.gif)
Demilitarized zone (computing)
Encyclopedia
In computer security
, a DMZ (sometimes referred to as a perimeter network) is a physical or logical subnetwork
that contains and exposes an organization's external services to a larger untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network
(LAN); an external attacker only has access to equipment in the DMZ, rather than any other part of the network. The name is derived from the term "demilitarized zone
", an area between nation states in which military action is not permitted.
, the host
s most vulnerable to attack are those that provide services to users outside of the local area network
, such as e-mail
, web
and Domain Name System
(DNS) servers. Because of the increased potential of these hosts being compromised, they are placed into their own sub-network in order to protect the rest of the network if an intruder were to succeed in attacking all of them.
Hosts in the DMZ have limited connectivity to specific hosts in the internal network, although communication with other hosts in the DMZ and to the external network is allowed. This allows hosts in the DMZ to provide services to both the internal and external network, while an intervening firewall controls the traffic between the DMZ servers and the internal network clients.
A DMZ configuration typically provides security from external attacks, but it typically has no bearing on internal attacks such as sniffing communication via a packet analyzer or spoofing
such as e-mail spoofing
.
Web servers that communicate with an internal database require access to a database server
, which may not be publicly accessible and may contain sensitive information. The web servers can communicate with database servers either directly or through an application firewall for security reasons.
E-mail
messages and particularly the user database are confidential information, so they are typically stored on servers that cannot be accessed from the Internet (at least not in an insecure manner), but can be accessed from the SMTP servers that are exposed to the Internet.
The mail server inside the DMZ passes incoming mail to the secured/internal mail servers. It also handles outgoing mail.
For security, legal compliance and monitoring reasons, in a business environment, some enterprises install a proxy server
within the DMZ. This has the following consequences:
A reverse proxy
server, like a proxy server, is an intermediary, but is used the other way around. Instead of providing a service to internal users wanting to access an external network, it provides indirect access for an external network (usually the Internet) to internal resources.
For example, a back office application access, such as an email system, could be provided to external users (to read emails while outside the company) but the remote user would not have direct access to his email server. Only the reverse proxy server can physically access the internal email server. This is an extra layer of security, which is particularly recommended when internal resources need to be accessed from the outside. Usually such a reverse proxy mechanism is provided by using an application layer firewall
as they focus on the specific shape of the traffic rather than controlling access to specific TCP and UDP port
s as a packet filter firewall does.
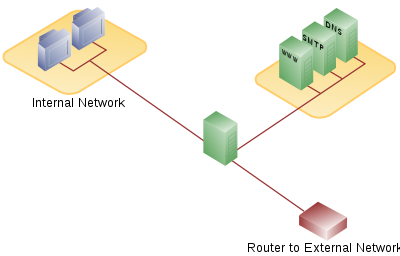
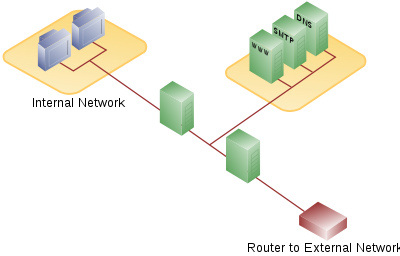 There are many different ways to design a network with a DMZ. Two of the most basic methods are with a single firewall, also known as the three legged model, and with dual firewalls. These architectures can be expanded to create very complex architectures depending on the network requirements.
There are many different ways to design a network with a DMZ. Two of the most basic methods are with a single firewall, also known as the three legged model, and with dual firewalls. These architectures can be expanded to create very complex architectures depending on the network requirements.
The zones are usually marked with colors -for example, purple for LAN, green for DMZ, red for Internet (with often another color used for wireless zones).
This setup is considered more secure, specially if the two firewalls are provided by two different vendors, because it makes it less likely that both devices suffer from the same security vulnerabilities, if any are found (whether from accidental misconfiguration less likely to occur the same way across the configuration interfaces of two different vendors, or from a security hole found to exist in one vendor's system but not the other). This architecture is, of course, more costly. The practice of using different firewalls from different vendors is sometimes described as a component of a "defense in depth
" security strategy.
