HUMINT
Encyclopedia
HUMINT, a syllabic abbreviation of the words HUMan INTelligence, refers to intelligence gathering
by means of interpersonal contact, as opposed to the more technical intelligence gathering disciplines such as SIGINT
, IMINT
and MASINT. NATO defines HUMINT as "a category of intelligence derived from information collected and provided by human sources." Typical HUMINT activities consist of interrogations and conversations with persons having access to pertinent information.
Good intelligence management begins with the proper determination of what needs to be known. Unless precise requirements are set, data will be collected unsystematically and the decision maker ultimately left without pertinent information on which to act. Collected data must be evaluated and transformed into a usable form and sometimes stored for future use. Evaluation is essential, because many of the wide variety of sources are of doubtful reliability. A standardized system is used to rate the reliability of sources and the likely accuracy of the information they provide; information may be classified as true once it is confirmed by a number of sources.
The manner in which HUMINT operations are conducted is dictated by both official protocol and the nature of the source of the information. Within the context of the U.S. Military, most HUMINT activity does not involve clandestine activities. Both CI and HUMINT do include clandestine HUMINT
and clandestine HUMINT operational techniques
.
Sources may be neutral, friendly, or hostile, and may or may not be witting of their involvement in the collection of information. "Witting" is a term of intelligence art that indicates that one is not only aware of a fact or piece of information, but also aware of its connection to intelligence activities. Examples of HUMINT sources include, but are not limited to, the following:
It is necessary to know the people from whom information is being obtained, and then to obtain it. HUMINT can provide several kinds of information. It can provide observations during travel or other events from travelers, refugees, escaped friendly POWs, etc. It can provide data on things about which the subject has specific knowledge, which can be another human subject, or, in the case of defectors and spies, sensitive information to which they had access. Finally, it can provide information on interpersonal relationships and networks of interest.
HUMINT is both a source of positive intelligence, but also of information of strong counterintelligence value. Interviews should balance any known information requirements of both intelligence collection guidance and of counterintelligence requirements.
Equally important is the broader area of cultural intelligence, which draws heavily on the social sciences. In a book review in the CIA professional journal, Lloyd F. Jordan recognizes two forms of study of culture, both of which are relevant to HUMINT. In the review, Jordan describes Patai's book as an excellent example of a second type of cultural analysis. He reviews the first group of scientific analyses of culture and character as beginning with "cultural anthropology as early as the 1920s. During World War II, those methods employed earlier in the academic community in this field of research were brought to bear upon a variety of problems connected with the war effort.
"It was precisely the inaccessibility of the target country and the availability of only fragmentary information about it that made national character research relevant to intelligence analysis during the war. The cultural anthropologists had long been developing models of former and disappearing cultures from fragmentary materials. The anthropologists, joined by the psychiatrists, combined the use of psychoanalytic theory, interaction theory, child development theory, and learning theory with standard anthropological research methods to construct models of the contemporary cultures of wartime enemy countries, Japan and Germany." The classic work of this type is Ruth Benedict
's study of Japan, The Chrysanthemum and the Sword.
Jordan observes that Benedict's approach was the only one in use until the late 1950s. "National character studies" focused on the statistically most significant personality characteristics of the group (i.e., the modal personality), rather than the most common manifestation of the traits. "...modal personality construct[s] tended to be related to the total culture, or at least, its salient features."
The second class of studies, of which Patai's is an exemplar for Arab culture, had a more narrow focus. "...they concentrated on the relationship of personality traits to subsets of a given society or a given category of roles of that society, rather than on the identification of relationships between personality and the social structure as a whole." A third category, the comparative study, included Francis L. K. Hsu's Americans and Chinese. Indeed, some recent and controversial works, such as Huntington's The Clash of Civilizations and the Remaking of World Order can be regarded as an extension of comparative study into the idea of conflicts among the groups compared.
Some organizations teach their members that the other side tortures everyone, and, if that is known, that fear must be addressed; Japanese prisoners in WWII often attempted suicide for that reason but were sometimes dissuaded, as by Guy Gabaldon
.
"The question of torture should be disposed of at once. Quite apart from moral and legal considerations, physical torture or extreme mental torture is not an expedient device. Maltreating the subject is from a strictly practical point of view as short-sighted as whipping a horse to his knees before a thirty-mile ride. It is true that almost anyone will eventually talk when subjected to enough physical pressures, but the information obtained in this way is likely to be of little intelligence value and the subject himself rendered unfit for further exploitation. Physical pressure will often yield a confession, true or false, but what an intelligence interrogation seeks is a continuing flow of information."
Especially when the subject is a prisoner, the screener, who need not be the main interrogator, should examine the Enemy Prisoner of War (EPW) captive tag or other basic information giving the circumstances of capture: when, where, how, by whom, and so forth.
If the subject is not under any restraint, it is still quite useful for a screener to prepare contact information comparable to the information on the EPW tag.
When the subject is a POW, screeners should pay particular attention to rank insignia, condition of uniforms and equipment, and behavior demonstrated by the source. Screeners should look for things like attempts to talk to the guards, intentionally joining placement in the wrong segregation group, or any signs of nervousness, anxiety, or fear. Any source whose appearance or behavior indicates that he is willing to talk should be noted by the screeners.
Assuming the subject has been under guard, the screener often can get valuable information about the subject's behavior from the guards. They can tell the screener how the source has responded to orders, what requests have been made by the source, what behavior has been demonstrated by the source, and so forth. Along with the basic contact information, such observations can be extremely helpful to the interrogator, who can study the information before the interview. Having background on the subject helps the interrogator retain the initiative in an interview.
Again for prisoners, screeners should examine the documents captured with the source and any documents pertaining to the source. If the subject is voluntary and providing documents, they may even be more valuable. Screeners may need to get help from linguists or document specialists in understanding the material. If the documents have insignia or other graphics, these should be compared with an existing graphics register, and added to it if they are new.
Documents captured with the source (identification card, letters, map sections, and so forth) can provide information that identifies the source, his organization, his mission, and other personal background (family, knowledge, experience, and so forth). This information can be used to verify information from documents captured with the source and further assess his willingness to cooperate. When examining documents, screeners should look for items that will indicate whether the source is cooperative or willing to cooperate based on any specific personal interest.
If the source has information pertaining to new foreign material, contact appropriate TECHINT
specialists, and if the source has information of target exploitation interest, contact the appropriate staff members who deal with targeting. These specialists are not necessarily qualified interrogators and may need to meet jointly with the subject and interrogator, or pass questions to the interrogator.
Screening techniques also can select individuals who may be prospects to collect intelligence or work, in other ways, with the HUMINT organization or its sponsor. Individuals may also be identified who are of interest to counterintelligence or to technical intelligence
specialists.
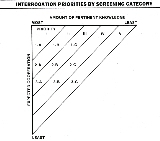
System for Prioritizing Interview Subjects >
Cooperation level
Cooperation code
Knowledgeability level
Knowledgeability code
Responds to direct questions
1
Very likely to have pertinent information
A
Responds hesitantly
2
May have pertinent information
B
Does not respond
3
Unlikely to have pertinent information
C
 It may be necessary to screen individuals in a local area, as residents or possibly workers, to determine if they may be security risks.
It may be necessary to screen individuals in a local area, as residents or possibly workers, to determine if they may be security risks.
and countertransference. In the former, the subject projects emotional experiences of his own onto the interrogator, and in the latter, the interrogator will start thinking of the subject in terms of his own life experiences.
There are other ways to use social science to understand interviews, in the broad sense of cooperative debriefing and hostile interrogation. Speaking of interrogation in the law enforcement context, "There is a vast literature on interrogation ... but hardly anything on it at all in the field of argumentation theory
. There is, of course, a reason for this imbalance. Argumentation theorists have taken as their point of interest rational argumentation in which two parties reason together to try to get at the truth of a matter following collaborative rules of procedure. And the interrogation is scarcely a model of how to conduct balanced rational argumentation. Far from that, it seems to represent a coercive kind of dialogue exchange that is associated with intimidation..."
but a debriefing is not necessarily coercive, and, in some cases, even an interrogation becomes less coercive, if the subject begins to identify with the conceptual framework of the interrogator. The latter can be a false Stockholm syndrome
context, or it can be a case where the subject actually sees that his belief system has fallacies, and he may start to share aspects of the interrogator's mindset.
One variant occurred with WWII Japanese prisoners who, perhaps having been captured while unconscious, believe that the shame of capture, in their native culture, permanently separates them from that culture.
If they are unable to commit suicide, they appeared to see themselves as now part of the interrogator's culture, and became quite cooperative. "...there was one infallible method of convincing a reluctant Japanese prisoner to tell all he knows: to tell him, via interpreters, that they will send his name and picture back to Japan. ... We might note that few Japanese ever attempt to hold anything back. Being taken prisoner is not in their handbooks. No Japanese is ever taken alive. Thus, they are not drilled in the "Name- Rank- Serial No- nothing more" routine. They usually reveal everything easily without any persuasion and seem unhappy when their lack of information does not permit them to answer a specific question. [a captured officer]...doesn't expect to return to Japan ever, has completely excluded his family and his wife from his thinking, and appears pleasantly resigned to going to the States and working there even as a prisoner for the rest of his life."
In argumentative theory, interrogation is a form of information-seeking dialogue, but also can include other kinds of dialogue, such as negotiation. In both police and intelligence interviews, there may be bargaining, where the interrogator offers incentives for the subject to reveal information. The revealed information, especially in a HUMINT context, is not necessarily about the interrogation and also may involve persuasion of the subject to speak.
Before going on to study the relationship of the interrogation to information seeking
dialogue, some account must be given of other types of dialogue related to interrogation as well. For the interrogation has a way of shifting from pure information-seeking to other types of dialogue. As an example, argumentative theory recognizes 'persuasion', in the sense meant in the persuasion dialogue, with certain strategic interrogations, the interrogator might objectively question some of the practices of the subject's side. This is not done for direct elicitation of information, but to set a new context for further interrogation in which the subject might question some of his own loyalties and assumptions. In the case of the Japanese prisoners of the US, they began to operate in that new context.
Types of people being interviewed include both "tasked" and "non-tasked" individuals. Tasked individuals are, in some way, part of the interviewer's organization.
