Autorun
Encyclopedia
AutoRun and the companion feature AutoPlay
are components of the Microsoft Windows
operating system
that dictate what actions the system takes when a drive is mounted
.
AutoRun was introduced in Windows 95
to ease application installation for non-technical users and reduce the cost of software support calls. When an appropriately configured CD-ROM
is inserted into a CD-ROM drive, Windows detects the arrival and checks the contents for a special file containing a set of instructions. For a commercial application, these instructions normally initiate installation of the software from the CD-ROM. To maximise the likelihood of installation success, AutoRun also acts when the drive is accessed ("double-click
ed") in Windows Explorer
(or "My Computer").
Until the introduction of Windows XP
, the terms AutoRun and AutoPlay were used interchangeably, developers often using the former term and end users the latter. This tendency is reflected in Windows Policy settings named AutoPlay that change Windows Registry entries named AutoRun, and in the autorun.inf
file which causes "AutoPlay" to be added to drives’ context menu
s. The terminology was of little importance until the arrival of Windows XP and its addition of a new feature to assist users in selecting appropriate actions when new media and devices were detected. This new feature was called AutoPlay and a differentiation between the two terms was created.
, stored in the root directory
of the medium.
Primarily used on installation CD-ROMs, the applications called are usually application installers. The autorun.inf file can also specify an icon which will represent the device visually in Explorer along with other advanced features.
The terms AutoRun and AutoPlay tend to be interchangeably used when referring to the initiating action, the action that detects and starts reading from discovered volume
s. The flowchart illustration in the AutoPlay article shows how AutoRun is positioned as a layer between AutoPlay and the Shell Hardware Detection service and may help in understanding the terminology. However, to avoid confusion, this article uses the term AutoRun when referring to the initiating action.
 AutoPlay
AutoPlay
is a feature introduced in Windows XP which examines removable media and devices and, based on content such as pictures, music or video files, launches an appropriate application to play or display the content. If available, settings in an autorun.inf file can add to the options presented to the user.
AutoPlay is based on a set of handler applications registered with the AutoPlay system. Each media type (Pictures, Music, Video) can have a set of registered handlers which can deal with playing or display that type of media.
Each hardware device can have a default action occurring on discovery of a particular media type, or the AutoPlay dialog can prompt the user what action to take.
settings to see if AutoRun can proceed, parsing of an optional autorun.inf may occur and any necessary actions are taken.(not working)
The initial sequence is handled much the same in every version of Windows from Windows 95. However, the way the autorun.inf file is read and acted upon and the level of integration of AutoRun with AutoPlay has changed significantly from the time AutoPlay was introduced in Windows XP until the present handling in Windows 7.
then notifies interested applications that a device change has occurred. The notification method used can change depending on the device type.
If the device changed is a volume (like a CD) or a port (like a serial port) Windows broadcasts a WM_DEVICECHANGE notification to all top-level windows. Windows calls this a "basic" notification. A top-level window is one which is a descendant of the desktop.
However, if the device changed is not one of these types an application can use the RegisterDeviceNotification function to register to receive device notifications.
Non-volume devices are those devices that do not appear as drive letters in "My Computer". These are not handled by any part of AutoRun - any actions taken for these devices are taken either by device specific software or by AutoPlay. See AutoPlay#Devices that are not drives.
When Explorer receives notification of a volume change, it performs a number of actions:
AutoRun will work with network drives (the DRIVE_REMOTE drive type) that are mapped to a drive letter. AutoRun will also work with floppy drives that are provided with autorun-compatible drivers.
The default Registry settings on Windows versions prior to Windows XP (See NoDriveTypeAutoRun), disable Remote and Removable drives from AutoRun initiation, leaving Fixed and CDROM drive types active by default.
The default Registry settings add Removable drives to those that initiated AutoRun. In Windows XP and higher, except Windows Server 2003, only the Unknown and Remote drive types are not active for AutoRun.
The handling of the autorun.inf file changes very significantly between each Windows version. The details can be found in the autorun.inf article. The current handling in Windows 7 is that only drives of type DRIVE_CDROM may specify an AutoRun task, alter double-click behaviour or change context menus.
However, it is important to note that:
values to decide whether to initiate actions for any particular drive or drive type. These values can be changed using several methods, one of which is using Group Policy
.
The primary relevant Registry entry names are NoDriveTypeAutoRun and NoDriveAutoRun. These exist in both per-machine and per-user settings and their location and priority in the Registry are described in further detail below.
A Registry key is similar to a folder that, in addition to values, each key can contain subkeys which in turn may contain subkeys, and so on.
A Registry value consists of a name-data pair. Microsoft documentation commonly uses the term "entry" as an equivalent term. It also uses "value" for "data" when it is obvious what is meant. To avoid confusion, this article always uses the term "entry" when referring to the name-data pair.
Two Registry keys that are very commonly referred to are HKEY_LOCAL_MACHINE which contains per-machine settings, and HKEY_CURRENT_USER which contains settings for the currently logged-on user. These are almost always abbreviated as HKLM and HKCU respectively. There may be many users of a machine; their settings are stored in HKEY_USERS, HKCU is actually just a link to the appropriate place in HKEY_USERS.
They can be changed indirectly by using Group Policy, applied locally to a single computer with GPEdit.msc or to a domain with gpmc.msc.
It may be necessary to either logout or restart the computer in order for any Registry changes to take effect.
When deciding whether to activate AutoRun, both NoDriveAutoRun and NoDriveTypeAutoRun Registry entries are consulted. If either value indicates a drive should be disabled then AutoRun is disabled for that drive.
