
Kernel Patch Protection
Encyclopedia
X86-64
x86-64 is an extension of the x86 instruction set. It supports vastly larger virtual and physical address spaces than are possible on x86, thereby allowing programmers to conveniently work with much larger data sets. x86-64 also provides 64-bit general purpose registers and numerous other...
) editions of Microsoft Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
that prevents patching the kernel. It was first introduced in 2005 with the x64 editions of Windows XP
Windows XP Professional x64 Edition
Microsoft Windows XP Professional x64 Edition released on April 25, 2005 is an edition of Windows XP for x86-64 personal computers. It is designed to use the expanded 64-bit memory address space provided by the x86-64 architecture....
and Windows Server 2003
Windows Server 2003
Windows Server 2003 is a server operating system produced by Microsoft, introduced on 24 April 2003. An updated version, Windows Server 2003 R2, was released to manufacturing on 6 December 2005...
Service Pack 1.
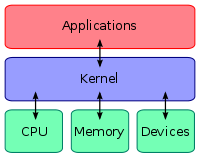
"Patching the kernel" refers to unsupported modification of the central component or kernel of the Windows operating system. Such modification has never been supported by Microsoft because it can greatly reduce system security and reliability. However, though Microsoft does not recommend it, it is technically possible to patch the kernel on x86 editions of Windows. But with the x64 editions of Windows, Microsoft chose to implement technical barriers to kernel patching.
Since patching the kernel is technically permitted in 32-bit (x86) editions of Windows, several antivirus software
Antivirus software
Antivirus or anti-virus software is used to prevent, detect, and remove malware, including but not limited to computer viruses, computer worm, trojan horses, spyware and adware...
developers use kernel patching to implement antivirus and other security services. This kind of antivirus software will not work on computers running x64 editions of Windows. Because of this, Kernel Patch Protection has been criticized for forcing antivirus makers to redesign their software without using kernel patching techniques.
Also, because of the design of the Windows kernel, Kernel Patch Protection cannot completely prevent kernel patching. This has led to additional criticism that since KPP is an imperfect defense, the problems caused to antivirus makers do not outweigh the benefits because authors of malicious software will simply find ways around its defenses. Nevertheless, Kernel Patching can still prevent system stability and reliability problems caused by legitimate software patching the kernel in unsupported ways.
Technical overview
The Windows kernel is designed so that device driverDevice driver
In computing, a device driver or software driver is a computer program allowing higher-level computer programs to interact with a hardware device....
s have the same privilege level as the kernel itself. In turn, device drivers are expected to not modify or patch core system structures within the kernel. In x86 editions of Windows, Windows does not enforce this expectation that drivers not patch the kernel. But because the expectation is not enforced on x86 systems, some programs, notably certain security and antivirus programs, were designed to perform needed tasks through loading drivers that modified core kernel structures.
In x64
X86-64
x86-64 is an extension of the x86 instruction set. It supports vastly larger virtual and physical address spaces than are possible on x86, thereby allowing programmers to conveniently work with much larger data sets. x86-64 also provides 64-bit general purpose registers and numerous other...
editions of Windows, Microsoft chose to begin to enforce the restrictions on what structures drivers can and cannot modify. Kernel Patch Protection is the technology that actually enforces these restrictions. It works by periodically checking to make sure that protected system structures in the kernel have not been modified. If a modification is detected, then Windows will initiate a bug check
Bug check
A fatal system error, also known as a system crash, stop error, kernel error, or bug check, is when an operating system halts the moment it reaches a condition where it cannot operate safely....
and shut down the system, with a blue screen and/or reboot. The corresponding bugcheck number is 0x109, the bugcheck code is CRITICAL_STRUCTURE_CORRUPTION.
Prohibited modifications include:
- Modifying system serviceSystem callIn computing, a system call is how a program requests a service from an operating system's kernel. This may include hardware related services , creating and executing new processes, and communicating with integral kernel services...
tables - Modifying the interrupt descriptor tableInterrupt descriptor tableThe Interrupt Descriptor Table is a data structure used by the x86 architecture to implement an interrupt vector table. The IDT is used by the processor to determine the correct response to interrupts and exceptions....
- Modifying the global descriptor tableGlobal Descriptor TableThe Global Descriptor Table or GDT is a data structure used by Intel x86-family processors starting with the 80286 in order to define the characteristics of the various memory areas used during program execution, including the base address, the size and access privileges like executability and...
