
PKCS1
Encyclopedia
In cryptography
, PKCS#1 is the first of a family of standards called Public-Key Cryptography Standards (PKCS)
, published by RSA Laboratories. It provides the basic definitions of and recommendations for implementing the RSA algorithm for public-key cryptography
. It defines the mathematical properties of public and private keys, primitive operations for encryption and signatures, secure cryptographic schemes, and related ASN.1
syntax representations.
The current version, 2.1, was published in June 2002, and was also republished as RFC 3447 in February 2003.
 , which is the product of two distinct large prime number
, which is the product of two distinct large prime number
s,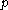 and
and 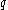 , such that
, such that 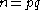 .
.
Starting with version 2.1, this definition was generalized to allow for a multi-prime keys, where the number of distinct primes may be two or more. When dealing with multi-prime keys, the prime factors are all generally labeled as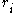 for some
for some 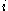 , such that:
, such that:
As a notational convenience, and
and 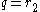 .
.
The RSA public key is represented as the tuple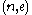 , where the integer
, where the integer  is the public exponent.
is the public exponent.
The RSA private key may have two representations. The first compact form is the tuple , where
, where 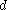 is the private exponent. The second form has at least five terms, or more for multi-prime keys. Although mathematically redundant to the compact form, the additional terms allow for certain computational optimizations when using the key.
is the private exponent. The second form has at least five terms, or more for multi-prime keys. Although mathematically redundant to the compact form, the additional terms allow for certain computational optimizations when using the key.
There are two schemes for encryption and decryption:
There are also two schemes for dealing with signatures:
The two signature schemes make use of separately defined encoding methods:
The signature schemes are actually signatures with appendix, which means that rather than signing some input data
directly a hash function
is used first to produce an intermediary representation of the data and then the result of the hash is signed. This technique is almost always used with RSA because the amount of data that can be directly signed is proportional to the size of the keys; which is almost always much smaller than the amount of data an application may wish to sign.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, PKCS#1 is the first of a family of standards called Public-Key Cryptography Standards (PKCS)
PKCS
In cryptography, PKCS refers to a group of public-key cryptography standards devised and published by RSA Security.RSA Data Security Inc was assigned the licensing rights for the patent on the RSA asymmetric key algorithm and acquired the licensing rights to several other key patents as well...
, published by RSA Laboratories. It provides the basic definitions of and recommendations for implementing the RSA algorithm for public-key cryptography
Public-key cryptography
Public-key cryptography refers to a cryptographic system requiring two separate keys, one to lock or encrypt the plaintext, and one to unlock or decrypt the cyphertext. Neither key will do both functions. One of these keys is published or public and the other is kept private...
. It defines the mathematical properties of public and private keys, primitive operations for encryption and signatures, secure cryptographic schemes, and related ASN.1
Abstract Syntax Notation One
Data generated at various sources of observation need to be transmitted to one or more locations that process it to generate useful results. For example, voluminous signal data collected by a radio telescope from outer space. The system recording the data and the system processing it later may be...
syntax representations.
The current version, 2.1, was published in June 2002, and was also republished as RFC 3447 in February 2003.
Keys
The PKCS#1 standard defines the mathematical definitions and properties that RSA public and private keys must have. The traditional key pair is based on a modulus, , which is the product of two distinct large prime number
, which is the product of two distinct large prime numberPrime number
A prime number is a natural number greater than 1 that has no positive divisors other than 1 and itself. A natural number greater than 1 that is not a prime number is called a composite number. For example 5 is prime, as only 1 and 5 divide it, whereas 6 is composite, since it has the divisors 2...
s,
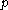 and
and 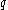 , such that
, such that 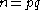 .
.Starting with version 2.1, this definition was generalized to allow for a multi-prime keys, where the number of distinct primes may be two or more. When dealing with multi-prime keys, the prime factors are all generally labeled as
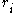 for some
for some 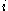 , such that:
, such that:-
 for
for 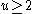
As a notational convenience,
 and
and 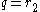 .
