
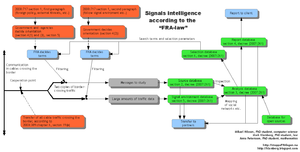
SIGINT
Encyclopedia

Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
, signals intelligence often involves the use of cryptanalysis
Cryptanalysis
Cryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key...
. Also, traffic analysis
Traffic analysis
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication. It can be performed even when the messages are encrypted and cannot be decrypted. In general, the greater the number of messages observed, or even intercepted and...
—the study of who is signaling whom and in what quantity—can often produce valuable information, even when the messages themselves cannot be decrypted.
As a means of collecting intelligence, signals intelligence is a subset
Subset
In mathematics, especially in set theory, a set A is a subset of a set B if A is "contained" inside B. A and B may coincide. The relationship of one set being a subset of another is called inclusion or sometimes containment...
of intelligence collection management
Intelligence collection management
Intelligence Collection Management is the process of managing and organizing the collection of intelligence information from various sources. The collection department of an intelligence organization may attempt basic validation of that which it collects, but is not intended to analyze its...
, which, in turn, is a subset of intelligence cycle management
Intelligence cycle management
The intelligence cycle is a investigation process used by end users , which allows that user to gather specific information, understand the possibilities of that information, and the limitations of the intelligence process.Within the context of government, military and business affairs,...
.
History
Intercepting written but encrypted communications, and extracting information, probably did not wait long after the development of writingWriting
Writing is the representation of language in a textual medium through the use of a set of signs or symbols . It is distinguished from illustration, such as cave drawing and painting, and non-symbolic preservation of language via non-textual media, such as magnetic tape audio.Writing most likely...
. A simple encryption system, for example, is the Caesar cipher
Caesar cipher
In cryptography, a Caesar cipher, also known as a Caesar's cipher, the shift cipher, Caesar's code or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number...
. Electronic interception appeared as early as 1900, during the Boer War
Boer War
The Boer Wars were two wars fought between the British Empire and the two independent Boer republics, the Oranje Vrijstaat and the Republiek van Transvaal ....
. The Boers had captured some British radios, and, since the British were the only people transmitting at the time, no special interpretation of the signals was necessary.


USS Liberty incident
The USS Liberty incident was an attack on a United States Navy technical research ship, , by Israeli Air Force jet fighter aircraft and Israeli Navy torpedo boats, on June 8, 1967, during the Six-Day War. The combined air and sea attack killed 34 crew members , wounded 170 crew members, and...
, USS Pueblo (AGER-2)
USS Pueblo (AGER-2)
USS Pueblo is an American ELINT and SIGINT Banner-class technical research ship which was boarded and captured by North Korean forces on January 23, 1968, in what is known as the Pueblo incident or alternatively as the Pueblo crisis or the Pueblo affair. Occurring less than a week after President...
incident, and the shooting down of Flight 60528, occurred during signals intelligence missions.
More technical definitions of SIGINT and its branches
In the United StatesUnited States
The United States of America is a federal constitutional republic comprising fifty states and a federal district...
and other nations involved with NATO, signals intelligence is defined as:
- A category of intelligence comprising either individually or in combination all communications intelligence (COMINT), electronic intelligence (ELINT), and Foreign instrumentation signals intelligenceForeign instrumentation signals intelligenceIn telecommunication, the term foreign instrumentation signals intelligence has the following meanings:1. Intelligence information derived from electromagnetic emissions associated with the testing and operational deployment of foreign aerospace, surface, and subsurface systems.2. Technical...
, however transmitted.
- Intelligence derived from communications, electronic, and foreign instrumentation signals.
The JCS definition may overemphasize "foreign instrumentation signals". That part should be considered in combination with measurement and signature intelligence (MASINT), which is closely linked to foreign instrumentation such as telemetry
Telemetry
Telemetry is a technology that allows measurements to be made at a distance, usually via radio wave transmission and reception of the information. The word is derived from Greek roots: tele = remote, and metron = measure...
or radionavigation. An ELINT sensor may find a radar, and then cue (i.e., guide) a COMINT sensor for listening in on the talk between the radar and its remote users. A nonspecific SIGINT sensor can cue a Frequency Domain MASINT sensor that can help identify the purpose of the signal. If MASINT cannot identify the signal, then the intelligence organization may task an IMINT
IMINT
Imagery Intelligence , is an intelligence gathering discipline which collects information via satellite and aerial photography. As a means of collecting intelligence, IMINT is a subset of intelligence collection management, which, in turn, is a subset of intelligence cycle management...
aircraft or satellite to take a picture of the source, so photo interpreters can try to understand its functions.
Being a broad field, SIGINT has many sub-disciplines. The two main ones are communications intelligence (COMINT) and electronic intelligence (ELINT). There are, however, some techniques that can apply to either branch, as well as to assist FISINT
FISINT
FISINT stands for Foreign Instrumentation Signals INTelligence from the intercept of foreign electromagnetic emissions associated with the testing and operational deployment of non-US aerospace, surface, and subsurface systems." Since it deals with signals that are not exchanged by humans, it is...
or MASINT.
Targeting
A collection system has to know to look for a particular signal. "System", in this context, has several nuances. Targeting is an output of the process of developing collection requirements:- "1. An intelligence need considered in the allocation of intelligence resources. Within the Department of Defense, these collection requirements fulfill the essential elements of information and other intelligence needs of a commander, or an agency.
- "2. An established intelligence need, validated against the appropriate allocation of intelligence resources (as a requirement) to fulfill the essential elements of information and other intelligence needs of an intelligence consumer."
Need for multiple, coordinated receivers
First, atmospheric conditions, sunspotSunspot
Sunspots are temporary phenomena on the photosphere of the Sun that appear visibly as dark spots compared to surrounding regions. They are caused by intense magnetic activity, which inhibits convection by an effect comparable to the eddy current brake, forming areas of reduced surface temperature....
s, the target's transmission schedule and antenna characteristics, and other factors create uncertainty that a given signal intercept sensor will be able to "hear" the signal of interest, even with a geographically fixed target and an opponent making no attempt to evade interception. Basic countermeasures against interception include frequent changing of radio frequency
Radio frequency
Radio frequency is a rate of oscillation in the range of about 3 kHz to 300 GHz, which corresponds to the frequency of radio waves, and the alternating currents which carry radio signals...
