
, integers 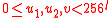 , and byte string
, and byte string 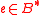 ,
,
For integer , byte string
, byte string 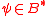 , such that
, such that 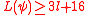 ,
,
input: public key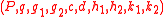 and byte string
and byte string 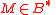 .
.
Output: byte string — ciphertext of
of 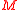 .
.
Before starting of the symmetric encryption process the input message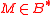 is divided into blocks
is divided into blocks  , where each of the block, possibly except the last one, is of 1024 bytes. Each block is encrypted by the stream cipher. For each encrypted block
, where each of the block, possibly except the last one, is of 1024 bytes. Each block is encrypted by the stream cipher. For each encrypted block 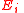 16-byte message authentication code is computed. We get the cryptogram
16-byte message authentication code is computed. We get the cryptogram
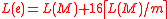 . Note that if
. Note that if 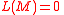 , then
, then 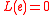 .
.
Algorithm. ACE asymmetric encryption process.
Input: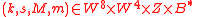

Output: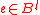 ,
,  .
.
Input: public key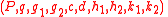 and corresponding private key
and corresponding private key 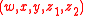 , byt e string
, byt e string 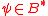 .
.
Output: Decrypted message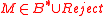 .
.
Algorithm. Decryption operation .
.
Input: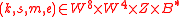

Output: Decrypted message .
.
ACE Signature public key: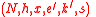 .
.
ACE Signature private key: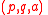 .
.
For the given size parameter , such that
, such that 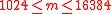 , key components are defined the following way:
, key components are defined the following way:
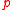 —
— 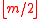 -bit prime number with
-bit prime number with  — is also a prime number.
— is also a prime number.
 —
— 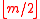 -bit prime number with
-bit prime number with 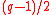 — is also a prime number.
— is also a prime number.
 —
—  and has either
and has either  or
or  бит.
бит.
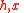 — elements
— elements 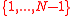 (quadratic residues modulo
(quadratic residues modulo  ).
).
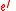 — 161-bit prime number.
— 161-bit prime number.
 — element
— element 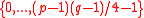
 — elements
— elements 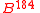 .
.
 — elements
— elements 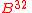 .
.
Input: size parameter , such that
, such that 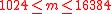 .
.
Output: public/private key pair.
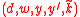 , where the components are defined the following way:
, where the components are defined the following way:
 — element
— element 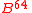 .
.
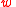 — integer, such that
— integer, such that 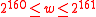 .
.
 — elements
— elements  .
.
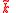 — element
— element 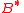 ;note that
;note that  , where
, where  — message being signed.
— message being signed.
We need to introduce the function, which maps a signature into its byte string representation, and the corresponding inverse function
function, which maps a signature into its byte string representation, and the corresponding inverse function 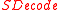 . For integer
. For integer  , byte string
, byte string  , integers
, integers 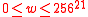 and
and 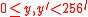 , and byte string
, and byte string 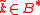 ,
,
For integer , byte string
, byte string 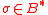 , where
, where 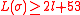 ,
,
Input: public key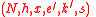 and corresponding private key
and corresponding private key 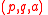 and byte string
and byte string 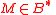 ,
,  .
.
Output: byte string — digital signature .
.
Both schemes were implemented in ANSI C, with the use of GNU GMP library. Tests were done on two platforms: Power PC 604 model 43P under AIX system and 266 MHz Pentium under Windows NT system. Result tables:
Table 1. Time costs on basic operations.
|
|colspan="2" |Power PC
|colspan="2" |Pentium
|-
|
|colspan="2" |Operand size(byte)
|colspan="2" |Operand size(byte)
|-
|
|512
|1024
|512
|1024
|-
|Multiplication
|3.5 * 10^(-5) sec
|1.0 * 10^(-4) sec
|4.5 * 10^(-5) sec
|1.4 * 10^(-4) sec
|-
|Squaring
|3.3 * 10^(-5) sec
|1.0 * 10^(-4) sec
|4.4 * 10^(-5) sec
|1.4 * 10^(-4) sec
|-
|Exponentiation
|1.9 * 10^(-2) sec
|1.2 * 10^(-1) sec
|2.6 * 10^(-2) sec
|1.7 * 10^(-1) sec
|}>
Table 2. Performance of encryption scheme and signature scheme.