Categories of interviewees for voluntary debriefing >
Tasked
Not tasked
Military police and infantry patrols in nominally controlled areas
Residents of nominally controlled areas
Special reconnaissance teams (see special reconnaissance
)
Nongovernmental organization workers in the area of operations
Diplomats of one's own country
Friendly or neutral foreign diplomats
National or higher command level subject matter experts (e.g., intelligence personnel)
Persons outside the area but knowledgeable about it (e.g., émigrés)
Tasked personnel giving brief reports of the enemy use the SALUTE technique. More formal or extensive debriefing methods are used for obtaining specialized or complex information.
Other than talking to tasked personnel, there is a tendency for some HUMINT collectors to regard debriefing as a waste of time. The approach to a voluntary source needs to be quite different than even to a cooperative prisoner, especially if the interrogator has reason to believe the source is knowledgeable. While a subject may be a volunteer, a refugee or displaced person is likely to have some of the fears and uncertainty undergone by POWs. Active listening and sympathy can pay great benefits, especially in the areas of love of family, and anger at those who made them homeless.
The HUMINT collector should allow specialized or senior sources more latitude to interpose their opinions and evaluations. Prior to the meeting, collectors need to examine all available information, to have an idea of the subject's personality and motivations when beginning to talk to them. It also may require unobtrusive observation of the subject to establish such things as patterns of activity and likes and dislikes. The closer the interview environment can be to the customary surroundings of the subject, the more comfortable and cooperative the source may be.
One example of source that should have latitude are trained foreign internal defense
(FID) or unconventional warfare
(UW) personnel that work with local residents, or military forces, on a routine basis. Such people may very well themselves have HUMINT and/or CI training; US Special Forces groups have two-man HUMINT/CI teams that can augment operational detachments.
Historically, after the WWII experience of resistance leaders such as the Jedburgh teams
, occurred to various commanders that soldiers trained to operate as guerillas would have a strong sense of how to fight guerillas. Even before specialist FID/UW units were constituted, organizations such as Military Assistance Advisory Group
s, as in Greece just after WWII, also had extensive local knowledge. Before the partition of French Indochina in 1954, French Groupement de Commandos Mixtes Aéroportés
(GCMA) took on this role, drawing on French experience with the Jedburgh teams. GCMA, operating in Tonkin and Laos under French intelligence, was complemented by Commandos Nord Viêt-Nam in the North. In these missions, the SOF teams lived and fought with the locals.
United States Army Special Forces
, U.S. Marine Corps
Combined Action Program
(CAP) program personnel (originally in Vietnam, but now in Iraq)
and various training detachments are apt to have valuable and structured information.
In all cases, the more knowledgeable the interrogator is to the volunteer, the better the result is likely to be. A collector does not need to keep the same level as control as in a hostile interrogation. Sometimes, admitting ignorance of a custom, and respectfully asking for explanation, will trigger a flow of information.
While it takes sophistication, the best general approach to willing subjects is a planned elicitation of information, always with a specific goal in mind. The key to elicitation is the establishment of a rapport between the elicitor and the source, normally based on shared interests. In the initial stages of an elicitation, the collector confines his conversations to innocuous subjects such as sports and social commentary. Dependent on the value of the source, the collection environment, and the security consciousness of the subject, the HUMINT specialist will then shift to a more focused topic.
Once in that mode, elicit the information by continuing to ask for clarification, with questions of the form "I agree, however, what did you mean by....?") or expressing a hypothetical situation. The focused discussion can involve mild flattery and interest in the conversation, or, in a much more delicate approach, selectively challenging statements or introducing new information to show knowledge and stimulate more responses.
is not necessarily cooperating with the obtaining of information by the organization. The subject is normally in custody, although the legal circumstances may be such that an uncooperative subject may be able to leave.
Examples of subjects being interrogated include POWs, individuals detained by patrol as not being from the area, and a thief arrested by the civilian police.
Interrogation is a skilled technique, which often involves building rapport with the subject. In an intelligence context, interrogators should be trained specialists, although they may work with linguists and subject matter experts.
Regardless of whether the interview is voluntary or involuntary, the interrogator needs to keep the initiative. To keep the initiative, the interrogator may not need to be harsh. Indeed, the many successful interrogators are formally polite within the subject's cultural traditions. If, in societies with a strong host-guest tradition, the interrogator takes the role of host, that can allow polite domination of the conversation.
The interrogation process itself is a HUMINT collection, not analysis, technique. It may well be that the interrogator, after the interview, does analysis, cross-checking statements made against name indices and "wiring diagrams" of social networks. The interrogator checks his notes against the finished report to ensure that the report contains and identifies the information as heard, seen, or assumed by the source
The basic elements to collect are:
"The preliminary interview is not intended to obtain intelligence, but only to enable the interrogators to make a firm assessment of the character and type of subject with whom they will have to deal."
How much psychological pressure to use, how many symbols of dominance are appropriate to use, require great judgment. Some classic interviewing techniques, without threatening the subject, make him uncomfortable, as, for example, having "interrogators - preferably two of them - seated behind a table at the far end of a long room, so that the subject after entering will have some distance to walk before taking his chair in front of them. This device will enable them to observe his poise and manner, and may often quite unsettle the subject. In this pressure-oriented technique, the interrogators should sit with their backs to the main source of light in order to obscure their faces, veil their expressions, and place a strain on the prisoner. The subject can be placed under further strain by providing him an uncomfortable chair, say one with a polished seat and shortened front legs so that he tends to slide off it, or one with wobbly legs.
"On the other hand, an opposite technique has sometimes been successful: the prisoner is made so comfortable, after a hearty lunch with beer, that he drops his guard in drowsiness.
When conducting military source operations, the location of the questioning will have psychological effects on the source. The questioning location should be chosen and set up to correspond to the effect that the HUMINT collector wants to project and his planned approach techniques. For example, meeting in a social type situation such as a restaurant may place the source at ease. Meeting in an apartment projects informality while meeting in an office projects more formality. Meeting at the source's home normally places him at a psychological advantage, while meeting in the HUMINT collector's work area gives the collector a psychological edge. The HUMINT collector should consider the status and level of the source, security, the workspace available, furnishings, the amount of lighting provided, and the ability to heat or cool the room as needed.
The HUMINT collector must also consider the physical conditions of the source and himself. After extended operations, there may be a limit on how long either the HUMINT collector or source can concentrate on a given subject.
The HUMINT collector must decide if he will need additional support including analytical, technical, or interpreter support. On rare occasions, it may be desirable for the HUMINT collector to seek polygraph support or support from a Behavioral Science Consultant (BSC). BSCs are authorized to make psychological assessments of the character, personality, social interactions, and other behavioral characteristics of interrogation subjects and advise HUMINT collectors of their assessments, as needed.
A cooperative and friendly source offers little resistance to the interrogation and normally speaks freely on almost any topic introduced, other than that which will tend to incriminate or degrade him personally.
To obtain the maximum amount of information from cooperative and friendly sources, the interrogator takes care to establish and to preserve a friendly and cooperative atmosphere by not inquiring into those private affairs which are beyond the scope of the interrogation. At the same time, he must avoid becoming overly friendly and losing control of the interrogation. The interrogator, however, may need to get expert advice on the customs of the subject's culture. While Americans might not spend time inquiring about the journey to the place of the interrogation, the health of one another's family, etc., not to do so is extremely impolite in some cultures. Not following cultural norms may transform a cooperative subject into a silent one.
For example, Arab cultural norms, reasonable to follow in a friendly conversation with a subject of that culture, do, often in ceremonial terms, speak of family. Handshakes are traditional at the start and end of the meeting.
A neutral and nonpartisan source is cooperative to a limited degree. He normally takes the position of answering questions asked directly, but seldom volunteers information. In some cases, he may be afraid to answer for fear of reprisals by the enemy. This often is the case in low-intensity conflict (LIC) where the people may be fearful of insurgent reprisals. With the neutral and nonpartisan source, the interrogator may have to ask many specific questions to obtain the information required.
A hostile and antagonistic source is most difficult to interrogate. In many cases, he refuses to talk at all and offers a real challenge to the interrogator. An interrogator must have self-control, patience, and tact when dealing with him.
Inexperienced interrogators may do well to limit their interview, and pass the subject to a more senior interrogator. When handing off the subject, the next interrogator will find it very useful to have any clues why the subject is being hostile.
"The recalcitrant subject of an intelligence interrogation must be "broken" but broken for use like a riding horse, not smashed in the search for a single golden egg."
No two interrogations are the same. Each interrogation is thus carefully tailored to the measure of the individual subject. The standard lines of procedure, however, may be divided into four parts:
The first three steps, which emphatically do not involve torture, can be combined and called the "softening-up" process. If the subject is using a cover story, it may be broken by softening-up.
"Showing some subjects up as liars is the very worst thing to do, because their determination not to lose face will only make them stick harder to the lie. For these it is necessary to provide loopholes by asking questions which let them correct their stories without any direct admission to lying".
The questioning itself can be carried out in a friendly, persuasive manner, from a hard, merciless and threatening posture, or with an impersonal and neutral approach. In order to achieve the disconcerting effect of alternation among these attitudes it may be necessary to use as many as four different interrogators playing the following roles, although one interrogator may sometimes double in two of them:
Which course is better will depend on the subject's character, the way he was broken, and his present attitude toward those who have been handling him. Sometimes only a fresh interrogator can get real cooperation from him. Sometimes, on the other hand, he is so ashamed of having broken that he is unwilling to expose himself further and wants to talk only to his original questioner. And sometimes he has built up a trustful and confiding relationship with his interrogator which should not be destroyed by the introduction of another personality.
If a source cooperates, his or her motivations vary. They can range from altruism to personal gain; they may be based on logic or emotion. From a psychological standpoint, the HUMINT collector must be cognizant of the following behaviors. People tend to—
If he does introduce himself, normally he will adopt a duty position and rank supportive of the approach strategy selected during the planning and preparation phase. The HUMINT collector must select a rank and duty position that is believable based on the HUMINT collector's age, appearance, and experience. A HUMINT collector may, according to international law, use ruses of war to build rapport with interrogation sources, and this may include posing or "passing himself off" as someone other than a military interrogator. However, the collector must not pose as—
"The attitude of the interrogators at the preliminary interview should usually be correct, studiously polite, and in some cases even sympathetic. It is imperative that they keep their tempers both now and throughout the interrogation. The prisoner may be given the true reason for his arrest or a false one, or he may be left in doubt, according to the circumstances of the case. The interrogators must try to determine whether his usually vigorous protestations of innocence are genuine or an act, but they should not at this stage give any indication of whether they believe or disbelieve him. A clever prisoner will try to find out how much the interrogators know; they should at all costs remain poker-faced and non-committal.
