Device Keys
Encyclopedia
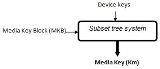
Device Keys play a role in the cryptographic key management procedure in the Advanced Access Content System
(AACS) specification. This specification defines a method for protecting audiovisual entertainment content, including high-definition content.
(MKB), in order to extract a secret Media Key (Km).
A MKB is located on the physical support (the disc) together with the content of the disc encrypted.
MKB enables system renewability. The MKB is generated by AACS LA
, and allows all compliant devices, each using their set of secret Device Keys, to calculate the same Media Key (Km).
If a set of Device Keys is compromised in a way that threatens the integrity of the system, an updated MKB can be released that causes a device with the compromised set of Device Keys to be unable to calculate the correct Km. In this way, the compromised Device Keys are “revoked” by the new MKB.
be different in different media types. These Device Keys, referred to as Kdi (i=0,1,…,n-1), are provided by AACS LA. The set of Device Keys may either be unique per device, or used commonly by multiple devices.
A device shall treat its Device Keys as highly confidential.
The MKB is encrypted in a subset difference tree approach. In order to decrypt it, a device must know the right Processing Key (P) which is available via the subset-difference tree process.
Essentially, the set of Device Keys are arranged in a tree such that any given Device Key can be used to find lower level Processing keys. The processing keys at higher position in the tree than the given set of Device Keys are not reachable.
A given set of Device Keys give access to a given set of Processing keys, it is to say to a given set of decodable MKB.
This way, to revoke a given device key, the MKB needs only be encrypted with a Processing Key which is not reachable by its Device Keys set.
For each Device Key, there is an associated number denoted the path number, the “u” bit mask , and the “v” bit mask.
The path number denotes the position in the tree associated with the Device Key. This path number defines a path from the root to that node in the tree.
The “u” and “v” masks are used in the subset difference tree process. They are always a single sequence of 1-bits followed by a single sequence of 0-bits. The bit masks indicate “don’t care” bits in the path number; if a bit is 0 in the mask, the corresponding bit in the path number is “don’t care”.
The deeper the position of a node in the tree, the shorter the sequence of 0-bits in the mask associated to that node.
The device number, path number, and masks denote nodes within a binary tree.
Advanced Access Content System
The Advanced Access Content System is a standard for content distribution and digital rights management, intended to restrict access to and copying of the "next generation" of optical discs and DVDs. The specification was publicly released in April 2005 and the standard has been adopted as the...
(AACS) specification. This specification defines a method for protecting audiovisual entertainment content, including high-definition content.
Introduction
The AACS’s cryptographic key management procedure uses Device Keys to decrypt one or more elements of a Media Key BlockMedia Key Block
The Media Key Block is one of the keys that are included inside the copying protection system AACS. This system is used to protect Blu-ray and HD DVD formats from being copied...
(MKB), in order to extract a secret Media Key (Km).
A MKB is located on the physical support (the disc) together with the content of the disc encrypted.
MKB enables system renewability. The MKB is generated by AACS LA
AACS LA
AACS LA is the body that develops and licenses the AACS copy-protection system used on the HD DVD and Blu-ray Disc high-definition optical disc formats....
, and allows all compliant devices, each using their set of secret Device Keys, to calculate the same Media Key (Km).
If a set of Device Keys is compromised in a way that threatens the integrity of the system, an updated MKB can be released that causes a device with the compromised set of Device Keys to be unable to calculate the correct Km. In this way, the compromised Device Keys are “revoked” by the new MKB.
| Key or Variable | Size |
|---|---|
| Device Keys (Kd0,Kd1,…,Kdn-1) | 128 bits each |
| Media Key Block (MKB) | Variable, multiple of 4 bytes |
| Media Key (Km) | 128 bits |
How it works
Each compliant device is given a set of secret Device Keys when manufactured. The actual number of keys maybe different in different media types. These Device Keys, referred to as Kdi (i=0,1,…,n-1), are provided by AACS LA. The set of Device Keys may either be unique per device, or used commonly by multiple devices.
A device shall treat its Device Keys as highly confidential.
The MKB is encrypted in a subset difference tree approach. In order to decrypt it, a device must know the right Processing Key (P) which is available via the subset-difference tree process.
Essentially, the set of Device Keys are arranged in a tree such that any given Device Key can be used to find lower level Processing keys. The processing keys at higher position in the tree than the given set of Device Keys are not reachable.
A given set of Device Keys give access to a given set of Processing keys, it is to say to a given set of decodable MKB.
This way, to revoke a given device key, the MKB needs only be encrypted with a Processing Key which is not reachable by its Device Keys set.
Storing
Each device is given its Device Keys and a 31-bit number d called the device number.For each Device Key, there is an associated number denoted the path number, the “u” bit mask , and the “v” bit mask.
The path number denotes the position in the tree associated with the Device Key. This path number defines a path from the root to that node in the tree.
The “u” and “v” masks are used in the subset difference tree process. They are always a single sequence of 1-bits followed by a single sequence of 0-bits. The bit masks indicate “don’t care” bits in the path number; if a bit is 0 in the mask, the corresponding bit in the path number is “don’t care”.
The deeper the position of a node in the tree, the shorter the sequence of 0-bits in the mask associated to that node.
The device number, path number, and masks denote nodes within a binary tree.
Sources
See also
- History of attacks against Advanced Access Content System
- AACS encryption key controversyAACS encryption key controversyA controversy surrounding the AACS cryptographic key arose in April 2007 when the Motion Picture Association of America and the Advanced Access Content System Licensing Administrator, LLC began issuing demand letters to websites publishing a 128-bit number, represented in hexadecimal as 09 F9 11...

