
Hacker culture
Encyclopedia
A hacker is a member of the computer programmer subculture
originated in the 1960s in the United States academia, in particular around the Massachusetts Institute of Technology
(MIT)'s Tech Model Railroad Club
(TMRC) and MIT Artificial Intelligence Laboratory. Some members of the "hacker" community most emphatically differentiate the term "hacker" from malicious hackers (whom they very strongly prefer to call "crackers"). Other hackers make no such distinction. The latter hackers' view that hackerdom is not inherently moral/immoral or ethical/unethical is broadly similar to the concept or attitude of a grey hat hacker.
, an influential but not universally accepted compendium of hacker slang, defines hacker as "A person who enjoys exploring the details of programmable systems and stretching their capabilities, as opposed to most users, who prefer to learn only the minimum necessary." The Request for Comments
(RFC) 1392, the Internet Users' Glossary, amplifies this meaning as "A person who delights in having an intimate understanding of the internal workings of a system, computers and computer networks in particular."
As documented in the Jargon File, these hackers are disappointed by the mass media and general public's usage of the word hacker to refer to security breakers
, calling them “crackers” instead. This includes both “good” crackers (“white hat hackers”) who use their computer security related skills and knowledge to learn more about how systems and networks work and to help to discover and fix security holes, as well as those more "evil" crackers (“black hat hackers”) who use the same skills to author harmful software (like viruses, trojans, etc.) and illegally infiltrate secure systems with the intention of doing harm to the system. The programmer subculture of hackers, in contrast to the cracker community, generally sees computer security related activities as contrary to the ideals of the original and true meaning of the hacker term that instead related to playful cleverness.
as they are now, there were multiple independent and parallel hacker subcultures, often unaware or only partially aware of each others' existence. All of these had certain important traits in common:
These sorts of subcultures were commonly found at academic
settings such as college
campus
es. The MIT Artificial Intelligence Laboratory, the University of California, Berkeley
and Carnegie Mellon University
were particularly well-known hotbeds of early hacker culture. They evolved in parallel, and largely unconsciously, until the Internet
, where a legendary PDP-10
machine at MIT, called AI, that was running ITS
, provided an early meeting point of the hacker community. This and other developments such as the rise of the free software movement
drew together a critically large population and encouraged the spread of a conscious, common, and systematic ethos. Symptomatic of this evolution were an increasing adoption of common slang and a shared view of history, similar to the way in which other occupational groups have professionalized themselves but without the formal credentialing process characteristic of most professional groups.
Over time, the academic hacker subculture has tended to become more conscious, more cohesive, and better organized. The most important consciousness-raising moments have included the composition of the first Jargon File
in 1973, the promulgation of the GNU Manifesto
in 1985, and the publication of The Cathedral and the Bazaar
in 1997. Correlated with this has been the gradual recognition of a set of shared culture heroes, including: Bill Joy
, Donald Knuth
, Dennis Ritchie
, Alan Kay
, Ken Thompson, Richard M. Stallman
, Linus Torvalds
, Larry Wall
, and Guido Van Rossum
.
The concentration of academic hacker subculture has paralleled and partly been driven by the commoditization of computer and networking technology, and has in turn accelerated that process. In 1975, hackerdom was scattered across several different families of operating system
s and disparate networks; today it is largely a Unix
and TCP/IP phenomenon, and is concentrated around various operating system
s based on free software
and open-source software development.
s that originated at MIT and at the Homebrew Computer Club
. The Hacker Ethics were chronicled by Steven Levy in Hackers: Heroes of the Computer Revolution
and in other texts.
Hacker ethics are concerned primarily with sharing, openness, collaboration, and engaging in the Hands-On Imperative.
Linus Torvalds
, one of the leaders of the Open Source movement (Known primarily for developing Linux's core), has noted in the book "The Hacker Ethic" that these principles have evolved from the known Protestant Ethics and incorporates the spirits of capitalism, as introduced in the early 20th century by Max Weber
.
 The academic hacker subculture is defined by shared work and play focused around central artifacts. Some of these artifacts are very large; the Internet
The academic hacker subculture is defined by shared work and play focused around central artifacts. Some of these artifacts are very large; the Internet
, the World Wide Web
, the GNU Project
, and the Linux
kernel
are all hacker creations, works of which the subculture considers itself primary custodian.
The academic hacker subculture has developed a rich range of symbols that serve as recognition symbols and reinforce its group identity. GNU
's Gnu
; the BSD Daemon
; Tux
, the Linux penguin
; and the Perl Camel
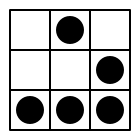
stand out as examples. The use of the glider structure
from Conway's Game of Life
as a general Hacker Emblem
has been proposed by Eric S. Raymond
.