"At this interview the interrogators should do as little as possible of the talking, however many questions they are anxious to have answered. The prisoner should be asked to tell his story in his own words, describe the circumstances of his arrest, give the history of some period of his life, or explain the details of his occupation. The object is to get him to talk without prompting in as much continuous narrative as possible; the more he talks the better the interrogators can assess his personality.
"The interrogators must on no account try to do this job themselves; it would distract them from the critical task of framing questions and steering the course of interrogation according to the implications of the subject's replies. Whether the stenographer or recorder should be concealed or visible depends on the subject's sophistication and the state of his alert. If the recording process is not evident some subjects may become careless of what they say when they see that the interrogators are not taking notes, whereas a visible recording would alert them to be more cautious. For others, consciousness of a recording going on in full view may be unnerving, and they may betray the weak links in their stories by showing signs of distress at these points.
"At a later stage of the interrogation it may be of value to play back to the subject some part of this recording. The sound of his own voice repeating his earlier statements, particularly any with intonations of anger or distress, may make a psychological breach in his defenses."
Interpreters are frequently a necessary aid to HUMINT collection. There are certain advantages to using an interpreter. The most obvious is that without an interpreter, a HUMINT collector without the proper language or necessary proficiency in that language is severely limited. Furthermore, if properly trained, briefed, and assessed, the interpreter can be a valuable assistant to the HUMINT collector.
Interpreters may have more knowledge of the local culture as well as the language, but the HUMINT manager must be cautious that the interpreter is not, for example, a member of a subculture, religion, etc., of the area, that would be offensive to the subject.
Going through an interpreter will slow the process, and also increase the chance of miscommunication. HUMINT collectors also need to be sure that local or third-country nationals are aware of security, and indeed will be loyal to the interpreter's side.
The collector should be aware of potential problems in interpretation. Some warning signs include:
of one's own side. See special reconnaissance
for details. Since these are highly trained specialists, they will usually have been communicating clandestinely to the HUMINT organization, and will be systematically prepared for debriefing. The debriefing may be done by HUMINT officers of their own organization, who are most familiar with their information-gathering techniques. Some of those techniques may be extremely sensitive and held on a need-to-know basis within the special reconnaissance organization. They operate significantly farther than the furthest forward friendly scouting and surveillance
units; they may be tens to hundreds of kilometers deeper. They may enter the area of operations in many ways.
Their mission is not to engage in direct combat. It may be to observe and report, or it may include directing air or artillery attacks on enemy positions. If the latter is the case, the patrol still tries to stay covert; the idea is that the enemy obviously knows they are being attacked, but not who is directing fire.
is the collection of information by people either in a position of trust for the enemy, or with access to people with such access. The process of recruiting such individuals and supporting their operations is the HUMINT discipline of agent handling
.
It may be possible for an agent handler to meet directly with the agent and debrief him. More commonly, agents send messages to the organization for which they work, by radio, Internet, or by leaving the messages in a hard-to-find place. The latter technique, called a dead drop
, will have either a courier
or the agent handler retrieve them in a clandestine
manner. These are examples of espionage tradecraft.
Once information is obtained, it is put into an organized form. Very frequently, information obtained at one interview may help structure the next interview with the same person, or with another subject.
 The interviewer, really not knowing many of the villagers, guesses and prompts. "The silk man? Is that the son of the olive farmer married to...umm...I will think of their names".
The interviewer, really not knowing many of the villagers, guesses and prompts. "The silk man? Is that the son of the olive farmer married to...umm...I will think of their names".
Anna responds, "No, the silk man is not of the village. I do not know his name."
 Knowing another subject to be debriefed is from the same village, the interviewer might arrange to have cheese and olives available as snacks in the interview room. During the interview with George the villager, the interviewer might say "these are poor olives, but the best I could find in the local market. They are not as good as Gregory, in your village, grows."
Knowing another subject to be debriefed is from the same village, the interviewer might arrange to have cheese and olives available as snacks in the interview room. During the interview with George the villager, the interviewer might say "these are poor olives, but the best I could find in the local market. They are not as good as Gregory, in your village, grows."
"Yes, Chino has excellent trees. It's too bad only one of his sons, Enzo, stayed on the farm. He misses his wandering son who sells cloth to women."
Confirming Anna's statement that the silk man is an outsider, the interviewer seeks confirmation. "Is that the silk man?"
"No, the silk man is Hassan, but only visits the village. Gregory's son Fritz sells wool."
"Do you know the sons of Diana and Chino?"
"Oh yes! I ran a long time to get Iliana the midwife to come. She delivered both his sons."
The interviewer sips his tea and asks, "Midwives are so valuable. Yet what if a baby is coming in wrong, and Iliana cannot get it?"
"Iliana's husband, Justinian, has a truck. Iliana will decide whether he should go get the doctor, or bring the mother and herself to the doctor."
 The interviewer sees Anna in the street, getting out of Justinian's truck, and asks if all is well. "Oh yes, I was just visiting the doctor and everything is fine." Note that Anna has confirmed a relationship between Justinian and the doctor, whose name is not yet known.
The interviewer sees Anna in the street, getting out of Justinian's truck, and asks if all is well. "Oh yes, I was just visiting the doctor and everything is fine." Note that Anna has confirmed a relationship between Justinian and the doctor, whose name is not yet known.
"Anna, I forgot to ask. Who is your husband?"
"I thought everyone knew that Homer and I are such lovers. You must be blind!" The culturally sensitive interviewer laughed, and agreed he needed new glasses.
 The interviewer now knows that the Silk Man and the Doctor are outsiders that visit the village. If there is underground activity, they are possible couriers. Either the interviewer, or a HUMINT analyst, need to find other villages that are visited by the Silk Man and the Doctor, and see if any guerilla events correlate to their visits.
The interviewer now knows that the Silk Man and the Doctor are outsiders that visit the village. If there is underground activity, they are possible couriers. Either the interviewer, or a HUMINT analyst, need to find other villages that are visited by the Silk Man and the Doctor, and see if any guerilla events correlate to their visits.
One relevant study looks at modeling terrorist networks in a manner similar to other systems that "exhibit regularity but not periodicity (i.e., locally random, but globally defined).
Their model focuses at the "mid-range", "not at the level of state leadership, and not at the level of mapping and predicting the behavior of each individual terrorist, but rather at an intermediate or organizational level"... Much as vulnerability analysis of connectionless packet networks such as the Internet
concentrates on the nodes whose loss would most interfere with connectivity, the study here looks for the "pattern of connections surrounding a node that allows for wide network reach with minimal direct ties. "Structural holes" at the intersection of flows across knowledge communities position unique and superior nodes. It is the individuals spanning these "internal holes of opportunity" that impact the network's functioning and performance. The implicit corollary of this is that if a small number of these critical nodes can be identified and "clipped" from the network, then command signals will not be able to propagate through the system."
In the 9/11 case, the pilots were such key nodes, once the US operational groups were in-country and operating. Taking the observation of centrality a step farther, COMINT can complement HUMINT in finding the nodes of a geographically dispersed human network.
process has several problems:
McConnell's solution to this is to
There have been other cases in the past where it has been necessary to balance security clearance policy against national needs, for example:
DNI McConnell notes also in Wright's article that the predominant risk factor which turns officers into traitors is not ethnicity, sexuality or politics, it is money:
For example,
Hence it is difficult to institute technical controls that would allow the organization to effectively compartimentalize the knowledge of officers in the organization so that even moderately untrusted people could serve. I.e., in many cases of "moles" or internal spies, low-level spies have had access to huge volumes of secret data. This would not be possible if adequate technical measures were instituted to effectively compartmentalize information access on a more finely categorized and motivated need-to-know basis. In other words, there is a so far lost opportunity to use technical measures to improve operational security while at the same time allowing a broader range of people to serve. Another aspect of this would be to automatically filter information "down to" and tailored to a specific subject-matter need-to-know characterization of the requesting individual.
in general is effective information sharing across the intelligence community
. Wright's article notes that
Lack of information sharing has been partly addressed technically by adding new information-sharing tools
However, Wright notes that "These innovations have not yet made their way to the analysts and agents in the field", and "the intelligence community has only warily appropriated models whose usefulness is blindingly obvious".
Intelligence (information gathering)
Intelligence assessment is the development of forecasts of behaviour or recommended courses of action to the leadership of an organization, based on a wide range of available information sources both overt and covert. Assessments are developed in response to requirements declared by the leadership...
by means of interpersonal contact, as opposed to the more technical intelligence gathering disciplines such as SIGINT
SIGINT
Signals intelligence is intelligence-gathering by interception of signals, whether between people , whether involving electronic signals not directly used in communication , or combinations of the two...
, IMINT
IMINT
Imagery Intelligence , is an intelligence gathering discipline which collects information via satellite and aerial photography. As a means of collecting intelligence, IMINT is a subset of intelligence collection management, which, in turn, is a subset of intelligence cycle management...
and MASINT. NATO defines HUMINT as "a category of intelligence derived from information collected and provided by human sources." Typical HUMINT activities consist of interrogations and conversations with persons having access to pertinent information.
Good intelligence management begins with the proper determination of what needs to be known. Unless precise requirements are set, data will be collected unsystematically and the decision maker ultimately left without pertinent information on which to act. Collected data must be evaluated and transformed into a usable form and sometimes stored for future use. Evaluation is essential, because many of the wide variety of sources are of doubtful reliability. A standardized system is used to rate the reliability of sources and the likely accuracy of the information they provide; information may be classified as true once it is confirmed by a number of sources.
The manner in which HUMINT operations are conducted is dictated by both official protocol and the nature of the source of the information. Within the context of the U.S. Military, most HUMINT activity does not involve clandestine activities. Both CI and HUMINT do include clandestine HUMINT
Clandestine HUMINT
Clandestine HUMINT includes a wide range of espionage sources. This includes the classic spy who collects intelligence, but also couriers and other personnel, who handle their secure communications...
and clandestine HUMINT operational techniques
Clandestine HUMINT operational techniques
The Clandestine HUMINT page deals with the functions of that discipline, including espionage and active counterintelligence. This page deals with Clandestine HUMINT operational techniques, also called "tradecraft". It applies to clandestine operations for espionage, and for a clandestine phase...