- Using kernel stackStack (data structure)In computer science, a stack is a last in, first out abstract data type and linear data structure. A stack can have any abstract data type as an element, but is characterized by only three fundamental operations: push, pop and stack top. The push operation adds a new item to the top of the stack,...
s not allocated by the kernel - Modifying or patching code contained within the kernel itself, or the HAL or NDIS kernel libraries
It should be noted that Kernel Patch Protection only defends against device drivers modifying the kernel. It does not offer any protection against one device driver patching another.
Ultimately, since device drivers have the same privilege level as the kernel itself, it is impossible to completely prevent drivers from bypassing Kernel Patch Protection and then patching the kernel. KPP does however present a significant obstacle to successful kernel patching. With highly obfuscated code
Obfuscated code
Obfuscated code is source or machine code that has been made difficult to understand for humans. Programmers may deliberately obfuscate code to conceal its purpose or its logic to prevent tampering, deter reverse engineering, or as a puzzle or recreational challenge for someone reading the source...
and misleading symbol names, KPP employs security through obscurity
Security through obscurity
Security through obscurity is a pejorative referring to a principle in security engineering, which attempts to use secrecy of design or implementation to provide security...
to hinder attempts to bypass it. Periodic updates to KPP also make it a "moving target", as bypass techniques that may work for a while are likely to break with the next update. Since its creation in 2005, Microsoft has so far released two major updates to KPP, each designed to break known bypass techniques in previous versions.
Advantages
Patching the kernel has never been supported by Microsoft because it can cause a number of negative effects. Kernel Patch Protection protects against these negative effects, which include:- The Blue Screen of DeathBlue Screen of DeathTo forse a BSOD Open regedit.exe,Then search: HKLM\SYSTEM\CurrentControlSet\services\i8042prt\ParametersThen make a new DWORD called "CrashOnCtrlScroll" And set the value to 1....
, which results from serious errors in the kernel. - Reliability issues resulting from multiple programs attempting to patch the same parts of the kernel.
- Compromised system security.
- RootkitRootkitA rootkit is software that enables continued privileged access to a computer while actively hiding its presence from administrators by subverting standard operating system functionality or other applications...
s can use kernel access to embed themselves in an operating system, becoming nearly impossible to remove. - Products that rely on kernel modifications are likely to break with newer versions of Windows or updates to Windows that change the way the kernel works.
Microsoft's Kernel Patch Protection FAQ further explains:
Third-party applications
Some computer security software, such as McAfeeMcAfee
McAfee, Inc. is a computer security company headquartered in Santa Clara, California, USA. It markets software and services to home users, businesses and the public sector. On August 19, 2010, electronics company Intel agreed to purchase McAfee for $7.68 billion...
's McAfee VirusScan
McAfee VirusScan
McAfee VirusScan is an antivirus program created and maintained by McAfee Inc. . McAfee markets VirusScan to home and home-office users; McAfee also develops VirusScan Enterprise for use in corporate environments...
and Symantec
Symantec
Symantec Corporation is the largest maker of security software for computers. The company is headquartered in Mountain View, California, and is a Fortune 500 company and a member of the S&P 500 stock market index.-History:...
's Norton AntiVirus
Norton AntiVirus
Norton AntiVirus, developed and distributed by Symantec Corporation, provides malware prevention and removal during a subscription period. It uses signatures and heuristics to identify viruses. Other features include e-mail spam filtering and phishing protection.Symantec distributes the product as...
, works by patching the kernel. Additionally, anti-virus software authored by Kaspersky Lab
Kaspersky Lab
Kaspersky Lab is a Russian computer security company, co-founded by Natalia Kaspersky and Eugene Kaspersky in 1997, offering anti-virus, anti-spyware, anti-spam, and anti-intrusion products...
has been known to make extensive use of kernel code patching on x86 editions of Windows. This kind of antivirus software will not work on computers running x64 editions of Windows because of Kernel Patch Protection. Because of this, McAfee called for Microsoft to either remove KPP from Windows entirely or make exceptions for software made by trusted companies such as themselves.
Interestingly, Symantec's corporate antivirus software and Norton 2010 range and beyond does work on x64 editions of Windows despite KPP's restrictions.
Antivirus software made by competitors ESET, Trend Micro
Trend Micro
Trend Micro Inc. is a computer security company. It is headquartered in Tokyo, Japan and markets Trend Micro Internet Security, Trend Micro Worry-Free Business Security, OfficeScan, and other related security products and services...
, Grisoft AVG, avast!
Avast!