, polarization, and other transmission characteristics. An intercept aircraft could not get off the ground if it had to carry antennas and receivers for every possible frequency and signal type to deal with such countermeasures.
Second, locating the transmitter's position is usually part of SIGINT. Triangulation
Triangulation
In trigonometry and geometry, triangulation is the process of determining the location of a point by measuring angles to it from known points at either end of a fixed baseline, rather than measuring distances to the point directly...
and more sophisticated radio location techniques, such as time of arrival
Time of arrival
Time of arrival , also called time of flight , is the travel time of a radio signal from a single transmitter to a remote single receiver. By the relation between light speed in vacuum and the carrier frequency of a signal the time is a measure for the distance between transmitter and receiver...
methods, require multiple receiving points at different locations. These receivers send location-relevant information to a central point, or perhaps to a distributed system in which all participate, such that the information can be correlated and a location computed.
Intercept management
Modern SIGINT systems, therefore, have substantial communications among intercept platforms. Even if some platforms are clandestine, there is a broadcast of information telling them where and how to look for signals. A U.S. targeting system under development in the late 1990s, PSTS, constantly sends out information that helps the interceptors properly aim their antennas and tune their receivers. Larger intercept aircraft, such as the EP-3 or RC-135, have the on-board capability to do some target analysis and planning, but others, such as the RC-12 GUARDRAILC-12 Huron
The C-12 Huron is the military designation for a series of twin-engine turboprop aircraft based on the Beechcraft Super King Air and Beechcraft 1900. C-12 variants are used by the United States Air Force, United States Army, United States Navy and United States Marine Corps...
, are completely under ground direction. GUARDRAIL aircraft are fairly small, and usually work in units of three to cover a tactical SIGINT requirement, where the larger aircraft tend to be assigned strategic/national missions.
Before the detailed process of targeting begins, someone has to decide there is a value in collecting information about something. While it would be possible to direct signals intelligence collection at a major sports event, the systems would capture a great deal of noise, news signals, and perhaps announcements in the stadium. If, however, an anti-terrorist organization believed that a small group would be trying to coordinate their efforts, using short-range unlicensed radios, at the event, SIGINT targeting of radios of that type would be reasonable. Targeting would not know where in the stadium the radios might be, or the exact frequency they are using; those are the functions of subsequent steps such as signal detection and direction finding.
Once the decision to target is made, the various interception points need to cooperate, since resources are limited.
Knowing what interception equipment to use becomes easier when a target country buys its radars and radios from known manufacturers, or is given them as part of foreign military aid. National intelligence services keep libraries of devices manufactured by their own country and others, and then use a variety of techniques to learn what equipment is acquired by a given country.
Knowledge of physics and electronic engineering further narrows the problem of what types of equipment might be in use. An intelligence aircraft flying well outside the borders of another country will listen for long-range search radars, not short-range fire control radars that would be used by a mobile air defense. Soldiers scouting the front lines of another army know that the other side will be using radios that must be portable and not have huge antennas.
Signal detection
Even if a signal is human communications (e.g., a radio), the intelligence collection specialists have to know it exists. If the targeting function described above learns that a country has a radar that operates in a certain frequency range, the first step is to use a sensitive receiver, with one or more antennas that listen in every direction, to find an area where such a radar is operating. Once the radar is known to be in the area, the next step is to find its location.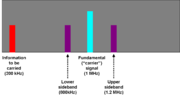
Sideband
In radio communications, a sideband is a band of frequencies higher than or lower than the carrier frequency, containing power as a result of the modulation process. The sidebands consist of all the Fourier components of the modulated signal except the carrier...
frequencies using a spectrum analyzer
Spectrum analyzer
A spectrum analyzer measures the magnitude of an input signal versus frequency within the full frequency range of the instrument. The primary use is to measure the power of the spectrum of known and unknown signals...
. Information from the spectrum analyzer is then used to tune receivers to signals of interest. For example, in this simplified spectrum, the actual information is at 800 kHz and 1.2 MHz.
Countermeasures to interception
Spread-spectrum communications is an electronic counter-countermeasures (ECCM)Electronic counter-countermeasures
Electronic counter-countermeasures is a part of electronic warfare which includes a variety of practices which attempt to reduce or eliminate the effect of electronic countermeasures on electronic sensors aboard vehicles, ships and aircraft and weapons such as missiles. ECCM is also known as...
technique to defeat looking for particular frequencies. Spectrum analysis can be used in a different ECCM way to identify frequencies not being jammed or not in use.
Direction-finding

The earliest, and still common, means of direction finding
Direction finding
Direction finding refers to the establishment of the direction from which a received signal was transmitted. This can refer to radio or other forms of wireless communication...
is to use directional antennas as goniometer
Goniometer
A goniometer is an instrument that either measures an angle or allows an object to be rotated to a precise angular position. The term goniometry is derived from two Greek words, gōnia, meaning angle, and metron, meaning measure....
s, so that a line can be drawn from the receiver through the position of the signal of interest. See HF/DF. Knowing the compass bearing, from a single point, to the transmitter does not locate it. Where the bearings from multiple points, using goniometry, are plotted on a map, the transmitter will be located at the point where the bearings intersect. This is the simplest case; a target may try to confuse listeners by having multiple transmitters, giving the same signal from different locations, switching on and off in a pattern known to their user but apparently random to the listener.
Individual directional antennas have to be manually or automatically turned to find the signal direction, which may be too slow when the signal is of short duration. One alternative is the Wullenweber
Wullenweber
The Wullenweber is a type of Circularly Disposed Antenna Array sometimes referred to as a Circularly Disposed Dipole Array . It is a large circular antenna array used for radio direction finding...
array technique. In this method, several concentric rings of antenna elements simultaneously receive the signal, so that the best bearing will ideally be clearly on a single antenna or a small set. Wullenweber arrays for high-frequency signals are enormous, referred to as "elephant cages" by their users.
An alternative to tunable directional antennas, or large omnidirectional arrays such as the Wullenweber, is to measure the time of arrival
Time of arrival
Time of arrival , also called time of flight , is the travel time of a radio signal from a single transmitter to a remote single receiver. By the relation between light speed in vacuum and the carrier frequency of a signal the time is a measure for the distance between transmitter and receiver...
of the signal at multiple points, using GPS or a similar method to have precise time synchronization. Receivers can be on ground stations, ships, aircraft, or satellites, giving great flexibility.