The academic hacker subculture has an annual ceremonial day—April Fool's
. There is a long tradition of perpetrating elaborate jokes, hoax
es, pranks and fake website
s on this date, which includes the publication of the annual joke RFC
.
describes the silent composition 4′33″ by John Cage and the 14th century palindromic three-part piece "Ma Fin Est Mon Commencement" by Guillaume de Machaut
as hacks.
According to the Jargon File, the word hacker was used in a similar sense among radio amateurs in the 1950s, predating the software hacking community.
for some.
An aspect of hack value is performing feats for the sake of showing that they can be done, even if others think it is difficult. Using things in a unique way outside their intended purpose is often perceived as having hack value. Examples are using a dot matrix impact printer
to produce musical notes, using a flatbed scanner to take ultra-high-resolution photographs or using an optical mouse
as barcode reader
.
A solution or feat has hack value if it is done in a way that has finesse, cleverness or brilliance. So creativity
is an important part of the meaning. For example, picking a difficult lock
has hack value; smashing a lock does not. As another example, proving Fermat's last theorem
by linking together most of modern mathematics has hack value; solving the four color map problem
by exhaustively trying all possibilities does not (both of these long-standing mathematical challenges have now in fact been proven).
has had a special role in acculturating hackers since its origins in the early 1970s. These academic and literary works help shaped the academic hacker subculture: influential are:
Subculture
In sociology, anthropology and cultural studies, a subculture is a group of people with a culture which differentiates them from the larger culture to which they belong.- Definition :...
originated in the 1960s in the United States academia, in particular around the Massachusetts Institute of Technology
Massachusetts Institute of Technology
The Massachusetts Institute of Technology is a private research university located in Cambridge, Massachusetts. MIT has five schools and one college, containing a total of 32 academic departments, with a strong emphasis on scientific and technological education and research.Founded in 1861 in...
(MIT)'s Tech Model Railroad Club
Tech Model Railroad Club
The Tech Model Railroad Club is a student organization at the Massachusetts Institute of Technology , and one of the most celebrated model railroad clubs in the world, because of its historic role as a wellspring of hacker culture...
(TMRC) and MIT Artificial Intelligence Laboratory. Some members of the "hacker" community most emphatically differentiate the term "hacker" from malicious hackers (whom they very strongly prefer to call "crackers"). Other hackers make no such distinction. The latter hackers' view that hackerdom is not inherently moral/immoral or ethical/unethical is broadly similar to the concept or attitude of a grey hat hacker.
Definition
The Jargon FileJargon File
The Jargon File is a glossary of computer programmer slang. The original Jargon File was a collection of terms from technical cultures such as the MIT AI Lab, the Stanford AI Lab and others of the old ARPANET AI/LISP/PDP-10 communities, including Bolt, Beranek and Newman, Carnegie Mellon...
, an influential but not universally accepted compendium of hacker slang, defines hacker as "A person who enjoys exploring the details of programmable systems and stretching their capabilities, as opposed to most users, who prefer to learn only the minimum necessary." The Request for Comments
Request for Comments
In computer network engineering, a Request for Comments is a memorandum published by the Internet Engineering Task Force describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems.Through the Internet Society, engineers and...
(RFC) 1392, the Internet Users' Glossary, amplifies this meaning as "A person who delights in having an intimate understanding of the internal workings of a system, computers and computer networks in particular."
As documented in the Jargon File, these hackers are disappointed by the mass media and general public's usage of the word hacker to refer to security breakers
Hacker (computer security)
In computer security and everyday language, a hacker is someone who breaks into computers and computer networks. Hackers may be motivated by a multitude of reasons, including profit, protest, or because of the challenge...
, calling them “crackers” instead. This includes both “good” crackers (“white hat hackers”) who use their computer security related skills and knowledge to learn more about how systems and networks work and to help to discover and fix security holes, as well as those more "evil" crackers (“black hat hackers”) who use the same skills to author harmful software (like viruses, trojans, etc.) and illegally infiltrate secure systems with the intention of doing harm to the system. The programmer subculture of hackers, in contrast to the cracker community, generally sees computer security related activities as contrary to the ideals of the original and true meaning of the hacker term that instead related to playful cleverness.
History
Before communications between computers and computer users were as networkedComputer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
as they are now, there were multiple independent and parallel hacker subcultures, often unaware or only partially aware of each others' existence. All of these had certain important traits in common:
- Creating software and sharing it with each other
- Placing a high value on freedom of inquiry; hostility to secrecy
- Information-sharing as both an ideal and a practical strategy
- Upholding the right to forkFork (software development)In software engineering, a project fork happens when developers take a legal copy of source code from one software package and start independent development on it, creating a distinct piece of software...
