Role-Based Access Control
Encyclopedia
In computer systems security, role-based access control (RBAC) is an approach to restricting system access to authorized users. It is used by the majority of enterprises with more than 500 employees, and can be implemented via mandatory access control
(MAC) or discretionary access control
(DAC). RBAC is sometimes referred to as role-based security.
Three primary rules are defined for RBAC:
Additional constraints may be applied as well, and roles can be combined in a hierarchy
where higher-level roles subsume permissions owned by sub-roles.
With the concepts of role hierarchy
and constraints, one can control RBAC to create or simulate lattice-based access control
(LBAC). Thus RBAC can be considered to be a superset of LBAC.
When defining an RBAC model, the following conventions are useful:
A constraint places a restrictive rule on the potential inheritance of permissions from opposing roles, thus it can be used to achieve appropriate separation of duties. For example, the same person should not be allowed to both create a login account and to authorize the account creation.
Thus, using set theory
notation
:
A subject may have multiple simultaneous sessions with different permissions.
.
Prior to the development of RBAC, MAC and DAC were considered to be the only known models for access control: if a model was not MAC, it was considered to be a DAC model, and vice versa. Research in the late 1990s demonstrated that RBAC falls in neither category. Unlike context-based access control (CBAC), RBAC does not look at the message context (such as a connection's source).
RBAC differs from access control lists (ACLs), used in traditional discretionary access-control systems, in that it assigns permissions to specific operations with meaning in the organization, rather than to low level data objects. For example, an access control list could be used to grant or deny write access to a particular system file, but it would not dictate how that file could be changed. In an RBAC-based system, an operation might be to 'create a credit account' transaction in a financial application or to 'populate a blood sugar level test' record in a medical application. The assignment of permission to perform a particular operation is meaningful, because the operations are granular with meaning within the application. RBAC has been shown to be particularly well suited to separation of duties
(SoD) requirements, which ensure that two or more people must be involved in authorizing critical operations. Necessary and sufficient conditions for safety of SoD in RBAC have been analyzed. An underlying principle of SoD is that no individual should be able to effect a breach of security through dual privilege. By extension, no person may hold a role that exercises audit, control or review authority over another, concurrently held role.
Active Directory
, Microsoft SQL Server
, SELinux, grsecurity
, FreeBSD
, Solaris
, Oracle DBMS
, PostgreSQL 8.1
, SAP R/3
, ISIS Papyrus
, FusionForge
and many others effectively implement some form of RBAC. A 2010 report prepared for NIST by the Research Triangle Institute analyzed the economic value of RBAC for enterprises, and estimated benefits per employee from reduced employee downtime, more efficient provisioning, and more efficient access control policy administration.
In an organization with a heterogeneous IT infrastructure and requirements that span dozens or hundreds of systems and applications, using RBAC to manage sufficient roles and assign adequate role memberships becomes extremely complex without hierarchical creation of roles and privilege assignments. Alternate strategies for large scale assignment of privileges to users are discussed in this white paper:
Beyond Roles: A Practical Approach to Enterprise User Provisioning. Newer systems extend the older NIST RBAC model
to address the limitations of RBAC for enterprise-wide deployments. Several academic papers exist. The NIST model was adopted as a standard by INCITS
as ANSI/INCITS 359-2004. A discussion of some of the design choices for the NIST model has also been published.
Mandatory access control
In computer security, mandatory access control refers to a type of access control by which the operating system constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target...
(MAC) or discretionary access control
Discretionary access control
In computer security, discretionary access control is a kind of access control defined by the Trusted Computer System Evaluation Criteria "as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong...
(DAC). RBAC is sometimes referred to as role-based security.
