IT Baseline Protection Catalogs
Encyclopedia
The IT Baseline Protection Catalogs, or IT-Grundschutz-Kataloge, ("IT Baseline Protection Manual" before 2005) are a collection of documents from the German
Federal Office for Security in Information Technology (BSI) that provide useful information for detecting weaknesses and combating attacks in the information technology
(IT) environment (IT cluster). The collection encompasses over 3000 pages, including the introduction and catalogs. It serves as the basis for the IT baseline protection
certification
of an enterprise
.
The detection and assessment of weak points in IT systems often occurs by way of a risk assessment
, wherein a threat potential is assessed, and the costs of damage to the system (or group of similar systems) are investigated individually. This approach is very time-intensive and very expensive.
Protection may rather proceed from a typical threat, which applies to 80% of cases, and recommend adequate countermeasures against it. In this way, a security level can be achieved, viewed as adequate in most cases, and, consequently, replace the more expensive risk assessment. In cases in which security needs are greater, such protection can be used as a basis for further action.
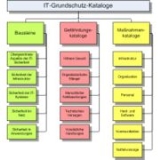
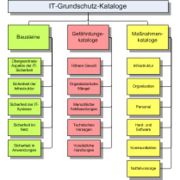 To familiarize the user with the manual itself, it contains an introduction with explanations, the approach to IT baseline protection, a series of concept and role definitions, and a glossary. The component catalogs, threat catalogs, and the measures catalogs follow these introductory sections. Forms and cross-reference tables supplement the collection available on the Federal Office for Security in Information Technology's (BSI) Internet platform. Here you can also find the Baseline Protection Guide, containing support functions for implementing IT baseline protection in procedural detail.
To familiarize the user with the manual itself, it contains an introduction with explanations, the approach to IT baseline protection, a series of concept and role definitions, and a glossary. The component catalogs, threat catalogs, and the measures catalogs follow these introductory sections. Forms and cross-reference tables supplement the collection available on the Federal Office for Security in Information Technology's (BSI) Internet platform. Here you can also find the Baseline Protection Guide, containing support functions for implementing IT baseline protection in procedural detail.
Each catalog element is identified by an individual mnemonic laid out according to the following scheme (the catalog groups are named first). C stands for component, M for measure, and T for threat. This is followed by the layer number affected by the element. Finally, a serial number within the layer identifies the element.
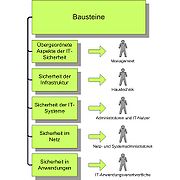 The component catalog is the central element, and contains the following five layers: overall aspects, infrastructure, IT systems, networks and IT applications.
The component catalog is the central element, and contains the following five layers: overall aspects, infrastructure, IT systems, networks and IT applications.
Partitioning into layers clearly isolates personnel groups impacted by a given layer from the layer in question. The first layer is addressed to management
, including personnel and outsourcing
. The second is addressed to in-house technicians, regarding structural aspects in the infrastructure layer. System administrators cover the third layer, looking at the characteristics of IT systems, including client
s, server
s and private branch exchanges or fax
machines. The fourth layer falls within the network administrators task area. The fifth within that of the applications administrator and the IT user, concerning software like database management system
s, e-mail
and web servers.
 Each individual component follows the same layout. The component number is composed of the layer number in which the component is located and a unique number within the layer. The given threat situation is depicted after a short description of the component examining the facts. An itemization of individual threat sources ultimately follows. These present supplementary information. It is not necessary to work through them to establish baseline protection.
Each individual component follows the same layout. The component number is composed of the layer number in which the component is located and a unique number within the layer. The given threat situation is depicted after a short description of the component examining the facts. An itemization of individual threat sources ultimately follows. These present supplementary information. It is not necessary to work through them to establish baseline protection.
The necessary measures are presented in a text with short illustrations. The text follows the facts of the life cycle in question and includes planning and design, acquisition (if necessary), realization, operation, selection (if necessary), and preventive measures. After a complete depiction, individual measures are once again collected into a list, which is arranged according to the measures catalog's structure, rather than that of the life cycle. In the process, classification of measures into the categories A, B, C, and Z is undertaken. Category A measures for the entry point into the subject, B measures expand this, and category C is ultimately necessary for baseline protection certification. Category Z measures any additional measures that have proven themselves in practice.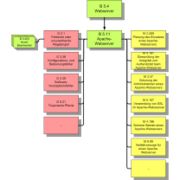 To keep each component as compact as possible, global aspects are collected in one component, while more specific information is collected into a second. In the example of an Apache web server, the general B 5.4 Web server component, in which measures and threats for each web server are depicted, would apply to it, as well as the B5.11 component, which deals specifically with the Apache web server. Both components must be successfully implemented to guarantee the system's security.