Modern anti-radiation missile
Anti-radiation missile
An anti-radiation missile is a missile which is designed to detect and home on an enemy radio emission source. Typically these are designed for use against an enemy radar, although jammers and even radios used for communication can also be targeted in this manner.- Air-to-Ground :Most ARM designs...
s can home in on and attack transmitters; military antennas are rarely a safe distance from the user of the transmitter.
Traffic analysis
When locations are known, usage patterns may emerge, from which inferences may be drawn. Traffic analysisTraffic analysis
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication. It can be performed even when the messages are encrypted and cannot be decrypted. In general, the greater the number of messages observed, or even intercepted and...
is the discipline of drawing patterns from information flow among a set of senders and receivers, whether those senders and receivers are designated by location determined through direction finding
Direction finding
Direction finding refers to the establishment of the direction from which a received signal was transmitted. This can refer to radio or other forms of wireless communication...
, by addressee and sender identifications in the message, or even MASINT techniques for "fingerprinting" transmitters or operators. Message content, other than the sender and receiver, is not necessary to do traffic analysis, although more information can be helpful.
For example, if a certain type of radio is known to be used only by tank units, even if the position is not precisely determined by direction finding, it may be assumed that a tank unit is in the general area of the signal. Of course, the owner of the transmitter can assume someone is listening, so might set up tank radios in an area where he wants the other side to believe he has actual tanks. As part of Operation Quicksilver
Operation Quicksilver (WWII)
In World War II, Operation Quicksilver was a sub-plan of Operation Fortitude, the 1944 deception plan designed to induce the Germans to hold troops away from Normandy in belief that the Normandy landing was only a feint and that the major invasion would come in the Pas-de-Calais...
, part of the deception
Deception
Deception, beguilement, deceit, bluff, mystification, bad faith, and subterfuge are acts to propagate beliefs that are not true, or not the whole truth . Deception can involve dissimulation, propaganda, and sleight of hand. It can employ distraction, camouflage or concealment...
plan for the invasion of Europe at the Battle of Normandy, radio transmissions simulated the headquarters and subordinate units of the fictitious First United States Army Group (FUSAG), commanded by George S. Patton
George S. Patton
George Smith Patton, Jr. was a United States Army officer best known for his leadership while commanding corps and armies as a general during World War II. He was also well known for his eccentricity and controversial outspokenness.Patton was commissioned in the U.S. Army after his graduation from...
, to make the German defense think that the main invasion was to come at another location. In like manner, fake radio transmissions from Japanese aircraft carriers, before the Battle of Pearl Harbor, were made from Japanese local waters, while the attacking ships moved under strict radio silence.
Traffic analysis need not focus on human communications. For example, if the sequence of a radar signal, followed by an exchange of targeting data and a confirmation, followed by observation of artillery fire, this may identify an automated counterbattery system. A radio signal that triggers navigational beacons could be a landing aid system for an airstrip or helicopter pad that is intended to be low-profile.
Patterns do emerge. Knowing a radio signal, with certain characteristics, originating from a fixed headquarters may be strongly suggestive that a particular unit will soon move out of its regular base. The contents of the message need not be known to infer the movement.
There is an art as well as science of traffic analysis. Expert analysts develop a sense for what is real and what is deceptive. Harry Kidder, for example, was one of the star cryptanalysts of World War II, a star hidden behind the secret curtain of SIGINT.
Electronic Order of Battle
Generating an Electronic order of battle (EOB) requires identifying SIGINT emitters in an area of interest, determining their geographic location or range of mobility, characterizing their signals, and, where possible, determining their role in the broader organizational order of battleOrder of battle
In modern use, the order of battle is the identification, command structure, strength, and disposition of personnel, equipment, and units of an armed force participating in field operations. Various abbreviations are in use, including OOB, O/B, or OB, while ORBAT remains the most common in the...
. EOB covers both COMINT and ELINT. The Defense Intelligence Agency
Defense Intelligence Agency
The Defense Intelligence Agency is a member of the Intelligence Community of the United States, and is the central producer and manager of military intelligence for the United States Department of Defense, employing over 16,500 U.S. military and civilian employees worldwide...
maintains an EOB by location. The Joint Spectrum Center (JSC) of the Defense Information Systems Agency
Defense Information Systems Agency
The Defense Information Systems Agency is a United States Department of Defense agency that provides information technology and communications support to the President, Vice President, Secretary of Defense, the military Services, and the Combatant Commands.As part of the Base Realignment and...
supplements this location database with five more technical databases:
-
- FRRS: Frequency Resource Record System
- BEI: Background Environment Information
- SCS: Spectrum Certification System
- EC/S: Equipment Characteristics/Space
- TACDB: platform lists, sorted by nomenclature, which contain links to the C-E equipment complement of each platform, with links to the parametric data for each piece of equipment, military unit lists and their subordinate units with equipment used by each unit.
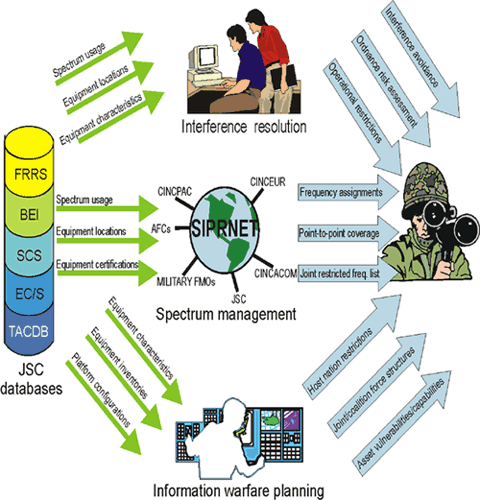
Signals intelligence units will identify changes in the EOB, which might indicate enemy unit movement, changes in command relationships, and increases or decreases in capability.
Using the COMINT gathering method enables the intelligence officer to produce an electronic order of battle by traffic analysis and content analysis among several enemy units. For example, if the following messages were intercepted:
-
- U1 from U2, requesting permission to proceed to checkpoint X.
- U2 from U1, approved. please report at arrival.
- (20 minutes later) U1 from U2, all vehicles have arrived to checkpoint X.
This sequence shows that there are two units in the battlefield, unit 1 is mobile, while unit 2 is in a higher hierarchical level, perhaps a command post. One can also understand that unit 1 moved from one point to another which are distant from each 20 minutes with a vehicle. If these are regular reports over a period of time, they might reveal a patrol pattern. Direction-finding and radiofrequency MASINT
Radiofrequency MASINT
Radiofrequency MASINT is one of the six major disciplines generally accepted to make up the field of Measurement and Signature Intelligence , with due regard that the MASINT subdisciplines may overlap, and MASINT, in turn, is complementary to more traditional intelligence collection and analysis...
could help confirm that the traffic is not deception.