.
Sources may be neutral, friendly, or hostile, and may or may not be witting of their involvement in the collection of information. "Witting" is a term of intelligence art that indicates that one is not only aware of a fact or piece of information, but also aware of its connection to intelligence activities. Examples of HUMINT sources include, but are not limited to, the following:
- Advisors or foreign internal defenseForeign internal defenseForeign internal defense is a term used by a number of Western militaries, including the United States, France and the United Kingdom, to describe an approach to combating actual or threatened insurgency in a foreign state called the Host Nation . The term counter-insurgency is more commonly used...
(FID) personnel working with host nation (HN) forces or populations - Diplomatic reportingDiplomacyDiplomacy is the art and practice of conducting negotiations between representatives of groups or states...
by accredited diplomats (e.g., military attachés); - EspionageEspionageEspionage or spying involves an individual obtaining information that is considered secret or confidential without the permission of the holder of the information. Espionage is inherently clandestine, lest the legitimate holder of the information change plans or take other countermeasures once it...
clandestine reporting, access agents, couriers, cutouts; - Military attachéMilitary attachéA military attaché is a military expert who is attached to a diplomatic mission . This post is normally filled by a high-ranking military officer who retains the commission while serving in an embassy...
s - Non-governmental organizationNon-governmental organizationA non-governmental organization is a legally constituted organization created by natural or legal persons that operates independently from any government. The term originated from the United Nations , and is normally used to refer to organizations that do not form part of the government and are...
s (NGOs); - Prisoners of war (POWs) or detainees;
- Refugees;
- Routine patrollingPatrollingPatrolling is a military tactic. Small groups or individual units are deployed from a larger formation to achieve a specific objective and then return. The tactic of patrolling may be applied to ground troops, armoured units, naval units, and combat aircraft...
(military policeMilitary policeMilitary police are police organisations connected with, or part of, the military of a state. The word can have different meanings in different countries, and may refer to:...
, patrols, etc.) - Special reconnaissanceSpecial reconnaissanceSpecial reconnaissance is conducted by small units of highly trained military personnel, usually from special forces units or military intelligence organisations, who operate behind enemy lines, avoiding direct combat and detection by the enemy. As a role, SR is distinct from commando operations,...
- Traveler debriefing (e.g., CIA Domestic Contact Service)
It is necessary to know the people from whom information is being obtained, and then to obtain it. HUMINT can provide several kinds of information. It can provide observations during travel or other events from travelers, refugees, escaped friendly POWs, etc. It can provide data on things about which the subject has specific knowledge, which can be another human subject, or, in the case of defectors and spies, sensitive information to which they had access. Finally, it can provide information on interpersonal relationships and networks of interest.
HUMINT is both a source of positive intelligence, but also of information of strong counterintelligence value. Interviews should balance any known information requirements of both intelligence collection guidance and of counterintelligence requirements.
Basic HUMINT operations
Human source screening is the logical start of collection of HUMINT. This involves selecting people who may be sources of meaningful HUMINT, possibly positively identifying them, and conducting interviews of various types. Properly recording and cross-indexing the results of interviews is essential. No intelligence collection discipline is more likely to find meaning in apparently small bits of information than is HUMINT. Especially when there is reason to have additional interviews with the same individual, the subsequent interviews need careful planning, especially when the interrogator does not speak the language of the person being interviewed.Intelligence preparation for working in cultures
As with other intelligence collection disciplines, intelligence analysis can play many supporting roles. An obvious one is biographical intelligence, to help identify known hostile undercover personnel, or individuals who will impartially mislead an assortment of national intelligence services for profit.Equally important is the broader area of cultural intelligence, which draws heavily on the social sciences. In a book review in the CIA professional journal, Lloyd F. Jordan recognizes two forms of study of culture, both of which are relevant to HUMINT. In the review, Jordan describes Patai's book as an excellent example of a second type of cultural analysis. He reviews the first group of scientific analyses of culture and character as beginning with "cultural anthropology as early as the 1920s. During World War II, those methods employed earlier in the academic community in this field of research were brought to bear upon a variety of problems connected with the war effort.
"It was precisely the inaccessibility of the target country and the availability of only fragmentary information about it that made national character research relevant to intelligence analysis during the war. The cultural anthropologists had long been developing models of former and disappearing cultures from fragmentary materials. The anthropologists, joined by the psychiatrists, combined the use of psychoanalytic theory, interaction theory, child development theory, and learning theory with standard anthropological research methods to construct models of the contemporary cultures of wartime enemy countries, Japan and Germany." The classic work of this type is Ruth Benedict
Ruth Benedict
Ruth Benedict was an American anthropologist, cultural relativist, and folklorist....
's study of Japan, The Chrysanthemum and the Sword.
Jordan observes that Benedict's approach was the only one in use until the late 1950s. "National character studies" focused on the statistically most significant personality characteristics of the group (i.e., the modal personality), rather than the most common manifestation of the traits. "...modal personality construct[s] tended to be related to the total culture, or at least, its salient features."
The second class of studies, of which Patai's is an exemplar for Arab culture, had a more narrow focus. "...they concentrated on the relationship of personality traits to subsets of a given society or a given category of roles of that society, rather than on the identification of relationships between personality and the social structure as a whole." A third category, the comparative study, included Francis L. K. Hsu's Americans and Chinese. Indeed, some recent and controversial works, such as Huntington's The Clash of Civilizations and the Remaking of World Order can be regarded as an extension of comparative study into the idea of conflicts among the groups compared.
Basic differentiation by subject type
Different types of human subjects will share information voluntarily or involuntarily. The interrogator builds a relationship with the subject, a relationship that can be based on trust, fear, friendship, or any of a range of human emotions. Prisoners have an understandable fear of what may happen, and, contrary to "tough guy" images, it can be important to relax them and, as much as possible, put them at ease.Some organizations teach their members that the other side tortures everyone, and, if that is known, that fear must be addressed; Japanese prisoners in WWII often attempted suicide for that reason but were sometimes dissuaded, as by Guy Gabaldon
Guy Gabaldon
PFC Guy Louis Gabaldon was a United States Marine who was credited with capturing about 1,500 Japanese soldiers and civilians during the Battle of Saipan in World War II...
.
"The question of torture should be disposed of at once. Quite apart from moral and legal considerations, physical torture or extreme mental torture is not an expedient device. Maltreating the subject is from a strictly practical point of view as short-sighted as whipping a horse to his knees before a thirty-mile ride. It is true that almost anyone will eventually talk when subjected to enough physical pressures, but the information obtained in this way is likely to be of little intelligence value and the subject himself rendered unfit for further exploitation. Physical pressure will often yield a confession, true or false, but what an intelligence interrogation seeks is a continuing flow of information."
Especially when the subject is a prisoner, the screener, who need not be the main interrogator, should examine the Enemy Prisoner of War (EPW) captive tag or other basic information giving the circumstances of capture: when, where, how, by whom, and so forth.
If the subject is not under any restraint, it is still quite useful for a screener to prepare contact information comparable to the information on the EPW tag.
When the subject is a POW, screeners should pay particular attention to rank insignia, condition of uniforms and equipment, and behavior demonstrated by the source. Screeners should look for things like attempts to talk to the guards, intentionally joining placement in the wrong segregation group, or any signs of nervousness, anxiety, or fear. Any source whose appearance or behavior indicates that he is willing to talk should be noted by the screeners.
Assuming the subject has been under guard, the screener often can get valuable information about the subject's behavior from the guards. They can tell the screener how the source has responded to orders, what requests have been made by the source, what behavior has been demonstrated by the source, and so forth. Along with the basic contact information, such observations can be extremely helpful to the interrogator, who can study the information before the interview. Having background on the subject helps the interrogator retain the initiative in an interview.
Again for prisoners, screeners should examine the documents captured with the source and any documents pertaining to the source. If the subject is voluntary and providing documents, they may even be more valuable. Screeners may need to get help from linguists or document specialists in understanding the material. If the documents have insignia or other graphics, these should be compared with an existing graphics register, and added to it if they are new.
Documents captured with the source (identification card, letters, map sections, and so forth) can provide information that identifies the source, his organization, his mission, and other personal background (family, knowledge, experience, and so forth). This information can be used to verify information from documents captured with the source and further assess his willingness to cooperate. When examining documents, screeners should look for items that will indicate whether the source is cooperative or willing to cooperate based on any specific personal interest.
If the source has information pertaining to new foreign material, contact appropriate TECHINT
Techint
Techint is a conglomerate multinational company founded in Milan in September 1945 by Italian industrialist Agostino Rocca and headquartered in Milan and Buenos Aires . Techint comprises more than 100 companies operating worldwide in the following areas of business: Engineering & Construction,...
specialists, and if the source has information of target exploitation interest, contact the appropriate staff members who deal with targeting. These specialists are not necessarily qualified interrogators and may need to meet jointly with the subject and interrogator, or pass questions to the interrogator.
Selecting potential sources
It involves evaluating an individual, or group of individuals, "to determine their potential to answer [intelligence] collection requirements or to identify individuals who match a predetermined source profile. The goal of the process is to identify individuals who may have information of interest, and are willing or can be persuaded to cooperate. Willing individuals will undergo debriefing, and, subject to the relevant laws, regulations and policies of the HUMINT organization, unwilling people may be interrogated.Screening techniques also can select individuals who may be prospects to collect intelligence or work, in other ways, with the HUMINT organization or its sponsor. Individuals may also be identified who are of interest to counterintelligence or to technical intelligence
Techint
Techint is a conglomerate multinational company founded in Milan in September 1945 by Italian industrialist Agostino Rocca and headquartered in Milan and Buenos Aires . Techint comprises more than 100 companies operating worldwide in the following areas of business: Engineering & Construction,...
specialists.