Thus in the following example:
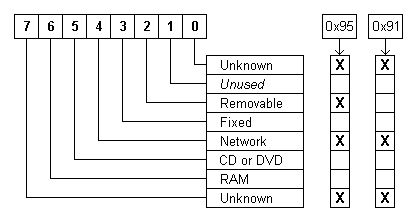
the data value taken for NoDriveAutoRun is 0x08, disabling drive D and the data value taken for NoDriveTypeAutoRun is 0x95, disabling removable and network drives. The per-user NoDriveAutoRun entry is never used.
This Registry entry disables or enables the AutoRun feature on all drives of the type specified. It reflects the setting of the relevant Autoplay Group Policy. Valid data ranges from 0x00 to 0xFF in hexadecimal
notation. If the entry is not present, the default data value is either 0x95 or 0x91 depending on the version of Windows used. An entry present in HKLM overrides any entry present in HKCU.
The entry data is a bitmapped value, where a bit set to 1 disables AutoRun on a particular type of drive. The bit settings for each type of drive are shown below:
Note that bit number 1 is unused and that the "Unknown" type is represented twice. Setting all bits to 1 would give a hexadecimal value of 0xFF, decimal 255, and would disable AutoRun on all types of drives.
The default setting for this entry depends on the version of Windows being used:
This Registry entry disables or enables the AutoRun feature on individual drives. It is not associated with a Group Policy and does not exist by default. The data value is taken to be 0 if the entry is not present. An entry present in HKLM overrides any entry present in HKCU.
The data is a 32 bit (DWORD) bitmapped value, of which the lower 26 bits are used to represent each of the 26 drive letters from A to Z. Thus the valid data range is from 0x0 to 0x03FFFFFF. The least significant bit (the right most bit) represents drive A, and the 26th bit from the right represents drive Z.
A bit set to 1 disables AutoRun on a particular drive. For example, if the data value is set to 0x8 (1000 binary), AutoRun is disabled on drive D.
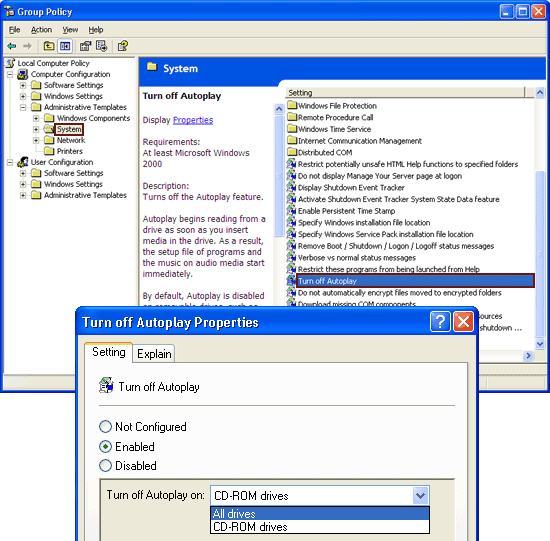 The only Group Policy settings available for AutoRun affect the NoDriveTypeAutoRun Registry entries. The policy is available on either a per-machine or a per-user basis reflecting the Registry entry location in either HKLM or HKCU. As described above, a per-machine policy setting will cause the per-user policy setting to be ignored.
The only Group Policy settings available for AutoRun affect the NoDriveTypeAutoRun Registry entries. The policy is available on either a per-machine or a per-user basis reflecting the Registry entry location in either HKLM or HKCU. As described above, a per-machine policy setting will cause the per-user policy setting to be ignored.
When a policy is Enabled, Group Policy will add the NoDriveTypeAutoRun entry to the Registry. If the policy is Disabled or set to Not configured, Group Policy deletes this entry from the Registry. System defaults may then take effect as described in the NoDriveTypeAutoRun section.
The policy names, locations and possible settings vary slightly between Windows versions. The list of settings are relatively short and are always additional to the system default setting. Therefore, on Windows 2000, enabling the "Disable Autoplay" policy and setting it to "CD-ROM drives", disables AutoRun (as distinct from AutoPlay) for CD-ROM and DVD drives, removable drives, network drives, and drives of unknown type.
This setting cannot be used to enable AutoRun on drives on which it is disabled by default or disable AutoRun for drives not listed. To disable or enable any particular drives or drive types, the Registry must be edited manually.
The per-user policy location is:
The relevant policy is "Turn off Autoplay". In Windows 2000 the policy is called "Disable Autoplay" instead.
Once the policy is Enabled it can be set to "All drives" or "CD-ROM drives". The latter setting adds CD-ROM drives to the existing list of disabled drive types as described above.
The per-user policy location is:
The relevant policy is "Turn off Autoplay" and can be set for CD-ROM, DVD-ROM and removable drives or all drives.
Two related policies were added in Vista and Server 2008:
Given that Shift must be held down until Windows checks for it, it may be a considerable amount of time before it becomes effective. The time taken primarily depends on the time to recognise the new hardware and the time taken for CD-ROMs to spin up. It is unsafe to rely on this method.
For CD-ROM drives, changing the value of this Registry entry to 0 will disable Auto Insert Notification for CD-ROM drives only. A Windows restart will be necessary.
Under Windows 95/98/ME, this setting can be changed under Device Manager, accessible from the System icon in Control Panel.
 Although the Registry entry is named "AutoRun", it only suppresses the MCN message. The MCN message does trigger AutoRun initiation but it also instructs the Explorer shell to update its views and contents.
Although the Registry entry is named "AutoRun", it only suppresses the MCN message. The MCN message does trigger AutoRun initiation but it also instructs the Explorer shell to update its views and contents.
Thus, as a side effect only, this disables AutoRun for CD-ROM drives. However, Explorer will now not update its view when a new CD is inserted; it will show the contents of the previous CD until is pressed or View/Refresh is selected from the Explorer menu. This could result in severe confusion for users.
For this reason the Media Change Notification message should not be disabled unless there is absolutely no alternative; AutoRun can be disabled for individual drives using Group Policy or the Registry.