The EOB buildup process is divided as following:
- Signal separation
- Measurements optimization
- Data Fusion
- Networks build-up
Separation of the intercepted spectrum and the signals intercepted from each sensors must take place in an extremely small period of time, in order to separate the deferent signals to different transmitters in the battlefield. The complexity of the separation process depends on the complexity of the transmission methods (e.g., hopping
Frequency-hopping spread spectrum
Frequency-hopping spread spectrum is a method of transmitting radio signals by rapidly switching a carrier among many frequency channels, using a pseudorandom sequence known to both transmitter and receiver...
or time division multiple access
Time division multiple access
Time division multiple access is a channel access method for shared medium networks. It allows several users to share the same frequency channel by dividing the signal into different time slots. The users transmit in rapid succession, one after the other, each using its own time slot. This...
(TDMA)).
By gathering and clustering data from each sensor, the measurements of the direction of signals can be optimized and get much more accurate then the basic measurements of a standard direction finding
Direction finding
Direction finding refers to the establishment of the direction from which a received signal was transmitted. This can refer to radio or other forms of wireless communication...
sensor. By calculating larger samples of the sensor's output data in near real-time, together with historical information of signals, better results are achieved.
Data fusion correlates data samples from different frequencies from the same sensor, "same" being confirmed by direction finding
Direction finding
Direction finding refers to the establishment of the direction from which a received signal was transmitted. This can refer to radio or other forms of wireless communication...
or radiofrequency MASINT
Radiofrequency MASINT
Radiofrequency MASINT is one of the six major disciplines generally accepted to make up the field of Measurement and Signature Intelligence , with due regard that the MASINT subdisciplines may overlap, and MASINT, in turn, is complementary to more traditional intelligence collection and analysis...
. If an emitter is mobile, direction finding, other than discovering a repetitive pattern of movement, is of limited value in determining if a sensor is unique. MASINT then becomes more informative, as individual transmitters and antennas may have unique side lobes, unintentional radiation, pulse timing, etc.
Network build-up among between each emitter (communication transmitter) to another enables creation of the communications flows of a battlefield.
COMINT
COMINT (Communications Intelligence) is a sub-category of signals intelligence that engages in dealing with messages or voice information derived from the interception of foreign communications. It should be noted that COMINT is commonly referred to as SIGINT, which can cause confusion when talking about the broader intelligence disciplines. The US Joint Chiefs of Staff defines it as "Technical information and intelligence derived from foreign communications by other than the intended recipients".COMINT, which is defined to be communications among people, will reveal some or all of the following:
-
- Who is transmitting
- Where they are located, and, if the transmitter is moving, the report may give a plot of the signal against location
- If known, the organizational function of the transmitter
- The time and duration of transmission, and the schedule if it is a periodic transmission
- The frequencies and other technical characteristics of their transmission
- If the transmission is encrypted or not, and if it can be decrypted. If it is possible to intercept either an originally transmitted cleartext or obtain it through cryptanalysis, the language of the communication and a translation (when needed).
- The addresses, if the signal is not a general broadcast and if addresses are retrievable from the message. These stations may also be COMINT (e.g., a confirmation of the message or a response message), ELINT (e.g., a navigation beacon being activated) or both. Rather than, or in addition to, an address or other identifier, there may be information on the location and signal characteristics of the responder.
Voice interception
A basic COMINT technique is to listen for voice communications, usually over radio but possibly "leaking" from telephones or from wiretaps. If the voice communications are encrypted, the encryption first must be solved through a process of introelectric diagram in order to listen to the conversation, although traffic analysisTraffic analysis
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication. It can be performed even when the messages are encrypted and cannot be decrypted. In general, the greater the number of messages observed, or even intercepted and...
(q.v.) may give information simply because one station is sending to another in a radial pattern. It is important to check for various cross sections of conversation. It is equally important to make sure that you have the correct x pattern in relation to the a2 pattern. These can be found by using the signals intelligence set given to all Naval communications officers and enlisted personnel with direct access to signals intelligence communications.
Obviously, the interceptor must understand the language being spoken. In the Second World War, the United States used volunteer communicators known as code talkers, who used languages such as Navajo
Navajo language
Navajo or Navaho is an Athabaskan language spoken in the southwestern United States. It is geographically and linguistically one of the Southern Athabaskan languages .Navajo has more speakers than any other Native American language north of the...
, Comanche
Comanche
The Comanche are a Native American ethnic group whose historic range consisted of present-day eastern New Mexico, southern Colorado, northeastern Arizona, southern Kansas, all of Oklahoma, and most of northwest Texas. Historically, the Comanches were hunter-gatherers, with a typical Plains Indian...
and Choctaw
Choctaw
The Choctaw are a Native American people originally from the Southeastern United States...
, which would be understood by few people, even in the U.S., who did not grow up speaking the language. Even within these uncommon languages, the code talkers used specialized codes, so a "butterfly" might be a specific Japanese aircraft. British forces made more limited use of Welsh
Welsh language
Welsh is a member of the Brythonic branch of the Celtic languages spoken natively in Wales, by some along the Welsh border in England, and in Y Wladfa...
speakers for the additional protection.
While modern electronic encryption does away with the need for armies to use obscure languages, it is certainly possible that guerrilla groups might use rare dialects that few outside their ethnic group would understand.
Text interception
Not all communication is in voice. Morse code interception was once very important, but Morse codeMorse code
Morse code is a method of transmitting textual information as a series of on-off tones, lights, or clicks that can be directly understood by a skilled listener or observer without special equipment...
telegraphy is now obsolescent in the western world, although possibly used by special operations forces. Such forces, however, now have portable cryptographic equipment. Morse code is still used by military forces of former Soviet Union countries.
Specialists scan radio frequencies for character sequences (e.g., electronic mail) and facsimile.
Signaling channel interception
A given digital communications link can carry thousands or millions of voice communications, especially in developed countries. Without addressing the legality of such actions, the problem of identifying which channel contains which conversation becomes much simpler when the first thing intercepted is the signaling channel that carries information to set up telephone calls. In civilian and many military use, this channel will carry messages in Signaling System 7 protocols.Retrospective analysis of telephone calls can be made from call detail records (CDR)
Call detail record
A call detail record , also known as call data record, is a data record produced by a telephone exchange or other telecommunications equipment documenting the details of a phone call that passed through the facility or device...
used for billing the calls.