- Emphasis on rationality
- Distaste for authority
- Playful cleverness, taking the serious humorously and their humor seriously
These sorts of subcultures were commonly found at academic
Academia
Academia is the community of students and scholars engaged in higher education and research.-Etymology:The word comes from the akademeia in ancient Greece. Outside the city walls of Athens, the gymnasium was made famous by Plato as a center of learning...
settings such as college
College
A college is an educational institution or a constituent part of an educational institution. Usage varies in English-speaking nations...
campus
Campus
A campus is traditionally the land on which a college or university and related institutional buildings are situated. Usually a campus includes libraries, lecture halls, residence halls and park-like settings...
es. The MIT Artificial Intelligence Laboratory, the University of California, Berkeley
University of California, Berkeley
The University of California, Berkeley , is a teaching and research university established in 1868 and located in Berkeley, California, USA...
and Carnegie Mellon University
Carnegie Mellon University
Carnegie Mellon University is a private research university in Pittsburgh, Pennsylvania, United States....
were particularly well-known hotbeds of early hacker culture. They evolved in parallel, and largely unconsciously, until the Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
, where a legendary PDP-10
PDP-10
The PDP-10 was a mainframe computer family manufactured by Digital Equipment Corporation from the late 1960s on; the name stands for "Programmed Data Processor model 10". The first model was delivered in 1966...
machine at MIT, called AI, that was running ITS
Incompatible Timesharing System
ITS, the Incompatible Timesharing System , was an early, revolutionary, and influential time-sharing operating system from MIT; it was developed principally by the Artificial Intelligence Laboratory at MIT, with some help from Project MAC.In addition to being technically influential ITS, the...
, provided an early meeting point of the hacker community. This and other developments such as the rise of the free software movement
Free software movement
The free software movement is a social and political movement with the goal of ensuring software users' four basic freedoms: the freedom to run their software, to study and change their software, and to redistribute copies with or without changes. The alternative terms "software libre", "open...
drew together a critically large population and encouraged the spread of a conscious, common, and systematic ethos. Symptomatic of this evolution were an increasing adoption of common slang and a shared view of history, similar to the way in which other occupational groups have professionalized themselves but without the formal credentialing process characteristic of most professional groups.
Over time, the academic hacker subculture has tended to become more conscious, more cohesive, and better organized. The most important consciousness-raising moments have included the composition of the first Jargon File
Jargon File
The Jargon File is a glossary of computer programmer slang. The original Jargon File was a collection of terms from technical cultures such as the MIT AI Lab, the Stanford AI Lab and others of the old ARPANET AI/LISP/PDP-10 communities, including Bolt, Beranek and Newman, Carnegie Mellon...
in 1973, the promulgation of the GNU Manifesto
GNU Manifesto
The GNU Manifesto was written by Richard Stallman and published in March 1985 in Dr. Dobb's Journal of Software Tools as an explanation and definition of the goals of the GNU Project, and to call for participation and support. It is held in high regard within the free software movement as a...
in 1985, and the publication of The Cathedral and the Bazaar
The Cathedral and the Bazaar
The Cathedral and the Bazaar is an essay by Eric S. Raymond on software engineering methods, based on his observations of the Linux kernel development process and his experiences managing an open source project, fetchmail. It examines the struggle between top-down and bottom-up design...
in 1997. Correlated with this has been the gradual recognition of a set of shared culture heroes, including: Bill Joy
Bill Joy
William Nelson Joy , commonly known as Bill Joy, is an American computer scientist. Joy co-founded Sun Microsystems in 1982 along with Vinod Khosla, Scott McNealy and Andy Bechtolsheim, and served as chief scientist at the company until 2003...
, Donald Knuth
Donald Knuth
Donald Ervin Knuth is a computer scientist and Professor Emeritus at Stanford University.He is the author of the seminal multi-volume work The Art of Computer Programming. Knuth has been called the "father" of the analysis of algorithms...
, Dennis Ritchie
Dennis Ritchie
Dennis MacAlistair Ritchie , was an American computer scientist who "helped shape the digital era." He created the C programming language and, with long-time colleague Ken Thompson, the UNIX operating system...
, Alan Kay
Alan Kay
Alan Curtis Kay is an American computer scientist, known for his early pioneering work on object-oriented programming and windowing graphical user interface design, and for coining the phrase, "The best way to predict the future is to invent it."He is the president of the Viewpoints Research...
, Ken Thompson, Richard M. Stallman
Richard Stallman
Richard Matthew Stallman , often shortened to rms,"'Richard Stallman' is just my mundane name; you can call me 'rms'"|last= Stallman|first= Richard|date= N.D.|work=Richard Stallman's homepage...
, Linus Torvalds
Linus Torvalds
Linus Benedict Torvalds is a Finnish software engineer and hacker, best known for having initiated the development of the open source Linux kernel. He later became the chief architect of the Linux kernel, and now acts as the project's coordinator...