This entry is used to suppress the MCN message for specifically listed type of CD-ROM drive, primarily CD-ROM changers. The data is a set of device identifiers, which matches those identifiers reported to the system by the devices themselves.
The default value for this entry consists of products identified by Microsoft testing as being unable to support AutoRun. This entry should not be altered from its default.
However, Group Policy would be the accepted method of disabling AutoRun on an entire Windows domain.
In the above example, AutoRun would be disabled for all drives and for all users. This example would need to be run as Administrator and a reboot would be needed for the setting to take complete effect.
leverages autorun.inf functionality to infect a machine. Previous versions of Windows do not have this policy setting but the use of initialisation file mapping is an effective workaround.
As an autorun.inf file is a standard Windows INI file, the appropriate API calls are used by Windows when fetching its settings. These API calls can be redirected using the INI file mapping method. The following Registry file illustrates the workaround, where all autorun.inf settings are taken solely from the HKEY_LOCAL_MACHINE\Software\DoesNotExist Registry key:
As this key does not exist, it is as if the autorun.inf file contains no settings information. It is important to note that this applies to any autorun.inf in any location and on any drive.
Both the policy setting and this workaround have the drawback is that installation of software from an autorunning install CD or DVD is no longer automatic. It will be necessary to view the CD's autorun.inf file and then execute the appropriate install program manually.
When AutoRun is disabled, Windows should not proceed further through the activation sequence than the Registry check. However, it parses any autorun.inf found and does everything except the final action to invoke AutoPlay or execute an application.
This leaves the user open to attack from malware which uses the autorun.inf to alter the double-click and contextual menu behaviours. Double clicking the drive icon will infect the machine. Right Clicking and selecting the "Explore" or "Open" options from the context menu is not a workaround as these menu items can be coopted by the appropriate autorun.inf entries.
This bug was fixed in a number of security updates, detailed in Microsoft Knowledge Base
article 967715.
In the same category are mixed content CD-ROMs. An audio CD, that a user would not expect to contain software at all, can contain a data section with an autorun.inf. Some companies, such as Sony BMG
, have used this vector to install malware that attempts to protect against copying of the audio tracks.
U3
enabled flash drives, by emulating
a CD-ROM unit, can also cause Windows to execute commands from the autorun.inf found on the emulated CD-ROM.
Devices like the Huawei E220
HSDPA modem, validly use this method to autoinstall drivers for the modem itself. However plugging in a flash drive from an unknown source is an unwise move. USB Switchblade, and other similar tools, have made U3 flash drive attacks trivial. Given the ease of writing script
based attacks, anti-virus software may be ineffective in preventing data and password stealing.
 With a standard flash drive, social engineering attacks can be employed to entice a user to click on the appropriate item in the AutoPlay dialog. An alluring action string promising free games or pornography would lure many users into the trap. At any time, double clicking on the drive icon will use the autorun.inf automatically, a trap more advanced users could fall into.
With a standard flash drive, social engineering attacks can be employed to entice a user to click on the appropriate item in the AutoPlay dialog. An alluring action string promising free games or pornography would lure many users into the trap. At any time, double clicking on the drive icon will use the autorun.inf automatically, a trap more advanced users could fall into.
Any user can configure AutoPlay to make various decisions for them; by checking the appropriate box in the AutoPlay dialog, running flash drive malware becomes silent and automatic.
AutoRun malware has been extended to use hard drives, picture frames and other digital devices. Care in dealing with external devices is a security priority.
exposure to these attacks can be minimised through the appropriate use of Group Policy and Registry settings. The following security policies are a summary of those described within this article:
In addition, the following actions have been recommended by Microsoft, primarily during the Conficker
worm attacks:
AutoPlay
AutoPlay, a feature introduced in Windows XP, examines newly discovered removable media and devices and, based on content such as pictures, music or video files, launches an appropriate application to play or display the content. It is closely related to the AutoRun operating system feature...
are components of the Microsoft Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
that dictate what actions the system takes when a drive is mounted
Mount (computing)
Mounting takes place before a computer can use any kind of storage device . The user or their operating system must make it accessible through the computer's file system. A user can access only files on mounted media.- Mount point :A mount point is a physical location in the partition used as a...
.
AutoRun was introduced in Windows 95
Windows 95
Windows 95 is a consumer-oriented graphical user interface-based operating system. It was released on August 24, 1995 by Microsoft, and was a significant progression from the company's previous Windows products...
to ease application installation for non-technical users and reduce the cost of software support calls. When an appropriately configured CD-ROM
CD-ROM
A CD-ROM is a pre-pressed compact disc that contains data accessible to, but not writable by, a computer for data storage and music playback. The 1985 “Yellow Book” standard developed by Sony and Philips adapted the format to hold any form of binary data....
is inserted into a CD-ROM drive, Windows detects the arrival and checks the contents for a special file containing a set of instructions. For a commercial application, these instructions normally initiate installation of the software from the CD-ROM. To maximise the likelihood of installation success, AutoRun also acts when the drive is accessed ("double-click
Double-click
A double-click is the act of pressing a computer mouse button twice quickly without moving the mouse. Double-clicking allows two different actions to be associated with the same mouse button...
ed") in Windows Explorer
Windows Explorer
This article is about the Windows file system browser. For the similarly named web browser, see Internet ExplorerWindows Explorer is a file manager application that is included with releases of the Microsoft Windows operating system from Windows 95 onwards. It provides a graphical user interface...
(or "My Computer").
Until the introduction of Windows XP
Windows XP
Windows XP is an operating system produced by Microsoft for use on personal computers, including home and business desktops, laptops and media centers. First released to computer manufacturers on August 24, 2001, it is the second most popular version of Windows, based on installed user base...