By definition this is not a true DMZ (Demilitarized Zone), since it alone does not separate the host from the internal network. That is, the DMZ host is able to connect to hosts on the internal network, whereas hosts within a real DMZ are prevented from connecting with the internal network by a firewall that separates them, unless the firewall permits the connection. A firewall may allow this if a host on the internal network first requests a connection to the host within the DMZ.
The DMZ host provides none of the security advantages that a subnet
provides and is often used as an easy method of forwarding all ports to another firewall / NAT
device.
Computer security
Computer security is a branch of computer technology known as information security as applied to computers and networks. The objective of computer security includes protection of information and property from theft, corruption, or natural disaster, while allowing the information and property to...
, a DMZ (sometimes referred to as a perimeter network) is a physical or logical subnetwork
Subnetwork
A subnetwork, or subnet, is a logically visible subdivision of an IP network. The practice of dividing a network into subnetworks is called subnetting....
that contains and exposes an organization's external services to a larger untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network
Local area network
A local area network is a computer network that interconnects computers in a limited area such as a home, school, computer laboratory, or office building...
(LAN); an external attacker only has access to equipment in the DMZ, rather than any other part of the network. The name is derived from the term "demilitarized zone
Demilitarized zone
In military terms, a demilitarized zone is an area, usually the frontier or boundary between two or more military powers , where military activity is not permitted, usually by peace treaty, armistice, or other bilateral or multilateral agreement...
", an area between nation states in which military action is not permitted.
Rationale
In a computer networkComputer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
, the host
Host (network)
A network host is a computer connected to a computer network. A network host may offer information resources, services, and applications to users or other nodes on the network. A network host is a network node that is assigned a network layer host address....
s most vulnerable to attack are those that provide services to users outside of the local area network
Local area network
A local area network is a computer network that interconnects computers in a limited area such as a home, school, computer laboratory, or office building...
, such as e-mail
E-mail
Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
, web
World Wide Web
The World Wide Web is a system of interlinked hypertext documents accessed via the Internet...
and Domain Name System
Domain name system
The Domain Name System is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities...
(DNS) servers. Because of the increased potential of these hosts being compromised, they are placed into their own sub-network in order to protect the rest of the network if an intruder were to succeed in attacking all of them.
Hosts in the DMZ have limited connectivity to specific hosts in the internal network, although communication with other hosts in the DMZ and to the external network is allowed. This allows hosts in the DMZ to provide services to both the internal and external network, while an intervening firewall controls the traffic between the DMZ servers and the internal network clients.
A DMZ configuration typically provides security from external attacks, but it typically has no bearing on internal attacks such as sniffing communication via a packet analyzer or spoofing
Spoofing attack
In the context of network security, a spoofing attack is a situation in which one person or program successfully masquerades as another by falsifying data and thereby gaining an illegitimate advantage.- Spoofing and TCP/IP :...
such as e-mail spoofing
E-mail spoofing
Email spoofing is email activity in which the sender address and other parts of the email header are altered to appear as though the email originated from a different source. Because core SMTP doesn't provide any authentication, it is easy to impersonate and forge emails...
.
Services in the DMZ
Any service that is being provided to users on the external network can be placed in the DMZ. The most common of these services are:- web serverWeb serverWeb server can refer to either the hardware or the software that helps to deliver content that can be accessed through the Internet....
s - mail servers
- FTP servers
- VoIP servers
Web servers that communicate with an internal database require access to a database server
Database server
A database server is a computer program that provides database services to other computer programs or computers, as defined by the client–server model. The term may also refer to a computer dedicated to running such a program...
, which may not be publicly accessible and may contain sensitive information. The web servers can communicate with database servers either directly or through an application firewall for security reasons.
E-mail
Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
messages and particularly the user database are confidential information, so they are typically stored on servers that cannot be accessed from the Internet (at least not in an insecure manner), but can be accessed from the SMTP servers that are exposed to the Internet.