, Larry Wall
Larry Wall
Larry Wall is a programmer and author, most widely known for his creation of the Perl programming language in 1987.-Education:Wall earned his bachelor's degree from Seattle Pacific University in 1976....
, and Guido Van Rossum
Guido van Rossum
Guido van Rossum is a Dutch computer programmer who is best known as the author of the Python programming language. In the Python community, Van Rossum is known as a "Benevolent Dictator For Life" , meaning that he continues to oversee the Python development process, making decisions where necessary...
.
The concentration of academic hacker subculture has paralleled and partly been driven by the commoditization of computer and networking technology, and has in turn accelerated that process. In 1975, hackerdom was scattered across several different families of operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
s and disparate networks; today it is largely a Unix
Unix
Unix is a multitasking, multi-user computer operating system originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Brian Kernighan, Douglas McIlroy, and Joe Ossanna...
and TCP/IP phenomenon, and is concentrated around various operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
s based on free software
Free software
Free software, software libre or libre software is software that can be used, studied, and modified without restriction, and which can be copied and redistributed in modified or unmodified form either without restriction, or with restrictions that only ensure that further recipients can also do...
and open-source software development.
Ethics and principles
Many of the values and tenets of the free and open source software movement stem from the hacker ethicHacker ethic
Hacker ethic is the generic phrase which describes the moral values and philosophy that are standard in the hacker community. The early hacker culture and resulting philosophy originated at the Massachusetts Institute of Technology in the 1950s and 1960s...
s that originated at MIT and at the Homebrew Computer Club
Homebrew Computer Club
The Homebrew Computer Club was an early computer hobbyist users' group in Silicon Valley, which met from March 5, 1975 to December 1986...
. The Hacker Ethics were chronicled by Steven Levy in Hackers: Heroes of the Computer Revolution
Hackers: Heroes of the Computer Revolution
Hackers: Heroes of the Computer Revolution is a book by Steven Levy about hacker culture. It was published in 1984 in Garden City, New York by Anchor Press/Doubleday...
and in other texts.
Hacker ethics are concerned primarily with sharing, openness, collaboration, and engaging in the Hands-On Imperative.
Linus Torvalds
Linus Torvalds
Linus Benedict Torvalds is a Finnish software engineer and hacker, best known for having initiated the development of the open source Linux kernel. He later became the chief architect of the Linux kernel, and now acts as the project's coordinator...
, one of the leaders of the Open Source movement (Known primarily for developing Linux's core), has noted in the book "The Hacker Ethic" that these principles have evolved from the known Protestant Ethics and incorporates the spirits of capitalism, as introduced in the early 20th century by Max Weber
Max Weber
Karl Emil Maximilian "Max" Weber was a German sociologist and political economist who profoundly influenced social theory, social research, and the discipline of sociology itself...
.
Artifacts and customs

Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
, the World Wide Web
World Wide Web
The World Wide Web is a system of interlinked hypertext documents accessed via the Internet...
, the GNU Project
GNU
GNU is a Unix-like computer operating system developed by the GNU project, ultimately aiming to be a "complete Unix-compatible software system"...
, and the Linux
Linux
Linux is a Unix-like computer operating system assembled under the model of free and open source software development and distribution. The defining component of any Linux system is the Linux kernel, an operating system kernel first released October 5, 1991 by Linus Torvalds...
kernel
Linux kernel
The Linux kernel is an operating system kernel used by the Linux family of Unix-like operating systems. It is one of the most prominent examples of free and open source software....
are all hacker creations, works of which the subculture considers itself primary custodian.
The academic hacker subculture has developed a rich range of symbols that serve as recognition symbols and reinforce its group identity. GNU
GNU Project
The GNU Project is a free software, mass collaboration project, announced on September 27, 1983, by Richard Stallman at MIT. It initiated GNU operating system development in January, 1984...
's Gnu
GNU
GNU is a Unix-like computer operating system developed by the GNU project, ultimately aiming to be a "complete Unix-compatible software system"...
; the BSD Daemon
BSD Daemon
The BSD daemon, nicknamed Beastie, is the generic mascot of BSD operating systems.-Overview:The BSD daemon is named after a software daemon, a computer program found on Unix-like operating systems, which through a play on words takes the cartoon shape of a mythical demon. The BSD daemon's nickname...
; Tux
Tux
Tux is a penguin character and the official mascot of the Linux kernel. Originally created as an entry to a Linux logo competition, Tux is the most commonly used icon for Linux, although different Linux distributions depict Tux in various styles. In video games featuring the character, female...
, the Linux penguin
Penguin
Penguins are a group of aquatic, flightless birds living almost exclusively in the southern hemisphere, especially in Antarctica. Highly adapted for life in the water, penguins have countershaded dark and white plumage, and their wings have become flippers...
