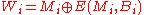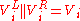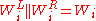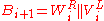MDC-2
Encyclopedia
In cryptography
, MDC-2 (Modification Detection Code 2, sometimes called Meyer-Schilling) is a cryptographic hash function
. MDC-2 is a hash function based on a block cipher with a proof of security in the ideal-cipher model. The length of the output hash depends on the underlying block cipher used.
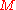 to hash and a given block cipher encryption function
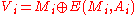
to hash and a given block cipher encryption function  , the MDC-2 algorithm proceed as followed. Let
, the MDC-2 algorithm proceed as followed. Let  be the block length,
be the block length, 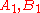 two different constants of size
two different constants of size  . If
. If 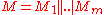 where each
where each 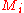 has size
has size  , then the hash
, then the hash 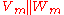 of the message is given by:
of the message is given by:
block cipher, the 128-bit (16-byte) MDC-2 hashes are typically represented as 32-digit hexadecimal
numbers. The following demonstrates a 43-byte ASCII
input and the corresponding MDC-2 hash:
MDC2("The quick brown fox jumps over the lazy dog")
= 000ed54e093d61679aefbeae05bfe33a
Even a small change in the message will (with probability) result in a completely different hash, e.g. changing d to c:
MDC2("The quick brown fox jumps over the lazy cog")
= 775f59f8e51aec29c57ac6ab850d58e8
The hash of the zero-length string is:
MDC2("")
= 52525252525252522525252525252525
on August 28, 1987.
For this reason, support for MDC-2 has been disabled in OpenSSL
on most Linux
distributions and is not implemented by many other cryptographic libraries.
But the maximum lifespan of 20 years from filing date means that the could not have lasted beyond August 28, 2007 ; in fact it has expired in 2002, because IBM has not paid the renewal fee. The same goes for the Canadian patent. There is no patent for Europe.
This means that MDC2 can be freely used.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, MDC-2 (Modification Detection Code 2, sometimes called Meyer-Schilling) is a cryptographic hash function
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
. MDC-2 is a hash function based on a block cipher with a proof of security in the ideal-cipher model. The length of the output hash depends on the underlying block cipher used.
Algorithm
For a given message to hash and a given block cipher encryption function
to hash and a given block cipher encryption function  , the MDC-2 algorithm proceed as followed. Let
, the MDC-2 algorithm proceed as followed. Let  be the block length,
be the block length, 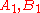 two different constants of size
two different constants of size  . If
. If 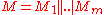 where each
where each 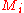 has size
has size  , then the hash
, then the hash 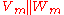 of the message is given by:
of the message is given by:
- for
 to
to  :
:
- return
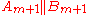
MDC-2DES hashes
When MDC-2 uses the DESData Encryption Standard
The Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
block cipher, the 128-bit (16-byte) MDC-2 hashes are typically represented as 32-digit hexadecimal
Hexadecimal
In mathematics and computer science, hexadecimal is a positional numeral system with a radix, or base, of 16. It uses sixteen distinct symbols, most often the symbols 0–9 to represent values zero to nine, and A, B, C, D, E, F to represent values ten to fifteen...
numbers. The following demonstrates a 43-byte ASCII
ASCII
The American Standard Code for Information Interchange is a character-encoding scheme based on the ordering of the English alphabet. ASCII codes represent text in computers, communications equipment, and other devices that use text...
input and the corresponding MDC-2 hash:
MDC2("The quick brown fox jumps over the lazy dog")
= 000ed54e093d61679aefbeae05bfe33a
Even a small change in the message will (with probability) result in a completely different hash, e.g. changing d to c:
MDC2("The quick brown fox jumps over the lazy cog")
= 775f59f8e51aec29c57ac6ab850d58e8
The hash of the zero-length string is:
MDC2("")
= 52525252525252522525252525252525
Patent issues
MDC-2 was covered by , issued on March 13, 1990 but filed by IBMIBM
International Business Machines Corporation or IBM is an American multinational technology and consulting corporation headquartered in Armonk, New York, United States. IBM manufactures and sells computer hardware and software, and it offers infrastructure, hosting and consulting services in areas...
on August 28, 1987.
For this reason, support for MDC-2 has been disabled in OpenSSL
OpenSSL
OpenSSL is an open source implementation of the SSL and TLS protocols. The core library implements the basic cryptographic functions and provides various utility functions...
on most Linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
distributions and is not implemented by many other cryptographic libraries.
But the maximum lifespan of 20 years from filing date means that the could not have lasted beyond August 28, 2007 ; in fact it has expired in 2002, because IBM has not paid the renewal fee. The same goes for the Canadian patent. There is no patent for Europe.
This means that MDC2 can be freely used.