
Stream cipher
Encyclopedia
In cryptography
, a stream cipher is a symmetric key cipher
where plaintext digits are combined with a pseudorandom cipher digit stream (keystream
). In a stream cipher the plaintext
digit
s are encrypted one at a time, and the transformation of successive digits varies during the encryption. An alternative name is a state cipher, as the encryption of each digit is dependent on the current state. In practice, a digit is typically a bit
and the combining operation an exclusive-or (xor).
Stream ciphers represent a different approach to symmetric encryption from block cipher
s. Block ciphers operate on large blocks of digits with a fixed, unvarying transformation. This distinction is not always clear-cut: in some modes of operation
, a block cipher primitive is used in such a way that it acts effectively as a stream cipher. Stream ciphers typically execute at a higher speed than block ciphers and have lower hardware complexity. However, stream ciphers can be susceptible to serious security problems if used incorrectly: see stream cipher attack
s — in particular, the same starting state must never be used twice.
(OTP), sometimes known as the Vernam cipher. A one-time pad uses a keystream
of completely random digits. The keystream is combined with the plaintext digits one at a time to form the ciphertext. This system was proved to be secure by Claude Shannon in 1949. However, the keystream must be (at least) the same length as the plaintext, and generated completely at random. This makes the system very cumbersome to implement in practice, and as a result the one-time pad has not been widely used, except for the most critical applications.
A stream cipher makes use of a much smaller and more convenient key — 128 bits, for example. Based on this key, it generates a pseudorandom keystream which can be combined with the plaintext digits in a similar fashion to the one-time pad. However, this comes at a cost: because the keystream is now pseudorandom, and not truly random, the proof of security associated with the one-time pad no longer holds: it is quite possible for a stream cipher to be completely insecure.
s), and the keystream is combined with the plaintext using the exclusive or operation (XOR). This is termed a binary additive stream cipher.
In a synchronous stream cipher, the sender and receiver must be exactly in step for decryption to be successful. If digits are added or removed from the message during transmission, synchronisation is lost. To restore synchronisation, various offsets can be tried systematically to obtain the correct decryption. Another approach is to tag the ciphertext with markers at regular points in the output.
If, however, a digit is corrupted in transmission, rather than added or lost, only a single digit in the plaintext is affected and the error does not propagate to other parts of the message. This property is useful when the transmission error rate is high; however, it makes it less likely the error would be detected without further mechanisms. Moreover, because of this property, synchronous stream ciphers are very susceptible to active attacks — if an attacker can change a digit in the ciphertext, he might be able to make predictable changes to the corresponding plaintext bit; for example, flipping a bit in the ciphertext causes the same bit to be flipped in the plaintext.
An example of a self-synchronising stream cipher is a block cipher in cipher feedback (CFB) mode
.
s (LFSRs) because they can be easily implemented in hardware
and can be readily analysed mathematically. The use of LFSRs on their own, however, is insufficient to provide good security. Various schemes have been proposed to increase the security of LFSRs.
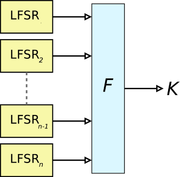 Because LFSRs are inherently linear, one technique for removing the linearity is to feed the outputs of several parallel LFSRs into a non-linear Boolean function to form a combination generator. Various properties of such a combining function are critical for ensuring the security of the resultant scheme, for example, in order to avoid correlation attack
Because LFSRs are inherently linear, one technique for removing the linearity is to feed the outputs of several parallel LFSRs into a non-linear Boolean function to form a combination generator. Various properties of such a combining function are critical for ensuring the security of the resultant scheme, for example, in order to avoid correlation attack
s.
and the shrinking generator
.
An alternating step generator
comprises three linear feedback shift registers, which we will call LFSR0, LFSR1 and LFSR2 for convenience. The output of one of the registers decides which of the other two is to be used; for instance if LFSR2 outputs a 0, LFSR0 is clocked, and if it outputs a 1, LFSR1 is clocked instead. The output is the exclusive OR of the last bit produced by LFSR0 and LFSR1. The initial state of the three LFSRs is the key.
The stop-and-go generator (Beth and Piper, 1984) consists of two LFSRs. One LFSR is clocked if the output of a second is a "1", otherwise it repeats its previous output. This output is then (in some versions) combined with the output of a third LFSR clocked at a regular rate.
The shrinking generator
takes a different approach. Two LFSRs are used, both clocked regularly. If the output of the first LFSR is "1", the output of the second LFSR becomes the output of the generator. If the first LFSR outputs "0", however, the output of the second is discarded, and no bit is output by the generator. This mechanism suffers from timing attacks on the second generator, since the speed of the output is variable in a manner that depends on the second generator's state. This can be alleviated by buffering the output.
 Instead of a linear driving device, one may use a nonlinear update function. For example, Klimov and Shamir proposed triangular functions (T-Functions) with a single cycle on n bit words.
Instead of a linear driving device, one may use a nonlinear update function. For example, Klimov and Shamir proposed triangular functions (T-Functions) with a single cycle on n bit words.