Monitoring friendly communications
More a part of communications security than true intelligence collection, SIGINT units still may have the responsibility of monitoring one's own communications or other electronic emissions, to avoid providing intelligence to the enemy. For example, a security monitor may hear an individual transmitting inappropriate information over an unencrypted radio network, or simply one that is not authorized for the type of information being given. If immediately calling attention to the violation would not create an even greater security risk, the monitor will call out one of the BEADWINDOW codes used by Australia, Canada, New Zealand, the United Kingdom, the United States, and other nations working under their procedures. Standard BEADWINDOW codes (e.g., "BEADWINDOW 2") include:-
- Position: (e.g., disclosing, in an insecure or inappropriate way, "Friendly or enemy position, movement or intended movement, position, course, speed, altitude or destination or any air, sea or ground element, unit or force."
- Capabilities: "Friendly or enemy capabilities or limitations. Force compositions or significant casualties to special equipment, weapons systems, sensors, units or personnel. Percentages of fuel or ammunition remaining."
- Operations: "Friendly or enemy operation – intentions progress, or results. Operational or logistic intentions; mission participants flying programmes; mission situation reports; results of friendly or enemy operations; assault objectives."
- Electronic warfare (EW): "Friendly or enemy electronic warfare (EW) or emanations control (EMCON) intentions, progress, or results. Intention to employ electronic countermeasures (ECM); results of friendly or enemy ECM; ECM objectives; results of friendly or enemy electronic counter-countermeasures (ECCM); results of electronic support measures/tactical SIGINT (ESM); present or intended EMCON policy; equipment affected by EMCON policy."
- Friendly or enemy key personnel: "Movement or identity of friendly or enemy officers, visitors, commanders; movement of key maintenance personnel indicating equipment limitations."
- Communications security (COMSEC): "Friendly or enemy COMSEC breaches. Linkage of codes or codewords with plain language; compromise of changing frequencies or linkage with line number/circuit designators; linkage of changing call signs with previous call signs or units; compromise of encrypted/classified call signs; incorrect authentication procedure."
- Wrong circuit: "Inappropriate transmission. Information requested, transmitted or about to be transmitted which should not be passed on the subject circuit because it either requires greater security protection or it is not appropriate to the purpose for which the circuit is provided."
- Other codes as appropriate for the situation may be defined by the commander.
In WWII, for example, the Japanese Navy made possible the interception and death of the Combined Fleet commander, Admiral Isoroku Yamamoto
Isoroku Yamamoto
was a Japanese Naval Marshal General and the commander-in-chief of the Combined Fleet during World War II, a graduate of the Imperial Japanese Naval Academy and a student of Harvard University ....
, by BEADWINDOW 5 and 7 violations. They identified a key person's movement over a low-security cryptosystem.
ELINT
Electronic signals intelligence (ELINT) refers to intelligence-gathering by use of electronic sensors. Its primary focus lies on non-communications signals intelligence. The Joint Chiefs of Staff define it as "Technical and geolocation intelligence derived from foreign noncommunications electromagnetic radiations emanating from other than nuclear detonations or radioactive sources."Signal identification is performed by analyzing the collected parameters of a specific signal, and either matching it to known criteria, or recording it as a possible new emitter. ELINT data are usually highly classified, and are protected as such.
The data gathered are typically pertinent to the electronics of an opponent's defense network, especially the electronic parts such as radar
Radar
Radar is an object-detection system which uses radio waves to determine the range, altitude, direction, or speed of objects. It can be used to detect aircraft, ships, spacecraft, guided missiles, motor vehicles, weather formations, and terrain. The radar dish or antenna transmits pulses of radio...
s, surface-to-air missile
Surface-to-air missile
A surface-to-air missile or ground-to-air missile is a missile designed to be launched from the ground to destroy aircraft or other missiles...
systems, aircraft, etc. ELINT can be used to detect ships and aircraft by their radar and other electromagnetic radiation; commanders have to make choices between not using radar (EMCON
EMCON
EMCON is a military condition in which electromagnetic emissions do not exceed a set limit. This helps to avoid electronic detection. The EMCON condition can be passed via an EMCON bill, directives, OP orders, message traffic or embarked or area commander.-External links:* ....
), intermittently using it, or using it and expecting to avoid defenses. ELINT can be collected from ground stations near the opponent's territory, ships off their coast, aircraft near or in their airspace, or by satellite.
Complementary relationship to COMINT
Combining other sources of information and ELINT allows traffic analysisTraffic analysis
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication. It can be performed even when the messages are encrypted and cannot be decrypted. In general, the greater the number of messages observed, or even intercepted and...
to be performed on electronic emissions which contain human encoded messages. The method of analysis differs from SIGINT
SIGINT
Signals intelligence is intelligence-gathering by interception of signals, whether between people , whether involving electronic signals not directly used in communication , or combinations of the two...
in that any human encoded message which is in the electronic transmission is not analyzed during ELINT. What is of interest is the type of electronic transmission and its location. For example, during the Battle of the Atlantic
Second Battle of the Atlantic
The Battle of the Atlantic was the longest continuous military campaign in World War II, running from 1939 to the defeat of Germany in 1945. At its core was the Allied naval blockade of Germany, announced the day after the declaration of war, and Germany's subsequent counter-blockade. It was at its...
in World War II
World War II
World War II, or the Second World War , was a global conflict lasting from 1939 to 1945, involving most of the world's nations—including all of the great powers—eventually forming two opposing military alliances: the Allies and the Axis...
, Ultra
Ultra
Ultra was the designation adopted by British military intelligence in June 1941 for wartime signals intelligence obtained by "breaking" high-level encrypted enemy radio and teleprinter communications at the Government Code and Cypher School at Bletchley Park. "Ultra" eventually became the standard...
COMINT was not always available because Bletchley Park
Bletchley Park
Bletchley Park is an estate located in the town of Bletchley, in Buckinghamshire, England, which currently houses the National Museum of Computing...
was not always able to read the U-Boat Enigma
Enigma machine
An Enigma machine is any of a family of related electro-mechanical rotor cipher machines used for the encryption and decryption of secret messages. Enigma was invented by German engineer Arthur Scherbius at the end of World War I...
traffic. But "Huff-Duff
Huff-Duff
High-frequency direction finding, usually known by its abbreviation HF/DF is the common name for a type of radio direction finding employed especially during the two World Wars....