, the terms AutoRun and AutoPlay were used interchangeably, developers often using the former term and end users the latter. This tendency is reflected in Windows Policy settings named AutoPlay that change Windows Registry entries named AutoRun, and in the autorun.inf
Autorun.inf
An autorun.inf file is a text file that can be used by the AutoRun and AutoPlay components of Microsoft Windows Operating systems. For the file to be discovered and used by these components, it must be located in the root directory of a volume...
file which causes "AutoPlay" to be added to drives’ context menu
Context menu
A context menu is a menu in a graphical user interface that appears upon user interaction, such as a right mouse click or middle click mouse operation...
s. The terminology was of little importance until the arrival of Windows XP and its addition of a new feature to assist users in selecting appropriate actions when new media and devices were detected. This new feature was called AutoPlay and a differentiation between the two terms was created.
AutoRun
AutoRun, a feature of Windows Explorer (actually of the shell32 dll) introduced in Windows 95, enables media and devices to launch programs by use of commands listed in a file called autorun.infAutorun.inf
An autorun.inf file is a text file that can be used by the AutoRun and AutoPlay components of Microsoft Windows Operating systems. For the file to be discovered and used by these components, it must be located in the root directory of a volume...
, stored in the root directory
Root directory
In computer file systems, the root directory is the first or top-most directory in a hierarchy. It can be likened to the root of a tree — the starting point where all branches originate.-Metaphor:...
of the medium.
Primarily used on installation CD-ROMs, the applications called are usually application installers. The autorun.inf file can also specify an icon which will represent the device visually in Explorer along with other advanced features.
The terms AutoRun and AutoPlay tend to be interchangeably used when referring to the initiating action, the action that detects and starts reading from discovered volume
Volume (computing)
In the context of computer operating systems, volume is the term used to describe a single accessible storage area with a single file system, typically resident on a single partition of a hard disk. Similarly, it refers to the logical interface used by an operating system to access data stored on...
s. The flowchart illustration in the AutoPlay article shows how AutoRun is positioned as a layer between AutoPlay and the Shell Hardware Detection service and may help in understanding the terminology. However, to avoid confusion, this article uses the term AutoRun when referring to the initiating action.
AutoPlay

AutoPlay
AutoPlay, a feature introduced in Windows XP, examines newly discovered removable media and devices and, based on content such as pictures, music or video files, launches an appropriate application to play or display the content. It is closely related to the AutoRun operating system feature...
is a feature introduced in Windows XP which examines removable media and devices and, based on content such as pictures, music or video files, launches an appropriate application to play or display the content. If available, settings in an autorun.inf file can add to the options presented to the user.
AutoPlay is based on a set of handler applications registered with the AutoPlay system. Each media type (Pictures, Music, Video) can have a set of registered handlers which can deal with playing or display that type of media.
Each hardware device can have a default action occurring on discovery of a particular media type, or the AutoPlay dialog can prompt the user what action to take.
AutoRun activation
The AutoRun sequence starts with the initial discovery of a new device or new piece of media. Following this, notification of interested parties occurs, of which the Windows Explorer shell is of primary interest. After checking certain RegistryWindows registry
The Windows Registry is a hierarchical database that stores configuration settings and options on Microsoft Windows operating systems. It contains settings for low-level operating system components as well as the applications running on the platform: the kernel, device drivers, services, SAM, user...
settings to see if AutoRun can proceed, parsing of an optional autorun.inf may occur and any necessary actions are taken.(not working)
The initial sequence is handled much the same in every version of Windows from Windows 95. However, the way the autorun.inf file is read and acted upon and the level of integration of AutoRun with AutoPlay has changed significantly from the time AutoPlay was introduced in Windows XP until the present handling in Windows 7.
Initiation and notification
When a device with AutoRun-compatible drivers receives new media, a "Media Change Notification" event occurs. The Windows OSOperating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
then notifies interested applications that a device change has occurred. The notification method used can change depending on the device type.
If the device changed is a volume (like a CD) or a port (like a serial port) Windows broadcasts a WM_DEVICECHANGE notification to all top-level windows. Windows calls this a "basic" notification. A top-level window is one which is a descendant of the desktop.
However, if the device changed is not one of these types an application can use the RegisterDeviceNotification function to register to receive device notifications.
An article on the CodeProject website, "Detecting Hardware Insertion and/or Removal", with clarifications from a blog by Doran Holan is of particular technical interest here.
Non-volume devices are those devices that do not appear as drive letters in "My Computer". These are not handled by any part of AutoRun - any actions taken for these devices are taken either by device specific software or by AutoPlay. See AutoPlay#Devices that are not drives.
When Explorer receives notification of a volume change, it performs a number of actions:
- Checks to see if AutoRun has been disabled through the Registry. If AutoRun is disabled for that drive or drive type, Explorer does not proceed further. There have been bugs in this area.
- Checks that the root directory of the inserted media contains an autorun.inf file, which might be read. See below.
- Sends a QueryCancelAutoPlay message to the foreground window. An application which has registered its interest in receiving this message using RegisterWindowMessage can respond to this message to halt AutoRun (and thus AutoPlay) at this point. Any application, foreground or not, can also be notified by using the IQueryCancelAutoPlay COMComponent Object ModelComponent Object Model is a binary-interface standard for software componentry introduced by Microsoft in 1993. It is used to enable interprocess communication and dynamic object creation in a large range of programming languages...
interface available in Windows XP and later. - Alters double-clickDouble-clickA double-click is the act of pressing a computer mouse button twice quickly without moving the mouse. Double-clicking allows two different actions to be associated with the same mouse button...
and contextual menu behaviours. When a user double clicks on the drive icon in Explorer or right clicks to get a context menu, what happens is fully programmable by settings in the autorun.inf file. - Adds an autorun.inf controllable icon and descriptive text to the drive icon.
- Checks to see if the key is held down. If it is then Windows Vista (and later Windows versions) will invoke the AutoPlay dialog regardless of settings to the contrary. Previous versions of Windows will not continue with the process.