Identification
Since the identity of individuals is very relevant to HUMINT, it makes extensive use of biometric data (e.g., fingerprints, iris scans, voice prints, facial/physical features) collected on persons of interest.Types of interviews
Often not realized is that either a friendly or hostile subject interview has many of the same dynamics as a psychotherapeutic relationship, although obviously for very different, nontherapeutic reasons. In an extended interrogation session, or series of sessions, if there is dialogue between interrogator and subject, as opposed to a subject remaining silent, there will be dynamics closely related to the psychotherapeutic concept of transferenceTransference
Transference is a phenomenon in psychoanalysis characterized by unconscious redirection of feelings from one person to another. One definition of transference is "the inappropriate repetition in the present of a relationship that was important in a person's childhood." Another definition is "the...
and countertransference. In the former, the subject projects emotional experiences of his own onto the interrogator, and in the latter, the interrogator will start thinking of the subject in terms of his own life experiences.
There are other ways to use social science to understand interviews, in the broad sense of cooperative debriefing and hostile interrogation. Speaking of interrogation in the law enforcement context, "There is a vast literature on interrogation ... but hardly anything on it at all in the field of argumentation theory
Argumentation theory
Argumentation theory, or argumentation, is the interdisciplinary study of how humans should, can, and do reach conclusions through logical reasoning, that is, claims based, soundly or not, on premises. It includes the arts and sciences of civil debate, dialogue, conversation, and persuasion...
. There is, of course, a reason for this imbalance. Argumentation theorists have taken as their point of interest rational argumentation in which two parties reason together to try to get at the truth of a matter following collaborative rules of procedure. And the interrogation is scarcely a model of how to conduct balanced rational argumentation. Far from that, it seems to represent a coercive kind of dialogue exchange that is associated with intimidation..."
but a debriefing is not necessarily coercive, and, in some cases, even an interrogation becomes less coercive, if the subject begins to identify with the conceptual framework of the interrogator. The latter can be a false Stockholm syndrome
Stockholm syndrome
In psychology, Stockholm Syndrome is an apparently paradoxical psychological phenomenon wherein hostages express empathy and have positive feelings towards their captors, sometimes to the point of defending them...
context, or it can be a case where the subject actually sees that his belief system has fallacies, and he may start to share aspects of the interrogator's mindset.
One variant occurred with WWII Japanese prisoners who, perhaps having been captured while unconscious, believe that the shame of capture, in their native culture, permanently separates them from that culture.
If they are unable to commit suicide, they appeared to see themselves as now part of the interrogator's culture, and became quite cooperative. "...there was one infallible method of convincing a reluctant Japanese prisoner to tell all he knows: to tell him, via interpreters, that they will send his name and picture back to Japan. ... We might note that few Japanese ever attempt to hold anything back. Being taken prisoner is not in their handbooks. No Japanese is ever taken alive. Thus, they are not drilled in the "Name- Rank- Serial No- nothing more" routine. They usually reveal everything easily without any persuasion and seem unhappy when their lack of information does not permit them to answer a specific question. [a captured officer]...doesn't expect to return to Japan ever, has completely excluded his family and his wife from his thinking, and appears pleasantly resigned to going to the States and working there even as a prisoner for the rest of his life."
In argumentative theory, interrogation is a form of information-seeking dialogue, but also can include other kinds of dialogue, such as negotiation. In both police and intelligence interviews, there may be bargaining, where the interrogator offers incentives for the subject to reveal information. The revealed information, especially in a HUMINT context, is not necessarily about the interrogation and also may involve persuasion of the subject to speak.
Before going on to study the relationship of the interrogation to information seeking
dialogue, some account must be given of other types of dialogue related to interrogation as well. For the interrogation has a way of shifting from pure information-seeking to other types of dialogue. As an example, argumentative theory recognizes 'persuasion', in the sense meant in the persuasion dialogue, with certain strategic interrogations, the interrogator might objectively question some of the practices of the subject's side. This is not done for direct elicitation of information, but to set a new context for further interrogation in which the subject might question some of his own loyalties and assumptions. In the case of the Japanese prisoners of the US, they began to operate in that new context.
Debriefing
Debriefing involves getting cooperating human sources to satisfy intelligence requirements, consistent with the rules, laws, and policies of the HUMINT organization. People being debriefed are usually willing to cooperate, although it is possible to obtain information through casual conversation. Debriefing may be conducted at all echelons and in all operational environments. While it is usually face-to-face, it can be done by voice, video, or computer messaging.Types of people being interviewed include both "tasked" and "non-tasked" individuals. Tasked individuals are, in some way, part of the interviewer's organization.
Special reconnaissance
Special reconnaissance is conducted by small units of highly trained military personnel, usually from special forces units or military intelligence organisations, who operate behind enemy lines, avoiding direct combat and detection by the enemy. As a role, SR is distinct from commando operations,...
)
Tasked personnel giving brief reports of the enemy use the SALUTE technique. More formal or extensive debriefing methods are used for obtaining specialized or complex information.
Other than talking to tasked personnel, there is a tendency for some HUMINT collectors to regard debriefing as a waste of time. The approach to a voluntary source needs to be quite different than even to a cooperative prisoner, especially if the interrogator has reason to believe the source is knowledgeable. While a subject may be a volunteer, a refugee or displaced person is likely to have some of the fears and uncertainty undergone by POWs. Active listening and sympathy can pay great benefits, especially in the areas of love of family, and anger at those who made them homeless.
The HUMINT collector should allow specialized or senior sources more latitude to interpose their opinions and evaluations. Prior to the meeting, collectors need to examine all available information, to have an idea of the subject's personality and motivations when beginning to talk to them. It also may require unobtrusive observation of the subject to establish such things as patterns of activity and likes and dislikes. The closer the interview environment can be to the customary surroundings of the subject, the more comfortable and cooperative the source may be.
One example of source that should have latitude are trained foreign internal defense
Foreign internal defense
Foreign internal defense is a term used by a number of Western militaries, including the United States, France and the United Kingdom, to describe an approach to combating actual or threatened insurgency in a foreign state called the Host Nation . The term counter-insurgency is more commonly used...
(FID) or unconventional warfare
Unconventional warfare
Unconventional warfare is the opposite of conventional warfare. Where conventional warfare is used to reduce an opponent's military capability, unconventional warfare is an attempt to achieve military victory through acquiescence, capitulation, or clandestine support for one side of an existing...
(UW) personnel that work with local residents, or military forces, on a routine basis. Such people may very well themselves have HUMINT and/or CI training; US Special Forces groups have two-man HUMINT/CI teams that can augment operational detachments.
Historically, after the WWII experience of resistance leaders such as the Jedburgh teams
Operation Jedburgh
Operation Jedburgh was a clandestine operation during World War II, in which personnel of the British Special Operations Executive, the U.S...
, occurred to various commanders that soldiers trained to operate as guerillas would have a strong sense of how to fight guerillas. Even before specialist FID/UW units were constituted, organizations such as Military Assistance Advisory Group
Military Assistance Advisory Group
Military Assistance Advisory Group is a designation for American military advisers sent to assist in the training of conventional armed forces of Third World countries. Before and during the Vietnam War, there were three of these groups operating in Southeast Asia...
s, as in Greece just after WWII, also had extensive local knowledge. Before the partition of French Indochina in 1954, French Groupement de Commandos Mixtes Aéroportés
Groupement de Commandos Mixtes Aéroportés
The Groupement de Commandos Mixtes Aéroportés commonly referred as just GCMA, was the "Action Service" of the SDECE French counter-intelligence service active during the Cold War...
(GCMA) took on this role, drawing on French experience with the Jedburgh teams. GCMA, operating in Tonkin and Laos under French intelligence, was complemented by Commandos Nord Viêt-Nam in the North. In these missions, the SOF teams lived and fought with the locals.
United States Army Special Forces
United States Army Special Forces
The United States Army Special Forces, also known as the Green Berets because of their distinctive service headgear, are a special operations force tasked with six primary missions: unconventional warfare, foreign internal defense, special reconnaissance, direct action, hostage rescue, and...
, U.S. Marine Corps
United States Marine Corps
The United States Marine Corps is a branch of the United States Armed Forces responsible for providing power projection from the sea, using the mobility of the United States Navy to deliver combined-arms task forces rapidly. It is one of seven uniformed services of the United States...
Combined Action Program
Combined action program
Drawing from previous experience in "small wars", the United States Marine Corps operated the Combined Action Program during the Vietnam War, from 1965 to 1971. "The Combined Action Platoon's genesis was not a deliberate plan from a higher headquarters, rather, it was a solution to one infantry...
(CAP) program personnel (originally in Vietnam, but now in Iraq)
and various training detachments are apt to have valuable and structured information.
In all cases, the more knowledgeable the interrogator is to the volunteer, the better the result is likely to be. A collector does not need to keep the same level as control as in a hostile interrogation. Sometimes, admitting ignorance of a custom, and respectfully asking for explanation, will trigger a flow of information.
While it takes sophistication, the best general approach to willing subjects is a planned elicitation of information, always with a specific goal in mind. The key to elicitation is the establishment of a rapport between the elicitor and the source, normally based on shared interests. In the initial stages of an elicitation, the collector confines his conversations to innocuous subjects such as sports and social commentary. Dependent on the value of the source, the collection environment, and the security consciousness of the subject, the HUMINT specialist will then shift to a more focused topic.
Once in that mode, elicit the information by continuing to ask for clarification, with questions of the form "I agree, however, what did you mean by....?") or expressing a hypothetical situation. The focused discussion can involve mild flattery and interest in the conversation, or, in a much more delicate approach, selectively challenging statements or introducing new information to show knowledge and stimulate more responses.
Interrogation
As opposed to debriefing, the subject of interrogationInterrogation
Interrogation is interviewing as commonly employed by officers of the police, military, and Intelligence agencies with the goal of extracting a confession or obtaining information. Subjects of interrogation are often the suspects, victims, or witnesses of a crime...
is not necessarily cooperating with the obtaining of information by the organization. The subject is normally in custody, although the legal circumstances may be such that an uncooperative subject may be able to leave.
Examples of subjects being interrogated include POWs, individuals detained by patrol as not being from the area, and a thief arrested by the civilian police.
Interrogation is a skilled technique, which often involves building rapport with the subject. In an intelligence context, interrogators should be trained specialists, although they may work with linguists and subject matter experts.
Regardless of whether the interview is voluntary or involuntary, the interrogator needs to keep the initiative. To keep the initiative, the interrogator may not need to be harsh. Indeed, the many successful interrogators are formally polite within the subject's cultural traditions. If, in societies with a strong host-guest tradition, the interrogator takes the role of host, that can allow polite domination of the conversation.