; and the Perl Camel
Perl
Perl is a high-level, general-purpose, interpreted, dynamic programming language. Perl was originally developed by Larry Wall in 1987 as a general-purpose Unix scripting language to make report processing easier. Since then, it has undergone many changes and revisions and become widely popular...
stand out as examples. The use of the glider structure
Glider (Conway's Life)
The glider is a pattern that travels across the board in Conway's Game of Life. It was first discovered by Richard K. Guy in 1970, while John Conway's group was attempting to track the evolution of the R-pentomino. Gliders are the smallest spaceships, and they travel diagonally at a speed of c/4...
from Conway's Game of Life
Conway's Game of Life
The Game of Life, also known simply as Life, is a cellular automaton devised by the British mathematician John Horton Conway in 1970....
as a general Hacker Emblem
Hacker Emblem
The Hacker Emblem was first proposed in October 2003 by Eric S. Raymond, who claimed a need for a unifying and recognizable symbol for his perception of hacker culture...
has been proposed by Eric S. Raymond
Eric S. Raymond
Eric Steven Raymond , often referred to as ESR, is an American computer programmer, author and open source software advocate. After the 1997 publication of The Cathedral and the Bazaar, Raymond was for a number of years frequently quoted as an unofficial spokesman for the open source movement...
.
The academic hacker subculture has an annual ceremonial day—April Fool's
April Fools' Day
April Fools' Day is celebrated in different countries around the world on April 1 every year. Sometimes referred to as All Fools' Day, April 1 is not a national holiday, but is widely recognized and celebrated as a day when many people play all kinds of jokes and foolishness...
. There is a long tradition of perpetrating elaborate jokes, hoax
Hoax
A hoax is a deliberately fabricated falsehood made to masquerade as truth. It is distinguishable from errors in observation or judgment, or rumors, urban legends, pseudosciences or April Fools' Day events that are passed along in good faith by believers or as jokes.-Definition:The British...
es, pranks and fake website
Website
A website, also written as Web site, web site, or simply site, is a collection of related web pages containing images, videos or other digital assets. A website is hosted on at least one web server, accessible via a network such as the Internet or a private local area network through an Internet...
s on this date, which includes the publication of the annual joke RFC
April Fools' Day RFC
Almost every April Fools' Day since 1989, the Internet Engineering Task Force has published one or more humorous RFC documents, following in the path blazed by the June 1973 RFC 527 entitled ARPAWOCKY, which parodied Lewis Carroll's nonsense poem Jabberwocky...
.
Use outside of computing
While the word hacker to refer to someone who enjoys playful cleverness is most often applied to computer programmers, it is sometimes used for people who apply the same attitude to other fields. For example, Richard StallmanRichard Stallman
Richard Matthew Stallman , often shortened to rms,"'Richard Stallman' is just my mundane name; you can call me 'rms'"|last= Stallman|first= Richard|date= N.D.|work=Richard Stallman's homepage...
describes the silent composition 4′33″ by John Cage and the 14th century palindromic three-part piece "Ma Fin Est Mon Commencement" by Guillaume de Machaut
Guillaume de Machaut
Guillaume de Machaut was a Medieval French poet and composer. He is one of the earliest composers on whom significant biographical information is available....
as hacks.
According to the Jargon File, the word hacker was used in a similar sense among radio amateurs in the 1950s, predating the software hacking community.
Hack value
Hack value is the notion used by hackers to express that something is worth doing or is interesting. This is something that hackers often feel intuitively about a problem or solution; the feeling approaches the mysticalAdrian Lamo
Adrian Lamo is a threat analyst and "grey hat" hacker. He first gained media attention for breaking into several high-profile computer networks, including those of The New York Times, Yahoo!, and Microsoft, culminating in his 2003 arrest...
for some.
An aspect of hack value is performing feats for the sake of showing that they can be done, even if others think it is difficult. Using things in a unique way outside their intended purpose is often perceived as having hack value. Examples are using a dot matrix impact printer
Dot matrix printer
A dot matrix printer or impact matrix printer is a type of computer printer with a print head that runs back and forth, or in an up and down motion, on the page and prints by impact, striking an ink-soaked cloth ribbon against the paper, much like the print mechanism on a typewriter...
to produce musical notes, using a flatbed scanner to take ultra-high-resolution photographs or using an optical mouse
Optical mouse
An optical computer mouse or "optic mouse" uses a light-emitting diode and photodiodes to detect movement relative to a surface, unlike a mechanical mouse which has a ball which rotates orthogonal shafts which drive chopper wheels for distance measurement.- Early optical mice :Early optical mice,...
as barcode reader
Barcode reader
A barcode reader is an electronic device for reading printed barcodes. Like a flatbed scanner, it consists of a light source, a lens and a light sensor translating optical impulses into electrical ones...
.