For a stream cipher to be secure, its keystream must have a large period
and it must be impossible to recover the cipher's key or internal state from the keystream. Cryptographers also demand that the keystream be free of even subtle biases that would let attackers distinguish a stream from random noise, and free of detectable relationships between keystreams that correspond to related keys or related cryptographic nonce
s. This should be true for all keys (there should be no weak keys), and true even if the attacker can know or choose some plaintext or ciphertext.
As with other attacks in cryptography, stream cipher attacks can be certificational, meaning they aren't necessarily practical ways to break the cipher but indicate that the cipher might have other weaknesses.
Securely using a secure synchronous stream cipher requires that one never reuse the same keystream twice; that generally means a different nonce
or key must be supplied to each invocation of the cipher. Application designers must also recognize that most stream ciphers don't provide authenticity, only privacy: encrypted messages may still have been modified in transit.
Short periods for stream ciphers have been a practical concern. For example, 64-bit block ciphers like DES
can be used to generate a keystream in output feedback (OFB) mode. However, when not using full feedback, the resulting stream has a period of around 232 blocks on average; for many applications, this period is far too low. For example, if encryption is being performed at a rate of 8 megabyte
s per second, a stream of period 232 blocks will repeat after about a half an hour.
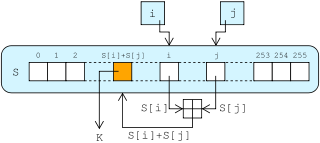
Some applications using the stream cipher RC4
are attackable because of weaknesses in RC4's key setup routine; new applications should either avoid RC4 or make sure all keys are unique and ideally unrelated (e.g., generated by a cryptographic hash function
) and that the first bytes of the keystream are discarded.
connection. If a block cipher
(not operating in a stream cipher mode) were to be used in this type of application, the designer would need to choose either transmission efficiency or implementation complexity, since block ciphers cannot directly work on blocks shorter than their block size. For example, if a 128-bit block cipher received separate 32-bit bursts of plaintext, three quarters of the data transmitted would be padding
. Block ciphers must be used in ciphertext stealing
or residual block termination
mode to avoid padding, while stream ciphers eliminate this issue by naturally operating on the smallest unit that can be transmitted (usually bytes).
Another advantage of stream ciphers in military cryptography is that the cipher stream can be generated in a separate box that is subject to strict security measures and fed to other devices, e.g. a radio set, which will perform the xor operation as part of their function. The latter device can then be designed and used in less stringent environments.
RC4 is the most widely used stream cipher in software; others include:
A5/1
,
A5/2
,
Chameleon,
FISH
,
Helix,
ISAAC
,
MUGI
,
Panama,
Phelix
,
Pike
,
SEAL
,
SOBER,
SOBER-128
and
WAKE.
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, a stream cipher is a symmetric key cipher
Cipher
In cryptography, a cipher is an algorithm for performing encryption or decryption — a series of well-defined steps that can be followed as a procedure. An alternative, less common term is encipherment. In non-technical usage, a “cipher” is the same thing as a “code”; however, the concepts...
where plaintext digits are combined with a pseudorandom cipher digit stream (keystream
Keystream
In cryptography, a keystream is a stream of random or pseudorandom characters that are combined with a plaintext message to produce an encrypted message ....
). In a stream cipher the plaintext
Plaintext
In cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
digit
Numerical digit
A digit is a symbol used in combinations to represent numbers in positional numeral systems. The name "digit" comes from the fact that the 10 digits of the hands correspond to the 10 symbols of the common base 10 number system, i.e...
s are encrypted one at a time, and the transformation of successive digits varies during the encryption. An alternative name is a state cipher, as the encryption of each digit is dependent on the current state. In practice, a digit is typically a bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
and the combining operation an exclusive-or (xor).
Stream ciphers represent a different approach to symmetric encryption from block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
s. Block ciphers operate on large blocks of digits with a fixed, unvarying transformation. This distinction is not always clear-cut: in some modes of operation
Block cipher modes of operation
In cryptography, modes of operation is the procedure of enabling the repeated and secure use of a block cipher under a single key.A block cipher by itself allows encryption only of a single data block of the cipher's block length. When targeting a variable-length message, the data must first be...
, a block cipher primitive is used in such a way that it acts effectively as a stream cipher. Stream ciphers typically execute at a higher speed than block ciphers and have lower hardware complexity. However, stream ciphers can be susceptible to serious security problems if used incorrectly: see stream cipher attack
Stream cipher attack
Stream ciphers, where plaintext bits are combined with a cipher bit stream by an exclusive-or operation , can be very secure if used properly. However they are vulnerable to attack if certain precautions are not followed:*keys must never be used twice...
s — in particular, the same starting state must never be used twice.
Loose inspiration from the one-time pad
Stream ciphers can be viewed as approximating the action of a proven unbreakable cipher, the one-time padOne-time pad
In cryptography, the one-time pad is a type of encryption, which has been proven to be impossible to crack if used correctly. Each bit or character from the plaintext is encrypted by a modular addition with a bit or character from a secret random key of the same length as the plaintext, resulting...