The mail server inside the DMZ passes incoming mail to the secured/internal mail servers. It also handles outgoing mail.
For security, legal compliance and monitoring reasons, in a business environment, some enterprises install a proxy server
Proxy server
In computer networks, a proxy server is a server that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource available from a different server...
within the DMZ. This has the following consequences:
- Obliges the internal users (usually employees) to use the proxy to get Internet access.
- Allows the company to reduce Internet access bandwidth requirements because some of the web content may be cached by the proxy server.
- Simplifies the recording and monitoring of user activities and block content violating acceptable use policies.
A reverse proxy
Reverse proxy
In computer networks, a reverse proxy is a type of proxy server that retrieves resources on behalf of a client from one or more servers. These resources are then returned to the client as though it originated from the reverse proxy itself...
server, like a proxy server, is an intermediary, but is used the other way around. Instead of providing a service to internal users wanting to access an external network, it provides indirect access for an external network (usually the Internet) to internal resources.
For example, a back office application access, such as an email system, could be provided to external users (to read emails while outside the company) but the remote user would not have direct access to his email server. Only the reverse proxy server can physically access the internal email server. This is an extra layer of security, which is particularly recommended when internal resources need to be accessed from the outside. Usually such a reverse proxy mechanism is provided by using an application layer firewall
Application layer firewall
An application firewall is a form of firewall which controls input, output, and/or access from, to, or by an application or service. It operates by monitoring and potentially blocking the input, output, or system service calls which do not meet the configured policy of the firewall...
as they focus on the specific shape of the traffic rather than controlling access to specific TCP and UDP port
TCP and UDP port
In computer networking, a port is an application-specific or process-specific software construct serving as a communications endpoint in a computer's host operating system. A port is associated with an IP address of the host, as well as the type of protocol used for communication...
s as a packet filter firewall does.
Architecture


Single firewall
A single firewall with at least 3 network interfaces can be used to create a network architecture containing a DMZ. The external network is formed from the ISP to the firewall on the first network interface, the internal network is formed from the second network interface, and the DMZ is formed from the third network interface. The firewall becomes a single point of failure for the network and must be able to handle all of the traffic going to the DMZ as well as the internal network.The zones are usually marked with colors -for example, purple for LAN, green for DMZ, red for Internet (with often another color used for wireless zones).
Dual firewall
A more secure approach is to use two firewalls to create a DMZ. The first firewall (also called the "front-end" firewall) must be configured to allow traffic destined to the DMZ only. The second firewall (also called "back-end" firewall) allows only traffic from the DMZ to the internal network.This setup is considered more secure, specially if the two firewalls are provided by two different vendors, because it makes it less likely that both devices suffer from the same security vulnerabilities, if any are found (whether from accidental misconfiguration less likely to occur the same way across the configuration interfaces of two different vendors, or from a security hole found to exist in one vendor's system but not the other). This architecture is, of course, more costly. The practice of using different firewalls from different vendors is sometimes described as a component of a "defense in depth
Defense in Depth (computing)
Defense in depth is an information assurance concept in which multiple layers of security controls are placed throughout an information technology system...
" security strategy.
DMZ host
Some home routers refer to a DMZ host. A home router DMZ host is a host on the internal network that has all ports exposed, except those ports otherwise forwarded.By definition this is not a true DMZ (Demilitarized Zone), since it alone does not separate the host from the internal network. That is, the DMZ host is able to connect to hosts on the internal network, whereas hosts within a real DMZ are prevented from connecting with the internal network by a firewall that separates them, unless the firewall permits the connection. A firewall may allow this if a host on the internal network first requests a connection to the host within the DMZ.
The DMZ host provides none of the security advantages that a subnet
Subnetwork
A subnetwork, or subnet, is a logically visible subdivision of an IP network. The practice of dividing a network into subnetworks is called subnetting....
provides and is often used as an easy method of forwarding all ports to another firewall / NAT
Network address translation
In computer networking, network address translation is the process of modifying IP address information in IP packet headers while in transit across a traffic routing device....
device.