To keep each component as compact as possible, global aspects are collected in one component, while more specific information is collected into a second. In the example of an Apache web server, the general B 5.4 Web server component, in which measures and threats for each web server are depicted, would apply to it, as well as the B5.11 component, which deals specifically with the Apache web server. Both components must be successfully implemented to guarantee the system's security.
The respective measures or threats, which are introduced in the component, can also be relevant for other components. In this way, a network of individual components arises in the baseline protection catalogs.
Managers are initially named to initiate and realize the measures in the respective measures description. A detailed description of the measures follows. Finally, control questions regarding correct realization are given. During realization of measures, personnel should verify whether adaptation to the operation in question is necessary; any deviations from the initial measures should be documented for future reference.
.
The forms provided serve to remedy protection needs for certain IT system components. A table summarizes the measures to be applied for individual components in this regard. Each measure is named and its degree of realization determined. Degrees of realization, "considerable", "yes", "partial", and "no", are distinguished. Finally, the realization is terminated and a manager is named. If the measures' realization is not possible, reasons for this are entered in the adjacent field for later traceability. The conclusion consists of a cost assessment.
Besides the forms, the cross-reference tables another useful supplement. They summarize the measures and most important threats for individual components. Measures, as well as threats, are cited with mnemonic
s. Measures are cited with a priority and a classification. The table contains correlations between measures and the threats they address. However, the cross-reference tables only cite the most important threats. If the measure cited for a given threat is not applicable for the individual IT system, it is not superfluous. Baseline protection can only be ensured if all measures are realized.
Germany
Germany , officially the Federal Republic of Germany , is a federal parliamentary republic in Europe. The country consists of 16 states while the capital and largest city is Berlin. Germany covers an area of 357,021 km2 and has a largely temperate seasonal climate...
Federal Office for Security in Information Technology (BSI) that provide useful information for detecting weaknesses and combating attacks in the information technology
Information technology
Information technology is the acquisition, processing, storage and dissemination of vocal, pictorial, textual and numerical information by a microelectronics-based combination of computing and telecommunications...
(IT) environment (IT cluster). The collection encompasses over 3000 pages, including the introduction and catalogs. It serves as the basis for the IT baseline protection
IT baseline protection
- Overview :The term baseline security is used in various contexts with somewhat different meanings. For example:* Microsoft Baseline Security Analyzer: Software tool focused on Microsoft operating system and services security...
certification
Certification
Certification refers to the confirmation of certain characteristics of an object, person, or organization. This confirmation is often, but not always, provided by some form of external review, education, assessment, or audit...
of an enterprise
Business
A business is an organization engaged in the trade of goods, services, or both to consumers. Businesses are predominant in capitalist economies, where most of them are privately owned and administered to earn profit to increase the wealth of their owners. Businesses may also be not-for-profit...
.
Basic protection
IT baseline protection (protection) encompasses standard security measures for typical IT systems, with normal protection needs.The detection and assessment of weak points in IT systems often occurs by way of a risk assessment
Risk assessment
Risk assessment is a step in a risk management procedure. Risk assessment is the determination of quantitative or qualitative value of risk related to a concrete situation and a recognized threat...
, wherein a threat potential is assessed, and the costs of damage to the system (or group of similar systems) are investigated individually. This approach is very time-intensive and very expensive.
Protection may rather proceed from a typical threat, which applies to 80% of cases, and recommend adequate countermeasures against it. In this way, a security level can be achieved, viewed as adequate in most cases, and, consequently, replace the more expensive risk assessment. In cases in which security needs are greater, such protection can be used as a basis for further action.
The IT Baseline Protection Catalogs layout

Each catalog element is identified by an individual mnemonic laid out according to the following scheme (the catalog groups are named first). C stands for component, M for measure, and T for threat. This is followed by the layer number affected by the element. Finally, a serial number within the layer identifies the element.
Component catalog

Partitioning into layers clearly isolates personnel groups impacted by a given layer from the layer in question. The first layer is addressed to management
Management
Management in all business and organizational activities is the act of getting people together to accomplish desired goals and objectives using available resources efficiently and effectively...
, including personnel and outsourcing
Outsourcing
Outsourcing is the process of contracting a business function to someone else.-Overview:The term outsourcing is used inconsistently but usually involves the contracting out of a business function - commonly one previously performed in-house - to an external provider...