A solution or feat has hack value if it is done in a way that has finesse, cleverness or brilliance. So creativity
Creativity
Creativity refers to the phenomenon whereby a person creates something new that has some kind of value. What counts as "new" may be in reference to the individual creator, or to the society or domain within which the novelty occurs...
is an important part of the meaning. For example, picking a difficult lock
Lock picking
Lock picking is the art of unlocking a lock by analyzing and manipulating the components of the lock device, without the original key. Although lock picking can be associated with criminal intent, it is an essential skill for a locksmith...
has hack value; smashing a lock does not. As another example, proving Fermat's last theorem
Fermat's Last Theorem
In number theory, Fermat's Last Theorem states that no three positive integers a, b, and c can satisfy the equation an + bn = cn for any integer value of n greater than two....
by linking together most of modern mathematics has hack value; solving the four color map problem
Four color theorem
In mathematics, the four color theorem, or the four color map theorem states that, given any separation of a plane into contiguous regions, producing a figure called a map, no more than four colors are required to color the regions of the map so that no two adjacent regions have the same color...
by exhaustively trying all possibilities does not (both of these long-standing mathematical challenges have now in fact been proven).
See also
- History of free softwareHistory of free softwareThis is a timeline-style look at how free and open-source software has evolved and existed from its inception.The phrase "free software" refers to software that is liberally licensed, allowing the end user more freedoms than conventional-software licences. This is not to be confused with software...
- Hacker (term)
- Unix philosophyUnix philosophyThe Unix philosophy is a set of cultural norms and philosophical approaches to developing software based on the experience of leading developers of the Unix operating system.-McIlroy: A Quarter Century of Unix:...
Further reading
The Jargon FileJargon File
The Jargon File is a glossary of computer programmer slang. The original Jargon File was a collection of terms from technical cultures such as the MIT AI Lab, the Stanford AI Lab and others of the old ARPANET AI/LISP/PDP-10 communities, including Bolt, Beranek and Newman, Carnegie Mellon...
has had a special role in acculturating hackers since its origins in the early 1970s. These academic and literary works help shaped the academic hacker subculture: influential are:
- Hackers: Heroes of the Computer RevolutionHackers: Heroes of the Computer RevolutionHackers: Heroes of the Computer Revolution is a book by Steven Levy about hacker culture. It was published in 1984 in Garden City, New York by Anchor Press/Doubleday...
, by Steven LevySteven LevySteven Levy is an American journalist who has written several books on computers, technology, cryptography, the Internet, cybersecurity, and privacy.-Career:...
(ISBN 9780385191951, Garden City, NY: Anchor Press/Doubleday) - Gödel, Escher, BachGödel, Escher, BachGödel, Escher, Bach: An Eternal Golden Braid is a book by Douglas Hofstadter, described by his publishing company as "a metaphorical fugue on minds and machines in the spirit of Lewis Carroll"....
, by Douglas HofstadterDouglas HofstadterDouglas Richard Hofstadter is an American academic whose research focuses on consciousness, analogy-making, artistic creation, literary translation, and discovery in mathematics and physics...
(ISBN 9780465026852, New York, NY: Basic BooksBasic BooksBasic Books is a book publisher founded in 1952 and located in New York. It publishes books in the fields of psychology, philosophy, economics, science, politics, sociology, current affairs, and history.-History:...
) - The Art of Computer ProgrammingThe Art of Computer ProgrammingThe Art of Computer Programming is a comprehensive monograph written by Donald Knuth that covers many kinds of programming algorithms and their analysis....
(TAOCP), by Donald KnuthDonald KnuthDonald Ervin Knuth is a computer scientist and Professor Emeritus at Stanford University.He is the author of the seminal multi-volume work The Art of Computer Programming. Knuth has been called the "father" of the analysis of algorithms...
(ISBN 9780201038019, Reading, MA: Addison-WesleyAddison-WesleyAddison-Wesley was a book publisher in Boston, Massachusetts, best known for its textbooks and computer literature. As well as publishing books, Addison-Wesley also distributed its technical titles through the Safari Books Online e-reference service...
) - The Mythical Man-MonthThe Mythical Man-MonthThe Mythical Man-Month: Essays on Software Engineering is a book on software engineering and project management by Fred Brooks, whose central theme is that "adding manpower to a late software project makes it later"...
, by BrooksFred BrooksFrederick Phillips Brooks, Jr. is a software engineer and computer scientist, best known for managing the development of IBM's System/360 family of computers and the OS/360 software support package, then later writing candidly about the process in his seminal book The Mythical Man-Month...
(ISBN 9780201006506, Reading, MA: Addison-WesleyAddison-WesleyAddison-Wesley was a book publisher in Boston, Massachusetts, best known for its textbooks and computer literature. As well as publishing books, Addison-Wesley also distributed its technical titles through the Safari Books Online e-reference service...