" (High Frequency Direction Finder) was still able to find where the U-Boat
U-boat
U-boat is the anglicized version of the German word U-Boot , itself an abbreviation of Unterseeboot , and refers to military submarines operated by Germany, particularly in World War I and World War II...
s were by analysis of radio transmissions and the positions through triangulation from the direction located by two or more Huff-Duff systems. The Admiralty
Admiralty
The Admiralty was formerly the authority in the Kingdom of England, and later in the United Kingdom, responsible for the command of the Royal Navy...
was able to use this information to plot courses which took convoys away from high concentrations of U-Boats.
Yet other ELINT disciplines include intercepting and analyzing enemy weapons control signals, or the Identification, friend or foe responses from transponders in aircraft used to distinguish enemy craft from friendly ones.
Role in air warfare
A very common area of ELINT is intercepting radars and learning their locations and operating procedures. Attacking forces may be able to avoid the coverage of certain radars, or, knowing their characteristics, electronic warfareElectronic warfare
Electronic warfare refers to any action involving the use of the electromagnetic spectrum or directed energy to control the spectrum, attack an enemy, or impede enemy assaults via the spectrum. The purpose of electronic warfare is to deny the opponent the advantage of, and ensure friendly...
units may jam radars or send them deceptive signals. Confusing a radar electronically is called a "soft kill", but military units will also send specialized missiles at radars, or bomb them, to get a "hard kill". Some modern air to air missiles also have radar homing guidance systems, particularly for use against large airborne radars.
Knowing where each surface-to-air missile and anti-aircraft artillery system is and its type means that air raids can be plotted to avoid the most heavily defended areas and to fly on a flight profile which will give the aircraft the best chance of evading ground fire and fighter patrols. It also allows for the jamming
Radar jamming and deception
Radar jamming and deception is the intentional emission of radio frequency signals to interfere with the operation of a radar by saturating its receiver with noise or false information...
or spoofing
Spoofing attack
In the context of network security, a spoofing attack is a situation in which one person or program successfully masquerades as another by falsifying data and thereby gaining an illegitimate advantage.- Spoofing and TCP/IP :...
of the enemy's defense network (see electronic warfare
Electronic warfare
Electronic warfare refers to any action involving the use of the electromagnetic spectrum or directed energy to control the spectrum, attack an enemy, or impede enemy assaults via the spectrum. The purpose of electronic warfare is to deny the opponent the advantage of, and ensure friendly...
). Good electronic intelligence can be very important to stealth operations; stealth aircraft
Stealth aircraft
Stealth aircraft are aircraft that use stealth technology to avoid detection by employing a combination of features to interfere with radar as well as reduce visibility in the infrared, visual, audio, and radio frequency spectrum. Development of stealth technology likely began in Germany during...
are not totally undetectable and need to know which areas to avoid. Similarly, conventional aircraft need to know where fixed or semi-mobile air defense systems are so that they can shut them down or fly around them.
ELINT and ESM
Electronic Support Measures (ESM) are really ELINT techniques, but the term is used in the specific context of tactical warfare. ESM give the information needed for Electronic Attack (EA) such as jamming. EA is also called Electronic Counter-Measures. ESM provides information needed for Electronic Counter-Counter Measures (ECCM), such as understanding a spoofing or jamming mode so one can change one's radar characteristics to avoid them.ELINT for meaconing
MeaconingMeaconing
Meaconing is the interception and rebroadcast of navigation signals. These signals are rebroadcast on the received frequency to confuse enemy navigation. Consequently, aircraft or ground stations are given inaccurate bearings. Meaconing is more of a concern to personnel in navigation ratings than...
is the combined intelligence and electronic warfare of learning the characteristics of enemy navigation aids, such as radio beacons, and retransmitting them with incorrect information. There are tales, perhaps apocryphal, that the meaconing was so confusing that an enemy aircraft landed, quite smoothly, at an airport of the other side.
FISINT
FISINT (Foreign instrumentation signals intelligence) is a sub-category of SIGINT, monitoring primarily non-human communication. Foreign instrumentation signals include (but not limited to) telemetryTelemetry
Telemetry is a technology that allows measurements to be made at a distance, usually via radio wave transmission and reception of the information. The word is derived from Greek roots: tele = remote, and metron = measure...
(TELINT), tracking systems, and video data links. TELINT is an important part of national means of technical verification for arms control.
Counter-ELINT
Still at the research level are techniques that can only be described as counter-ELINT, which would be part of a SEADSEAD
Suppression of Enemy Air Defenses , also known as "Wild Weasel" and "Iron Hand" operations in the United States, are military actions to suppress enemy surface-based air defenses , primarily in the first hours of an attack.One fourth of American combat sorties in recent conflicts have been SEAD...
campaign. It may be informative to compare and contrast counter-ELINT with ECCM.
SIGINT versus MASINT
Signals intelligence and measurement and signature intelligenceMeasurement and Signature Intelligence
Measurement and signature intelligence is a branch of intelligence gathering activities.MASINT, may have aspects of intelligence analysis management, since certain aspects of MASINT, such as the analysis of electromagnetic radiation received by signals intelligence are more of an analysis...
(MASINT) are closely, and sometimes confusingly, related.
The signals intelligence disciplines of communications and electronic intelligence focus on the information in those signals themselves, as with COMINT detecting the speech in a voice communication or ELINT measuring the frequency, pulse repetition rate, and other characteristics
Radar signal characteristics
A radar system uses a radio frequency electromagnetic signal reflected from a target to determine information about that target. In any radar system, the signal transmitted and received will exhibit many of the characteristics described below....
of a radar.
MASINT also works with collected signals, but is more of an analysis discipline. There are, however, unique MASINT sensors, typically working in different regions or domains of the electromagnetic spectrum, such as infrared or magnetic fields. While NSA and other agencies have MASINT groups, the Central MASINT Office is in the Defense Intelligence Agency
Defense Intelligence Agency
The Defense Intelligence Agency is a member of the Intelligence Community of the United States, and is the central producer and manager of military intelligence for the United States Department of Defense, employing over 16,500 U.S. military and civilian employees worldwide...
(DIA).