RBAC model
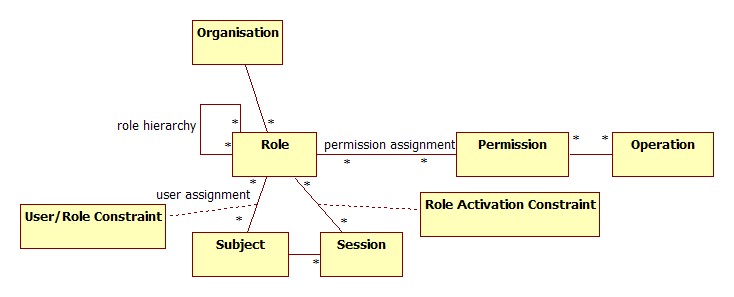
Within an organization, roles are created for various job functions. The permissions to perform certain operations are assigned to specific roles. Members of staff (or other system users) are assigned particular roles, and through those role assignments acquire the computer permissions to perform particular computer-system functions. Since users are not assigned permissions directly, but only acquire them through their role (or roles), management of individual user rights becomes a matter of simply assigning appropriate roles to the user's account; this simplifies common operations, such as adding a user, or changing a user's department.Three primary rules are defined for RBAC:
- Role assignment: A subject can exercise a permission only if the subject has selected or been assigned a role.
- Role authorization: A subject's active role must be authorized for the subject. With rule 1 above, this rule ensures that users can take on only roles for which they are authorized.
- Permission authorization: A subject can exercise a permission only if the permission is authorized for the subject's active role. With rules 1 and 2, this rule ensures that users can exercise only permissions for which they are authorized.
Additional constraints may be applied as well, and roles can be combined in a hierarchy
Hierarchy
A hierarchy is an arrangement of items in which the items are represented as being "above," "below," or "at the same level as" one another...
where higher-level roles subsume permissions owned by sub-roles.
With the concepts of role hierarchy
Role hierarchy
In role based access control, the role hierarchy defines an inheritance relationship among roles. For example, the role structure for a bank may treat all employees as members of the ‘employee’ role...
and constraints, one can control RBAC to create or simulate lattice-based access control
Lattice-Based Access Control
In computer security, lattice-based access control is a complex access control model based on the interaction between any combination of objects and subjects .In this type of label-based mandatory access control model, a lattice is used to define the levels of security...
(LBAC). Thus RBAC can be considered to be a superset of LBAC.
When defining an RBAC model, the following conventions are useful:
- S = Subject = A person or automated agent
- R = Role = Job function or title which defines an authority level
- P = Permissions = An approval of a mode of access to a resource
- SE = Session = A mapping involving S, R and/or P
- SA = Subject Assignment
- PA = Permission Assignment
- RH = Partially ordered Role Hierarchy. RH can also be written: ≥ (The notation: x ≥ y means that x inherits the permissions of y.)
- A subject can have multiple roles.
- A role can have multiple subjects.
- A role can have many permissions.
- A permission can be assigned to many roles.
- An operation can be assigned many permissions.
- A permission can be assigned to many operations.
A constraint places a restrictive rule on the potential inheritance of permissions from opposing roles, thus it can be used to achieve appropriate separation of duties. For example, the same person should not be allowed to both create a login account and to authorize the account creation.
Thus, using set theory
Set theory
Set theory is the branch of mathematics that studies sets, which are collections of objects. Although any type of object can be collected into a set, set theory is applied most often to objects that are relevant to mathematics...
notation
Mathematical notation
Mathematical notation is a system of symbolic representations of mathematical objects and ideas. Mathematical notations are used in mathematics, the physical sciences, engineering, and economics...
:
-
 and is a many to many permission to role assignment relation.
and is a many to many permission to role assignment relation. -
 and is a many to many subject to role assignment relation.
and is a many to many subject to role assignment relation. -

A subject may have multiple simultaneous sessions with different permissions.

Relation to other models
RBAC is a policy neutral and flexible access control technology sufficiently powerful to simulate DAC and MAC. Conversely, MAC can simulate RBAC if the role graph is restricted to a tree rather than a partially ordered setPartially ordered set
In mathematics, especially order theory, a partially ordered set formalizes and generalizes the intuitive concept of an ordering, sequencing, or arrangement of the elements of a set. A poset consists of a set together with a binary relation that indicates that, for certain pairs of elements in the...
.
Prior to the development of RBAC, MAC and DAC were considered to be the only known models for access control: if a model was not MAC, it was considered to be a DAC model, and vice versa. Research in the late 1990s demonstrated that RBAC falls in neither category. Unlike context-based access control (CBAC), RBAC does not look at the message context (such as a connection's source).