(OTP), sometimes known as the Vernam cipher. A one-time pad uses a keystream
Keystream
In cryptography, a keystream is a stream of random or pseudorandom characters that are combined with a plaintext message to produce an encrypted message ....
of completely random digits. The keystream is combined with the plaintext digits one at a time to form the ciphertext. This system was proved to be secure by Claude Shannon in 1949. However, the keystream must be (at least) the same length as the plaintext, and generated completely at random. This makes the system very cumbersome to implement in practice, and as a result the one-time pad has not been widely used, except for the most critical applications.
A stream cipher makes use of a much smaller and more convenient key — 128 bits, for example. Based on this key, it generates a pseudorandom keystream which can be combined with the plaintext digits in a similar fashion to the one-time pad. However, this comes at a cost: because the keystream is now pseudorandom, and not truly random, the proof of security associated with the one-time pad no longer holds: it is quite possible for a stream cipher to be completely insecure.
Types of stream ciphers
A stream cipher generates successive elements of the keystream based on an internal state. This state is updated in essentially two ways: if the state changes independently of the plaintext or ciphertext messages, the cipher is classified as a synchronous stream cipher. By contrast, self-synchronising stream ciphers update their state based on previous ciphertext digits.Synchronous stream ciphers
In a synchronous stream cipher a stream of pseudo-random digits is generated independently of the plaintext and ciphertext messages, and then combined with the plaintext (to encrypt) or the ciphertext (to decrypt). In the most common form, binary digits are used (bitBit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
s), and the keystream is combined with the plaintext using the exclusive or operation (XOR). This is termed a binary additive stream cipher.
In a synchronous stream cipher, the sender and receiver must be exactly in step for decryption to be successful. If digits are added or removed from the message during transmission, synchronisation is lost. To restore synchronisation, various offsets can be tried systematically to obtain the correct decryption. Another approach is to tag the ciphertext with markers at regular points in the output.
If, however, a digit is corrupted in transmission, rather than added or lost, only a single digit in the plaintext is affected and the error does not propagate to other parts of the message. This property is useful when the transmission error rate is high; however, it makes it less likely the error would be detected without further mechanisms. Moreover, because of this property, synchronous stream ciphers are very susceptible to active attacks — if an attacker can change a digit in the ciphertext, he might be able to make predictable changes to the corresponding plaintext bit; for example, flipping a bit in the ciphertext causes the same bit to be flipped in the plaintext.
Self-synchronizing stream ciphers
Another approach uses several of the previous N ciphertext digits to compute the keystream. Such schemes are known as self-synchronizing stream ciphers, asynchronous stream ciphers or ciphertext autokey (CTAK). The idea of self-synchronization was patented in 1946, and has the advantage that the receiver will automatically synchronise with the keystream generator after receiving N ciphertext digits, making it easier to recover if digits are dropped or added to the message stream. Single-digit errors are limited in their effect, affecting only up to N plaintext digits.An example of a self-synchronising stream cipher is a block cipher in cipher feedback (CFB) mode
Block cipher modes of operation
In cryptography, modes of operation is the procedure of enabling the repeated and secure use of a block cipher under a single key.A block cipher by itself allows encryption only of a single data block of the cipher's block length. When targeting a variable-length message, the data must first be...
.
Linear feedback shift register-based stream ciphers
Binary stream ciphers are often constructed using linear feedback shift registerLinear feedback shift register
A linear feedback shift register is a shift register whose input bit is a linear function of its previous state.The most commonly used linear function of single bits is XOR...
s (LFSRs) because they can be easily implemented in hardware
Hardware
Hardware is a general term for equipment such as keys, locks, hinges, latches, handles, wire, chains, plumbing supplies, tools, utensils, cutlery and machine parts. Household hardware is typically sold in hardware stores....
and can be readily analysed mathematically. The use of LFSRs on their own, however, is insufficient to provide good security. Various schemes have been proposed to increase the security of LFSRs.
Non-linear combining functions

Correlation attack
In cryptography, correlation attacks are a class of known plaintext attacks for breaking stream ciphers whose keystream is generated by combining the output of several linear feedback shift registers using a Boolean function...
s.
Clock-controlled generators
Normally LFSRs are stepped regularly. One approach to introducing non-linearity is to have the LFSR clocked irregularly, controlled by the output of a second LFSR. Such generators include the stop-and-go generator, the alternating step generatorAlternating step generator
In cryptography, an alternating step generator is a cryptographic pseudorandom number generator intended to be used in a stream cipher. The design was published in 1987 by C. G. Günther...
and the shrinking generator
Shrinking generator
In cryptography, the shrinking generator is a form of pseudorandom number generator intended to be used in a stream cipher. It was published in Crypto 1993 by Don Coppersmith, Hugo Krawczyk, and Yishay Mansour....
.
An alternating step generator
Alternating step generator
In cryptography, an alternating step generator is a cryptographic pseudorandom number generator intended to be used in a stream cipher. The design was published in 1987 by C. G. Günther...
comprises three linear feedback shift registers, which we will call LFSR0, LFSR1 and LFSR2 for convenience. The output of one of the registers decides which of the other two is to be used; for instance if LFSR2 outputs a 0, LFSR0 is clocked, and if it outputs a 1, LFSR1 is clocked instead. The output is the exclusive OR of the last bit produced by LFSR0 and LFSR1. The initial state of the three LFSRs is the key.