- Finally, if this point has been reached, either:
- takes no further action.
- executes the "AutoRun task", the application optionally specified in the
openorshellexecutekeys in an autorun.inf's [autorun] section. - invokes AutoPlay.
Which choice is made depends on the version of Windows in use, instructions from the autorun.inf if available and the type of the media discovered.
Before AutoPlay
On Windows versions prior to Windows XP, an autorun.inf file on any drive type will be read and its instructions followed. The AutoRun task, if specified, is executed immediately without user interaction. This includes DRIVE_REMOVABLE, DRIVE_FIXED and DRIVE_REMOTE drive types.AutoRun will work with network drives (the DRIVE_REMOTE drive type) that are mapped to a drive letter. AutoRun will also work with floppy drives that are provided with autorun-compatible drivers.
The default Registry settings on Windows versions prior to Windows XP (See NoDriveTypeAutoRun), disable Remote and Removable drives from AutoRun initiation, leaving Fixed and CDROM drive types active by default.
Introducing AutoPlay
With the introduction of AutoPlay in Windows XP, the final stage action (stage 7 above) for some drive types changed from executing an application to invoking AutoPlay. From Windows Vista, the AutoPlay system is integrated into every aspect of media handling and there is no automatic execution of the AutoRun task.The default Registry settings add Removable drives to those that initiated AutoRun. In Windows XP and higher, except Windows Server 2003, only the Unknown and Remote drive types are not active for AutoRun.
The handling of the autorun.inf file changes very significantly between each Windows version. The details can be found in the autorun.inf article. The current handling in Windows 7 is that only drives of type DRIVE_CDROM may specify an AutoRun task, alter double-click behaviour or change context menus.
The AutoPlay safety net
It would appear that AutoPlay, by transferring control of what were previously automatic and invisible actions to AutoPlay, acts to increase user control and safety. This applies especially from Windows Vista, where all media and devices fall under AutoPlay control.However, it is important to note that:
- A user can instruct AutoPlay to make automatic choices on their behalf, including the execution of any AutoRun task.
- When a user double clicks on the drive icon in Explorer or right clicks to get a context menu, what happens next is fully programmable by the autorun.inf file and is essentially outside AutoPlay's purview. This is true under any Windows operating system.
- Disabling AutoRun may force a user to double click the drive icon to get a contents list, thus (potentially? possibly?) increasing the chance of malware infiltration.
Registry settings
AutoRun consults Windows RegistryWindows registry
The Windows Registry is a hierarchical database that stores configuration settings and options on Microsoft Windows operating systems. It contains settings for low-level operating system components as well as the applications running on the platform: the kernel, device drivers, services, SAM, user...
values to decide whether to initiate actions for any particular drive or drive type. These values can be changed using several methods, one of which is using Group Policy
Group Policy
Group Policy is a feature of the Microsoft Windows NT family of operating systems. Group Policy is a set of rules that control the working environment of user accounts and computer accounts. Group Policy provides the centralized management and configuration of operating systems, applications, and...
.
The primary relevant Registry entry names are NoDriveTypeAutoRun and NoDriveAutoRun. These exist in both per-machine and per-user settings and their location and priority in the Registry are described in further detail below.
Drive types
The drive types are distinguished by Type Name as follows:| Type name | Description |
|---|---|
| DRIVE_UNKNOWN | The drive type cannot be determined |
| DRIVE_REMOVABLE | The drive has removable media (floppy drive, USB flash drive USB flash drive A flash drive is a data storage device that consists of flash memory with an integrated Universal Serial Bus interface. flash drives are typically removable and rewritable, and physically much smaller than a floppy disk. Most weigh less than 30 g... ) |
| DRIVE_FIXED | The disk cannot be removed from the drive (hard disk) |
| DRIVE_REMOTE | The drive is a remote (network) drive |
| DRIVE_CDROM | The drive is a CD-ROM or DVD-ROM drive |
| DRIVE_RAMDISK | The drive is a RAM disk RAM disk A RAM disk or RAM drive is a block of RAM that a computer's software is treating as if the memory were a disk drive... |
Registry terminology
The Windows Registry is a hierarchical database that stores configuration settings and options for the operating system. The terminology is somewhat misleading so it is briefly summarised here.A Registry key is similar to a folder that, in addition to values, each key can contain subkeys which in turn may contain subkeys, and so on.
A Registry value consists of a name-data pair. Microsoft documentation commonly uses the term "entry" as an equivalent term. It also uses "value" for "data" when it is obvious what is meant. To avoid confusion, this article always uses the term "entry" when referring to the name-data pair.
Two Registry keys that are very commonly referred to are HKEY_LOCAL_MACHINE which contains per-machine settings, and HKEY_CURRENT_USER which contains settings for the currently logged-on user. These are almost always abbreviated as HKLM and HKCU respectively. There may be many users of a machine; their settings are stored in HKEY_USERS, HKCU is actually just a link to the appropriate place in HKEY_USERS.
Changing Registry settings
Registry settings may be changed directly by using the GUI regedit tool or the command line reg.exe utility. Settings can also be placed in a text file, named with a .reg extension type. For example, "mychanges.reg". When the file is double clicked, the settings in the file are entered into the Registry, permissions allowing.They can be changed indirectly by using Group Policy, applied locally to a single computer with GPEdit.msc or to a domain with gpmc.msc.
It may be necessary to either logout or restart the computer in order for any Registry changes to take effect.
Evaluation order
The NoDriveAutoRun and NoDriveTypeAutoRun Registry entries can exist in two places, the per-user setting (under HKEY_CURRENT_USER) and the per-machine setting (under HKEY_LOCAL_MACHINE). If an entry appears under HKEY_LOCAL_MACHINE, then any corresponding entry under HKEY_CURRENT_USER is completely ignored. The data values are not merged in any way.When deciding whether to activate AutoRun, both NoDriveAutoRun and NoDriveTypeAutoRun Registry entries are consulted. If either value indicates a drive should be disabled then AutoRun is disabled for that drive.