RBAC differs from access control lists (ACLs), used in traditional discretionary access-control systems, in that it assigns permissions to specific operations with meaning in the organization, rather than to low level data objects. For example, an access control list could be used to grant or deny write access to a particular system file, but it would not dictate how that file could be changed. In an RBAC-based system, an operation might be to 'create a credit account' transaction in a financial application or to 'populate a blood sugar level test' record in a medical application. The assignment of permission to perform a particular operation is meaningful, because the operations are granular with meaning within the application. RBAC has been shown to be particularly well suited to separation of duties
Separation of duties
Separation of duties is the concept of having more than one person required to complete a task. In business the separation by sharing of more than one individual in one single task shall prevent from fraud and error. The concept is alternatively called segregation of duties or, in the political...
(SoD) requirements, which ensure that two or more people must be involved in authorizing critical operations. Necessary and sufficient conditions for safety of SoD in RBAC have been analyzed. An underlying principle of SoD is that no individual should be able to effect a breach of security through dual privilege. By extension, no person may hold a role that exercises audit, control or review authority over another, concurrently held role.
Use and availability
The use of RBAC to manage user privileges (computer permissions) within a single system or application is widely accepted as a best practice. Systems including MicrosoftMicrosoft
Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions...
Active Directory
Active Directory
Active Directory is a directory service created by Microsoft for Windows domain networks. It is included in most Windows Server operating systems. Server computers on which Active Directory is running are called domain controllers....
, Microsoft SQL Server
Microsoft SQL Server
Microsoft SQL Server is a relational database server, developed by Microsoft: It is a software product whose primary function is to store and retrieve data as requested by other software applications, be it those on the same computer or those running on another computer across a network...
, SELinux, grsecurity
Grsecurity
grsecurity is a set of patches for the Linux kernel with an emphasis on enhancing security. Its typical application is in computer systems that accept remote connections from untrusted locations, such as web servers and systems offering shell access to its users.Released under the GNU General...
, FreeBSD
FreeBSD
FreeBSD is a free Unix-like operating system descended from AT&T UNIX via BSD UNIX. Although for legal reasons FreeBSD cannot be called “UNIX”, as the direct descendant of BSD UNIX , FreeBSD’s internals and system APIs are UNIX-compliant...
, Solaris
Solaris Operating System
Solaris is a Unix operating system originally developed by Sun Microsystems. It superseded their earlier SunOS in 1993. Oracle Solaris, as it is now known, has been owned by Oracle Corporation since Oracle's acquisition of Sun in January 2010....
, Oracle DBMS
Oracle database
The Oracle Database is an object-relational database management system produced and marketed by Oracle Corporation....
, PostgreSQL 8.1
PostgreSQL
PostgreSQL, often simply Postgres, is an object-relational database management system available for many platforms including Linux, FreeBSD, Solaris, MS Windows and Mac OS X. It is released under the PostgreSQL License, which is an MIT-style license, and is thus free and open source software...
, SAP R/3
SAP R/3
SAP R/3 is the former name of the main enterprise resource planning software produced by SAP AG. It is an enterprise-wide information system designed to coordinate all the resources, information, and activities needed to complete business processes such as order fulfillment or billing.- History of...
, ISIS Papyrus
ISIS Papyrus
ISIS Papyrus is a Swiss-based commercial software development group that sells its products in 42 countries either directly or through business partners...
, FusionForge
FusionForge
FusionForge is a free software application descendant of the forge originally created for running the SourceForge.net platform...
and many others effectively implement some form of RBAC. A 2010 report prepared for NIST by the Research Triangle Institute analyzed the economic value of RBAC for enterprises, and estimated benefits per employee from reduced employee downtime, more efficient provisioning, and more efficient access control policy administration.
In an organization with a heterogeneous IT infrastructure and requirements that span dozens or hundreds of systems and applications, using RBAC to manage sufficient roles and assign adequate role memberships becomes extremely complex without hierarchical creation of roles and privilege assignments. Alternate strategies for large scale assignment of privileges to users are discussed in this white paper:
Beyond Roles: A Practical Approach to Enterprise User Provisioning. Newer systems extend the older NIST RBAC model
NIST RBAC model
The NIST RBAC model is a standardized definition of role based access control. Although originally developed by the National Institute of Standards and Technology, the standard was adopted and is copyrighted and distributed as INCITS 359-2004 by the International Committee for Information...
to address the limitations of RBAC for enterprise-wide deployments. Several academic papers exist. The NIST model was adopted as a standard by INCITS
INCITS
The InterNational Committee for Information Technology Standards, or INCITS , is an ANSI-accredited forum of IT developers. It was formerly known as the X3 and NCITS....
as ANSI/INCITS 359-2004. A discussion of some of the design choices for the NIST model has also been published.