The stop-and-go generator (Beth and Piper, 1984) consists of two LFSRs. One LFSR is clocked if the output of a second is a "1", otherwise it repeats its previous output. This output is then (in some versions) combined with the output of a third LFSR clocked at a regular rate.
The shrinking generator
Shrinking generator
In cryptography, the shrinking generator is a form of pseudorandom number generator intended to be used in a stream cipher. It was published in Crypto 1993 by Don Coppersmith, Hugo Krawczyk, and Yishay Mansour....
takes a different approach. Two LFSRs are used, both clocked regularly. If the output of the first LFSR is "1", the output of the second LFSR becomes the output of the generator. If the first LFSR outputs "0", however, the output of the second is discarded, and no bit is output by the generator. This mechanism suffers from timing attacks on the second generator, since the speed of the output is variable in a manner that depends on the second generator's state. This can be alleviated by buffering the output.
Filter generator
Another approach to improving the security of an LFSR is to pass the entire state of a single LFSR into a non-linear filtering function.Other designs

Security
- Main article: Stream cipher attackStream cipher attackStream ciphers, where plaintext bits are combined with a cipher bit stream by an exclusive-or operation , can be very secure if used properly. However they are vulnerable to attack if certain precautions are not followed:*keys must never be used twice...
For a stream cipher to be secure, its keystream must have a large period
Periodic function
In mathematics, a periodic function is a function that repeats its values in regular intervals or periods. The most important examples are the trigonometric functions, which repeat over intervals of length 2π radians. Periodic functions are used throughout science to describe oscillations,...
and it must be impossible to recover the cipher's key or internal state from the keystream. Cryptographers also demand that the keystream be free of even subtle biases that would let attackers distinguish a stream from random noise, and free of detectable relationships between keystreams that correspond to related keys or related cryptographic nonce
Cryptographic nonce
In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
s. This should be true for all keys (there should be no weak keys), and true even if the attacker can know or choose some plaintext or ciphertext.
As with other attacks in cryptography, stream cipher attacks can be certificational, meaning they aren't necessarily practical ways to break the cipher but indicate that the cipher might have other weaknesses.
Securely using a secure synchronous stream cipher requires that one never reuse the same keystream twice; that generally means a different nonce
Cryptographic nonce
In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused...
or key must be supplied to each invocation of the cipher. Application designers must also recognize that most stream ciphers don't provide authenticity, only privacy: encrypted messages may still have been modified in transit.
Short periods for stream ciphers have been a practical concern. For example, 64-bit block ciphers like DES
Data Encryption Standard
The Data Encryption Standard is a block cipher that uses shared secret encryption. It was selected by the National Bureau of Standards as an official Federal Information Processing Standard for the United States in 1976 and which has subsequently enjoyed widespread use internationally. It is...
can be used to generate a keystream in output feedback (OFB) mode. However, when not using full feedback, the resulting stream has a period of around 232 blocks on average; for many applications, this period is far too low. For example, if encryption is being performed at a rate of 8 megabyte
Megabyte
The megabyte is a multiple of the unit byte for digital information storage or transmission with two different values depending on context: bytes generally for computer memory; and one million bytes generally for computer storage. The IEEE Standards Board has decided that "Mega will mean 1 000...
s per second, a stream of period 232 blocks will repeat after about a half an hour.
Some applications using the stream cipher RC4
RC4
In cryptography, RC4 is the most widely used software stream cipher and is used in popular protocols such as Secure Sockets Layer and WEP...
are attackable because of weaknesses in RC4's key setup routine; new applications should either avoid RC4 or make sure all keys are unique and ideally unrelated (e.g., generated by a cryptographic hash function
Cryptographic hash function
A cryptographic hash function is a deterministic procedure that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that an accidental or intentional change to the data will change the hash value...
) and that the first bytes of the keystream are discarded.
Usage
Stream ciphers are often used for their speed and simplicity of implementation in hardware, and in applications where plaintext comes in quantities of unknowable length—for example, a secure wirelessWireless network
Wireless network refers to any type of computer network that is not connected by cables of any kind. It is a method by which homes, telecommunications networks and enterprise installations avoid the costly process of introducing cables into a building, or as a connection between various equipment...
connection. If a block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
(not operating in a stream cipher mode) were to be used in this type of application, the designer would need to choose either transmission efficiency or implementation complexity, since block ciphers cannot directly work on blocks shorter than their block size. For example, if a 128-bit block cipher received separate 32-bit bursts of plaintext, three quarters of the data transmitted would be padding
Padding (cryptography)
-Classical cryptography:Official messages often start and end in predictable ways: My dear ambassador, Weather report, Sincerely yours, etc. The primary use of padding with classical ciphers is to prevent the cryptanalyst from using that predictability to find cribs that aid in breaking the...
. Block ciphers must be used in ciphertext stealing
Ciphertext stealing
In cryptography, ciphertext stealing is a general method of using a block cipher mode of operation that allows for processing of messages that are not evenly divisible into blocks without resulting in any expansion of the ciphertext, at the cost of slightly increased complexity.-General...
or residual block termination
Residual block termination
In cryptography, residual block termination is a variation of cipher block chaining mode that does not require any padding. It does this by effectively changing to cipher feedback mode for one block...
mode to avoid padding, while stream ciphers eliminate this issue by naturally operating on the smallest unit that can be transmitted (usually bytes).