Where COMINT and ELINT focus on the intentionally transmitted part of the signal, MASINT focuses on unintentionally transmitted information. For example, a given radar antenna will have sidelobes emanating from other than the direction in which the main antenna is aimed. The RADINT (radar intelligence) discipline involves learning to recognize a radar both by its primary signal, captured by ELINT, and its sidelobes, perhaps captured by the main ELINT sensor, or, more likely, a sensor aimed at the sides of the radio antenna.
MASINT associated with COMINT might involve the detection of common background sounds expected with human voice communications. For example, if a given radio signal comes from a radio used in a tank, if the interceptor does not hear engine noise or higher voice frequency than the voice modulation
Modulation
In electronics and telecommunications, modulation is the process of varying one or more properties of a high-frequency periodic waveform, called the carrier signal, with a modulating signal which typically contains information to be transmitted...
usually uses, even though the voice conversation is meaningful, MASINT might suggest it is a deception, not coming from a real tank.
See HF/DF for a discussion of SIGINT-captured information with a MASINT flavor, such as determining the frequency to which a receiver is tuned, from detecting the frequency of the beat frequency oscillator of the superheterodyne receiver.
Defensive signals intelligence
There are a number of ways that a person or organization can defend against signals intelligence. There is a delicate balance between the level of protection and the actual threat, as expressed in the clichés about "tinfoil hats".One must begin by defining the threat. It is considerably more difficult to defend against detection that one is signaling, as opposed to defending against an opponent discovering the content of the transmitted message. Appropriate encryption can protect against content interception, but protecting against signal detection, especially with a capable opponent, requires measures to make the signal hard to detect which can also make it difficult for the intended recipient to receive the signal. Any defensive program needs to consider the nature of the threat and the capabilities of the opponent.
Strong and well-managed encryption
EncryptionEncryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
is central to the defense. The encryption process is vulnerable if the cryptographic keys
Key (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
are not strong and protected, and, on computers, if the cleartext is not deleted when not needed.
Appropriate transmission security
When using radio transmitters, use directional antennaDirectional antenna
A directional antenna or beam antenna is an antenna which radiates greater power in one or more directions allowing for increased performance on transmit and receive and reduced interference from unwanted sources....
s that have as little "spillover" into sidelobes as possible. If it is most important to hide the location of a transmitter, the minimum is to cable the antennas as far as possible away from the transmitter proper. In many circumstances, aiming the antenna upward to a satellite will help hide its location.
The amount of total transmission power needs to be minimized, and the power preferably should be split into multiple and changing frequencies using spread spectrum
Spread spectrum
Spread-spectrum techniques are methods by which a signal generated in a particular bandwidth is deliberately spread in the frequency domain, resulting in a signal with a wider bandwidth...
techniques. If possible, avoid transmitting when hostile SIGINT satellites or monitoring aircraft are overhead.
If in an urban area, avoid using regular commercial power to transmit. There are ways in which the signal can "leak" into power and ground lines. The adversary may turn off power to an area, which will tell him there is a line-operated transmitter if the transmission stops, and that there is a battery-powered transmitter if it continues.
Use highly variable transmission schedules and vary frequencies if technically possible. Also see low probability of intercept
Low probability of intercept
A low-probability-of-intercept radar is designed to be difficult to detect by passive radar detection equipment while it is searching for a target or engaged in target tracking...
.
Appropriate receiving security
If Operation RAFTEROperation RAFTER
RAFTER was a code name for the MI5 radio receiver detection technique, mostly used against clandestine Soviet agents and monitoring of domestic radio transmissions by foreign embassy personnel from the 1950s on.- Explanation :...
-style intercept is a threat, protect against this form of unintentional radiation MASINT by using optoisolators or other shielded techniques (e.g., waveguides) to bring in the radio frequency
Radio frequency
Radio frequency is a rate of oscillation in the range of about 3 kHz to 300 GHz, which corresponds to the frequency of radio waves, and the alternating currents which carry radio signals...
received signal, and shield the local oscillator
Local oscillator
A local oscillator is an electronic device used to generate a signal normally for the purpose of converting a signal of interest to a different frequency using a mixer. This process of frequency conversion, also referred to as heterodyning, produces the sum and difference frequencies of the...
and intermediate frequency
Intermediate frequency
In communications and electronic engineering, an intermediate frequency is a frequency to which a carrier frequency is shifted as an intermediate step in transmission or reception. The intermediate frequency is created by mixing the carrier signal with a local oscillator signal in a process called...
stages in the superheterodyne receiver
Superheterodyne receiver
In electronics, a superheterodyne receiver uses frequency mixing or heterodyning to convert a received signal to a fixed intermediate frequency, which can be more conveniently processed than the original radio carrier frequency...
. This technique should be far less effective against the new generation of software-defined radio
Software-defined radio
A software-defined radio system, or SDR, is a radio communication system where components that have been typically implemented in hardware are instead implemented by means of software on a personal computer or embedded computing devices...
.
Unintentional radiation on power or ground circuits is a threat here as well; use appropriate TEMPEST or other techniques.
Protection against compromising emanations
There are risks that electronic, acoustic, or other information could "leak" from a computer system or other electronic communications devices.The risk
Understanding details of the risks requires a substantial knowledge of electronics, but a simple example might serve. Many people have put a radio receiver near a computer, to listen to music as they work, and discovered that the radio suffered clicks, squeals, and other interference. These interfering signals are radiating from various parts of the computer, especially its display but often also from the power and grounding system. TEMPEST is the name for one family of protective measures against an opponent intercepting these emanations and extracting sensitive information from them.While not strictly within the scope of protecting against "leakage", a place where sensitive information is processed or discussed needs protection against hidden microphones, wiretaps, and other "bugging". Sometimes, an electronic sweep to verify TEMPEST compliance reveals the presence of hidden transmitters. Again, there is probably more suspicion than reality in most cases. A member of a crime organization, in the middle of a nasty divorce, or a foreign intelligence agent might have reason to worry, but, even with the serious questions about warrantless surveillance in the US and other countries, there is little reason for someone to go to the risk and expense of illegal surveillance on an ordinary citizen. TEMPEST is usually associated with direct electromagnetic radiation from the device, either free-space or through power and ground lines. TEMPEST generically talks about acoustic isolation, but that is fairly easily solved through physical security and noise damping, as well as searches for microphones.