The interrogation process itself is a HUMINT collection, not analysis, technique. It may well be that the interrogator, after the interview, does analysis, cross-checking statements made against name indices and "wiring diagrams" of social networks. The interrogator checks his notes against the finished report to ensure that the report contains and identifies the information as heard, seen, or assumed by the source
Planning the initial interview
While the actual interview technique will vary with the attitude of the subject and the needs of the interviewer's service, the interrogator should develop a basic plan for the first interview. This might be put into a paper folder along with documents (or copies) associated with the subject, or, if available, it can go into a HUMINT database so other interrogators, analysts, cultural and language specialists, can review it. Reviews can help plan the current interview, or give ideas to other interrogators for other interviews.The basic elements to collect are:
- Any urgent HUMINT collection requirements
- Serial number of EPW/detainee to be questioned.
- Location and time for the questioning.
- Primary and alternate approaches.
- Questioning plan including topics to be covered and the planned sequence of these topics.
- Prepared questions for unfamiliar or highly technical topics.
- Method of recording and reporting information obtained
- Linguist support, if needed
- Additional general or technical interrogators needed
"The preliminary interview is not intended to obtain intelligence, but only to enable the interrogators to make a firm assessment of the character and type of subject with whom they will have to deal."
How much psychological pressure to use, how many symbols of dominance are appropriate to use, require great judgment. Some classic interviewing techniques, without threatening the subject, make him uncomfortable, as, for example, having "interrogators - preferably two of them - seated behind a table at the far end of a long room, so that the subject after entering will have some distance to walk before taking his chair in front of them. This device will enable them to observe his poise and manner, and may often quite unsettle the subject. In this pressure-oriented technique, the interrogators should sit with their backs to the main source of light in order to obscure their faces, veil their expressions, and place a strain on the prisoner. The subject can be placed under further strain by providing him an uncomfortable chair, say one with a polished seat and shortened front legs so that he tends to slide off it, or one with wobbly legs.
"On the other hand, an opposite technique has sometimes been successful: the prisoner is made so comfortable, after a hearty lunch with beer, that he drops his guard in drowsiness.
When conducting military source operations, the location of the questioning will have psychological effects on the source. The questioning location should be chosen and set up to correspond to the effect that the HUMINT collector wants to project and his planned approach techniques. For example, meeting in a social type situation such as a restaurant may place the source at ease. Meeting in an apartment projects informality while meeting in an office projects more formality. Meeting at the source's home normally places him at a psychological advantage, while meeting in the HUMINT collector's work area gives the collector a psychological edge. The HUMINT collector should consider the status and level of the source, security, the workspace available, furnishings, the amount of lighting provided, and the ability to heat or cool the room as needed.
Characteristics of the interrogator(s)
Interrogation is an interaction, and, even before considering the different attitudes the subject may have, the interrogator needs to know his own style, strengths and weaknesses. He needs to judge if he needs cultural advice, how to handle language issues, and if he needs specialist help.The HUMINT collector must also consider the physical conditions of the source and himself. After extended operations, there may be a limit on how long either the HUMINT collector or source can concentrate on a given subject.
Support needs
If the interrogator thinks that offering incentives will help, he must decide what they are and how they are obtained. If incentives were promised in earlier interviews, the collector must know if they were delivered. If they were not, the interrogator needs to plan how the failure to deliver may interfere with any trust built, and how to correct the problem.The HUMINT collector must decide if he will need additional support including analytical, technical, or interpreter support. On rare occasions, it may be desirable for the HUMINT collector to seek polygraph support or support from a Behavioral Science Consultant (BSC). BSCs are authorized to make psychological assessments of the character, personality, social interactions, and other behavioral characteristics of interrogation subjects and advise HUMINT collectors of their assessments, as needed.
Attitudes of the subject
The basic attitude of the subject will help define the approach to the interview. There are four primary factors that must be considered when selecting tentative approaches:- The source's mental and physical state. Is the source injured, angry, crying, arrogant, cocky, or frightened?
- The source's background. What is the source's age and level of military or civilian experience? Consider cultural, ethnic, and religious factors.
- The objective of the HUMINT collection. How valuable is the source's potential information? Is it beneficial to spend more effort convincing this source to talk?
- The HUMINT collector himself. What abilities does he have that can be brought into play? What weaknesses does he have that may interfere with the HUMINT collection? Are there social or ethnic barriers to communication? Can his personality adapt to the personality of the source?
Cooperative and friendly
A cooperative and friendly source offers little resistance to the interrogation and normally speaks freely on almost any topic introduced, other than that which will tend to incriminate or degrade him personally.
To obtain the maximum amount of information from cooperative and friendly sources, the interrogator takes care to establish and to preserve a friendly and cooperative atmosphere by not inquiring into those private affairs which are beyond the scope of the interrogation. At the same time, he must avoid becoming overly friendly and losing control of the interrogation. The interrogator, however, may need to get expert advice on the customs of the subject's culture. While Americans might not spend time inquiring about the journey to the place of the interrogation, the health of one another's family, etc., not to do so is extremely impolite in some cultures. Not following cultural norms may transform a cooperative subject into a silent one.
For example, Arab cultural norms, reasonable to follow in a friendly conversation with a subject of that culture, do, often in ceremonial terms, speak of family. Handshakes are traditional at the start and end of the meeting.
Neutral and nonpartisan
A neutral and nonpartisan source is cooperative to a limited degree. He normally takes the position of answering questions asked directly, but seldom volunteers information. In some cases, he may be afraid to answer for fear of reprisals by the enemy. This often is the case in low-intensity conflict (LIC) where the people may be fearful of insurgent reprisals. With the neutral and nonpartisan source, the interrogator may have to ask many specific questions to obtain the information required.
Hostile and antagonistic
A hostile and antagonistic source is most difficult to interrogate. In many cases, he refuses to talk at all and offers a real challenge to the interrogator. An interrogator must have self-control, patience, and tact when dealing with him.
Inexperienced interrogators may do well to limit their interview, and pass the subject to a more senior interrogator. When handing off the subject, the next interrogator will find it very useful to have any clues why the subject is being hostile.
"The recalcitrant subject of an intelligence interrogation must be "broken" but broken for use like a riding horse, not smashed in the search for a single golden egg."
No two interrogations are the same. Each interrogation is thus carefully tailored to the measure of the individual subject. The standard lines of procedure, however, may be divided into four parts:
-
- arrest and detention
- preliminary interview and questioning
- intensive examination
- exploitation.
The first three steps, which emphatically do not involve torture, can be combined and called the "softening-up" process. If the subject is using a cover story, it may be broken by softening-up.
"Showing some subjects up as liars is the very worst thing to do, because their determination not to lose face will only make them stick harder to the lie. For these it is necessary to provide loopholes by asking questions which let them correct their stories without any direct admission to lying".
The questioning itself can be carried out in a friendly, persuasive manner, from a hard, merciless and threatening posture, or with an impersonal and neutral approach. In order to achieve the disconcerting effect of alternation among these attitudes it may be necessary to use as many as four different interrogators playing the following roles, although one interrogator may sometimes double in two of them:
-
- the cold, unfeeling individual whose questions are shot out as from a machine-gun, whose voice is hard and monotonous, who neither threatens nor shows compassion.
- the bullying interrogator who uses threats, insults and sarcasm to break through the subject's guard by making him lose his temper or by exhausting him.
- the ostensibly naive and credulous questioner, who seems to be taken in by the prisoner's story, makes him feel smarter than the interrogator, gives him his rope and builds up false confidence which may betray him.
- the kind and friendly man, understanding and persuasive, whose sympathetic approach is of decisive importance at the climactic phase of the interrogation. He is most effectively used after a siege with the first and second types, or after a troubled sleep following such a siege.
Planning additional interviews
This can be part of softening-up, or part of the exploitation phase. "When the cover story and the will to resist have been broken, when the subject is ready to answer a series of carefully prepared questions aimed at an intelligence target, the exploitation can begin, often in a veiled spirit of cooperation and mutual assistance. At this stage the interrogation may for example be moved to an office assigned the subject, where he might even be left alone for a few minutes to show that he is being trusted and that there is something constructive for him to do. This feeling of trust and responsibility can be very important to a broken subject, because he may now have suicidal inclinations; he must be given something to occupy his mind and keep him from too much introspection.Which course is better will depend on the subject's character, the way he was broken, and his present attitude toward those who have been handling him. Sometimes only a fresh interrogator can get real cooperation from him. Sometimes, on the other hand, he is so ashamed of having broken that he is unwilling to expose himself further and wants to talk only to his original questioner. And sometimes he has built up a trustful and confiding relationship with his interrogator which should not be destroyed by the introduction of another personality.
Principles of questioning
The HUMINT collector adopts an appropriate persona based on his appraisal of the source but remains alert for verbal and non-verbal clues that indicate the need for a change in the approach techniques. The amount of time spent on this phase will depend mostly on the probable quantity and value of information the source possesses, the availability of other sources with knowledge on the same topics, and available time. At the initial contact, a businesslike relationship should be maintained. As the source assumes a cooperative attitude, a more relaxed atmosphere may be advantageous. The HUMINT collector must carefully determine which of the various approach techniques to employ.If a source cooperates, his or her motivations vary. They can range from altruism to personal gain; they may be based on logic or emotion. From a psychological standpoint, the HUMINT collector must be cognizant of the following behaviors. People tend to—
- Want to talk when they are under stress and respond to kindness and understanding during trying circumstances. For example, enemy soldiers who have just been captured have experienced a significant stress-producing episode. The natural inclination is for people to want to talk about this sort of experience. If the EPW has been properly segregated and silenced, the HUMINT collector will be the first person the EPW has a chance to talk to. This is a powerful tool for the collector to use to get the subject talking. The desire to talk may also be manifested in refugees, DPs, and even local civilians when confronted by an unsettled situation.
- Show deference when confronted by superior authority. This is culturally dependent but in most areas of the world people are used to responding to questions from a variety of government and quasi-government officials.
- Operate within a framework of personal and culturally derived values. People tend to respond positively to individuals who display the same value system and negatively when their core values are challenged.
- Respond to physical and, more importantly, emotional self-interest. This may be as simple as responding to material rewards such as extresponding to support in rationalizing guilt.
- Fail to apply or remember lessons they may have been taught regarding security if confronted with a disorganized or strange situation.
- Be more willing to discuss a topic about which the HUMINT collector demonstrates identical or related experience or knowledge.