|
|colspan="2" |Power PC
|colspan="2" |Pentium
|-
|
|Fixed costs (ms)
|MBit/sec
|Fixed costs (ms)
|MBit/sec
|-
|Encrypt
|160
|18
|230
|16
|-
|Decrypt
|68
|18
|97
|14
|-
|Sign
|48
|64
|62
|52
|-
|Sign set-up
|29
|
|41
|
|-
|Verify
|52
|65
|73
|53
|}>
Authors
All the algorithms, implemented in ACE are based on algorithms developed by Victor Shoup and Ronald Cramer. The full algorithms specification is written by Victor Shoup. Implementation of algorithms is done by Thomas Schweinberger and Mehdi Nassehi, its supporting and maintaining is done by Victor Shoup. Thomas Schweinberger participated in construction of ACE specification document and also wrote a user manual.Ronald Cramer currently stays in the university of Aarhus, Denmark
Denmark
Denmark is a Scandinavian country in Northern Europe. The countries of Denmark and Greenland, as well as the Faroe Islands, constitute the Kingdom of Denmark . It is the southernmost of the Nordic countries, southwest of Sweden and south of Norway, and bordered to the south by Germany. Denmark...
. He worked on the project of ACE Encrypt while his staying in ETH in Zürich
Zürich
Zurich is the largest city in Switzerland and the capital of the canton of Zurich. It is located in central Switzerland at the northwestern tip of Lake Zurich...
, Switzerland
Switzerland
Switzerland name of one of the Swiss cantons. ; ; ; or ), in its full name the Swiss Confederation , is a federal republic consisting of 26 cantons, with Bern as the seat of the federal authorities. The country is situated in Western Europe,Or Central Europe depending on the definition....
.
Mehdi Nassehi and Thomas Schweinberger worked on ACE project in the IBM research lab in Zürich
Zürich
Zurich is the largest city in Switzerland and the capital of the canton of Zurich. It is located in central Switzerland at the northwestern tip of Lake Zurich...
, Switzerland
Switzerland
Switzerland name of one of the Swiss cantons. ; ; ; or ), in its full name the Swiss Confederation , is a federal republic consisting of 26 cantons, with Bern as the seat of the federal authorities. The country is situated in Western Europe,Or Central Europe depending on the definition....
.
Victor Shoup works in the IBM research lab in Zürich
Zürich
Zurich is the largest city in Switzerland and the capital of the canton of Zurich. It is located in central Switzerland at the northwestern tip of Lake Zurich...
, Switzerland
Switzerland
Switzerland name of one of the Swiss cantons. ; ; ; or ), in its full name the Swiss Confederation , is a federal republic consisting of 26 cantons, with Bern as the seat of the federal authorities. The country is situated in Western Europe,Or Central Europe depending on the definition....
..
Security
The encryption scheme in ACE can be proven secure under reasonable and naturalintractability assumptions.
These four assumptions are:
- The Decisional Diffie-Hellman (DDH) assumption
- Strong RSA assumption
- SHA-1 second preimage collision resistance
- MARS sum/counter mode pseudo-randomness
Basic mathematical notation
 — The set of integers.
— The set of integers.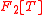 — The set of univariate polynomials with coefficients in the finite field
— The set of univariate polynomials with coefficients in the finite field 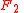 of cardinality 2.
of cardinality 2. — integer
— integer  such that
such that  for integer
for integer  and
and  .
. — polynomial
— polynomial 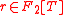 with
with 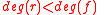 such that
such that  with
with 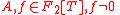 .
.Basic string notation
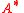 — The set of all strings.
— The set of all strings.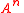 — The set of all strings with length n.
— The set of all strings with length n.For
 — length of string
— length of string  . The string of length zero is denoted
. The string of length zero is denoted 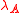 .
.For
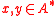
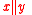 — the result of
— the result of  and
and  concatenation.
concatenation.Bits,Bytes,Words
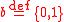 — The set of bits.
— The set of bits.Let us take all sets of form
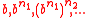 . For such a set A we define the "zero element":
. For such a set A we define the "zero element":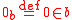 ;
; for
for  .
.