Another advantage of stream ciphers in military cryptography is that the cipher stream can be generated in a separate box that is subject to strict security measures and fed to other devices, e.g. a radio set, which will perform the xor operation as part of their function. The latter device can then be designed and used in less stringent environments.
RC4 is the most widely used stream cipher in software; others include:
A5/1
A5/1
A5/1 is a stream cipher used to provide over-the-air communication privacy in the GSM cellular telephone standard. It was initially kept secret, but became public knowledge through leaks and reverse engineering. A number of serious weaknesses in the cipher have been identified.-History and...
,
A5/2
A5/2
A5/2 is a stream cipher used to provide voice privacy in the GSM cellular telephone protocol.The cipher is based around a combination of four linear feedback shift registers with irregular clocking and a non-linear combiner.In 1999, Ian Goldberg and David A...
,
Chameleon,
FISH
FISH (cipher)
The FISH stream cipher is a fast software based stream cipher using Lagged Fibonacci generators, plus a concept from the shrinking generator cipher. It was published by Siemens in 1993. FISH is quite fast in software and has a huge key length...
,
Helix,
ISAAC
ISAAC (cipher)
ISAAC is a cryptographically secure pseudorandom number generator and a stream cipher designed by Robert J. Jenkins Jr. in 1996.- Operation :...
,
MUGI
MUGI
In cryptography, MUGI is a pseudorandom number generator designed for use as a stream cipher. It has been recommended for Japanese government use by the CRYPTREC project.MUGI takes a 128-bit secret key and a 128-bit initial vector...
,
Panama,
Phelix
Phelix
Phelix is a high-speed stream cipher with a built-in single-pass message authentication code functionality, submitted in 2004 to the eSTREAM contest by Doug Whiting, Bruce Schneier, Stefan Lucks, and Frédéric Muller. The cipher uses only the operations of addition modulo 232, exclusive or, and...
,
Pike
Pike (cipher)
The Pike stream cipher was invented by Ross Anderson to be a "leaner and meaner" version of FISH after he broke FISH in 1994; the name is a humorous allusion to the Pike fish. The cipher combines ideas from A5 with the Lagged Fibonacci generators used in FISH. It is about 10% faster than FISH, yet...
,
SEAL
SEAL (cipher)
In cryptography, SEAL is a very fast stream cipher optimised for machines with a 32-bit word size and plenty of RAM. SEAL is actually a pseudorandom function family in that it can easily generate arbitrary portions of the keystream without having to start from the beginning...
,
SOBER,
SOBER-128
SOBER-128
SOBER-128 is a synchronous stream cipher designed by Hawkes and Rose and is a member of the SOBER family of ciphers. SOBER-128 was also designed to provide MAC functionality....
and
WAKE.
Comparison Of Stream Ciphers
| Stream Cipher |
Creation Date |
Speed (cycles per byte Cycles per byte Cycles per byte is a unit of measurement which indicates the number of clock cycles a microprocessor will perform per byte of data processed in an algorithm. It is commonly used as a partial indicator of real-world performance in cryptographic functions.... ) |
(bits) | Attack | |||
|---|---|---|---|---|---|---|---|
| Effective Key- Key (cryptography) In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa... Length Key size In cryptography, key size or key length is the size measured in bits of the key used in a cryptographic algorithm . An algorithm's key length is distinct from its cryptographic security, which is a logarithmic measure of the fastest known computational attack on the algorithm, also measured in bits... |
Initialization vector Initialization vector In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom... |
Internal State |
Best Known | Computational Complexity |
|||
| A5/1 A5/1 A5/1 is a stream cipher used to provide over-the-air communication privacy in the GSM cellular telephone standard. It was initially kept secret, but became public knowledge through leaks and reverse engineering. A number of serious weaknesses in the cipher have been identified.-History and... |
1989 | Voice (Wphone) Mobile phone A mobile phone is a device which can make and receive telephone calls over a radio link whilst moving around a wide geographic area. It does so by connecting to a cellular network provided by a mobile network operator... |
54 | 114 | 64 | Active KPA Known-plaintext attack The known-plaintext attack is an attack model for cryptanalysis where the attacker has samples of both the plaintext , and its encrypted version . These can be used to reveal further secret information such as secret keys and code books... OR KPA Known-plaintext attack The known-plaintext attack is an attack model for cryptanalysis where the attacker has samples of both the plaintext , and its encrypted version . These can be used to reveal further secret information such as secret keys and code books... Time-Memory Tradeoff |
~2 seconds OR 239.91 |
| A5/2 A5/2 A5/2 is a stream cipher used to provide voice privacy in the GSM cellular telephone protocol.The cipher is based around a combination of four linear feedback shift registers with irregular clocking and a non-linear combiner.In 1999, Ian Goldberg and David A... |
1989 | Voice (Wphone) Mobile phone A mobile phone is a device which can make and receive telephone calls over a radio link whilst moving around a wide geographic area. It does so by connecting to a cellular network provided by a mobile network operator... |