.The RSA public key is represented as the tuple
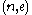 , where the integer
, where the integer  is the public exponent.
is the public exponent.The RSA private key may have two representations. The first compact form is the tuple
 , where
, where 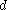 is the private exponent. The second form has at least five terms, or more for multi-prime keys. Although mathematically redundant to the compact form, the additional terms allow for certain computational optimizations when using the key.
is the private exponent. The second form has at least five terms, or more for multi-prime keys. Although mathematically redundant to the compact form, the additional terms allow for certain computational optimizations when using the key.Primitives
The standard defines several basic primitives. The primitive operations provide the fundamental instructions for turning the raw mathematical formulas into computable algorithms.- I2OSP, OS2IP: conversion between the potentially large nonnegative integers encountered in the mathematical formulas and their computer data representation as a sequence of bytes (an octet stringOctet (computing)An octet is a unit of digital information in computing and telecommunications that consists of eight bits. The term is often used when the term byte might be ambiguous, as there is no standard for the size of the byte.-Overview:...
). - RSAEP, RSADP: basic encryption and decryption algorithms.
- RSASP1, RSAVP1: algorithms for producing and verifying signatures.
Schemes
By themselves the primitive operations do not necessarily provide any security. The concept of a cryptographic scheme is to define higher level algorithms or uses of the primitives so they achieve certain security goals.There are two schemes for encryption and decryption:
- RSAES-OAEP: improved encryption/decryption scheme; based on the Optimal Asymmetric Encryption PaddingOptimal Asymmetric Encryption PaddingIn cryptography, Optimal Asymmetric Encryption Padding is a padding scheme often used together with RSA encryption. OAEP was introduced by Bellare and Rogaway....
scheme proposed by Mihir BellareMihir BellareMihir Bellare is a cryptographer and professor at the University of California, San Diego. He has published several seminal papers in the field of cryptography , many coauthored with Phillip Rogaway. Bellare has published a number of papers in the field of Format-Preserving Encryption...
and Phillip RogawayPhillip RogawayPhillip Rogaway is a professor of computer science at the University of California, Davis. He graduated with an BA in computer science from UC Berkeley and completed his PhD in cryptography at MIT, in the Theory of Computation group. He has taught at UC Davis since 1994.Dr...
. - RSAES-PKCS1-v1_5: older encryption/decryption scheme as first standardized in version 1.5 of PKCS#1.
There are also two schemes for dealing with signatures:
- RSASSA-PSS: improved probabilistic signature scheme with appendix; based on the Probabilistic Signature Scheme originally invented by Bellare and Rogaway.
- RSASSA-PKCS1-v1_5: old signature scheme with appendix as first standardized in version 1.5 of PKCS#1.
The two signature schemes make use of separately defined encoding methods:
- EMSA-PSS: encoding method for signature appendix, probabilistic signature scheme.
- EMSA-PKCS1-v1_5: encoding method for signature appendix as first standardized in version 1.5 of PKCS#1.
The signature schemes are actually signatures with appendix, which means that rather than signing some input data
directly a hash function
Hash function
A hash function is any algorithm or subroutine that maps large data sets to smaller data sets, called keys. For example, a single integer can serve as an index to an array...
is used first to produce an intermediary representation of the data and then the result of the hash is signed. This technique is almost always used with RSA because the amount of data that can be directly signed is proportional to the size of the keys; which is almost always much smaller than the amount of data an application may wish to sign.
Version history
- Versions 1.1–1.3, February through March 1991, privately distributed.
- Version 1.4, June 1991, published for NIST/OSI Implementors' Workshop.
- Version 1.5, November 1993. First public publication. Republished as RFC 2313.
- Version 2.0, September 1998. Republished as RFC 2437.
- Version 2.1, June 2002. Republished as RFC 3447.
External links
- PKCS #1: RSA Cryptography Standard, RSA Laboratories
- RFC 3447
- Raising the Standard for RSA Signatures: RSA-PSS, Burt Kaliski, RSA Laboratories February 26, 2003.