We define
 as a set of bytes, and
as a set of bytes, and  as a set of words.
as a set of words.For
 with
with 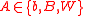 and
and  we define a padding operator:
we define a padding operator: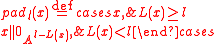 .
.
Conversion operator
Conversion operator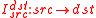 makes a conversion between elements
makes a conversion between elements 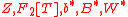 .
.Encryption Key Pair
The encryption scheme employs two key types:ACE public key:
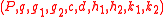 .
.ACE private key:
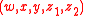 .
.For a given size parameter m
 , such that
, such that 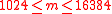 , key components are defined as:
, key components are defined as: — a 256-bit prime number.
— a 256-bit prime number. — a m-bit prime number, such that
— a m-bit prime number, such that  .
.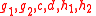 — elements
— elements 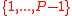 (whose multiplicative order modulo
(whose multiplicative order modulo  divides
divides  ).
). — elements
— elements  .
.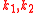 — elements
— elements 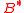 with
with 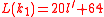 and
and  , where
, where  and
and 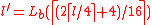 .
.Key Generation
Algorithm. Key Generation for ACE encryption scheme.Input: a size parameter m
 , such that
, such that 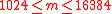 .
.Output: a public/private key pair.
- Generate a random prime
 , such that
, such that 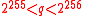 .
. - Generate a random prime
 ,
, 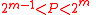 , such that
, such that  .
. - Generate a random integer
 , such that
, such that 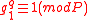 .
. - Generate random integers
 and
and 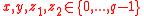
- Compute the following integers in
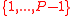 :
: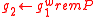 ,
, ,
,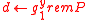 ,
,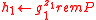 ,
,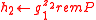 .
. - Generate random byte strings
 and
and 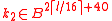 , where
, where 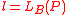 and
and 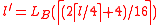 .
. - Return the public key/private key pair

Ciphertext Representation
A ciphertext of the ACE encryption scheme has the form ,
,
where the components are defined as:
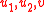 — integers from
— integers from 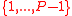 (whose multiplicative order modulo
(whose multiplicative order modulo  divides
divides  ).
). — element
— element 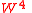 .
. — element
— element 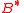 .
. we call the preamble, and
we call the preamble, and  — the cryptogram. If a cleartext is a string consisting of
— the cryptogram. If a cleartext is a string consisting of  байт, then the length of
байт, then the length of  is equal to
is equal to 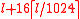 .
.We need to introduce the function
 , which maps a ciphertext to its byte-string
, which maps a ciphertext to its byte-stringrepresentation, and the corresponding inverse function
 . For the integer
. For the integer  , word string
, word string  , integers
, integers 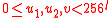 , and byte string
, and byte string  ,
,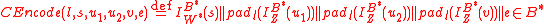 .
.
For integer
 , byte string
, byte string 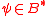 , such that
, such that 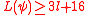 ,
, .
.
Encryption Process
Algorithm. ACE asymmetric encryption operation.input: public key
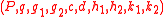 and byte string
and byte string 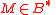 .
.Output: byte string — ciphertext
 of
of 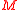 .
.
- Generate
 at random.
at random. - Generate the ciphertext preamble:
- Generate
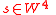 at random.
at random. - Compute
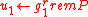 ,
,  .
. - Compute
 ; note that
; note that  .
. - Compute
 .
.
- Generate
- Compute the key for the symmetric encryption operation:
-
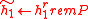 ,
, 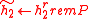 .
. - Compute
 .
.
-
- Compute cryptogram
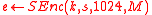 .
. - Encode the ciphertext:
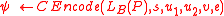 .
. - Return
 .
.
Before starting of the symmetric encryption process the input message
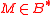 is divided into blocks
is divided into blocks  , where each of the block, possibly except the last one, is of 1024 bytes. Each block is encrypted by the stream cipher. For each encrypted block
, where each of the block, possibly except the last one, is of 1024 bytes. Each block is encrypted by the stream cipher. For each encrypted block 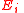 16-byte message authentication code is computed. We get the cryptogram
16-byte message authentication code is computed. We get the cryptogram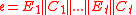 .
.
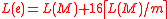 . Note that if
. Note that if 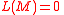 , then
, then  .
.Algorithm. ACE asymmetric encryption process.