. The second is addressed to in-house technicians, regarding structural aspects in the infrastructure layer. System administrators cover the third layer, looking at the characteristics of IT systems, including client
Client (computing)
A client is an application or system that accesses a service made available by a server. The server is often on another computer system, in which case the client accesses the service by way of a network....
s, server
Server (computing)
In the context of client-server architecture, a server is a computer program running to serve the requests of other programs, the "clients". Thus, the "server" performs some computational task on behalf of "clients"...
s and private branch exchanges or fax
Fax
Fax , sometimes called telecopying, is the telephonic transmission of scanned printed material , normally to a telephone number connected to a printer or other output device...
machines. The fourth layer falls within the network administrators task area. The fifth within that of the applications administrator and the IT user, concerning software like database management system
Database management system
A database management system is a software package with computer programs that control the creation, maintenance, and use of a database. It allows organizations to conveniently develop databases for various applications by database administrators and other specialists. A database is an integrated...
s, e-mail
E-mail
Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
and web servers.

The necessary measures are presented in a text with short illustrations. The text follows the facts of the life cycle in question and includes planning and design, acquisition (if necessary), realization, operation, selection (if necessary), and preventive measures. After a complete depiction, individual measures are once again collected into a list, which is arranged according to the measures catalog's structure, rather than that of the life cycle. In the process, classification of measures into the categories A, B, C, and Z is undertaken. Category A measures for the entry point into the subject, B measures expand this, and category C is ultimately necessary for baseline protection certification. Category Z measures any additional measures that have proven themselves in practice.

The respective measures or threats, which are introduced in the component, can also be relevant for other components. In this way, a network of individual components arises in the baseline protection catalogs.
Threat catalogs
The threat catalogs, in connection with the component catalogs, offer more detail about potential threats to IT systems. These threat catalogs follow the general layout in layers. "Force majeure", "organizational deficiencies", "spurious human action", "technical failure", and "premeditated acts" are distinguished. According to the BSI, the knowledge collected in these catalogs is not necessary to establish baseline protection. Baseline protection does, however, demand an understanding of the measures, as well as the vigilance of management. Individual threat sources are described briefly. Finally, examples of damages that can be triggered by these threat sources are given.Measures catalogs
The measures catalogs summarize the actions necessary to achieve baseline protection; measures appropriate for several system components are described centrally. In the process, layers are used for structuring individual measures groups. The following layers are formed: infrastructure, organization, personnel, hardware and software, communication, and preventive measures.Managers are initially named to initiate and realize the measures in the respective measures description. A detailed description of the measures follows. Finally, control questions regarding correct realization are given. During realization of measures, personnel should verify whether adaptation to the operation in question is necessary; any deviations from the initial measures should be documented for future reference.
Supplementary material
Besides the information summarized in the IT Baseline Protection Manual, the Federal Office for Data Security provides further material in the InternetInternet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
.
The forms provided serve to remedy protection needs for certain IT system components. A table summarizes the measures to be applied for individual components in this regard. Each measure is named and its degree of realization determined. Degrees of realization, "considerable", "yes", "partial", and "no", are distinguished. Finally, the realization is terminated and a manager is named. If the measures' realization is not possible, reasons for this are entered in the adjacent field for later traceability. The conclusion consists of a cost assessment.
Besides the forms, the cross-reference tables another useful supplement. They summarize the measures and most important threats for individual components. Measures, as well as threats, are cited with mnemonic
Mnemonic
A mnemonic , or mnemonic device, is any learning technique that aids memory. To improve long term memory, mnemonic systems are used to make memorization easier. Commonly encountered mnemonics are often verbal, such as a very short poem or a special word used to help a person remember something,...
s. Measures are cited with a priority and a classification. The table contains correlations between measures and the threats they address. However, the cross-reference tables only cite the most important threats. If the measure cited for a given threat is not applicable for the individual IT system, it is not superfluous. Baseline protection can only be ensured if all measures are realized.
Further reading
- IT Baseline Protection Handbook. Germany. Federal Office for Security in Information Technology. BundesanzeigerBundesanzeigerThe Bundesanzeiger is an official publication of the Federal Republic of Germany published by the German department of Justice with a scope similar to that of the Federal Register in the United States. It is used for announcing laws, mandatory legal and judicial announcements, announcing changes in...
, Cologne 2003-2005. - Baseline Protection Guide. Germany. Federal Office for Security in Information Technology, 2006 version.