) - Compilers: Principles, Techniques, and ToolsCompilers: Principles, Techniques, and ToolsCompilers: Principles, Techniques, and Tools is a famous computer science textbook by Alfred V. Aho, Monica S. Lam, Ravi Sethi, and Jeffrey D. Ullman about compiler construction...
("the Dragon Book"), by Aho, SethiRavi SethiRavi Sethi is an Indian computer scientist retired from Bell Labs and president of Avaya Labs Research. He is best known as one of three authors of the classic computer science textbook Compilers: Principles, Techniques, and Tools, also known as the Dragon Book.Sethi was born in 1947 in Murdana,...
, and Ullman (ISBN 9780201100884, Reading, MA: Addison-WesleyAddison-WesleyAddison-Wesley was a book publisher in Boston, Massachusetts, best known for its textbooks and computer literature. As well as publishing books, Addison-Wesley also distributed its technical titles through the Safari Books Online e-reference service...
) - Structure and Interpretation of Computer ProgramsStructure and Interpretation of Computer ProgramsStructure and Interpretation of Computer Programs is a textbook published in 1984 about general computer programming concepts from MIT Press written by Massachusetts Institute of Technology professors Harold Abelson and Gerald Jay Sussman, with Julie Sussman...
(SICP), by AbelsonHal AbelsonHarold Abelson is a Professor of Electrical Engineering and Computer Science at MIT, a fellow of the IEEE, and is a founding director of both Creative Commons and the Free Software Foundation....
and SussmanGerald Jay SussmanGerald Jay Sussman is the Panasonic Professor of Electrical Engineering at the Massachusetts Institute of Technology . He received his S.B. and Ph.D. degrees in mathematics from MIT in 1968 and 1973 respectively. He has been involved in artificial intelligence research at MIT since 1964...
(ISBN 9780070004849, LondonLondonLondon is the capital city of :England and the :United Kingdom, the largest metropolitan area in the United Kingdom, and the largest urban zone in the European Union by most measures. Located on the River Thames, London has been a major settlement for two millennia, its history going back to its...
: MIT PressMIT PressThe MIT Press is a university press affiliated with the Massachusetts Institute of Technology in Cambridge, Massachusetts .-History:...
) - The C Programming Language (K&R), by Kernighan and RitchieDennis RitchieDennis MacAlistair Ritchie , was an American computer scientist who "helped shape the digital era." He created the C programming language and, with long-time colleague Ken Thompson, the UNIX operating system...
(ISBN 9780131103702, Englewood Cliffs, NJ: Prentice HallPrentice HallPrentice Hall is a major educational publisher. It is an imprint of Pearson Education, Inc., based in Upper Saddle River, New Jersey, USA. Prentice Hall publishes print and digital content for the 6-12 and higher-education market. Prentice Hall distributes its technical titles through the Safari...
) - The Hitchhiker's Guide to the GalaxyThe Hitchhiker's Guide to the GalaxyThe Hitchhiker's Guide to the Galaxy is a science fiction comedy series created by Douglas Adams. Originally a radio comedy broadcast on BBC Radio 4 in 1978, it was later adapted to other formats, and over several years it gradually became an international multi-media phenomenon...
, by Douglas AdamsDouglas AdamsDouglas Noel Adams was an English writer and dramatist. He is best known as the author of The Hitchhiker's Guide to the Galaxy, which started life in 1978 as a BBC radio comedy before developing into a "trilogy" of five books that sold over 15 million copies in his lifetime, a television...
(ISBN 9780517542095, New York, NY: Harmony BooksHarmony BooksHarmony Books is an imprint of the Crown Publishing Group, itself part of publisher Random House. It focusses on topics such as religion, the occult, the paranormal and other pseudoscientific material...
) - The Tao of ProgrammingThe Tao of ProgrammingThe Tao of Programming is a book written in 1987 by Geoffrey James. Written in a tongue-in-cheek style spoof of classic Taoist texts such as the Tao Te Ching and Zhuangzi which belies its serious message...
, by Geoffrey JamesGeoffrey JamesGeoffrey James is an author, journalist, and freelance writer. His works have been published in Wired, The New York Times, and ComputerWorld. He has written several books. He lives in New Hampshire. From February 2007 to September of 2011, he wrote a blog about sales for CBS Interactive...
(ISBN 9780931137075, Santa Monica, CA: InfoBooks) - The Illuminatus! TrilogyThe Illuminatus! TrilogyThe Illuminatus! Trilogy is a series of three novels written by Robert Shea and Robert Anton Wilson first published in 1975. The trilogy is a satirical, postmodern, science fiction-influenced adventure story; a drug-, sex-, and magick-laden trek through a number of conspiracy theories, both...