Thus in the following example:
| HKEY_LOCAL_MACHINE | | HKEY_CURRENT_USER | ||
|---|---|---|---|
| NoDriveAutoRun | NoDriveTypeAutoRun | NoDriveAutoRun | NoDriveTypeAutoRun |
| |
|
|
|
the data value taken for NoDriveAutoRun is 0x08, disabling drive D and the data value taken for NoDriveTypeAutoRun is 0x95, disabling removable and network drives. The per-user NoDriveAutoRun entry is never used.
NoDriveTypeAutoRun
| HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer |
|||
| Entry name | Data type | Range | Default |
|---|---|---|---|
| NoDriveTypeAutoRun | |
|
|
This Registry entry disables or enables the AutoRun feature on all drives of the type specified. It reflects the setting of the relevant Autoplay Group Policy. Valid data ranges from 0x00 to 0xFF in hexadecimal
Hexadecimal
In mathematics and computer science, hexadecimal is a positional numeral system with a radix, or base, of 16. It uses sixteen distinct symbols, most often the symbols 0–9 to represent values zero to nine, and A, B, C, D, E, F to represent values ten to fifteen...
notation. If the entry is not present, the default data value is either 0x95 or 0x91 depending on the version of Windows used. An entry present in HKLM overrides any entry present in HKCU.
The entry data is a bitmapped value, where a bit set to 1 disables AutoRun on a particular type of drive. The bit settings for each type of drive are shown below:
Note that bit number 1 is unused and that the "Unknown" type is represented twice. Setting all bits to 1 would give a hexadecimal value of 0xFF, decimal 255, and would disable AutoRun on all types of drives.
The default setting for this entry depends on the version of Windows being used:
| Operating system | Default setting |
|---|---|
| Windows 7 | |
| Windows Server 2008 | |
| Windows Vista | |
| Windows Server 2003 | |
| Windows XP | |
| Windows 2000 | |
| Windows 95/98 | |
NoDriveAutoRun
| HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer |
|||
| Entry name | Data type | Range | Default |
|---|---|---|---|
| NoDriveAutoRun | |
|
|
This Registry entry disables or enables the AutoRun feature on individual drives. It is not associated with a Group Policy and does not exist by default. The data value is taken to be 0 if the entry is not present. An entry present in HKLM overrides any entry present in HKCU.
The data is a 32 bit (DWORD) bitmapped value, of which the lower 26 bits are used to represent each of the 26 drive letters from A to Z. Thus the valid data range is from 0x0 to 0x03FFFFFF. The least significant bit (the right most bit) represents drive A, and the 26th bit from the right represents drive Z.
A bit set to 1 disables AutoRun on a particular drive. For example, if the data value is set to 0x8 (1000 binary), AutoRun is disabled on drive D.
Group Policy

When a policy is Enabled, Group Policy will add the NoDriveTypeAutoRun entry to the Registry. If the policy is Disabled or set to Not configured, Group Policy deletes this entry from the Registry. System defaults may then take effect as described in the NoDriveTypeAutoRun section.
The policy names, locations and possible settings vary slightly between Windows versions. The list of settings are relatively short and are always additional to the system default setting. Therefore, on Windows 2000, enabling the "Disable Autoplay" policy and setting it to "CD-ROM drives", disables AutoRun (as distinct from AutoPlay) for CD-ROM and DVD drives, removable drives, network drives, and drives of unknown type.
This setting cannot be used to enable AutoRun on drives on which it is disabled by default or disable AutoRun for drives not listed. To disable or enable any particular drives or drive types, the Registry must be edited manually.
Windows Server 2003, Windows XP, and Windows 2000
The per-machine policy location is:- Group Policy \ Computer Configuration \ Administrative Templates \ System
The per-user policy location is:
- Group Policy \ User Configuration \ Administrative Templates \ System
The relevant policy is "Turn off Autoplay". In Windows 2000 the policy is called "Disable Autoplay" instead.
Once the policy is Enabled it can be set to "All drives" or "CD-ROM drives". The latter setting adds CD-ROM drives to the existing list of disabled drive types as described above.
Windows Vista, Windows Server 2008
The per-machine policy location is:- Computer Configuration \ Administrative Templates \ Windows Components \ Autoplay Policies
The per-user policy location is:
- User Configuration \ Administrative Templates \ Windows Components \ AutoPlay Policies
The relevant policy is "Turn off Autoplay" and can be set for CD-ROM, DVD-ROM and removable drives or all drives.
Two related policies were added in Vista and Server 2008:
- Default behavior for AutoRun
-
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\ExplorerEntry name Data type Range Default NoAutoRun REG_DWORD
Sets the default behavior for AutoRun commands found in autorun.inf files.
Prior to Windows Vista, when media containing an autorun.inf specifying an AutoRun task was inserted, the default action was to automatically execute the program without user intervention. From Windows Vista the default behaviour is to invoke AutoPlay and represent the AutoRun task as one of the dialog options. This is also the behaviour when this policy is Not configured or Disabled.
If this policy is Enabled, the behaviour can be changed to either:- Completely disable autorun.inf commands or
- Automatically execute the autorun.inf command as per previous Windows versions.
- Don't set the always do this checkbox
-
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\ExplorerEntry name Data type Range Default DontSetAutoplayCheckbox REG_DWORD
If this policy is Enabled, the "Always do this..." checkbox in the AutoPlay dialog will not be set by default when the dialog is shown.