- Appreciate flattery and exoneration from guilt.
- Attach less importance to a topic if it is treated routinely by the HUMINT collector.
- Resent having someone or something they respect belittled, especially by someone they dislike.
Building rapport
"Establish and maintain a rapport between the HUMINT collector and the source. Rapport is a condition established by the HUMINT collector that is characterized by source confidence in the HUMINT collector and a willingness to cooperate with him. This does not necessarily equate to a friendly atmosphere. It means that a relationship is established and maintained that facilitates the collection of information by the HUMINT collector. The HUMINT collector may establish a relationship as superior, equal, or even inferior to the source. The relationship may be based on friendship, mutual gain, or even fear.If he does introduce himself, normally he will adopt a duty position and rank supportive of the approach strategy selected during the planning and preparation phase. The HUMINT collector must select a rank and duty position that is believable based on the HUMINT collector's age, appearance, and experience. A HUMINT collector may, according to international law, use ruses of war to build rapport with interrogation sources, and this may include posing or "passing himself off" as someone other than a military interrogator. However, the collector must not pose as—
- A doctor, medic, or any other type of medical personnel.
- Any member of the International Committee of the Red Cross (ICRC) or its affiliates. Such a ruse is a violation of treaty obligations.
- A chaplain or clergyman.
- A journalist.
- A member of the civilian government, such as a Member of Parliament.
"The attitude of the interrogators at the preliminary interview should usually be correct, studiously polite, and in some cases even sympathetic. It is imperative that they keep their tempers both now and throughout the interrogation. The prisoner may be given the true reason for his arrest or a false one, or he may be left in doubt, according to the circumstances of the case. The interrogators must try to determine whether his usually vigorous protestations of innocence are genuine or an act, but they should not at this stage give any indication of whether they believe or disbelieve him. A clever prisoner will try to find out how much the interrogators know; they should at all costs remain poker-faced and non-committal.
"At this interview the interrogators should do as little as possible of the talking, however many questions they are anxious to have answered. The prisoner should be asked to tell his story in his own words, describe the circumstances of his arrest, give the history of some period of his life, or explain the details of his occupation. The object is to get him to talk without prompting in as much continuous narrative as possible; the more he talks the better the interrogators can assess his personality.
Use of recorders
"The interview must of course be recorded, either [as audio] or in stenographic notes." An audio recording is particularly useful if the interview requires an interpreter. If the interpreter is not a regular member of the interrogator's forces, a recording, which can be reviewed by a staff linguist, can be an important part of quality control."The interrogators must on no account try to do this job themselves; it would distract them from the critical task of framing questions and steering the course of interrogation according to the implications of the subject's replies. Whether the stenographer or recorder should be concealed or visible depends on the subject's sophistication and the state of his alert. If the recording process is not evident some subjects may become careless of what they say when they see that the interrogators are not taking notes, whereas a visible recording would alert them to be more cautious. For others, consciousness of a recording going on in full view may be unnerving, and they may betray the weak links in their stories by showing signs of distress at these points.
"At a later stage of the interrogation it may be of value to play back to the subject some part of this recording. The sound of his own voice repeating his earlier statements, particularly any with intonations of anger or distress, may make a psychological breach in his defenses."
Working with interpreters
"Without doubt an interrogator using the subject's language is in a much better position than one who has to work through an interpreter. But the interrogation skill is infinitely more important than the language skill, and a good linguist should not be substituted for a good interrogator. In the absence of an interrogator who speaks the language, an interpreter should be used, preferably one with some training in interrogation techniques. It is very important that the interpreter not only report accurately what both parties say but also reflect as faithfully as he can their inflection, tone, manner, and emphasis. He should try to become part of the furniture in the room rather than a third personality, and the interrogator should act as though he were not there."Interpreters are frequently a necessary aid to HUMINT collection. There are certain advantages to using an interpreter. The most obvious is that without an interpreter, a HUMINT collector without the proper language or necessary proficiency in that language is severely limited. Furthermore, if properly trained, briefed, and assessed, the interpreter can be a valuable assistant to the HUMINT collector.
Interpreters may have more knowledge of the local culture as well as the language, but the HUMINT manager must be cautious that the interpreter is not, for example, a member of a subculture, religion, etc., of the area, that would be offensive to the subject.
Going through an interpreter will slow the process, and also increase the chance of miscommunication. HUMINT collectors also need to be sure that local or third-country nationals are aware of security, and indeed will be loyal to the interpreter's side.
The collector should be aware of potential problems in interpretation. Some warning signs include:
- Long-to-short. If the interpreter delivers a long statement of yours as a short statement in the subject language, there are several possibilities. The interpreter may be trying to speed the interview, and the collector has to insist on accurate translation. The question may relate to a sensitive subject, perhaps even inducing fear in the interpreter.
- Short-to-long. If a brief question of the collector turns into a lengthy statement, it must be resolved that the interpreter does not have his own agenda. It is possible that the interpreter is using honorifics, indirect approach, or other culturally appropriate phrasing. There are times, however, when a translation, to control the relationship, needs to be translated exactly and without indirect language.
- Body-language shift. If the interpreter seems to change his body language or tone, the collector needs to learn the reason. This may be a justification to suspend the questioning until the interrogator can speak privately with the interpreter and find out if there is a problem. Sometimes, the change may be do to nothing more than fatigue or physical discomfort, but the interrogator must be sure that the native-language conversation has not gotten into dislike, threats, or personal connection that would bias the translation.
Special Reconnaissance Patrolling
Special reconnaissance is done by soldiers, normally uniformed, who observe enemy activity deep beyond the front lineFront line
A front line is the farthest-most forward position of an armed force's personnel and equipment - generally in respect of maritime or land forces. Forward Line of Own Troops , or Forward Edge of Battle Area are technical terms used by all branches of the armed services...
of one's own side. See special reconnaissance
Special reconnaissance
Special reconnaissance is conducted by small units of highly trained military personnel, usually from special forces units or military intelligence organisations, who operate behind enemy lines, avoiding direct combat and detection by the enemy. As a role, SR is distinct from commando operations,...
for details. Since these are highly trained specialists, they will usually have been communicating clandestinely to the HUMINT organization, and will be systematically prepared for debriefing. The debriefing may be done by HUMINT officers of their own organization, who are most familiar with their information-gathering techniques. Some of those techniques may be extremely sensitive and held on a need-to-know basis within the special reconnaissance organization. They operate significantly farther than the furthest forward friendly scouting and surveillance
Surveillance
Surveillance is the monitoring of the behavior, activities, or other changing information, usually of people. It is sometimes done in a surreptitious manner...
units; they may be tens to hundreds of kilometers deeper. They may enter the area of operations in many ways.
Their mission is not to engage in direct combat. It may be to observe and report, or it may include directing air or artillery attacks on enemy positions. If the latter is the case, the patrol still tries to stay covert; the idea is that the enemy obviously knows they are being attacked, but not who is directing fire.
Espionage
EspionageEspionage
Espionage or spying involves an individual obtaining information that is considered secret or confidential without the permission of the holder of the information. Espionage is inherently clandestine, lest the legitimate holder of the information change plans or take other countermeasures once it...
is the collection of information by people either in a position of trust for the enemy, or with access to people with such access. The process of recruiting such individuals and supporting their operations is the HUMINT discipline of agent handling
Agent handling
In intelligence organizations, agent handling is the management of agents, principal agents, and agent networks by intelligence officers typically known as case officers.-Human intelligence:...
.
It may be possible for an agent handler to meet directly with the agent and debrief him. More commonly, agents send messages to the organization for which they work, by radio, Internet, or by leaving the messages in a hard-to-find place. The latter technique, called a dead drop
Dead drop
A dead drop or dead letter box is a method of espionage tradecraft used to pass items between two individuals by using a secret location and thus does not require them to meet directly. Using a dead drop permits a Case Officer and his Agent to exchange objects and information while maintaining...
, will have either a courier
Courier
A courier is a person or a company who delivers messages, packages, and mail. Couriers are distinguished from ordinary mail services by features such as speed, security, tracking, signature, specialization and individualization of express services, and swift delivery times, which are optional for...
or the agent handler retrieve them in a clandestine
Clandestine operation
A clandestine operation is an intelligence or military operation carried out in such a way that the operation goes unnoticed.The United States Department of Defense Dictionary of Military and Associated Terms defines "clandestine operation" as "An operation sponsored or conducted by governmental...
manner. These are examples of espionage tradecraft.
Analyzing relationships among HUMINT subjects
After interviews, be they debriefings or interrogations, there is likely to be data about other people with whom the subject has had contact or knows about. These data are focused on human relationship networks, not, for example, on military information that the subject knows.Once information is obtained, it is put into an organized form. Very frequently, information obtained at one interview may help structure the next interview with the same person, or with another subject.
Identifying other people of interest
During interviews, a subject is apt to mention things about other people, or be prompted in a seemingly conversational way.Social networks
A first interview could begin with a villager named Anna. The interviewer notices that she is wearing a very attractive scarf, and inquires about it, careful to avoid customs that might obligate the wearer to give him the object he admired. She said "Thank you. I bought it from the silk man."
Anna responds, "No, the silk man is not of the village. I do not know his name."

"Yes, Chino has excellent trees. It's too bad only one of his sons, Enzo, stayed on the farm. He misses his wandering son who sells cloth to women."
Confirming Anna's statement that the silk man is an outsider, the interviewer seeks confirmation. "Is that the silk man?"
"No, the silk man is Hassan, but only visits the village. Gregory's son Fritz sells wool."
"Do you know the sons of Diana and Chino?"
"Oh yes! I ran a long time to get Iliana the midwife to come. She delivered both his sons."
The interviewer sips his tea and asks, "Midwives are so valuable. Yet what if a baby is coming in wrong, and Iliana cannot get it?"
"Iliana's husband, Justinian, has a truck. Iliana will decide whether he should go get the doctor, or bring the mother and herself to the doctor."

"Anna, I forgot to ask. Who is your husband?"
"I thought everyone knew that Homer and I are such lovers. You must be blind!" The culturally sensitive interviewer laughed, and agreed he needed new glasses.