Input:
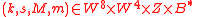

Output:
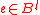 ,
,  .
.
- If
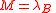 , then return
, then return  .
. - Initialize a pseudo-random generator state:
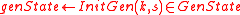
- Generate the key
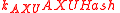 :
:
 .
.
-
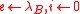 .
. - While
 , do the following:
, do the following:
-
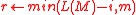 .
. - Generate mask values for the encryption and MAC:
-
 .
. -
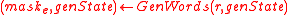 .
.
-
- Encrypt the plaintext:
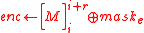 .
. - Generate the message authentication code:
- If
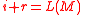 , then
, then 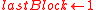 ; else
; else 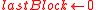 .
. -
 .
.
- If
- Update the ciphertext:
 .
. -
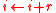 .
.
-
- Return
 .
.
Decryption process
Algorithm. ACE decryption process.Input: public key
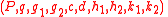 and corresponding private key
and corresponding private key 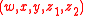 , byt e string
, byt e string 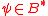 .
.Output: Decrypted message
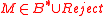 .
.
- Decrypt the ciphertext:
- If
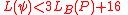 , then return
, then return 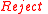 .
. - Compute:
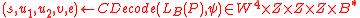 ;
;
note that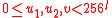 , where
, where 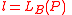 .
.
- If
- Verify the ciphertext preamble:
- If
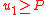 or
or  or
or  , then return
, then return 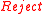 .
. - If
 , then return
, then return 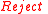 .
. -
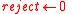 .
. - If
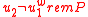 , then
, then  .
. - Compute
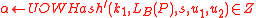 ; note that
; note that 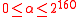 .
. - If
 , then
, then 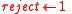 .
. - If
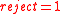 , then return
, then return 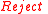 .
.
- If
- Compute the key for the symmetric decryption operation:
-
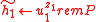 ,
, 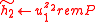 .
. - Compute
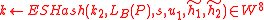 .
.
-
- Compute
 ;note that
;note that  can return
can return 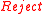 .
. - Return
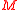 .
.
Algorithm. Decryption operation
 .
.Input:
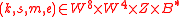

Output: Decrypted message
 .
.
- If
 , then return
, then return 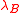 .
. - Initialize a pseudo-random generator state:
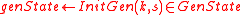
- Generate the key
 :
: .
. -
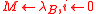 .
. - While
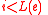 , do the following:
, do the following:
-
 .
. - If
 , then return
, then return 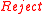 .
. - Generate mask values for the encryption and MAC:
-
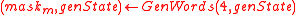 .
. -
 .
.
-
- Verify the message authentication code:
- If
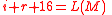 , then
, then  ; else
; else 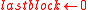 .
. -
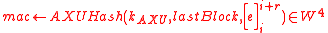 .
. - If
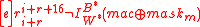 , then return
, then return 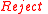 .
.
- If
- Update the plaintext:
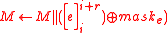 .
. -
 .
.
-
- Return
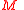 .
.
Signature Scheme
The signature scheme employs two key types:ACE Signature public key:
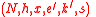 .
.ACE Signature private key:
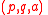 .
.For the given size parameter
 , such that
, such that 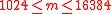 , key components are defined the following way:
, key components are defined the following way: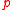 —
— 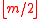 -bit prime number with
-bit prime number with  — is also a prime number.
— is also a prime number. —
— 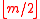 -bit prime number with
-bit prime number with 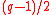 — is also a prime number.
— is also a prime number. —
—  and has either
and has either  or
or  бит.
бит.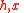 — elements
— elements 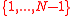 (quadratic residues modulo
(quadratic residues modulo  ).
).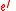 — 161-bit prime number.
— 161-bit prime number. — element
— element 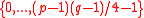
 — elements
— elements 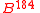 .
. — elements
— elements 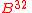 .
.Key Generation
Algorithm. Key generation for the ACE public-key signature scheme.Input: size parameter
 , such that
, such that 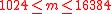 .
.Output: public/private key pair.
- Generate random prime numbers
 , such that
, such that 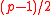 and
and 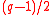 — is also a prime number, and
— is also a prime number, and 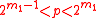 ,
, 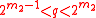 , и
, и  ,
,
where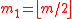 and
and 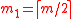 .