Windows 7, Windows Server 2008 R2
In these versions of Windows, the ability of an autorun.inf file to set an AutoRun task, alter double-click behaviour or change context menus is restricted to drives of type DRIVE_CDROM. There are no policy settings that will override this behaviour. Policy locations and settings are as per Windows Vista, Windows Server 2008 above with the addition of:- Turn off Autoplay for non-volume devices
-
HKLM\Software\Policies\Microsoft\Windows\Explorer
HKCU\Software\Policies\Microsoft\Windows\ExplorerEntry name Data type Range Default NoAutoplayfornonVolume
If this policy is enabled, AutoPlay will be disabled for non-volume devices.
Pressing the Shift key
If the key is held down at a certain point in the execution sequence Windows Vista invokes the AutoPlay dialog regardless of any AutoPlay settings to the contrary. Previous versions of Windows do not execute the AutoRun task.Given that Shift must be held down until Windows checks for it, it may be a considerable amount of time before it becomes effective. The time taken primarily depends on the time to recognise the new hardware and the time taken for CD-ROMs to spin up. It is unsafe to rely on this method.
Auto Insert Notification
Certain Media Change Notification events may be suppressed by altering certain Registry entries. "Media Change Notification" is the generic term; for CD-ROM drives, the specific term is "Auto Insert Notification".| HKLM\SYSTEM\CurrentControlSet\Services\Cdrom | |||
| Entry name | Data type | Range | Default |
|---|---|---|---|
| AutoRun | |
|
|
For CD-ROM drives, changing the value of this Registry entry to 0 will disable Auto Insert Notification for CD-ROM drives only. A Windows restart will be necessary.
| Data value | Meaning |
|---|---|
| |
Does not send an MCN message |
| |
Sends an MCN message |
Under Windows 95/98/ME, this setting can be changed under Device Manager, accessible from the System icon in Control Panel.

Thus, as a side effect only, this disables AutoRun for CD-ROM drives. However, Explorer will now not update its view when a new CD is inserted; it will show the contents of the previous CD until is pressed or View/Refresh is selected from the Explorer menu. This could result in severe confusion for users.
For this reason the Media Change Notification message should not be disabled unless there is absolutely no alternative; AutoRun can be disabled for individual drives using Group Policy or the Registry.
| HKLM\SYSTEM\CurrentControlSet\Services\Cdrom | |
| Entry name | Data type |
|---|---|
| AutoRunAlwaysDisable | REG_MULTI_SZ |
This entry is used to suppress the MCN message for specifically listed type of CD-ROM drive, primarily CD-ROM changers. The data is a set of device identifiers, which matches those identifiers reported to the system by the devices themselves.
The default value for this entry consists of products identified by Microsoft testing as being unable to support AutoRun. This entry should not be altered from its default.
Editing Group Policy
AutoRun may be suppressed on particular drives and drive types by using the methods described in the Group Policy section. However, the Group Policy Editor is not available on Home versions of Windows XP and does not provide any fine-grained drive selection facilities.However, Group Policy would be the accepted method of disabling AutoRun on an entire Windows domain.
Registry files
A Registry setting file can be created that, when executed, makes the desired changes in the Registry.Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\Explorer] "NoDriveTypeAutoRun"=dword:000000ff
|
In the above example, AutoRun would be disabled for all drives and for all users. This example would need to be run as Administrator and a reboot would be needed for the setting to take complete effect.
Initialization file mapping
Windows Vista and later versions of Windows have a policy setting, "Default behavior for AutoRun", that can be set to disallow the reading of an autorun.inf file on any volume. This avoids certain scenarios where malwareMalware
Malware, short for malicious software, consists of programming that is designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, or gain unauthorized access to system resources, or that otherwise exhibits abusive behavior...
leverages autorun.inf functionality to infect a machine. Previous versions of Windows do not have this policy setting but the use of initialisation file mapping is an effective workaround.
As an autorun.inf file is a standard Windows INI file, the appropriate API calls are used by Windows when fetching its settings. These API calls can be redirected using the INI file mapping method. The following Registry file illustrates the workaround, where all autorun.inf settings are taken solely from the HKEY_LOCAL_MACHINE\Software\DoesNotExist Registry key:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf] @="@SYS:DoesNotExist" |
As this key does not exist, it is as if the autorun.inf file contains no settings information. It is important to note that this applies to any autorun.inf in any location and on any drive.
Both the policy setting and this workaround have the drawback is that installation of software from an autorunning install CD or DVD is no longer automatic. It will be necessary to view the CD's autorun.inf file and then execute the appropriate install program manually.
The AutoRun disable bug
From Windows 2000 through to Windows 2008 Server, AutoRun-relevant Registry entries were not handled properly leading to a security vulnerability. Windows 95 and Windows 98 were not affected.When AutoRun is disabled, Windows should not proceed further through the activation sequence than the Registry check. However, it parses any autorun.inf found and does everything except the final action to invoke AutoPlay or execute an application.
This leaves the user open to attack from malware which uses the autorun.inf to alter the double-click and contextual menu behaviours. Double clicking the drive icon will infect the machine. Right Clicking and selecting the "Explore" or "Open" options from the context menu is not a workaround as these menu items can be coopted by the appropriate autorun.inf entries.
This bug was fixed in a number of security updates, detailed in Microsoft Knowledge Base
Microsoft Knowledge Base
Microsoft Knowledge Base is a repository of over 150,000 articles made available to the public by Microsoft Corporation. It contains information on many problems encountered by users of Microsoft products...
article 967715.
Other issues
- If you add the computer to an Active Directory domain, the NoDriveTypeAutoRun value may be reset to a default value. This is due to Group Policy settings in the domain taking effect. This is not a bug.
- Some programs may deliberately change AutoRun Registry settings. Early versions of CD burning software like Roxio have been known to change settings in this way.
- If the Group Policy "Restrict CD-ROM access to locally logged-on user only" security option under:
- Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
is turned on (Enabled), then AutoRun may not function.
Windows Installers will also malfunction because "Local System" access to the CD-ROM will be denied.