54 | 114 | 64? | Active | 4.6 milliseconds |
| Achterbahn-128/80 Achterbahn In cryptography, Achterbahn is the name of a synchronous stream cipher algorithmsubmitted to the eSTREAM Project of the eCRYPT network.In the final specification the cipher is called ACHTERBAHN-128/80,... |
2006 | 1 (hardware) | 80/128 | 80/128 | 297/351 | Brute force for frame lengths L ≤ 244. Correlation attack for L ≥ 248. | 280 resp. 2128 for L ≤ 244. |
| FISH FISH (cipher) The FISH stream cipher is a fast software based stream cipher using Lagged Fibonacci generators, plus a concept from the shrinking generator cipher. It was published by Siemens in 1993. FISH is quite fast in software and has a huge key length... |
1993 | Quite Fast (Wsoft) Computer software Computer software, or just software, is a collection of computer programs and related data that provide the instructions for telling a computer what to do and how to do it.... |
Variable | Known-plaintext attack Known-plaintext attack The known-plaintext attack is an attack model for cryptanalysis where the attacker has samples of both the plaintext , and its encrypted version . These can be used to reveal further secret information such as secret keys and code books... |
211 | ||
| Grain Grain (cipher) Grain is a stream cipher submitted to eSTREAM in 2004 by Martin Hell, Thomas Johansson and Willi Meier. It has been selected for the final eSTREAM portfolio for Profile 2 by the eSTREAM project. Grain is designed primarily for restricted hardware environments. It accepts an 80-bit key and a... |
Pre-2004 | Fast | 80 | 64 | 160 | Key-Derivation | 243 |
| HC-256 HC-256 HC-256 is a stream cipher designed to provide bulk encryption in software at high speeds while permitting strong confidence in its security. A 128-bit variant was submitted as an eSTREAM cipher candidate and has been selected as one of the four final contestants in the software profile.The... |
Pre-2004 | 4 (WP4) Pentium 4 Pentium 4 was a line of single-core desktop and laptop central processing units , introduced by Intel on November 20, 2000 and shipped through August 8, 2008. They had a 7th-generation x86 microarchitecture, called NetBurst, which was the company's first all-new design since the introduction of the... |
256 | 256 | 65536 | ||
| ISAAC ISAAC (cipher) ISAAC is a cryptographically secure pseudorandom number generator and a stream cipher designed by Robert J. Jenkins Jr. in 1996.- Operation :... |
1996 | 2.375 (W64-bit) 64-bit 64-bit is a word size that defines certain classes of computer architecture, buses, memory and CPUs, and by extension the software that runs on them. 64-bit CPUs have existed in supercomputers since the 1970s and in RISC-based workstations and servers since the early 1990s... - 4.6875 (W32-bit) 32-bit The range of integer values that can be stored in 32 bits is 0 through 4,294,967,295. Hence, a processor with 32-bit memory addresses can directly access 4 GB of byte-addressable memory.... |
8-8288 usually 40-256 |
N/A | 8288 | (2006) First-round Weak-Internal-State-Derivation |
4.67×101240 (2001) |
| MUGI MUGI In cryptography, MUGI is a pseudorandom number generator designed for use as a stream cipher. It has been recommended for Japanese government use by the CRYPTREC project.MUGI takes a 128-bit secret key and a 128-bit initial vector... |
1998–2002 | 128 | 128 | 1216 | N/A (2002) | ~282 | |
| PANAMA PANAMA Panama is a cryptography primitive which can be used both as a hash function and a stream cipher. Based on StepRightUp, it was designed by Joan Daemen and Craig Clapp and presented in the paper Fast Hashing and Stream Encryption with PANAMA on the Fast Software Encryption conference 1998... |
1998 | 2 | 256 | 128? | 1216? | Hash Collisions (2001) | 282 |
| Phelix Phelix Phelix is a high-speed stream cipher with a built-in single-pass message authentication code functionality, submitted in 2004 to the eSTREAM contest by Doug Whiting, Bruce Schneier, Stefan Lucks, and Frédéric Muller. The cipher uses only the operations of addition modulo 232, exclusive or, and... |
Pre-2004 | up to 8 (Wx86) X86 architecture The term x86 refers to a family of instruction set architectures based on the Intel 8086 CPU. The 8086 was launched in 1978 as a fully 16-bit extension of Intel's 8-bit based 8080 microprocessor and also introduced segmentation to overcome the 16-bit addressing barrier of such designs... |
256 + a 128-bit Nonce Cryptographic nonce In security engineering, nonce is an arbitrary number used only once to sign a cryptographic communication. It is similar in spirit to a nonce word, hence the name. It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused... |
128? | Differential (2006) | 237 | |
| Pike Pike (cipher) The Pike stream cipher was invented by Ross Anderson to be a "leaner and meaner" version of FISH after he broke FISH in 1994; the name is a humorous allusion to the Pike fish. The cipher combines ideas from A5 with the Lagged Fibonacci generators used in FISH. It is about 10% faster than FISH, yet... |
1994 | 0.9 x FISH FISH (cipher) The FISH stream cipher is a fast software based stream cipher using Lagged Fibonacci generators, plus a concept from the shrinking generator cipher. It was published by Siemens in 1993. FISH is quite fast in software and has a huge key length... (Wsoft) Computer software Computer software, or just software, is a collection of computer programs and related data that provide the instructions for telling a computer what to do and how to do it.... |