. - Set
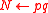 .
. - Generate random prime number
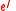 , где
, где 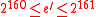 .
. - Generate random
 , taking into account
, taking into account 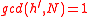 and
and 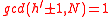 , and compute
, and compute 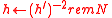 .
. - Generate random
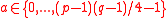 and compute
and compute  .
. - Generate random byte strings
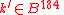 , and
, and 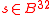 .
. - Return public key/private key pair
 .
.
Signature Representation
The signature in the ACE signature scheme has the form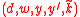 , where the components are defined the following way:
, where the components are defined the following way: — element
— element 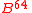 .
. — integer, such that
— integer, such that 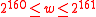 .
. — elements
— elements  .
.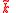 — element
— element 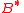 ;note that
;note that  , where
, where  — message being signed.
— message being signed.We need to introduce the
 function, which maps a signature into its byte string representation, and the corresponding inverse function
function, which maps a signature into its byte string representation, and the corresponding inverse function 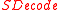 . For integer
. For integer  , byte string
, byte string  , integers
, integers  and
and 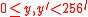 , and byte string
, and byte string 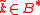 ,
,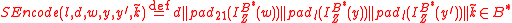 .
.
For integer
 , byte string
, byte string 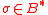 , where
, where 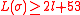 ,
,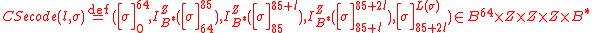 .
.
Signature Generation Process
Algorithm. ACE Signature Generation Process.Input: public key
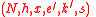 and corresponding private key
and corresponding private key 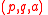 and byte string
and byte string 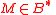 ,
,  .
.Output: byte string — digital signature
 .
.
- Perform the following steps to hash the input data:
- Generate a hash key
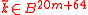 at random, such that
at random, such that  .
. - Compute
 .
.
- Generate a hash key
- Select
 at random, and compute
at random, and compute 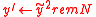 .
. - Compute
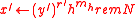 .
. - Generate a random prime
 ,
, 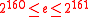 , and its certificate of correctness
, and its certificate of correctness  :
: 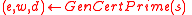 . Repeat this step until
. Repeat this step until  .
. - Set
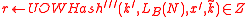 ; note that
; note that 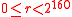 .
. - Compute
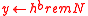 , where
, where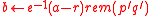 ,
,
and where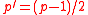 and
and 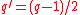 .
. - Encode the signature:
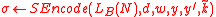 .
. - Return

Implementation, Utilization and Performance
ACE Encryption scheme is recommended by NESSIE (New European Schemes for Signatures, Integrity and Encryption) as asymmetric encryption scheme. Press-release is dated by February of 2003.Both schemes were implemented in ANSI C, with the use of GNU GMP library. Tests were done on two platforms: Power PC 604 model 43P under AIX system and 266 MHz Pentium under Windows NT system. Result tables:
Table 1. Time costs on basic operations.
|colspan="2" |Power PC
|colspan="2" |Pentium
|-
|
|colspan="2" |Operand size(byte)
|colspan="2" |Operand size(byte)
|-
|
|512
|1024
|512
|1024
|-
|Multiplication
|3.5 * 10^(-5) sec
|1.0 * 10^(-4) sec
|4.5 * 10^(-5) sec
|1.4 * 10^(-4) sec
|-
|Squaring
|3.3 * 10^(-5) sec
|1.0 * 10^(-4) sec
|4.4 * 10^(-5) sec
|1.4 * 10^(-4) sec
|-
|Exponentiation
|1.9 * 10^(-2) sec
|1.2 * 10^(-1) sec
|2.6 * 10^(-2) sec
|1.7 * 10^(-1) sec
|}>
Table 2. Performance of encryption scheme and signature scheme.
|colspan="2" |Power PC
|colspan="2" |Pentium
|-
|
|Fixed costs (ms)
|MBit/sec
|Fixed costs (ms)
|MBit/sec
|-
|Encrypt
|160
|18
|230
|16
|-
|Decrypt
|68
|18
|97
|14
|-
|Sign
|48
|64
|62
|52
|-
|Sign set-up
|29
|
|41
|
|-
|Verify
|52
|65
|73
|53
|}>