See also
- NIST RBAC modelNIST RBAC modelThe NIST RBAC model is a standardized definition of role based access control. Although originally developed by the National Institute of Standards and Technology, the standard was adopted and is copyrighted and distributed as INCITS 359-2004 by the International Committee for Information...
- Lattice-based access controlLattice-Based Access ControlIn computer security, lattice-based access control is a complex access control model based on the interaction between any combination of objects and subjects .In this type of label-based mandatory access control model, a lattice is used to define the levels of security...
(LBAC), equivalent to mandatory access controlMandatory access controlIn computer security, mandatory access control refers to a type of access control by which the operating system constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target...
(MAC). - Discretionary access controlDiscretionary access controlIn computer security, discretionary access control is a kind of access control defined by the Trusted Computer System Evaluation Criteria "as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong...
- Security label
- Security classification
- Covert channelCovert channelIn computer security, a covert channel is a type of computer security attack that creates a capability to transfer information objects between processes that are not supposed to be allowed to communicate by the computer security policy...
- Chinese wallChinese wallIn business, a Chinese wall or firewall is an information barrier implemented within a firm to separate and isolate persons who make investment decisions from persons who are privy to undisclosed material information which may influence those decisions...
- AuthenticationAuthenticationAuthentication is the act of confirming the truth of an attribute of a datum or entity...
- Blind credentialBlind credentialA blind credential is a token asserting that someone qualifies under some criteria or has some status or right, without revealing "who" that person is — without including their name or address, for instance...
- SudoSudosudo is a program for Unix-like computer operating systems that allows users to run programs with the security privileges of another user...
(super user do) Unix program - Identity Driven NetworkingIdentity Driven NetworkingIdentity Driven Networking is the process of applying network controls to a network device access based on the identity of an individual or group of individuals responsible to or operating the device...
- XACMLXACMLXACML stands for eXtensible Access Control Markup Language. The standard defines a declarative access control policy language implemented in XML and a processing model describing how to evaluate authorization requests according to the rules defined in policies.As a published standard...
An Attribute Based Access Control (ABAC) model which incorporates RBAC - grsecurityGrsecuritygrsecurity is a set of patches for the Linux kernel with an emphasis on enhancing security. Its typical application is in computer systems that accept remote connections from untrusted locations, such as web servers and systems offering shell access to its users.Released under the GNU General...
A Linux kernel patch to implement RBAC - AGDLPAGDLPAGDLP briefly summarizes Microsoft's recommendations for implementing role based access controls using nested groups in a native-mode Active Directory domain: User and computer accounts are members of global groups that represent business roles, which are members of domain local groups that...
How to implement RBAC in Active Directory domains/forests - PERMISPERMISPERMIS is a sophisticated policy-based authorisation system that implements an enhanced version of the U.S. National Institute of Standards and Technology standard Role-Based Access Control model...
(PrivilEge and Role Management Infrastructure Standards)
External links
- RBAC White Paper A White Paper from Tools4ever for Role-Based Access Control
- FAQ on RBAC models and standards
- Role Based Access Controls at NIST - huge US government website with lots of information on the theory and implementation of RBAC
- XACML core and hierarchical role based access control profile - OASISOASIS (organization)The Organization for the Advancement of Structured Information Standards is a global consortium that drives the development, convergence and adoption of e-business and web service standards...
XACMLXACMLXACML stands for eXtensible Access Control Markup Language. The standard defines a declarative access control policy language implemented in XML and a processing model describing how to evaluate authorization requests according to the rules defined in policies.As a published standard...
standard. (PDF file) - RBAC Microsoft's article
- RBAC .net article
- Getting Started with AzMan
- Institute for Cyber Security at the University of Texas San Antonio
- Trustifier RoBAC/RuBAC overview
- RBAC implementation for ASP.NET web applications
- Open Source RBAC implementation
- Practical experiences in implementing RBAC
- Role-based approach to Active Directory delegation