Variable | N/A (2004) | N/A (2004) | ||
| Py Py (cipher) Py is a stream cipher submitted to eSTREAM by Eli Biham and Jennifer Seberry. It is one of the fastest eSTREAM candidates at around 2.6 cycles per byte on some platforms... |
Pre-2004 | 2.6 | 8-2048? usually 40-256? |
64 | 8320 | Cryptanalytic Cryptanalysis Cryptanalysis is the study of methods for obtaining the meaning of encrypted information, without access to the secret information that is normally required to do so. Typically, this involves knowing how the system works and finding a secret key... Theory (2006) |
275 |
| Rabbit Rabbit (cipher) Rabbit is a high-speed stream cipher first presented in February 2003 at the 10th FSE workshop. In May 2005, it was submitted to the eSTREAM project of the ECRYPT network.... |
2003-Feb | 3.7(WP3) Pentium III The Pentium III brand refers to Intel's 32-bit x86 desktop and mobile microprocessors based on the sixth-generation P6 microarchitecture introduced on February 26, 1999. The brand's initial processors were very similar to the earlier Pentium II-branded microprocessors... -9.7(WARM7) ARM7TDMI ARM7 is a generation of ARM processor designs. This generation introduced the Thumb 16-bit instruction set providing improved code density compared to previous designs. The most widely used ARM7 designs implement the ARMv4T architecture, but some implement ARMv3 or ARMv5TEJ... |
128 | 64 | 512 | N/A (2006) | N/A (2006) |
| RC4 RC4 In cryptography, RC4 is the most widely used software stream cipher and is used in popular protocols such as Secure Sockets Layer and WEP... |
1987 | Impressive | 8-2048 usually 40-256 |
8 | 2064 | Shamir Adi Shamir Adi Shamir is an Israeli cryptographer. He is a co-inventor of the RSA algorithm , a co-inventor of the Feige–Fiat–Shamir identification scheme , one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography and computer... Initial-Bytes Key-Derivation OR KPA Known-plaintext attack The known-plaintext attack is an attack model for cryptanalysis where the attacker has samples of both the plaintext , and its encrypted version . These can be used to reveal further secret information such as secret keys and code books... |
213 OR 233 |
| Salsa20 Salsa20 Salsa20 is a stream cipher submitted to eSTREAM by Daniel Bernstein. It is built on a pseudorandom function based on 32-bit addition, bitwise addition and rotation operations, which maps a 256-bit key, a 64-bit nonce , and a 64-bit stream position to a 512-bit output... |
Pre-2004 | 4.24 (WG4) PowerPC G4 PowerPC G4 is a designation used by Apple Computer to describe a fourth generation of 32-bit PowerPC microprocessors. Apple has applied this name to various processor models from Freescale, a former part of Motorola.... - 11.84 (WP4) |
256 | a 64-bit Nonce + a 64-bit stream position | 512 | Probabilistic neutral bits method | 2251 for 8 rounds (2007) |
| Scream Scream (cipher) The Scream cipher is a word-based stream cipher developed by Shai Halevi, Don Coppersmith and Charanjit Jutla from IBM.The cipher is designed as a software efficient stream cipher. The authors describe the goal of the cipher to be a more secure version of the SEAL cipher.The general design of... |
2002 | 4 - 5 (Wsoft) Computer software Computer software, or just software, is a collection of computer programs and related data that provide the instructions for telling a computer what to do and how to do it.... |
128 + a 128-bit Nonce | 32? | 64-bit round function | ||
| SEAL SEAL (cipher) In cryptography, SEAL is a very fast stream cipher optimised for machines with a 32-bit word size and plenty of RAM. SEAL is actually a pseudorandom function family in that it can easily generate arbitrary portions of the keystream without having to start from the beginning... |
1997 | Very Fast (W32-bit) 32-bit The range of integer values that can be stored in 32 bits is 0 through 4,294,967,295. Hence, a processor with 32-bit memory addresses can directly access 4 GB of byte-addressable memory.... |
32? | ||||
| SNOW SNOW SNOW 1.0, SNOW 2.0, and SNOW 3G are word-based synchronous stream ciphers developed by Thomas Johansson and Patrik Ekdahl at Lund University.-History:... |
Pre-2003 | Very Good (W32-bit) 32-bit The range of integer values that can be stored in 32 bits is 0 through 4,294,967,295. Hence, a processor with 32-bit memory addresses can directly access 4 GB of byte-addressable memory.... |
128 OR 256 | 32 | |||
| SOBER-128 SOBER-128 SOBER-128 is a synchronous stream cipher designed by Hawkes and Rose and is a member of the SOBER family of ciphers. SOBER-128 was also designed to provide MAC functionality.... |
2003 | up to 128 | Message Forge | 2−6 | |||
| SOSEMANUK SOSEMANUK Sosemanuk is a stream cipher developed by Come Berbain, Olivier Billet, Anne Canteaut, Nicolas Courtois, Henri Gilbert, Louis Goubin, Aline Gouget, Louis Granboulan, Cédric Lauradoux, Marine Minier, Thomas Pornin and Hervé Sibert... |
Pre-2004 | Very Good (W32-bit) 32-bit The range of integer values that can be stored in 32 bits is 0 through 4,294,967,295. Hence, a processor with 32-bit memory addresses can directly access 4 GB of byte-addressable memory.... |
128 | 128 | |||