This Group Policy setting reflects the value of the Registry entry:
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon Entry name Data type Range Default allocatecdroms REG_SZ 0 or 1 0
and should be set to 0.
- Real Player 10 interferes with AutoPlay functionality to the extent that it may look as if AutoRun or AutoPlay is not working at all.
Attack vectors
AutoRun functionality has been used as a malware vector for some time. Prior to Windows Vista, the default action with a CD-ROM drive type was to follow any autorun.inf file instructions without prompts or warnings. This makes rogue CD-ROMs one possible infection vector.In the same category are mixed content CD-ROMs. An audio CD, that a user would not expect to contain software at all, can contain a data section with an autorun.inf. Some companies, such as Sony BMG
2005 Sony BMG CD copy protection scandal
The Sony BMG CD copy protection rootkit scandal concerns the copy protection measures included by Sony BMG on Compact Discs in 2005. Sony BMG included the Extended Copy Protection and MediaMax CD-3 software on music CDs. XCP was put on 52 titles and MediaMax was put on 50 titles...
, have used this vector to install malware that attempts to protect against copying of the audio tracks.
U3
U3
U3 was a joint venture between SanDisk and M-Systems , producing a proprietary method of launching Windows applications from special USB flash drives. Flash drives adhering to the U3 specification are termed "U3 smart drives"....
enabled flash drives, by emulating
Emulator
In computing, an emulator is hardware or software or both that duplicates the functions of a first computer system in a different second computer system, so that the behavior of the second system closely resembles the behavior of the first system...
a CD-ROM unit, can also cause Windows to execute commands from the autorun.inf found on the emulated CD-ROM.
Devices like the Huawei E220
Huawei E220
The Huawei E220 is a Huawei HSDPA access device manufactured by Huawei and notable for using the USB interface .Technically it is a modem, USB and virtual CD-ROM device....
HSDPA modem, validly use this method to autoinstall drivers for the modem itself. However plugging in a flash drive from an unknown source is an unwise move. USB Switchblade, and other similar tools, have made U3 flash drive attacks trivial. Given the ease of writing script
Scripting language
A scripting language, script language, or extension language is a programming language that allows control of one or more applications. "Scripts" are distinct from the core code of the application, as they are usually written in a different language and are often created or at least modified by the...
based attacks, anti-virus software may be ineffective in preventing data and password stealing.

Any user can configure AutoPlay to make various decisions for them; by checking the appropriate box in the AutoPlay dialog, running flash drive malware becomes silent and automatic.
AutoRun malware has been extended to use hard drives, picture frames and other digital devices. Care in dealing with external devices is a security priority.
Attack mitigation
In addition to basic security precautions, which include- following the principle of least privilegePrinciple of least privilegeIn information security, computer science, and other fields, the principle of least privilege, also known as the principle of minimal privilege or just least privilege, requires that in a particular abstraction layer of a computing environment, every module must be able to access only the...
by not habitually running with AdministratorSuperuserOn many computer operating systems, the superuser is a special user account used for system administration. Depending on the operating system, the actual name of this account might be: root, administrator or supervisor....
privileges and - applying all relevant security patches and updates,
exposure to these attacks can be minimised through the appropriate use of Group Policy and Registry settings. The following security policies are a summary of those described within this article:
- Disable AutoRun (but see the AutoRun disable bug)
- Use the "Default behavior for AutoRun" Group Policy under Vista (see above) to disable autorun.inf commands
- Use initialization file mapping to nullify autorun.inf sections
- Under Windows 7, only CD and DVD drives may specify applications like the AutoRun task in the autorun.inf file. Windows XP and later can be patchPatch (computing)A patch is a piece of software designed to fix problems with, or update a computer program or its supporting data. This includes fixing security vulnerabilities and other bugs, and improving the usability or performance...
ed to behave in the same way with update KB971029. In February 2011, this patch was added to the official Windows UpdateWindows UpdateWindows Update is a service provided by Microsoft that provides updates for the Microsoft Windows operating system and its installed components, including Internet Explorer...
channel. The Windows 7 AutoRun task behaviour now becomes the default for all current versions of the Windows OS.
In addition, the following actions have been recommended by Microsoft, primarily during the Conficker
Conficker
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008...
worm attacks:
- Prevent autorun.inf invocation from network shares by:
- Deleting any existing autorun.inf file from the root of a mapped network drive
- Denying Create rights to the root of a mapped network drive
- Prevent the use of USB storage devices by means of:
- USB settings within the System BIOSBIOSIn IBM PC compatible computers, the basic input/output system , also known as the System BIOS or ROM BIOS , is a de facto standard defining a firmware interface....
- Appropriate Registry settings as described in Knowledge Base article 823732
- Setting USB devices to read only to prevent propagation of unknown worms (and theft of proprietary data)
- USB settings within the System BIOS
External links
- AutoRun and AutoPlay Reference, Microsoft, MSDN Library
- Memory stick worms, Nick Brown's blog
- Dan McCloy's Autorun Reference Guide
- Security Watch Island Hopping: The Infectious Allure of Vendor Swag, TechNet Magazine
- Figure 4: querycancelautoplay example code, Microsoft Systems Journal, September 1998
- AutoPlay Repair Wizard, Microsoft Download Center
- Test your defenses against malicious USB flash drives, Computerworld blog, January 24, 2009
- The best way to disable Autorun for protection from infected USB flash drives, Computerworld blog, January 30, 2009
- How To Remove AutoRun Virus
- Microsoft PowerToys, Microsoft, Tweak UI
- Online Information Resource on the autorun/autostart feature of Microsoft Windows
- AutoRunConf simple configuration tool for Autorun settings.
- Disable Autorun turn on/off the autorun/autoplay feature of Windows
- Create an AutoRun Menu Create your own AutoRun Menu
- Autorun Virus Remover - Learn how to clean the Autorun.inf virus