Operational network "wiring diagram"
Much modern interest in tracking networks of people are relevant to guerilla operations and terrorist networks, two loose categories that do not completely overlap. When examining the overall structure of terrorist groups, there are two general categories of organization: networked and hierarchical. A terrorist group may employ either type or a combination of the two models. Newer groups tend towards organizing or adapting to the possibilities inherent in the network model. Ideology can have an effect on internal organization, with strict Leninist or Maoist groups tending towards centralized control and hierarchical structure. Whether the organizational model is hierarchical or not, the operational personnel almost invariably use the cell system for security.One relevant study looks at modeling terrorist networks in a manner similar to other systems that "exhibit regularity but not periodicity (i.e., locally random, but globally defined).
Their model focuses at the "mid-range", "not at the level of state leadership, and not at the level of mapping and predicting the behavior of each individual terrorist, but rather at an intermediate or organizational level"... Much as vulnerability analysis of connectionless packet networks such as the Internet
concentrates on the nodes whose loss would most interfere with connectivity, the study here looks for the "pattern of connections surrounding a node that allows for wide network reach with minimal direct ties. "Structural holes" at the intersection of flows across knowledge communities position unique and superior nodes. It is the individuals spanning these "internal holes of opportunity" that impact the network's functioning and performance. The implicit corollary of this is that if a small number of these critical nodes can be identified and "clipped" from the network, then command signals will not be able to propagate through the system."
In the 9/11 case, the pilots were such key nodes, once the US operational groups were in-country and operating. Taking the observation of centrality a step farther, COMINT can complement HUMINT in finding the nodes of a geographically dispersed human network.
Obstacles to development of HUMINT capabilities
The following observations are drawn from the article by Lawrence Wright who interviews Director of National Intelligence John Michael McConnell.Inability to recruit people who are different due to a misperception of security risk factors
To develop HUMINT agents it is necessary to recruit HUMINT controlling officers with native foreign-language skills. However, the U.S. Security clearanceSecurity clearance
A security clearance is a status granted to individuals allowing them access to classified information, i.e., state secrets, or to restricted areas after completion of a thorough background check. The term "security clearance" is also sometimes used in private organizations that have a formal...
process has several problems:
- It is biased against first-generation immigrants with active relationships to their former country.
- It is biased against non-heterosexuals. (For overview see Wikipedia article Sexual orientation and military serviceSexual orientation and military serviceThe military forces of the world have differing approaches to the enlistment of homosexual and bisexual individuals. The armed forces of most developed countries have now removed policies excluding non-heterosexual individuals...
.) The U.S. Army, for example, has dismissed hundreds of gays with important language skills, during a time of critical national need for Arabic linguists. This while, according to Wright's article, the FBI has gone from 8 Arabic-speaking agents to 9 in the seven years since the 9/11 attacks. - It takes up to two years to complete, longer than many immigrants are willing to put their careers on hold while waiting for a clearance.
McConnell's solution to this is to
- Shorten the clearance process to a month or less.
- Subject officers to "'life-cycle monitoring' – that is, constant surveillance".
There have been other cases in the past where it has been necessary to balance security clearance policy against national needs, for example:
- Alan TuringAlan TuringAlan Mathison Turing, OBE, FRS , was an English mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, providing a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which played a...
's homosexuality versus Britain's need for cryptanalysis. - Robert OppenheimerRobert OppenheimerJulius Robert Oppenheimer was an American theoretical physicist and professor of physics at the University of California, Berkeley. Along with Enrico Fermi, he is often called the "father of the atomic bomb" for his role in the Manhattan Project, the World War II project that developed the first...
's radical politics versus US need for nuclear weapons.
DNI McConnell notes also in Wright's article that the predominant risk factor which turns officers into traitors is not ethnicity, sexuality or politics, it is money:
"'Look back at all the spies we've had in our history', he said. 'About a hundred and thirty. How many did it for money? A hundred and twenty-eight.'"
For example,
- Philip AgeePhilip AgeePhilip Burnett Franklin Agee was a Central Intelligence Agency case officer and writer, best known as author of the 1975 book, Inside the Company: CIA Diary, detailing his experiences in the CIA. Agee joined the CIA in 1957, and over the following decade had postings in Washington, D.C., Ecuador,...
received $1 million from Cuban intelligence service to publicize the names of CIACentral Intelligence AgencyThe Central Intelligence Agency is a civilian intelligence agency of the United States government. It is an executive agency and reports directly to the Director of National Intelligence, responsible for providing national security intelligence assessment to senior United States policymakers...
agents as part of an active measuresActive measuresActive Measures were a form of political warfare conducted by the Soviet security services to influence the course of world events, "in addition to collecting intelligence and producing politically correct assessment of it". Active measures ranged "from media manipulations to special actions...
campaign by the KGBKGBThe KGB was the commonly used acronym for the . It was the national security agency of the Soviet Union from 1954 until 1991, and was the premier internal security, intelligence, and secret police organization during that time.The State Security Agency of the Republic of Belarus currently uses the...
. - Israel Defense ForcesIsrael Defense ForcesThe Israel Defense Forces , commonly known in Israel by the Hebrew acronym Tzahal , are the military forces of the State of Israel. They consist of the ground forces, air force and navy. It is the sole military wing of the Israeli security forces, and has no civilian jurisdiction within Israel...
psychiatrist David Shamir "attempted to make contact with the Iranian Foreign Ministry, Hamas officials, and the Russian intelligence service, the FSB, with the intention of selling them classified information which he came upon during his military service". While his claimed motivation was political, the bottom line was still money (emphasis added in quote):
- "Shamir said his prime motivation for his actions was what he viewed as the continued breakdown of the state's social fabric. 'The idea was to save my life and that of my son and the last years of my parents' lives, and to have things happen so that we can really be saved,' he said. The thinking was that I would receive money which I would use to attain asylum for me, my son, and my family, and to enable them to live as reasonably as possible, not in Iran, not in Lebanon, but rather in a European country.' "
Inability to trust people who are different due to failure to innovate in technical OPSEC
Wright claims that
"Much of the intelligence community is technophobic and is also hamstrung by security concerns. Only recently have BlackBerryBlackBerryBlackBerry is a line of mobile email and smartphone devices developed and designed by Canadian company Research In Motion since 1999.BlackBerry devices are smartphones, designed to function as personal digital assistants, portable media players, internet browsers, gaming devices, and much more...
s made their way into some agencies, and many offices don't even have Internet connections."
Hence it is difficult to institute technical controls that would allow the organization to effectively compartimentalize the knowledge of officers in the organization so that even moderately untrusted people could serve. I.e., in many cases of "moles" or internal spies, low-level spies have had access to huge volumes of secret data. This would not be possible if adequate technical measures were instituted to effectively compartmentalize information access on a more finely categorized and motivated need-to-know basis. In other words, there is a so far lost opportunity to use technical measures to improve operational security while at the same time allowing a broader range of people to serve. Another aspect of this would be to automatically filter information "down to" and tailored to a specific subject-matter need-to-know characterization of the requesting individual.
Inability to share information across the community due to operational technophobia
A third obstacle to HUMINT and intelligence analysisIntelligence analysis
Intelligence analysis is the process of taking known information about situations and entities of strategic, operational, or tactical importance, characterizing the known, and, with appropriate statements of probability, the future actions in those situations and by those entities...
in general is effective information sharing across the intelligence community
Intelligence community
Intelligence community may refer to* Bangladeshi intelligence community* Croatian intelligence community * Israeli intelligence community* Italian intelligence community, see SISMI...
. Wright's article notes that
- "the community still relies on more than thirty online networks and eighty databases, most of which are largely inaccessible to one another."
Lack of information sharing has been partly addressed technically by adding new information-sharing tools
- IntellipediaIntellipediaIntellipedia is an online system for collaborative data sharing used by the United States Intelligence Community . It was established as a pilot project in late 2005 and formally announced in April 2006 and consists of three wikis running on JWICS, SIPRNet, and Intelink-U...
, using MediaWikiMediaWikiMediaWiki is a popular free web-based wiki software application. Developed by the Wikimedia Foundation, it is used to run all of its projects, including Wikipedia, Wiktionary and Wikinews. Numerous other wikis around the world also use it to power their websites...
software with additional security features. - A-SpaceUS intelligence community A-SpaceThe United States Intelligence Community A-Space, or Analytic Space, is a project from the Office of the Director of National Intelligence's Office of Analytic Transformation and Technology to develop a common collaborative workspace for all analysts from the USIC...
, "based on sites such as MySpaceMySpaceMyspace is a social networking service owned by Specific Media LLC and pop star Justin Timberlake. Myspace launched in August 2003 and is headquartered in Beverly Hills, California. In August 2011, Myspace had 33.1 million unique U.S. visitors....
and FacebookFacebookFacebook is a social networking service and website launched in February 2004, operated and privately owned by Facebook, Inc. , Facebook has more than 800 million active users. Users must register before using the site, after which they may create a personal profile, add other users as...
– in which analysts post their current projects as a way of creating social networks." - The Library of National Intelligence, which "is an online digest of official reports that will soon provide analysts who use it with tips, much the way AmazonAmazon.comAmazon.com, Inc. is a multinational electronic commerce company headquartered in Seattle, Washington, United States. It is the world's largest online retailer. Amazon has separate websites for the following countries: United States, Canada, United Kingdom, Germany, France, Italy, Spain, Japan, and...
and iTunesITunesiTunes is a media player computer program, used for playing, downloading, and organizing digital music and video files on desktop computers. It can also manage contents on iPod, iPhone, iPod Touch and iPad....
offer recommendations to their customers."
However, Wright notes that "These innovations have not yet made their way to the analysts and agents in the field", and "the intelligence community has only warily appropriated models whose usefulness is blindingly obvious".
See also
- Document Exploitation (DOCEX)Document Exploitation (DOCEX)Document Exploitation is the set of procedures used by the United States Armed Forces to discover, categorize, and use documents seized in combat operations. In the course of performing its missions in the War on Terrorism, members of the United States Armed Forces discover vast amounts of...
- EspionageEspionageEspionage or spying involves an individual obtaining information that is considered secret or confidential without the permission of the holder of the information. Espionage is inherently clandestine, lest the legitimate holder of the information change plans or take other countermeasures once it...
- Intelligence collection managementIntelligence collection managementIntelligence Collection Management is the process of managing and organizing the collection of intelligence information from various sources. The collection department of an intelligence organization may attempt basic validation of that which it collects, but is not intended to analyze its...
- List of intelligence gathering disciplines