| Trivium Trivium (cipher) Trivium is a synchronous stream cipher designed to provide a flexible trade-off between speed and gate count in hardware, and reasonably efficient software implementation.... |
Pre-2004 | 4 (Wx86) X86 architecture The term x86 refers to a family of instruction set architectures based on the Intel 8086 CPU. The 8086 was launched in 1978 as a fully 16-bit extension of Intel's 8-bit based 8080 microprocessor and also introduced segmentation to overcome the 16-bit addressing barrier of such designs... - 8 (WLG) Logic gate A logic gate is an idealized or physical device implementing a Boolean function, that is, it performs a logical operation on one or more logic inputs and produces a single logic output. Depending on the context, the term may refer to an ideal logic gate, one that has for instance zero rise time and... |
80 | 80 | 288 | Brute force attack Brute force attack In cryptography, a brute-force attack, or exhaustive key search, is a strategy that can, in theory, be used against any encrypted data. Such an attack might be utilized when it is not possible to take advantage of other weaknesses in an encryption system that would make the task easier... (2006) |
2135 |
| Turing Turing (cipher) Turing is a stream cipher developed by Gregory G. Rose and Philip Hawkes at Qualcomm for CDMA. It is designed to be fast in software and achieves around 5.5 cycles/byte on some x86 processors.... |
2000–2003 | 5.5 (Wx86) X86 architecture The term x86 refers to a family of instruction set architectures based on the Intel 8086 CPU. The 8086 was launched in 1978 as a fully 16-bit extension of Intel's 8-bit based 8080 microprocessor and also introduced segmentation to overcome the 16-bit addressing barrier of such designs... |
160 | ||||
| VEST VEST VEST ciphers are a set of families of general-purpose hardware-dedicated ciphers that support single pass authenticated encryption and can operate as collision-resistant hash functions designed by Sean O'Neil, Benjamin Gittins and Howard Landman... |
2005 | 42 (WASIC) Application-specific integrated circuit An application-specific integrated circuit is an integrated circuit customized for a particular use, rather than intended for general-purpose use. For example, a chip designed solely to run a cell phone is an ASIC... - 64 (WFPGA) Field-programmable gate array A field-programmable gate array is an integrated circuit designed to be configured by the customer or designer after manufacturing—hence "field-programmable"... |
Variable usually 80-256 |
Variable usually 80-256 |
256 - 800 | N/A (2006) | N/A (2006) |
| WAKE | 1993 | Fast | 8192 | CPA Chosen-plaintext attack A chosen-plaintext attack is an attack model for cryptanalysis which presumes that the attacker has the capability to choose arbitrary plaintexts to be encrypted and obtain the corresponding ciphertexts. The goal of the attack is to gain some further information which reduces the security of the... & CCA Chosen-ciphertext attack A chosen-ciphertext attack is an attack model for cryptanalysis in which the cryptanalyst gathers information, at least in part, by choosing a ciphertext and obtaining its decryption under an unknown key. In the attack, an adversary has a chance to enter one or more known ciphertexts into the... |
Vulnerable | ||
| Stream Cipher |
Creation Date |
Speed (cycles per byte Cycles per byte Cycles per byte is a unit of measurement which indicates the number of clock cycles a microprocessor will perform per byte of data processed in an algorithm. It is commonly used as a partial indicator of real-world performance in cryptographic functions.... ) |
(bits) | Attack | |||
| Effective Key- Key (cryptography) In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa... Length Key size In cryptography, key size or key length is the size measured in bits of the key used in a cryptographic algorithm . An algorithm's key length is distinct from its cryptographic security, which is a logarithmic measure of the fastest known computational attack on the algorithm, also measured in bits... |
Initialization vector Initialization vector In cryptography, an initialization vector is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom... |
Internal State |
Best Known | Computational Complexity |
|||
Trivia
- United States National Security AgencyNational Security AgencyThe National Security Agency/Central Security Service is a cryptologic intelligence agency of the United States Department of Defense responsible for the collection and analysis of foreign communications and foreign signals intelligence, as well as protecting U.S...
documents sometimes use the term combiner-type algorithms, referring to algorithms that use some function to combine a pseudorandom number generatorPseudorandom number generatorA pseudorandom number generator , also known as a deterministic random bit generator , is an algorithm for generating a sequence of numbers that approximates the properties of random numbers...
(PRNG) with a plaintextPlaintextIn cryptography, plaintext is information a sender wishes to transmit to a receiver. Cleartext is often used as a synonym. Before the computer era, plaintext most commonly meant message text in the language of the communicating parties....
stream.
External links
- [ftp://ftp.rsasecurity.com/pub/pdfs/tr701.pdf RSA technical report on stream cipher operation.]
- Analysis of Lightweight Stream Ciphers (thesis by S. Fischer).
- SVG Animation of simple stream cipher