, by Robert SheaRobert SheaRobert Joseph Shea was an American novelist and former journalist best known as co-author with Robert Anton Wilson of the science fantasy trilogy Illuminatus!. It became a cult success and was later turned into a marathon-length stage show put on at the British National Theatre and elsewhere. In...
and Robert Anton WilsonRobert Anton WilsonRobert Anton Wilson , known to friends as "Bob", was an American author and polymath who became at various times a novelist, philosopher, psychologist, essayist, editor, playwright, poet, futurist, civil libertarian and self-described agnostic mystic...
(ISBN 9780440539810, New York, NY: Dell PublishingDell PublishingDell Publishing, an American publisher of books, magazines and comic books, was founded in 1921 by George T. Delacorte, Jr.During the 1920s, 1930s and 1940s, Dell was one of the largest publishers of magazines, including pulp magazines. Their line of humor magazines included 1000 Jokes, launched in...
) - Principia DiscordiaPrincipia DiscordiaPrincipia Discordia is a Discordian religious text written by Greg Hill and Kerry Thornley . It was originally published under the title "Principia Discordia or How The West Was Lost" in a limited edition of 5 copies in 1965...
, by Greg HillMalaclypse the YoungerGregory Hill , better known by the pen name Malaclypse the Younger , was one of the two writers of the Principia Discordia, along with Kerry Wendell Thornley . He was also adapted as a character in The Illuminatus! Trilogy...
and Kerry ThornleyKerry ThornleyKerry Wendell Thornley is known as the co-founder of Discordianism, in which context he is usually known as Omar Khayyam Ravenhurst or simply Lord Omar...
(ISBN 9780962653421, Avondale Estates, GA: IllumiNet Press) - The Soul of a New MachineThe Soul of a New MachineTracy Kidder's non-fiction book, The Soul of a New Machine, chronicles the experiences of an engineering team racing to design a next generation computer under a blistering schedule and tremendous pressure. This machine was eventually launched in 1980 as the Data General Eclipse MV/8000...
, by Tracy KidderTracy KidderJohn Tracy Kidder is a Pulitzer Prize-winning American writer of the 1981 nonfiction narrative, The Soul of a New Machine, about the creation of a new computer at Data General Corporation...
(ISBN 9780316491709, Boston, MA: Little, Brown and CompanyLittle, Brown and CompanyLittle, Brown and Company is a publishing house established by Charles Coffin Little and his partner, James Brown. Since 2006 it has been a constituent unit of Hachette Book Group USA.-19th century:...
) - The Cuckoo's Egg, by Cliff Stoll (ISBN 9780385249461, New York, NY: Doubleday)
- The Unix SystemThe Unix SystemThe Unix System is a book by Stephen R. Bourne; it was the first widely-available general introduction to the Unix operating system. It included some historical material on Unix, as well as material on using the system, editing, the software tools concept, C programming using the Unix API, data...
, by Stephen R. BourneStephen R. BourneSteve Bourne is a computer scientist, originally from the United Kingdom and based in the US for most of his career. He is most famous as the author of the Bourne shell , which is the foundation for the standard command line interfaces to Unix....
(ISBN 9780201137910, Reading, MA: Addison-WesleyAddison-WesleyAddison-Wesley was a book publisher in Boston, Massachusetts, best known for its textbooks and computer literature. As well as publishing books, Addison-Wesley also distributed its technical titles through the Safari Books Online e-reference service...
) - Hackers & PaintersHackers & PaintersHackers & Painters: Big Ideas from the Computer Age is a collection of essays from Paul Graham discussing hacking, programming languages, start-up companies, and many other technological issues....
, by Paul Graham (ISBN 9780596006624, Sebastopol, CA: O'Reilly MediaO'Reilly MediaO'Reilly Media is an American media company established by Tim O'Reilly that publishes books and Web sites and produces conferences on computer technology topics...
) - The Cathedral and the BazaarThe Cathedral and the BazaarThe Cathedral and the Bazaar is an essay by Eric S. Raymond on software engineering methods, based on his observations of the Linux kernel development process and his experiences managing an open source project, fetchmail. It examines the struggle between top-down and bottom-up design...
, by Eric S. RaymondEric S. RaymondEric Steven Raymond , often referred to as ESR, is an American computer programmer, author and open source software advocate. After the 1997 publication of The Cathedral and the Bazaar, Raymond was for a number of years frequently quoted as an unofficial spokesman for the open source movement...
(ISBN 9781565927247, Cambridge, MA: O'Reilly MediaO'Reilly MediaO'Reilly Media is an American media company established by Tim O'Reilly that publishes books and Web sites and produces conferences on computer technology topics...
) - The essays of Richard M. Stallman (many published in Free Software, Free Society: Select Essays of Richard M. Stallman) [ISBN, Publisher Name and Location Needed]
External links
- A Brief History of Hackerdom
- Gabriella Coleman: The Anthropology of Hackers. The Atlantic, 2010.

