
Winzapper
Encyclopedia
Freeware
Freeware is computer software that is available for use at no cost or for an optional fee, but usually with one or more restricted usage rights. Freeware is in contrast to commercial software, which is typically sold for profit, but might be distributed for a business or commercial purpose in the...
utility / hacking tool
Hacking tool
A hacking tool is a program designed to assist with hacking, or a piece of software which can be used for hacking purposes.- Examples :Examples include Nmap, Nessus, John the Ripper, SuperScan, p0f, and Winzapper. Bribes, have also been designated as among the most potent hacking tools, due to its...
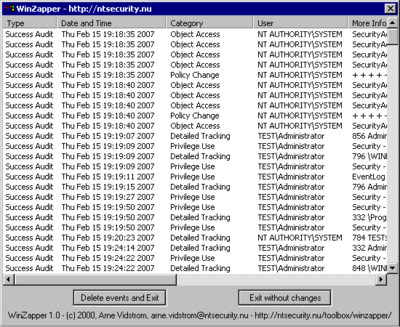
used to delete events from the Microsoft
Microsoft
Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions...
Windows NT 4.0
Windows NT 4.0
Windows NT 4.0 is a preemptive, graphical and business-oriented operating system designed to work with either uniprocessor or symmetric multi-processor computers. It was the next release of Microsoft's Windows NT line of operating systems and was released to manufacturing on 31 July 1996...
and Windows 2000
Windows 2000
Windows 2000 is a line of operating systems produced by Microsoft for use on personal computers, business desktops, laptops, and servers. Windows 2000 was released to manufacturing on 15 December 1999 and launched to retail on 17 February 2000. It is the successor to Windows NT 4.0, and is the...
Security Log
Security log
A security log is used to track security-related information on a computer system. Examples include:* Windows Security Log* Internet Connection Firewall security log...
. It was developed by Arne Vidstrom as a proof-of-concept tool, demonstrating that once the Administrator account has been compromised, event logs are no longer reliable. According to Hacking Exposed: Windows Server 2003, Winzapper works with Windows NT/2000/2003.
Prior to Winzapper's creation, Administrators already had the ability to clear the Security log either through the Event Viewer
Event Viewer
Event Viewer, a component of Microsoft's Windows NT line of operating systems, lets administrators and users view the event logs on a local or remote machine. In Windows Vista, Microsoft overhauled the event system.- Overview :...
or through third-party tools such as Clearlogs However, Windows lacked any built-in method of selectively deleting events from the Security Log. An unexpected clearing of the log would likely be a red flag to system administrators that an intrusion had occurred. Winzapper would allow a hacker to hide the intrusion by deleting only those log events relevant to the attack. Winzapper, as publicly released, lacked the ability to be run remotely without the use of a tool such as Terminal Services
Terminal Services
Remote Desktop Services in Windows Server 2008 R2, formerly known as Terminal Services in Windows Server 2008 and previous versions, is one of the components of Microsoft Windows that allows a user to access applications and data on a remote computer over a network, using the Remote Desktop...
. However, according to Arne Vidstrom, it could easily be modified for remote operation.
There is also an unrelated trojan horse
Trojan horse (computing)
A Trojan horse, or Trojan, is software that appears to perform a desirable function for the user prior to run or install, but steals information or harms the system. The term is derived from the Trojan Horse story in Greek mythology.-Malware:A destructive program that masquerades as a benign...
by the same name.
Countermeasures
Winzapper creates a backup security log, "dummy.dat," at %systemroot%\system32\config. This file may be undeleted after an attack to recover the original log. Conceivably, however, a savvy user might copy a sufficiently large file over the dummy.dat file and thus irretrievably overwrite it. Winzapper causes the Event Viewer to become unusable until after a rebootBooting
In computing, booting is a process that begins when a user turns on a computer system and prepares the computer to perform its normal operations. On modern computers, this typically involves loading and starting an operating system. The boot sequence is the initial set of operations that the...
, so an unexpected reboot may be a clue that Winzapper has recently been used.. Another potential clue to a Winzapper-based attempt would be corruption of the Security Log (requiring it to be cleared), since there is always a small risk that Winzapper will do this.
According to WindowsNetworking.com, "One way to prevent rogue admins from using this tool on your servers is to implement a Software Restriction Policy using Group Policy that prevents the WinZapper executable from running".