There are several threats that have not been officially defined in the unclassified literature. Nevertheless, there are some informed guesses:
- NONSTOP is a threat that involves some type of coupling of compromising RF energy from a classified system, which "leaks" into an independent RF-transmitting or -recording device such as cell phones, PDAs, pager, alarm systems. Commercial AM/FM radios are not considered a risk.
- HIJACK is a similar threat of coupling, but to some type of digital computer or related equipment.
- TEAPOT is a very different vulnerability, which appears to apply to incidental audio modulation of the backscatter from an RF, typically microwave, directed into the secure area. A passive resonant cavity bug of this type was discovered in a Great Seal of the United States presented by the USSR, but containing a resonant cavity with a wall that moved with sound in the room, thus imposing frequency modulation onto the backscattered signal.
Mitigation and countermeasures
The word TEMPEST itself, and its meaning, are unclassified. Some of the techniques for measuring the compliance of a piece of equipment, or whether it is actually emitting compromising emanations, are classified. A good deal of the information has come into public view either through Freedom of Information Act queries, books talking about interception techniques, inferences drawn from partially released documents, and straightforward thinking by electronic engineers. Some documents released fully or partially under FOIA:-
- Red/Black Installation Guidance
- Specification for Shielded Enclosures
- Specification for Shielded Enclosures (partially redacted)
A number of individuals have made a hobby of ferreting out TEMPEST and related information, and firms in the broader-than-TEMPEST business of technical surveillance counter-measures
Technical Surveillance Counter-Measures
TSCM is the original United States Federal government abbreviation denoting the process of bug-sweeping or electronic countersurveillance...
(TSCM) also reveal concepts.
Protection against side channel attacks and covert channels
A side channel attackSide channel attack
In cryptography, a side channel attack is any attack based on information gained from the physical implementation of a cryptosystem, rather than brute force or theoretical weaknesses in the algorithms...
is an unintentional vulnerability of an encryption device, not related to the encryption algorithm. Potential vulnerabilities include different processing and thus transmission speeds for blocks of plaintext with certain statistical characteristics, changes in power consumption, or compromising emanations.
Covert channel
Covert channel
In computer security, a covert channel is a type of computer security attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy...
s are deliberate means to elude communications security. They send out an unauthorized signal by stealing bandwidth from a legitimate, often encrypted channel. One low-bandwidth method would be to send information by varying the inter-block transmission times. A steganographic
Steganography
Steganography is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message, a form of security through obscurity...
covert channel might use the low-order bit of pixels in a graphic image, perhaps not even consecutive pixels, in a manner that would not be obvious to a person looking at the graphic.
See also
- Canadian Forces Intelligence Branch
- Central Intelligence Agency Directorate of Science & TechnologyCentral Intelligence Agency Directorate of Science & TechnologyThe Directorate of Science and Technology is the branch of the United States Central Intelligence Agency charged with developing and applying technology to advance the United States intelligence gathering.-Origins:...
- Communications securityCommunications securityCommunications security is the discipline of preventing unauthorized interceptors from accessing telecommunications in an intelligible form, while still delivering content to the intended recipients. In the United States Department of Defense culture, it is often referred to by the abbreviation...
(COMSEC) - Geospatial intelligence
- Human intelligence (espionage)
- Imagery intelligence
- List of intelligence gathering disciplines
- Measurement and signature intelligenceMeasurement and Signature IntelligenceMeasurement and signature intelligence is a branch of intelligence gathering activities.MASINT, may have aspects of intelligence analysis management, since certain aspects of MASINT, such as the analysis of electromagnetic radiation received by signals intelligence are more of an analysis...
- National Security AgencyNational Security AgencyThe National Security Agency/Central Security Service is a cryptologic intelligence agency of the United States Department of Defense responsible for the collection and analysis of foreign communications and foreign signals intelligence, as well as protecting U.S...
- Open source intelligenceOpen source intelligenceOpen-source intelligence is a form of intelligence collection management that involves finding, selecting, and acquiring information from publicly available sources and analyzing it to produce actionable intelligence...
- Radio Reconnaissance PlatoonRadio Reconnaissance PlatoonThe Radio Reconnaissance Platoon is a specially trained element of a United States Marine Corps Radio Battalion. A Radio Reconnaissance Team was assigned as the tactical signals intelligence collection element for the Marine Corps Special Operations Command, Detachment One...
- RAF IntelligenceRAF IntelligenceIntelligence services in the Royal Air Force is delivered by Officers of the Royal Air Force Operations Support Intelligence Branch and Airmen from the Intelligence Analyst Trade and Intelligence Analyst Trade...
- Signals intelligence by alliances, nations and industriesSignals intelligence by alliances, nations and industries-Multilateral SIGINT :Many organizations, national or not, are responsible for communications security as well as SIGINT; the organization makes codes and ciphers that it hopes opponents cannot break...
- Signals intelligence in modern historySignals intelligence in modern historySIGINT is a contraction of SIGnals INTelligence. Before the development of radar and other electronics techniques, signals intelligence and communications intelligence were essentially synonymous...
- Signals intelligence operational platforms by nationSignals intelligence operational platforms by nationSignals intelligence Operational Platforms are employed by nations to collect signals intelligence, which is intelligence-gathering by interception of signals, whether between people or between machines , or mixtures of the two...
for current collection systems, - Traffic analysisTraffic analysisTraffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication. It can be performed even when the messages are encrypted and cannot be decrypted. In general, the greater the number of messages observed, or even intercepted and...
Further reading
- Bamford, JamesJames BamfordV. James Bamford is an American bestselling author and journalist who writes about United States intelligence agencies, most notably the National Security Agency.-Biography:...
, Body of Secrets: How America's NSA and Britain's GCHQ eavesdrop on the world (Century, London, 2001) - West, Nigel, The SIGINT Secrets: The Signals Intelligence War, 1900 to Today (William Morrow, New York, 1988)
- Richard J. Aldrich, GCHQ: The Uncensored Story of Britain's Most Secret Intelligence Agency (HarperCollins, London, 2010) ISBN 9780007278473
External links
- NSA's overview of SIGINT
- USAF Pamphlet on sources of intelligence
- German WWII SIGINT/COMINT
- Intelligence Programs and Systems
- The U.S. Intelligence Community by Jeffrey T. Richelson
- Secrets of Signals Intelligence During the Cold War and Beyond by Matthew Aid et. al.
- Maritime SIGINT Architecture Technical Standards Handbook
- GCHQ: Britain's Most Secret Intelligence Agency