Avast! is an antivirus computer program developed by AVAST Software a.s. , a company based in Prague, Czech Republic. It was first released in 1988 although back then it was just a tool to remove the Vienna malware...
, Avira Anti-Vir
Avira
Avira Operations GmbH & Co. KG is a German antivirus software company. When founded, the company was called "H+BEDV Datentechnik GmbH". Its antivirus applications are based on the AntiVir scan engine also known as "Luke Filewalker" , first launched in 1988. For aesthetic reasons, the name was...
and Sophos
Sophos
Sophos is a developer and vendor of security software and hardware, including anti-virus, anti-spyware, anti-spam, network access control, encryption software and data loss prevention for desktops, servers, email systems and other network gateways....
do not patch the kernel in default configurations, but may patch the kernel when features such as "advanced process protection" or "prevent unauthorized termination of processes" are enabled. Sophos publicly stated that it does not feel KPP limits the effectiveness of its software.

Hypervisor
In computing, a hypervisor, also called virtual machine manager , is one of many hardware virtualization techniques that allow multiple operating systems, termed guests, to run concurrently on a host computer. It is so named because it is conceptually one level higher than a supervisory program...
virtualization software. Instead, Microsoft worked with third party companies to create new Application Programming Interface
Application programming interface
An application programming interface is a source code based specification intended to be used as an interface by software components to communicate with each other...
s that help security software perform needed tasks without patching the kernel. These new interfaces were included in Windows Vista Service Pack 1.
On December 21, 2006, McAfee's chief scientist George Heron stated that McAfee was pleased with the progress Microsoft was making on the new APIs.
Weaknesses
Because of the design of the Windows kernel, Kernel Patch Protection cannot completely prevent kernel patching. This led the computer security providers McAfeeMcAfee
McAfee, Inc. is a computer security company headquartered in Santa Clara, California, USA. It markets software and services to home users, businesses and the public sector. On August 19, 2010, electronics company Intel agreed to purchase McAfee for $7.68 billion...
and Symantec
Symantec
Symantec Corporation is the largest maker of security software for computers. The company is headquartered in Mountain View, California, and is a Fortune 500 company and a member of the S&P 500 stock market index.-History:...
to say that since KPP is an imperfect defense, the problems caused to security providers do not outweigh the benefits because malicious software will simply find ways around KPP's defenses.
In January 2006, security researchers known by the pseudonym
Pseudonym
A pseudonym is a name that a person assumes for a particular purpose and that differs from his or her original orthonym...
s "skape" and "Skywing" published a report that describes methods, some theoretical, through which Kernel Patch Protection might be bypassed. Skywing went on to publish a second report in January 2007 on bypassing KPP version 2, and a third report in September 2007 on KPP version 3. Also, in October 2006 security company Authentium developed a working method to bypass KPP.
Nevertheless, Microsoft has stated that they are committed to remove any flaws that allow KPP to be bypassed as part of its standard Security Response Center process. In keeping with this statement, Microsoft has so far released two major updates to KPP, each designed to break known bypass techniques in previous versions.
Antitrust behavior
In 2006, the European CommissionEuropean Commission
The European Commission is the executive body of the European Union. The body is responsible for proposing legislation, implementing decisions, upholding the Union's treaties and the general day-to-day running of the Union....
expressed concern over Kernel Patch Protection, saying it was anticompetitive. However, Microsoft's own antivirus product, Windows Live OneCare
Windows Live OneCare
Windows Live OneCare was a computer security and performance enhancement service developed by Microsoft for Microsoft Windows. A core technology of OneCare was the multi-platform RAV , which Microsoft purchased from GeCAD Software Srl in 2003, but subsequently discontinued...
, had no special exception to KPP. Instead, Windows Live OneCare used (and had always used) methods other than patching the kernel to provide virus protection services. Still, for other reasons a x64 edition of Windows Live OneCare was not available until November 15, 2007.
External links
- The Truth About PatchGuard: Why Symantec Keeps Complaining
- An Introduction to Kernel Patch Protection
- Microsoft executive clarifies recent market confusion about Windows Vista Security
- Kernel Patch Protection: Frequently Asked Questions
- Windows Vista x64 Security – Pt 2 – Patchguard
Uninformed.org articles:
- Bypassing PatchGuard on Windows x64
- Subverting PatchGuard Version 2
- PatchGuard Reloaded: A Brief Analysis of PatchGuard Version 3
Working bypass approaches
- A working driver to bypass PatchGuard 3 (including source code)
- Bypassing PatchGuard with a hex editor
Microsoft security advisories:

