
Critical Infrastructure Protection
Encyclopedia
Critical infrastructure protection (CIP) is a concept that relates to the preparedness and response to serious incidents that involve the critical infrastructure
of a region or nation.
The American Presidential directive
PDD-63 of May 1998 set up a national program of "Critical Infrastructure Protection".
In Europe the equivalent 'European Programme for Critical Infrastructure Protection' (EPCIP) refers to the doctrine or specific programs created as a result of the European Commission
's directive EU COM(2006) 786 which designates European critical infrastructure that, in case of fault, incident or attack, could impact both the country where it is hosted and at least one other European Member State
. Member states are obliged to adopt the 2006 directive into their national statutes.
. In May 1998, President Bill Clinton
issued Presidential directive
PDD-63 on the subject of Critical Infrastructure Protection. This recognized certain parts of the national infrastructure
as critical to the national and economic security of the United States and the well-being of its citizenry, and required steps to be taken to protect it.
This was updated on December 17, 2003 by President Bush through Homeland Security Presidential Directive HSPD-7 for Critical Infrastructure Identification, Prioritization, and Protection. The directive broadened the definition of infrastructure in accordance with the Patriot Act, as the physical and virtual systems that are ' so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety.'
Take, for example, a computer virus
that disrupts the distribution of natural gas
across a region. This could lead to a consequential reduction in electrical power generation
, which in turn leads to the forced shutdown of computerized controls
and communications. Road traffic, air traffic, and rail transportation might then become affected. Emergency services might also be hampered.
 An entire region can become debilitated because some critical elements in the infrastructure become disabled through natural disaster
An entire region can become debilitated because some critical elements in the infrastructure become disabled through natural disaster
. While potentially in contravention of the Geneva Conventions
, military forces have also recognized that it can cripple an enemy's ability to resist by attacking key elements of its civilian and military infrastructure.
The federal government has developed a standardized description of critical infrastructure, in order to facilitate monitoring and preparation for disabling events. The government requires private industry in each critical economic sector to:

In 2003 the remit was expanded to include:
With much of the critical infrastructure privately owned, the Department of Defense
(DoD) depends on commercial infrastructure to support its normal operations. The Department of State
and the Central Intelligence Agency
are also involved in foreign affairs
and intelligence analysis
with friendly countries.
In May 2007 the DHS completed its sector-specific plans (SSP) for co-ordinating and dealing with critical events.
warned the United States Congress
of a cyber terrorist "electronic Pearl Harbor
" saying, "It is not going to be against Navy ships sitting in a Navy shipyard. It is going to be against commercial infrastructure…." Later this fear was qualified by President Clinton after reports of actual cyber terrorist attacks in 2000: "I think it was an alarm. I don't think it was Pearl Harbor. We lost our Pacific fleet at Pearl Harbor. I don't think the analogous loss was that great."
There are many examples of computer systems that have been hacked or victims of extortion. One such example occurred in September 1995 where a Russian national allegedly masterminded the break-in of Citicorp's electronic funds transfer
system and was ordered to stand trial in the United States. A gang of hackers
under his leadership had breached Citicorp's security 40 times during 1994. They were able to transfer $12 million from customer accounts and withdraw an estimated $400,000.
In the past, the systems and networks of the infrastructure elements were physically and logically independent and separate. They had little interaction or connection with each other or other sectors of the infrastructure. With advances in technology, the systems within each sector became automated, and interlinked through computers and communications facilities. As a result, the flow of electricity, oil, gas, and telecommunications throughout the country are linked - albeit sometimes indirectly - but the resulting linkages blur traditional security borders.
While this increased reliance on interlinked capabilities helps make the economy and nation more efficient and perhaps stronger, it also makes the country more vulnerable to disruption and attack. This interdependent and interrelated infrastructure is more vulnerable to physical and cyber disruptions because it has become a complex system with single points of failure. In the past an incident that would have been an isolated failure can now cause widespread disruption because of cascading effects. As an example, capabilities within the information and communication sector have enabled the United States to reshape its government and business processes, while becoming increasingly software driven. One catastrophic failure in this sector now has the potential bring down multiple systems including air traffic control, emergency services, banking, trains, electrical power, and dam control.
The elements of the infrastructure themselves are also considered possible targets of terrorism
. Traditionally, critical infrastructure elements have been lucrative targets for anyone wanting to attack another country. Now, because the infrastructure has become a national life-line, terrorists can achieve high economic and political value by attacking elements of it. Disrupting or even disabling the infrastructure may reduce the ability to defend the nation, erode public confidence in critical services, and reduce economic strength. Additionally, well chosen terrorist attacks can become easier and less costly than traditional warfare because of the interdependence of infrastructure elements. These infrastructure elements can become easier targets where there is a low probability of detection.
The elements of the infrastructure are also increasingly vulnerable to a dangerous mix of traditional and nontraditional types of threats. Traditional and non-traditional threats include equipment failures, human error, weather and natural causes, physical attacks, and cyber attacks. For each of these threats, the cascading effect caused by single points of failure has the potential to pose dire and far-reaching consequences.
Although efforts are under way, there is no unified national capability to protect the interrelated aspects of the country's infrastructure. One reason for this is that a good understanding of the inter-relationships does not exist. There is also no consensus on how the elements of the infrastructure mesh together, or how each element functions and affects the others. Securing national infrastructure depends on understanding the relationships among its elements. Thus when one sector scheduled a 3-week drill to mimic the effects of a pandemic flu, even though two-thirds of the participants claimed to have business continuity
plans in place, barely half reported that their plan was moderately effective.
Critical infrastructure protection requires the development of a national capability to identify and monitor the critical elements and to determine when and if the elements are under attack or are the victim of destructive natural occurrences. CIP is important because it is the link between risk management and infrastructure assurance. It provides the capability needed to eliminate potential vulnerabilities in the critical infrastructure.
CIP practitioners determine vulnerabilities and analyze alternatives in order to prepare for incidents. They focus on improving the capability to detect and warn of impending attacks on, and system failures within, the critical elements of the national infrastructure.
The different entities of the national CIP structure work together as a partnership between the government and the public sectors. Each department and agency of the federal government is responsible for protecting its portion of the government's critical infrastructure. In addition, there are grants made available through the Department of Homeland Security for municipal and private entities to use for CIP and security purposes.
These include grants for emergency management, water security training, rail, transit and port security, metropolitan medical response, LEA
terrorism prevention programs and the Urban Areas Security Initiative.
PDD-63 identified certain functions related to critical infrastructure protection that must be performed chiefly by the federal government. These are national defense, foreign affairs, intelligence, and law enforcement. Each lead agency for these special functions appoints a senior official to serve as a functional coordinator for the federal government. In 2008 a mobile PDA based Vulnerability Assessment Security Survey Tool (VASST) was introduced to speed physical security assessment of critical infrastructure by law enforcement to meet compliance requirements of PDD-63.
In addition, each department and agency of the federal government was responsible for developing its own CIP plan for protecting its portion of the federal government's critical infrastructure. The federal department and agency plans were assimilated with the sector NIAPs to create one comprehensive National Infrastructure Assurance Plan. Additionally the national structure must ensure there is a national CIP program. This program includes responsibilities such as education and awareness, threat assessment and investigation, and research.
The process includes assessments of:
. Commentators note that these initiatives started directly after the collapse of the Cold War
, raising the concern that this was simply a diversion of the military-industrial complex away from a funding area which was shrinking and into a richer previously civilian arena.
Grants have been distributed across the different states even though the perceived risk is not evenly spread, leading to accusations of pork barrel
politics that directs money and jobs towards marginal voting areas.
The Urban Areas Security Initiative grant program has been particularly controversial, with the 2006 infrastructure list covering 77,000 assets, including a popcorn factory and a hot dog stand. The 2007 criteria were reduced to 2,100 and now those facilities must make a much stronger case to become eligible for grants.
While well-intentioned, some of the results have also been questioned regarding claims of poorly-designed and intrusive security theater
that distracts attention and money from more pressing issues or creates damaging side effects.
An absence of comparative risk analysis and benefits tracking it has made it difficult to counter such allegations with authority. In order to better understand this, and ultimately direct effort more productively, a Risk Management and Analysis Office was recently created in the National Protection and Programs directorate at the Department of Homeland Security.
PDD 63 identified the responsibilities DoD had for critical infrastructure protection. First, DoD had to identify its own critical assets and infrastructures and provide assurance through analysis, assessment, and remediation. DoD was also responsible for identifying and monitoring the national and international infrastructure requirements of industry and other government agencies, all of which needed to be included in the protection planning. DoD also addressed the assurance and protection of commercial assets and infrastructure services in DoD acquisitions. Other DoD responsibilities for CIP included assessing the potential impact on military operations that would result from the loss or compromise of infrastructure service. There were also requirements for monitoring DoD operations, detecting and responding to infrastructure incidents, and providing department indications and warnings as part of the national process. Ultimately, DoD was responsible for supporting national critical infrastructure protection.
In response to the requirements identified in PDD 63, DoD categorized its own critical assets by sector, in a manner similar to the national CIP organization. The DoD identified a slightly different list of infrastructure sectors for those areas that specifically required protection by DoD. DoD’s organizational structure for critical infrastructure protection reflects, complements, and effectively interacts with the national structure for CIP.
DoD’s special function components currently include seven areas of focus. They include the following components:
It was deemed that it was nearly impossible to protect every critical asset at every location, therefore the focus was directed on protecting the critical Defense Infrastructure. The critical Defense Infrastructure is the critical assets essential to providing mission assurance.
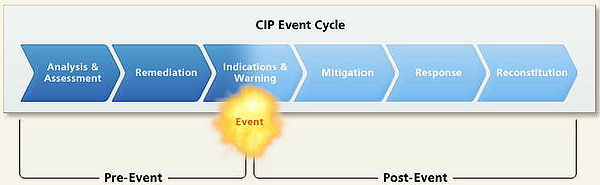
Effective management of the CIP life cycle ensures that protection activities can be coordinated and reconciled among all DoD sectors. In many ways, DoD CIP, is risk management at its most imperative. Achieving success means obtaining mission assurance. Missing the mark can mean mission failure as well as human and material losses. For critical infrastructure protection, risk management requires leveraging resources to address the most critical infrastructure assets that are also the most vulnerable and that have the greatest threat exposure.
The most important part of the CIP lifecye is Phase 1. Because it is crucial to target the right assets for infrastructure protection, determining these assets is the first phase in the CIP life cycle. This phase, Analysis and Assessment, is the key and foundation of the seven lifecycle activities. Without a solid foundation, the remaining CIP life cycle phases may be flawed, resulting in a CIP plan that fails to protect the critical infrastructure and, therefore, mission assurance.
The Defense Infrastructure, or DI, is organized into ten sectors. Each sector is composed of assets, such as systems, programs, people, equipment, or facilities. Assets may be simple, such as one facility within one geographic location, or complex, involving geographically dispersed links and nodes.
The Analysis and Assessment is made up of five steps that include activities that span and encompass the ten DI sectors and their assets.
USPACOM focused the Analysis and Assessment phase by organizing its activities to answer three major questions:
To answer the question, “What is critical?”, USPACOM outlined a three-step procedure:
To accomplish these steps, USPACOM adopted a methodology that focuses its CIP efforts on Tier 1 assets. Tier 1 assets are assets that could cause mission failure if they are compromised or damaged. The methodology UAPACOM adopted and modified is Mission Area Analysis, or MAA. The MAA links combatant command missions to infrastructure assets that are critical to a given Operations Plan, or OPLAN, Contingency Plan, or CONPLAN, or Crisis Action Plan. Typically, the MAA process determines the assessment site priorities. USPACOM modified the process and selected the CIP assessment sites and installations prior to conducting the MAA. The following is an illustration of the USPACOM MAA process:
USPACOM uses the MAA data it gathers to scope and focus its efforts on truly mission-critical assets to answer the next question in its process, Is it vulnerable?
The first step in answering this question is to complete an installation analysis. The next step is to complete a commercial infrastructure analysis. USPACOM relied upon two different DoD organizations for CIP assessments: Balanced Survivability Assessments, or BSAs, and Mission Assurance Assessments. The BSA is a two-week mission-focused assessment at a military installation or designated site. A Mission Assurance Assessment is unique because it uses an area assessment approach to focus on both commercial and military asset vulnerabilities and dependencies. The final step to determine vulnerabilities is to integrate the two analyses and assessments. With its critical assets and their vulnerabilities identified, USPACOM is ready to perform risk management activities to decide what can be done to protect the mission-critical assets.
Booz Allen Hamilton developed this process at PACOM.
The second phase is the Remediation phase. In the Remediation phase, the known weaknesses and vulnerabilities are addressed. Remediation actions are deliberate, precautionary measures designed to fix known virtual and physical vulnerabilities before an event occurs. The purpose of remediation is to improve the reliability, availability, and survivability of critical assets and infrastructures. Remediation actions apply to any type of vulnerability, regardless of its cause. They apply to acts of nature, technology failures, or deliberate malicious actions.
The cost of each remediation action depends on the nature of the vulnerability it addresses. The Defense Infrastructure Sector Assurance Plan that each infrastructure sector must develop, establishes the priorities and resources for remediation. Remediation requirements are determined by multiple factors. These are analysis and assessment, input from military planners and other DoD sectors, the National Infrastructure Assurance Plan and other plans, reports, and information on national infrastructure vulnerabilities and remediation, as well as intelligence estimates and assessments of threats.
Remediation requirements are also gathered through lessons learned from Defense Infrastructure sector monitoring and reporting and infrastructure protection operations and exercises. The CIP program tracks the status of remediation activities for critical assets. Remediation activities to protect the critical Defense Infrastructure cross multiple Department components.
Indications and warnings are actions or infrastructure conditions that signal an event is either”
Historically, DoD event indications have focused and relied on intelligence information about foreign developments. These event indications have been expanded to include all potential infrastructure disruption or degradation, regardless of its cause. DoD CIP indications are based on four levels of input:
This fusion of traditional intelligence information with sector-specific information has been determined to be essential for meaningful CIP indications.
If an indication is detected, a warning notifying the appropriate asset owners of a possible or occurring event or hazard can be issued. The sector’s assurance plan determines what conditions and actions are monitored and reported for each Defense Infrastructure Sector.
Each sector must develop a written Defense Sector Assurance Plan that includes a compendium of sector incidents for monitoring and reporting. The sector incident compendium is made up of three types of incidents:
DoD critical asset owners, installations, and sector CIAOs determine the DoD and sector-defined incidents. Each of the reportable incidents or classes of incidents must include the following components:
The National Infrastructure Protection Center, or NIPC, is the primary national warning center for significant infrastructure attacks. Critical asset owners, DoD installations, and Sector CIAOs monitor the infrastructure daily. Indications of an infrastructure incident are reported to the National Military Command Center, or NMCC. If indications are on a computer network, they are also reported to the Joint Task Force Computer Network Operations, or JTF-CNO. The NMCC and JTF-CNO assess the indications and pass them to the NIPC and appropriate DoD organizations. When the NIPC determines that an infrastructure event is likely to occur, is planned, or is under way, it issues a national warning. For DoD, the NIPC passes its warnings and alerts to the NMCC and JTF-CNO. These warnings and alerts are then passed to the DoD components. The warning may include guidance regarding additional protection measures DoD should take.
The Mitigation phase (Phase 4), is made up of preplanned coordinated actions in response to infrastructure warnings or incidents. Mitigation actions are taken before or during an infrastructure event. These actions are designed to minimize the operational impact of the loss of a critical asset, facilitate incident response, and quickly restore the infrastructure service.
A primary purpose of the Mitigation phase is to minimize the operational impact on other critical Defense Infrastructures and assets when a critical asset is lost or damaged. As am example, if there is a U.S. installation, Site A, located in a host nation. Site A is a tier 1 asset, meaning that if it fails, the Combatant Commands mission fails. Site A has mutual Global Information Grid Command Control, or GIG/C2, information interdependencies with Sites B and C. In addition, other Defense Infrastructure sectors rely on Site A for mission capabilities. In this scenario, what could be the impact if the supply line to the commercial power plant that provides the installation’s primary power is accidentally severed. Because of all the interdependencies, losing this asset is more than the loss of just one site. It means the loss of other sector capabilities.
A possible mitigation action might be for Site A to go on backup power.
An alternate action could be to pass complete control of Site A’s functionality to another site, where redundancy has been previously arranged. These actions would limit the impact of this incident on the other sites and related sectors. In addition to lessening the operational impact of a critical infrastructure event, the Mitigation phase of the CIP life cycle supports and complements two other life cycle phases. Mitigation actions aid in the emergency, investigation, and management activities of Phase 5, Incident Response. They also facilitate the reconstitution activities of Phase 6.
During the Mitigation phase, DoD critical asset owners, DoD installations, and Sector Chief Infrastructure Assurance Officers, or CIAOs, work with the National Military Command Center, or NMCC, and the Joint Task Force-Computer Network Operations, or JTF-CNO, to develop, train for, and exercise mitigation responses for various scenarios. When there is a warning, emergency, or infrastructure incident, the critical asset owners, installations, and Sector CIAOs initiate mitigation actions to sustain service to the DoD. They also provide mitigation status information to the NMCC and JTF-CNO. The NMCC monitors for consequences from an event within one Defense Infrastructure sector that are significant enough to affect other sectors. For events that cross two or more sectors, the NMCC advises on the prioritization and coordination of mitigation actions. When event threats or consequences continue to escalate, the NMCC directs mitigation actions by sector to ensure a coordinated response across the DoD. The NMCC and the JTF-CNO keep the National Infrastructure Protection Center, or NIPC, apprised of any significant mitigation activities.
When incidents compromise a DoD computer network, the Joint Task Force-Computer Network Operations, or JTF-CNO, directs the response activities. These activities are designed to stop the computer network attack, contain and mitigate damage to a DoD information network and then restore minimum required functionality. JTF-CNO also requests and coordinates any support or assistance from other Federal agencies and civilian organizations during incidents affecting a DoD network. When incidents impact any other DoD owned assets, installation commanders and critical asset owners follow traditional channels and procedures to coordinate responses. This includes notifying affected Sector Chief Infrastructure Assurance Officers, or CIAOs, in the initial notice and status reporting. Although third parties play a major role in the response to Defense Infrastructure events, DoD CIP personnel also have responsibilities to fulfill.
Critical infrastructure
Critical infrastructure is a term used by governments to describe assets that are essential for the functioning of a society and economy. Most commonly associated with the term are facilities for:*electricity generation, transmission and distribution;...
of a region or nation.
The American Presidential directive
Presidential directive
Presidential Directives, better known as Presidential Decision Directives or PDD are a form of an executive order issued by the President of the United States with the advice and consent of the National Security Council...
PDD-63 of May 1998 set up a national program of "Critical Infrastructure Protection".
In Europe the equivalent 'European Programme for Critical Infrastructure Protection' (EPCIP) refers to the doctrine or specific programs created as a result of the European Commission
European Commission
The European Commission is the executive body of the European Union. The body is responsible for proposing legislation, implementing decisions, upholding the Union's treaties and the general day-to-day running of the Union....
's directive EU COM(2006) 786 which designates European critical infrastructure that, in case of fault, incident or attack, could impact both the country where it is hosted and at least one other European Member State
Member State of the European Union
A member state of the European Union is a state that is party to treaties of the European Union and has thereby undertaken the privileges and obligations that EU membership entails. Unlike membership of an international organisation, being an EU member state places a country under binding laws in...
. Member states are obliged to adopt the 2006 directive into their national statutes.
History of the US CIP
The US CIP is a national program to assure the security of vulnerable and interconnected infrastructures of the United StatesUnited States
The United States of America is a federal constitutional republic comprising fifty states and a federal district...
. In May 1998, President Bill Clinton
Bill Clinton
William Jefferson "Bill" Clinton is an American politician who served as the 42nd President of the United States from 1993 to 2001. Inaugurated at age 46, he was the third-youngest president. He took office at the end of the Cold War, and was the first president of the baby boomer generation...
issued Presidential directive
Presidential directive
Presidential Directives, better known as Presidential Decision Directives or PDD are a form of an executive order issued by the President of the United States with the advice and consent of the National Security Council...
PDD-63 on the subject of Critical Infrastructure Protection. This recognized certain parts of the national infrastructure
Infrastructure
Infrastructure is basic physical and organizational structures needed for the operation of a society or enterprise, or the services and facilities necessary for an economy to function...
as critical to the national and economic security of the United States and the well-being of its citizenry, and required steps to be taken to protect it.
This was updated on December 17, 2003 by President Bush through Homeland Security Presidential Directive HSPD-7 for Critical Infrastructure Identification, Prioritization, and Protection. The directive broadened the definition of infrastructure in accordance with the Patriot Act, as the physical and virtual systems that are ' so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety.'
Overview
The systems and networks that make up the infrastructure of society are often taken for granted, yet a disruption to just one of those systems can have dire consequences across other sectors.Take, for example, a computer virus
Computer virus
A computer virus is a computer program that can replicate itself and spread from one computer to another. The term "virus" is also commonly but erroneously used to refer to other types of malware, including but not limited to adware and spyware programs that do not have the reproductive ability...
that disrupts the distribution of natural gas
Pipeline transport
Pipeline transport is the transportation of goods through a pipe. Most commonly, liquids and gases are sent, but pneumatic tubes that transport solid capsules using compressed air are also used....
across a region. This could lead to a consequential reduction in electrical power generation
Electricity generation
Electricity generation is the process of generating electric energy from other forms of energy.The fundamental principles of electricity generation were discovered during the 1820s and early 1830s by the British scientist Michael Faraday...
, which in turn leads to the forced shutdown of computerized controls
SCADA
SCADA generally refers to industrial control systems : computer systems that monitor and control industrial, infrastructure, or facility-based processes, as described below:...
and communications. Road traffic, air traffic, and rail transportation might then become affected. Emergency services might also be hampered.

Natural disaster
A natural disaster is the effect of a natural hazard . It leads to financial, environmental or human losses...
. While potentially in contravention of the Geneva Conventions
Geneva Conventions
The Geneva Conventions comprise four treaties, and three additional protocols, that establish the standards of international law for the humanitarian treatment of the victims of war...
, military forces have also recognized that it can cripple an enemy's ability to resist by attacking key elements of its civilian and military infrastructure.
The federal government has developed a standardized description of critical infrastructure, in order to facilitate monitoring and preparation for disabling events. The government requires private industry in each critical economic sector to:
- Assess its vulnerabilities to both physical or cyber attacks,
- Plan to eliminate significant vulnerabilities;
- Develop systems to identify and prevent attempted attacks;
- Alert, contain and rebuff attacks and then, with the Federal Emergency Management AgencyFederal Emergency Management AgencyThe Federal Emergency Management Agency is an agency of the United States Department of Homeland Security, initially created by Presidential Reorganization Plan No. 1 of 1978 and implemented by two Executive Orders...
(FEMA), to rebuild essential capabilities in the aftermath.
Infrastructure sectors
CIP defines sectors and organizational responsibilities in a standard way:- Banking and financeBankA bank is a financial institution that serves as a financial intermediary. The term "bank" may refer to one of several related types of entities:...
: - The Department of the TreasuryUnited States Department of the TreasuryThe Department of the Treasury is an executive department and the treasury of the United States federal government. It was established by an Act of Congress in 1789 to manage government revenue...
is responsible for co-ordinating the protection of not just systems but also maintaining public confidenceBank runA bank run occurs when a large number of bank customers withdraw their deposits because they believe the bank is, or might become, insolvent...
, through industry initiatives such as the Financial Services Information Sharing and Analysis Centre
- TransportTransportTransport or transportation is the movement of people, cattle, animals and goods from one location to another. Modes of transport include air, rail, road, water, cable, pipeline, and space. The field can be divided into infrastructure, vehicles, and operations...
ation: - The Department of TransportationUnited States Department of TransportationThe United States Department of Transportation is a federal Cabinet department of the United States government concerned with transportation. It was established by an act of Congress on October 15, 1966, and began operation on April 1, 1967...
is responsible for protecting the road, rail, air, and water transportation infrastructure, including computer-controlled just-in-time delivery systems, optimization of distribution through hubsTransportation hubA transport hub is a place where passengers and cargo are exchanged between vehicles or between transport modes. Public transport hubs include train stations, rapid transit stations, bus stops, tram stop, airports and ferry slips. Freight hubs include classification yards, seaports and truck...
, and traffic and operations centers that are consolidated into key locations, and regulation of the transport of hazardous materials.
- Power: - The Department of EnergyUnited States Department of EnergyThe United States Department of Energy is a Cabinet-level department of the United States government concerned with the United States' policies regarding energy and safety in handling nuclear material...
oversees energy suppliesEnergy supplyEnergy supply is the delivery of fuels or transformed fuels to point of consumption. It potentially encompasses the extraction, transmission, generation, distribution and storage of fuels...
including electricity, oil, and gas, and works with the Nuclear Regulatory CommissionNuclear Regulatory CommissionThe Nuclear Regulatory Commission is an independent agency of the United States government that was established by the Energy Reorganization Act of 1974 from the United States Atomic Energy Commission, and was first opened January 19, 1975...
for the protection of nuclear materials and power. Note that CIP in this sector is different from energy securityEnergy securityEnergy security is a term for an association between national security and the availability of natural resources for energy consumption. Access to cheap energy has become essential to the functioning of modern economies. However, the uneven distribution of energy supplies among countries has led...
, which is the politics and economics of supply. Additionally, operating under the auspices of the Federal Energy Regulatory CommissionFederal Energy Regulatory CommissionThe Federal Energy Regulatory Commission is the United States federal agency with jurisdiction over interstate electricity sales, wholesale electric rates, hydroelectric licensing, natural gas pricing, and oil pipeline rates...
is the North American Electric Reliability Corporation (NERC), a non-profit organizationNon-profit organizationNonprofit organization is neither a legal nor technical definition but generally refers to an organization that uses surplus revenues to achieve its goals, rather than distributing them as profit or dividends...
that defines and enforces reliability standards for the bulk power system.
- Information and communications: - Overseen by the Department of Commerce, most areas of life rely on telecommunications and information technology.

- Federal and municipal services: - Overseen jointly by Federal and State agencies. They guarantee continuity of government at the federal, state, and local levels to meet for provision of essential services.
- Emergency services: - Overseen by the Health and Human ServicesUnited States Department of Health and Human ServicesThe United States Department of Health and Human Services is a Cabinet department of the United States government with the goal of protecting the health of all Americans and providing essential human services. Its motto is "Improving the health, safety, and well-being of America"...
, this includes emergency health servicesEmergency medical servicesEmergency medical services are a type of emergency service dedicated to providing out-of-hospital acute medical care and/or transport to definitive care, to patients with illnesses and injuries which the patient, or the medical practitioner, believes constitutes a medical emergency...
and public healthPublic healthPublic health is "the science and art of preventing disease, prolonging life and promoting health through the organized efforts and informed choices of society, organizations, public and private, communities and individuals" . It is concerned with threats to health based on population health...
- Fire departments: - Overseen by the Federal Emergency Management Agency FEMAFederal Emergency Management AgencyThe Federal Emergency Management Agency is an agency of the United States Department of Homeland Security, initially created by Presidential Reorganization Plan No. 1 of 1978 and implemented by two Executive Orders...
.
- Law enforcement agenciesLaw enforcement agencyIn North American English, a law enforcement agency is a government agency responsible for the enforcement of the laws.Outside North America, such organizations are called police services. In North America, some of these services are called police while others have other names In North American...
: - Overseen jointly by the Department of JusticeUnited States Department of JusticeThe United States Department of Justice , is the United States federal executive department responsible for the enforcement of the law and administration of justice, equivalent to the justice or interior ministries of other countries.The Department is led by the Attorney General, who is nominated...
and the Federal Bureau of InvestigationFederal Bureau of InvestigationThe Federal Bureau of Investigation is an agency of the United States Department of Justice that serves as both a federal criminal investigative body and an internal intelligence agency . The FBI has investigative jurisdiction over violations of more than 200 categories of federal crime...
to ensure the orderly running of activities during times of threat or crises.
- Public worksPublic worksPublic works are a broad category of projects, financed and constructed by the government, for recreational, employment, and health and safety uses in the greater community...
: - Overseen by the United States Environmental Protection AgencyUnited States Environmental Protection AgencyThe U.S. Environmental Protection Agency is an agency of the federal government of the United States charged with protecting human health and the environment, by writing and enforcing regulations based on laws passed by Congress...
. This includes safe water systems and drainage.
In 2003 the remit was expanded to include:
- Agriculture and food, with the Department of AgricultureUnited States Department of AgricultureThe United States Department of Agriculture is the United States federal executive department responsible for developing and executing U.S. federal government policy on farming, agriculture, and food...
overseeing the safe supply of meat, poultry, and egg products.
- National monuments and icons, under the Department of the InteriorUnited States Department of the InteriorThe United States Department of the Interior is the United States federal executive department of the U.S. government responsible for the management and conservation of most federal land and natural resources, and the administration of programs relating to Native Americans, Alaska Natives, Native...
With much of the critical infrastructure privately owned, the Department of Defense
United States Department of Defense
The United States Department of Defense is the U.S...
(DoD) depends on commercial infrastructure to support its normal operations. The Department of State
United States Department of State
The United States Department of State , is the United States federal executive department responsible for international relations of the United States, equivalent to the foreign ministries of other countries...
and the Central Intelligence Agency
Central Intelligence Agency
The Central Intelligence Agency is a civilian intelligence agency of the United States government. It is an executive agency and reports directly to the Director of National Intelligence, responsible for providing national security intelligence assessment to senior United States policymakers...
are also involved in foreign affairs
Foreign Affairs
Foreign Affairs is an American magazine and website on international relations and U.S. foreign policy published since 1922 by the Council on Foreign Relations six times annually...
and intelligence analysis
Intelligence analysis
Intelligence analysis is the process of taking known information about situations and entities of strategic, operational, or tactical importance, characterizing the known, and, with appropriate statements of probability, the future actions in those situations and by those entities...
with friendly countries.
In May 2007 the DHS completed its sector-specific plans (SSP) for co-ordinating and dealing with critical events.
The importance of CIP
On March 9, 1999: Deputy Defense Secretary John HamreJohn Hamre
John J. Hamre is a specialist in international studies, a former Washington bureaucrat and the current president and CEO of the Center for Strategic and International Studies, a position he has held with that think tank since April 2000.-Education:Hamre is the son of Melvin Sanders and Ruth Lucile...
warned the United States Congress
United States Congress
The United States Congress is the bicameral legislature of the federal government of the United States, consisting of the Senate and the House of Representatives. The Congress meets in the United States Capitol in Washington, D.C....
of a cyber terrorist "electronic Pearl Harbor
Attack on Pearl Harbor
The attack on Pearl Harbor was a surprise military strike conducted by the Imperial Japanese Navy against the United States naval base at Pearl Harbor, Hawaii, on the morning of December 7, 1941...
" saying, "It is not going to be against Navy ships sitting in a Navy shipyard. It is going to be against commercial infrastructure…." Later this fear was qualified by President Clinton after reports of actual cyber terrorist attacks in 2000: "I think it was an alarm. I don't think it was Pearl Harbor. We lost our Pacific fleet at Pearl Harbor. I don't think the analogous loss was that great."
There are many examples of computer systems that have been hacked or victims of extortion. One such example occurred in September 1995 where a Russian national allegedly masterminded the break-in of Citicorp's electronic funds transfer
Electronic funds transfer
Electronic funds transfer is the electronic exchange or transfer of money from one account to another, either within a single financial institution or across multiple institutions, through computer-based systems....
system and was ordered to stand trial in the United States. A gang of hackers
Black hat
A black hat is the villain or bad guy, especially in a western movie in which such a character would stereotypically wear a black hat in contrast to the hero's white hat, especially in black and white movies....
under his leadership had breached Citicorp's security 40 times during 1994. They were able to transfer $12 million from customer accounts and withdraw an estimated $400,000.
In the past, the systems and networks of the infrastructure elements were physically and logically independent and separate. They had little interaction or connection with each other or other sectors of the infrastructure. With advances in technology, the systems within each sector became automated, and interlinked through computers and communications facilities. As a result, the flow of electricity, oil, gas, and telecommunications throughout the country are linked - albeit sometimes indirectly - but the resulting linkages blur traditional security borders.
While this increased reliance on interlinked capabilities helps make the economy and nation more efficient and perhaps stronger, it also makes the country more vulnerable to disruption and attack. This interdependent and interrelated infrastructure is more vulnerable to physical and cyber disruptions because it has become a complex system with single points of failure. In the past an incident that would have been an isolated failure can now cause widespread disruption because of cascading effects. As an example, capabilities within the information and communication sector have enabled the United States to reshape its government and business processes, while becoming increasingly software driven. One catastrophic failure in this sector now has the potential bring down multiple systems including air traffic control, emergency services, banking, trains, electrical power, and dam control.
The elements of the infrastructure themselves are also considered possible targets of terrorism
Terrorism
Terrorism is the systematic use of terror, especially as a means of coercion. In the international community, however, terrorism has no universally agreed, legally binding, criminal law definition...
. Traditionally, critical infrastructure elements have been lucrative targets for anyone wanting to attack another country. Now, because the infrastructure has become a national life-line, terrorists can achieve high economic and political value by attacking elements of it. Disrupting or even disabling the infrastructure may reduce the ability to defend the nation, erode public confidence in critical services, and reduce economic strength. Additionally, well chosen terrorist attacks can become easier and less costly than traditional warfare because of the interdependence of infrastructure elements. These infrastructure elements can become easier targets where there is a low probability of detection.
The elements of the infrastructure are also increasingly vulnerable to a dangerous mix of traditional and nontraditional types of threats. Traditional and non-traditional threats include equipment failures, human error, weather and natural causes, physical attacks, and cyber attacks. For each of these threats, the cascading effect caused by single points of failure has the potential to pose dire and far-reaching consequences.
Challenges
There are fears that the frequency and severity of critical infrastructure incidents will increase in the future.Although efforts are under way, there is no unified national capability to protect the interrelated aspects of the country's infrastructure. One reason for this is that a good understanding of the inter-relationships does not exist. There is also no consensus on how the elements of the infrastructure mesh together, or how each element functions and affects the others. Securing national infrastructure depends on understanding the relationships among its elements. Thus when one sector scheduled a 3-week drill to mimic the effects of a pandemic flu, even though two-thirds of the participants claimed to have business continuity
Business continuity
Business continuity is the activity performed by an organization to ensure that critical business functions will be available to customers, suppliers, regulators, and other entities that must have access to those functions. These activities include many daily chores such as project management,...
plans in place, barely half reported that their plan was moderately effective.
Critical infrastructure protection requires the development of a national capability to identify and monitor the critical elements and to determine when and if the elements are under attack or are the victim of destructive natural occurrences. CIP is important because it is the link between risk management and infrastructure assurance. It provides the capability needed to eliminate potential vulnerabilities in the critical infrastructure.
CIP practitioners determine vulnerabilities and analyze alternatives in order to prepare for incidents. They focus on improving the capability to detect and warn of impending attacks on, and system failures within, the critical elements of the national infrastructure.
Organization and structure
PDD-63 mandated the formation of a national structure for critical infrastructure protection. To accomplish this one of the primary actions was to produce a National Infrastructure Assurance Plan, or NIAP, later renamed National Infrastructure Protection Plan or NIPP.The different entities of the national CIP structure work together as a partnership between the government and the public sectors. Each department and agency of the federal government is responsible for protecting its portion of the government's critical infrastructure. In addition, there are grants made available through the Department of Homeland Security for municipal and private entities to use for CIP and security purposes.
These include grants for emergency management, water security training, rail, transit and port security, metropolitan medical response, LEA
Law enforcement agency
In North American English, a law enforcement agency is a government agency responsible for the enforcement of the laws.Outside North America, such organizations are called police services. In North America, some of these services are called police while others have other names In North American...
terrorism prevention programs and the Urban Areas Security Initiative.
PDD-63 identified certain functions related to critical infrastructure protection that must be performed chiefly by the federal government. These are national defense, foreign affairs, intelligence, and law enforcement. Each lead agency for these special functions appoints a senior official to serve as a functional coordinator for the federal government. In 2008 a mobile PDA based Vulnerability Assessment Security Survey Tool (VASST) was introduced to speed physical security assessment of critical infrastructure by law enforcement to meet compliance requirements of PDD-63.
National Infrastructure Assurance Plan / National Infrastructure Protection Plan
For each of the identified major sectors of the critical infrastructure, the federal government appointed a Sector Liaison Official from a designated Lead Agency. A private sector counterpart, a Sector Coordinator, was also identified. Together, the two sector representatives, one federal government and one corporate, were responsible for developing a sector NIAP.In addition, each department and agency of the federal government was responsible for developing its own CIP plan for protecting its portion of the federal government's critical infrastructure. The federal department and agency plans were assimilated with the sector NIAPs to create one comprehensive National Infrastructure Assurance Plan. Additionally the national structure must ensure there is a national CIP program. This program includes responsibilities such as education and awareness, threat assessment and investigation, and research.
The process includes assessments of:
- Protection - Can be defined as the state of being defended, safeguarded, or shielded from injury, loss, or destruction from natural or un-natural forces.
- Vulnerability – The quality of being susceptible to attack or injury, warranted or unwarranted, by accident or by design.
- Risk – The possibility or likelihood of being attacked or injured.
- Mitigation – The ability to alleviate, reduce, or moderate a vulnerability, thus reducing or eliminating risk.
Controversy
There have been public criticisms of the mechanisms and implementation of some security initiatives and grants, with claims they are being led by the same companies who stand to benefit, and that they are encouraging an unnecessary culture of fearCulture of fear
Culture of fear is a term used by certain scholars, writers, journalists and politicians who believe that some in society incite fear in the general public to achieve political goals, for example......
. Commentators note that these initiatives started directly after the collapse of the Cold War
Cold War
The Cold War was the continuing state from roughly 1946 to 1991 of political conflict, military tension, proxy wars, and economic competition between the Communist World—primarily the Soviet Union and its satellite states and allies—and the powers of the Western world, primarily the United States...
, raising the concern that this was simply a diversion of the military-industrial complex away from a funding area which was shrinking and into a richer previously civilian arena.
Grants have been distributed across the different states even though the perceived risk is not evenly spread, leading to accusations of pork barrel
Pork barrel
Pork barrel is a derogatory term referring to appropriation of government spending for localized projects secured solely or primarily to bring money to a representative's district...
politics that directs money and jobs towards marginal voting areas.
The Urban Areas Security Initiative grant program has been particularly controversial, with the 2006 infrastructure list covering 77,000 assets, including a popcorn factory and a hot dog stand. The 2007 criteria were reduced to 2,100 and now those facilities must make a much stronger case to become eligible for grants.
While well-intentioned, some of the results have also been questioned regarding claims of poorly-designed and intrusive security theater
Security theater
Security theater is a term that describes security countermeasures intended to provide the feeling of improved security while doing little or nothing to actually improve security. The term was coined by computer security specialist and writer Bruce Schneier for his book Beyond Fear, but has gained...
that distracts attention and money from more pressing issues or creates damaging side effects.
An absence of comparative risk analysis and benefits tracking it has made it difficult to counter such allegations with authority. In order to better understand this, and ultimately direct effort more productively, a Risk Management and Analysis Office was recently created in the National Protection and Programs directorate at the Department of Homeland Security.
Department of Defense and CIP
The DoD is responsible for protecting its portion of the government's critical infrastructure. But as part of the CIP program, DoD has responsibilities that traverse both the national and department-wide critical infrastructure.PDD 63 identified the responsibilities DoD had for critical infrastructure protection. First, DoD had to identify its own critical assets and infrastructures and provide assurance through analysis, assessment, and remediation. DoD was also responsible for identifying and monitoring the national and international infrastructure requirements of industry and other government agencies, all of which needed to be included in the protection planning. DoD also addressed the assurance and protection of commercial assets and infrastructure services in DoD acquisitions. Other DoD responsibilities for CIP included assessing the potential impact on military operations that would result from the loss or compromise of infrastructure service. There were also requirements for monitoring DoD operations, detecting and responding to infrastructure incidents, and providing department indications and warnings as part of the national process. Ultimately, DoD was responsible for supporting national critical infrastructure protection.
In response to the requirements identified in PDD 63, DoD categorized its own critical assets by sector, in a manner similar to the national CIP organization. The DoD identified a slightly different list of infrastructure sectors for those areas that specifically required protection by DoD. DoD’s organizational structure for critical infrastructure protection reflects, complements, and effectively interacts with the national structure for CIP.
DoD sectors
There are ten defense critical infrastructure sectors that are protected by the DoD. These include:- Financial Services - Defense financial services support activities related to officially appropriated funds. These activities include the disbursement of cash, receipt of funds, and acceptance of deposits for credit to officially designated Treasury general accounts. This sector also provides financial services to individuals and on-base organizations, including deposits, account maintenance, and safekeeping. The Defense Finance and Accounting ServiceDefense Finance and Accounting ServiceThe Defense Finance and Accounting Service is an agency of the United States Department of Defense that provides finance and accounting services for the civil and military members of the Department. Headquartered in Indianapolis, IN, it was activated on Jan. 18, 1991...
is the lead component for the Financial Services sector.
- Transportation - The Defense Transportation System, or DTS, includes resources that support global DoD transportation needs. These include surface, sea, and lift assets; supporting infrastructure; personnel; and related systems. Transportation CommandUnited States Transportation CommandThe United States Transportation Command is one of nine unified commands of the United States Department of Defense. The mission of USTRANSCOM is to provide air, land and sea transportation for the Department of Defense, both in time of peace and time of war.USTRANSCOM, located at Scott Air Force...
, or USTRANSCOM, is the single manager for DoD transportation.
- Public Works - Public works includes four distinct physical infrastructure sectors: electric power, oil and natural gas, water and sewer; and emergency services, such as fire, medical, and hazardous material handling. This defense infrastructure sector is composed of networks and systems, principally for the distribution of the associated commodities. The Corps of EngineersUnited States Army Corps of EngineersThe United States Army Corps of Engineers is a federal agency and a major Army command made up of some 38,000 civilian and military personnel, making it the world's largest public engineering, design and construction management agency...
is responsible for coordinating the assurance activities of the public works infrastructure sector.
- Global Information Grid Command Control, or GIG/C2 - The Global Information Grid Command Control, or GIG/C2, are two combined sectors that support overall asset assurance for CIP. The GIG is the globally interconnected set of personnel, information, and communication capabilities necessary to achieve information superiority. C2 includes assets, facilities, networks, and systems that support mission accomplishment. The Defense Information Systems AgencyDefense Information Systems AgencyThe Defense Information Systems Agency is a United States Department of Defense agency that provides information technology and communications support to the President, Vice President, Secretary of Defense, the military Services, and the Combatant Commands.As part of the Base Realignment and...
, or DISA, is the lead component responsible for Global Information Grid Command Control.
- Intelligence Surveillance, and Reconnaissance, or ISR - The Defense Intelligence, Surveillance and Reconnaissance infrastructure sector is composed of facilities, networks, and systems that support ISR activities such as intelligence production and fusion centers. The Defense Intelligence AgencyDefense Intelligence AgencyThe Defense Intelligence Agency is a member of the Intelligence Community of the United States, and is the central producer and manager of military intelligence for the United States Department of Defense, employing over 16,500 U.S. military and civilian employees worldwide...
, or DIA, is responsible for coordinating the assurance activities of this infrastructure sector.
- Health Affairs - The health care infrastructure consists of facilities and sites worldwide. Some are located at DoD installations; however, DoD also manages a larger system of non-DoD care facilities within its health care network. These health care facilities are linked by information systems. The Office of the Assistant Secretary of Defense, Heath Affairs is the designated lead component for this sector.
- Personnel - The defense personnel infrastructure sector includes a large number of assets hosted on component sites, a network of facilities, and information systems linking those sites and facilities. In addition to being responsible for its own assets, the personnel infrastructure sector also coordinates commercial services that support the personnel function. These services include recruitment, record keeping, and training. The Defense Human Resources ActivityDefense Human Resources ActivityThe Defense Human Resources Activity is a United States Department of Defense Field Activity chartered to support the Under Secretary of Defense for Personnel and Readiness...
is the designated lead component for the Defense Personnel infrastructure sector.
- Space - The defense space infrastructure sector is composed of both space- and ground- based assets including launch, specialized logistics, and control systems. Facilities are located worldwide on both DoD-controlled and private sites. The Defense Space sector is led by the United States Strategic CommandUnited States Strategic CommandUnited States Strategic Command is one of nine Unified Combatant Commands of the United States Department of Defense . The Command, including components, employs more than 2,700 people, representing all four services, including DoD civilians and contractors, who oversee the command's operationally...
, or USSTRATCOM.
- Logistics - The defense logistics sector includes all activities, facilities, networks, and systems that support the provision of supplies and services to U.S. forces worldwide. Logistics includes the acquisition, storage, movement, distribution, and maintenance of material and supplies. This sector also includes the final disposition of material no longer needed by DoD. The Defense Logistics AgencyDefense Logistics AgencyThe Defense Logistics Agency is an agency in the United States Department of Defense, with more than 26,000 civilian and military personnel throughout the world...
, or DLA, is the lead component for the DoD Logistics infrastructure.
- Defense Industrial Base - The Defense Industrial Base consists of DoD product and service providers from the private sector. The services and products provided constitute critical assets for DoD. The lead component for the Defense Industrial Base is the Defense Contract Management AgencyDefense Contract Management AgencyThe Defense Contract Management Agency is the agency of the United States federal government responsible for performing contract administration services for the Department of Defense and other authorized federal agencies. Its headquarters is at Fort Lee, Va...
. For those cases when infrastructure protection requirements affect more than one defense sector, DoD has set up special function components that support the implementation of CIP.
DoD special functions
The DoD CIP special function components interface with the equivalent national functional coordinators and coordinate all activities related to their function within DoD.DoD’s special function components currently include seven areas of focus. They include the following components:
- Policy and Strategy - The Policy and Strategy Special Function Component provides the strategic planning required to prepare our Armed Forces for the 21st century. In part, it satisfies this responsibility through the development of the National Military Strategy. Within the area of policy development it is responsible for leading the Chairman's biennial review of the Unified Command Plan and developing Joint Staff positions on such key issues as the organization, roles and missions, and functions of the Armed Forces and the combatant commands.
- Intelligence Support - The CIP Intelligence Support Special Function Component provides intelligence support to DoD in protection of the Defense portion of the Federal Government Critical Infrastructure. Intelligence Support responsibilities also include supporting the Defense Warning System, Alert and Notification, and interfacing with the national intelligence community. The responsibilities of the Intelligence Support agencies include such activities as provisioning threat assessments; indications and warnings of potential attacks; advice and support to Sector CIAOs in the development of defense infrastructure sector monitoring and reporting; crisis management support; and counter-intelligence. This special function component is also tasked with the support to the DoD contingent of the NIPC related to intelligence and counter-intelligence.
- Industrial Policy - The Under Secretary of Defense for Acquisition, Technology & Logistics ensures that an adequate defense industrial base exists and remains viable to meet current, future, and emergent national security requirements."
- Defense Security - The Defense Security Service provides to the Department of Defense and other Federal agencies an array of security products and services which are designed to deter and detect espionage
- Information Assurance - The Assistant Secretary of Defense for Networks and Information Integration, or ASD NII, is the principal OSD staff assistant for the development, oversight, and integration of DoD policies and programs relating to the strategy of information superiority for the Department of Defense. Information Assurance, or IA, is the component of Information Operations that assures DoD's operational readiness by providing for the continuous availability and reliability of information systems and networks. IA protects the DII against exploitation, degradation, and denial of service, while providing the means to efficiently reconstitute and reestablish vital capabilities following an attack.
- Research and Development - The Research and Development Special Function Component is responsible for information assurance and protection. The Office of Director, Defense Research and Engineering coordinates a CIP DoD research and development agenda. As well as reconciling the DoD agenda with the national R&D agenda.
- Education and Awareness - Although education and awareness may rightly be considered everyone's responsibility, a comprehensive education and awareness strategy was deemed essential for a successful DoD CIP program. The National Defense University, or NDU, provided advice and assistance in assessing DoD education and awareness requirements. The Education and Awareness Component also developed the CIAO Education Program. This component was tasked to assist in the development of any special education or training required for CIP crisis management personnel. Education and Awareness also supports both DoD and national CIP policy and strategy formulation and executive leadership development through periodic "infrastructure games."
DoD CIP lifecycle
As mandated by PDD 63, the DoD must protect its portion of the federal government's critical infrastructure. For DoD, this is the Defense Infrastructure or DI. Protecting the Defense Infrastructure is a complex task involving ten defense sectors.It was deemed that it was nearly impossible to protect every critical asset at every location, therefore the focus was directed on protecting the critical Defense Infrastructure. The critical Defense Infrastructure is the critical assets essential to providing mission assurance.

The six phases
The six phases of the DoD CIP life cycle build on one another to create a framework for a comprehensive solution for infrastructure assurance. The life cycle phases occur before, during, and after an event that may compromise or degrade the infrastructure. A synopsis of the six phases are:- Analysis and Assessment (occurs before an event) - The Analysis and Assessment phase is the foundation and most important phase of the CIP life cycle. This phase identifies the assets absolutely critical to mission success and determines the assets’ vulnerabilities, as well as their interdependencies, configurations, and characteristics. An assessment is then made of the operational impact of infrastructure loss or degradation. In addition, Proactive Cyber DefenceProactive Cyber DefenceProactive Cyber Defence means acting in anticipation to oppose an attack against computers and networks. Proactive cyber defence will most often require additional security from internet service providers....
may anticipate an attack against computers and networks. It applies equally well to all critical infrastructure sectors, as it involves interdicting and disrupting an attack or a threat’s preparation to attack, either pre-emptively or in self-defense.
- Remediation (occurs before an event) - The Remediation phase involves precautionary measures and actions taken before an event occurs to fix the known cyber and physical vulnerabilities that could cause an outage or compromise a National Defense Infrastructure, or NDI, or critical asset. For example, remediation actions may include education and awareness, operational process or procedural changes or system configuration and component changes.
- Indications and Warnings (occurs before and/or during an event) - The Indications and Warnings phase involves daily sector monitoring to assess the mission assurance capabilities of critical infrastructure assets and to determine if there are event indications to report. Indications are preparatory actions that indicate whether an infrastructure event is likely to occur or is planned. Indications are based on input at the tactical, operational, theater, and strategic level. At the tactical level, input comes from asset owners. At the operational level, input comes from the NDI sectors. At the theater level input comes from regional assets such as allied intelligence, NATO, command intelligence, allied governments, and coalition forces. At the strategic level, input comes from intelligence, law-enforcement, and the private sector. Warning is the process of notifying asset owners of a possible threat or hazard.
- Mitigation (occurs both before and during an event) - The Mitigation phase comprises actions taken before or during an event in response to warnings or incidents. DoD Critical Asset owners, NDI sectors, DoD installations, and military operators take these actions to minimize the operational impact of a critical asset’s loss or debilitation.
- Incident Response (occurs after an event) - Incident Response comprises the plans and activities taken to eliminate the cause or source of an infrastructure event.
- Reconstitution (occurs after an event) - The last phase of the CIP life cycle, involves actions taken to rebuild or restore a critical asset capability after it has been damaged or destroyed. This phase is the most challenging and least developed process.
Effective management of the CIP life cycle ensures that protection activities can be coordinated and reconciled among all DoD sectors. In many ways, DoD CIP, is risk management at its most imperative. Achieving success means obtaining mission assurance. Missing the mark can mean mission failure as well as human and material losses. For critical infrastructure protection, risk management requires leveraging resources to address the most critical infrastructure assets that are also the most vulnerable and that have the greatest threat exposure.
The most important part of the CIP lifecye is Phase 1. Because it is crucial to target the right assets for infrastructure protection, determining these assets is the first phase in the CIP life cycle. This phase, Analysis and Assessment, is the key and foundation of the seven lifecycle activities. Without a solid foundation, the remaining CIP life cycle phases may be flawed, resulting in a CIP plan that fails to protect the critical infrastructure and, therefore, mission assurance.
Phase 1: Analysis and Assessment
Phase 1 determines what assets are important, and identifies their vulnerabilities, and dependencies so that decision makers have the information they need to make effective risk management choices.The Defense Infrastructure, or DI, is organized into ten sectors. Each sector is composed of assets, such as systems, programs, people, equipment, or facilities. Assets may be simple, such as one facility within one geographic location, or complex, involving geographically dispersed links and nodes.
The Analysis and Assessment is made up of five steps that include activities that span and encompass the ten DI sectors and their assets.
- I. The first step in the Analysis and Assessment phase is to identify critical assets. An asset’s criticality is a function of both time and situation based on the asset’s operational or business value. For the DI, value depends on several factors: First, what military operations or services rely on an asset and how those dependencies change across time Next, how sensitive the operation is to the loss or compromise of the asset, in other words what is the maximum allowable down time if the asset is compromised. Finally, what the asset’s assurance profile is, in particular whether asset restoration or a switch to a backup can occur within the allowable down time. Through domain expertise and inspection, critical assets are identified and then reported to the CIP Program.
- II. The second step of the Analysis and Assessment phase is Defense Infrastructure characterization. This step maps and associates critical asset functions and relationships within a DI sector.
- III. The third step in the Analysis and Assessment phase is the Operational Impact Analysis. This step is accomplished through the development of operational dependency matrices and the application of operations research methods. Potential operational impacts and service-level requirements are then reflected in the asset’s criticality attributes and criticality index in the CIP program.
- IV. The fourth step is the Vulnerability Assessment. This step is accomplished through multiple channels. Through the CIP program, all critical assets have a baseline vulnerability index, which is calculated from inputs associated with the class of asset and geographic region such as the probability of natural disasters, criminal or national security events, and technological failures. Asset owners, host installations, the sector CIAO, or other DoD entities may provide asset operational readiness and emergency preparedness information.
- V. The fifth and final step in the Analysis and Assessment phase is Interdependency Analysis. Interdependency analysis seeks to map functions and relationships among DI sectors. As a result of the Interdependency Analysis, the criticality attributes for previously identified assets may be updated and additional critical assets may be identified to the CIP program. Multiple groups within the DoD CIP structure perform analysis and assessment activities. Translating the analysis and assessment process into concrete data requires specific activities, tasks, and tools.
Phase 1 example in the “Real World”
On August 24 2001, the Director of the Joint Staff requested USPACOM to serve as the lead support Combatant Command for creating a CIP first-ever theater CIP Plan – known as the “CIP Appendix 16 Plan.” The following is how USPACOM approached the task.USPACOM focused the Analysis and Assessment phase by organizing its activities to answer three major questions:
- What is critical?
- Is it vulnerable?
- What can be done?
To answer the question, “What is critical?”, USPACOM outlined a three-step procedure:
- First, identify the project focus.
- Second, complete an operational analysis.
- Third, complete a Defense Infrastructure analysis.
To accomplish these steps, USPACOM adopted a methodology that focuses its CIP efforts on Tier 1 assets. Tier 1 assets are assets that could cause mission failure if they are compromised or damaged. The methodology UAPACOM adopted and modified is Mission Area Analysis, or MAA. The MAA links combatant command missions to infrastructure assets that are critical to a given Operations Plan, or OPLAN, Contingency Plan, or CONPLAN, or Crisis Action Plan. Typically, the MAA process determines the assessment site priorities. USPACOM modified the process and selected the CIP assessment sites and installations prior to conducting the MAA. The following is an illustration of the USPACOM MAA process:
- First, it identified the Mission Essential Requirements, or MERs, which are specific combatant commands or joint task force capabilities essential for execution of a warfighting plan. Then, they created an MER matrix for the specific command. For example, one MER may be to provide command, control, communications, and computers, or C4.
- Second, it identified forces required for each MER. For example, the C4 MER is linked to a specific signal battalion. Third, it linked the forces to the necessary functions and tasks supporting the force. For example, the signal battalion is linked to the Communications and Civil Engineers functions and the task of managing the theater’s C4 information systems requirements.
- Third, it links assets to the functions supporting the tasks. The result is a mission area analysis of mission-critical assets.
USPACOM uses the MAA data it gathers to scope and focus its efforts on truly mission-critical assets to answer the next question in its process, Is it vulnerable?
The first step in answering this question is to complete an installation analysis. The next step is to complete a commercial infrastructure analysis. USPACOM relied upon two different DoD organizations for CIP assessments: Balanced Survivability Assessments, or BSAs, and Mission Assurance Assessments. The BSA is a two-week mission-focused assessment at a military installation or designated site. A Mission Assurance Assessment is unique because it uses an area assessment approach to focus on both commercial and military asset vulnerabilities and dependencies. The final step to determine vulnerabilities is to integrate the two analyses and assessments. With its critical assets and their vulnerabilities identified, USPACOM is ready to perform risk management activities to decide what can be done to protect the mission-critical assets.
Booz Allen Hamilton developed this process at PACOM.
Phase 2: Remediation Phase
The first phase of the CIP life cycle, Analysis and Assessment, identified the critical assets of DoD sector infrastructures and the vulnerabilities or weaknesses of those critical assets.The second phase is the Remediation phase. In the Remediation phase, the known weaknesses and vulnerabilities are addressed. Remediation actions are deliberate, precautionary measures designed to fix known virtual and physical vulnerabilities before an event occurs. The purpose of remediation is to improve the reliability, availability, and survivability of critical assets and infrastructures. Remediation actions apply to any type of vulnerability, regardless of its cause. They apply to acts of nature, technology failures, or deliberate malicious actions.
The cost of each remediation action depends on the nature of the vulnerability it addresses. The Defense Infrastructure Sector Assurance Plan that each infrastructure sector must develop, establishes the priorities and resources for remediation. Remediation requirements are determined by multiple factors. These are analysis and assessment, input from military planners and other DoD sectors, the National Infrastructure Assurance Plan and other plans, reports, and information on national infrastructure vulnerabilities and remediation, as well as intelligence estimates and assessments of threats.
Remediation requirements are also gathered through lessons learned from Defense Infrastructure sector monitoring and reporting and infrastructure protection operations and exercises. The CIP program tracks the status of remediation activities for critical assets. Remediation activities to protect the critical Defense Infrastructure cross multiple Department components.
Phase 3: Indications and Warnings Phase
The need to monitor activities and warn of potential threats to the United States is not new. From conventional assaults to potential nuclear attacks, the military has been at the forefront of monitoring and warning of potential dangers since the founding of the country. Protecting the security and well being of the United States, including the critical Defense Infrastructure, has now entered a new era. It has been deemed essential to have a coordinated ability to identify and warn of potential or actual incidents among critical infrastructure domains. The ability to detect and warn of infrastructure events is the third phase of the critical infrastructure protection life cycle, the Indications and Warnings phase.Indications and warnings are actions or infrastructure conditions that signal an event is either”
- Likely,
- Planned or
- Underway.
Historically, DoD event indications have focused and relied on intelligence information about foreign developments. These event indications have been expanded to include all potential infrastructure disruption or degradation, regardless of its cause. DoD CIP indications are based on four levels of input:
- Tactical level input from DoD asset owners or installations
- Operational-level input from sector Chief Information Assurance Officers, or CIAOs
- Theater-level input from command and service intelligence and counter-intelligence activities.
- Strategic-level intelligence from the intelligence community, law enforcement, and the private sector.
This fusion of traditional intelligence information with sector-specific information has been determined to be essential for meaningful CIP indications.
If an indication is detected, a warning notifying the appropriate asset owners of a possible or occurring event or hazard can be issued. The sector’s assurance plan determines what conditions and actions are monitored and reported for each Defense Infrastructure Sector.
Each sector must develop a written Defense Sector Assurance Plan that includes a compendium of sector incidents for monitoring and reporting. The sector incident compendium is made up of three types of incidents:
- Nationally-defined reportable incidents
- DoD defined reportable incidents, and
- Sector-defined reportable incidents.
DoD critical asset owners, installations, and sector CIAOs determine the DoD and sector-defined incidents. Each of the reportable incidents or classes of incidents must include the following components:
- Who should monitor the incident
- How soon the incident must be reported
- Which information elements the incident should contain
- How the incident reporting should be routed
- What follow-up actions are required
The National Infrastructure Protection Center, or NIPC, is the primary national warning center for significant infrastructure attacks. Critical asset owners, DoD installations, and Sector CIAOs monitor the infrastructure daily. Indications of an infrastructure incident are reported to the National Military Command Center, or NMCC. If indications are on a computer network, they are also reported to the Joint Task Force Computer Network Operations, or JTF-CNO. The NMCC and JTF-CNO assess the indications and pass them to the NIPC and appropriate DoD organizations. When the NIPC determines that an infrastructure event is likely to occur, is planned, or is under way, it issues a national warning. For DoD, the NIPC passes its warnings and alerts to the NMCC and JTF-CNO. These warnings and alerts are then passed to the DoD components. The warning may include guidance regarding additional protection measures DoD should take.
Phase 4: Mitigation Phase
Phase 1 of the CIP life cycle provided a layer of protection by identifying and assessing critical assets and their vulnerabilities. Phase 2 provided another layer of protection by remediating or improving the identified deficiencies and weaknesses of an asset. Even with these protections and precautions, an infrastructure incident was still possible. When it does the Indications and Warnings phase goes into effect.The Mitigation phase (Phase 4), is made up of preplanned coordinated actions in response to infrastructure warnings or incidents. Mitigation actions are taken before or during an infrastructure event. These actions are designed to minimize the operational impact of the loss of a critical asset, facilitate incident response, and quickly restore the infrastructure service.
A primary purpose of the Mitigation phase is to minimize the operational impact on other critical Defense Infrastructures and assets when a critical asset is lost or damaged. As am example, if there is a U.S. installation, Site A, located in a host nation. Site A is a tier 1 asset, meaning that if it fails, the Combatant Commands mission fails. Site A has mutual Global Information Grid Command Control, or GIG/C2, information interdependencies with Sites B and C. In addition, other Defense Infrastructure sectors rely on Site A for mission capabilities. In this scenario, what could be the impact if the supply line to the commercial power plant that provides the installation’s primary power is accidentally severed. Because of all the interdependencies, losing this asset is more than the loss of just one site. It means the loss of other sector capabilities.
A possible mitigation action might be for Site A to go on backup power.
An alternate action could be to pass complete control of Site A’s functionality to another site, where redundancy has been previously arranged. These actions would limit the impact of this incident on the other sites and related sectors. In addition to lessening the operational impact of a critical infrastructure event, the Mitigation phase of the CIP life cycle supports and complements two other life cycle phases. Mitigation actions aid in the emergency, investigation, and management activities of Phase 5, Incident Response. They also facilitate the reconstitution activities of Phase 6.
During the Mitigation phase, DoD critical asset owners, DoD installations, and Sector Chief Infrastructure Assurance Officers, or CIAOs, work with the National Military Command Center, or NMCC, and the Joint Task Force-Computer Network Operations, or JTF-CNO, to develop, train for, and exercise mitigation responses for various scenarios. When there is a warning, emergency, or infrastructure incident, the critical asset owners, installations, and Sector CIAOs initiate mitigation actions to sustain service to the DoD. They also provide mitigation status information to the NMCC and JTF-CNO. The NMCC monitors for consequences from an event within one Defense Infrastructure sector that are significant enough to affect other sectors. For events that cross two or more sectors, the NMCC advises on the prioritization and coordination of mitigation actions. When event threats or consequences continue to escalate, the NMCC directs mitigation actions by sector to ensure a coordinated response across the DoD. The NMCC and the JTF-CNO keep the National Infrastructure Protection Center, or NIPC, apprised of any significant mitigation activities.
Phase 5: Incident Response
When an event affects the Defense Infrastructure, the Incident Response phase begins. Incident Response is the fifth phase of the CIP life cycle. The purpose of the Incident Response phase is to eliminate the cause or source of an infrastructure event. For example, during the 9/11 attacks on the World Trade Center and Pentagon, all non-military airplanes were grounded over the United States to prevent further incidents. Response activities included emergency measures, not from the asset owners or operators, but from dedicated third parties such as law enforcement, medical rescue, fire rescue, hazardous material or explosives handling, and investigative agencies. Response to Defense Infrastructure incidents can take one of two paths depending on whether or not the event affects a DoD computer network.When incidents compromise a DoD computer network, the Joint Task Force-Computer Network Operations, or JTF-CNO, directs the response activities. These activities are designed to stop the computer network attack, contain and mitigate damage to a DoD information network and then restore minimum required functionality. JTF-CNO also requests and coordinates any support or assistance from other Federal agencies and civilian organizations during incidents affecting a DoD network. When incidents impact any other DoD owned assets, installation commanders and critical asset owners follow traditional channels and procedures to coordinate responses. This includes notifying affected Sector Chief Infrastructure Assurance Officers, or CIAOs, in the initial notice and status reporting. Although third parties play a major role in the response to Defense Infrastructure events, DoD CIP personnel also have responsibilities to fulfill.
Phase 6: Reconstitution
After the source or cause of an infrastructure event is eliminated or contained, the infrastructure and its capabilities must be restored. Reconstitution is the last phase of the critical infrastructure protection. Reconstitution is probably the most challenging and least developed process of the life cycle. DoD critical asset owners have the major responsibility for reconstitution.See also
- Richard A. ClarkeRichard A. ClarkeRichard Alan Clarke was a U.S. government employee for 30 years, 1973–2003. He worked for the State Department during the presidency of Ronald Reagan. In 1992, President George H.W. Bush appointed him to chair the Counter-terrorism Security Group and to a seat on the United States National...
Former Special Advisor to the President for Counterterrorism, Cybersecurity, and Critical Infrastructure Protection - Proactive Cyber DefenceProactive Cyber DefenceProactive Cyber Defence means acting in anticipation to oppose an attack against computers and networks. Proactive cyber defence will most often require additional security from internet service providers....
Proactive Cyber Defence in Depth to protect critical information infrastructures - Presidential Decision Directive 62PDD-62Presidential Decision Directive 62 , titled Combating Terrorism, was a Presidential Decision Directive , signed on May 22, 1998 by President Bill Clinton. It identified the fight against terrorism a top national security priority....
- ITU Global Cybersecurity Agenda
- North American Electric Reliability Corporation (NERC)
- Critical Foreign Dependencies InitiativeCritical Foreign Dependencies InitiativeThe Critical Foreign Dependencies Initiative is a strategy and list, maintained by the United States Department of Homeland Security, of foreign infrastructure which "if attacked or destroyed would critically impact the U.S." A copy of the 2008 list was redacted and leaked by WikiLeaks on 5...
External links
- Anderson, K. "Intelligence-Based Threat Assessments for Information Networks and Infrastructures: A White Paper".
- Strategy to Secure CyberspaceUnited States Department of Homeland SecurityThe United States Department of Homeland Security is a cabinet department of the United States federal government, created in response to the September 11 attacks, and with the primary responsibilities of protecting the territory of the United States and protectorates from and responding to...
- Critical Infrastructure Protection Program, George Mason University
- "Critical Infrastructure: Homeland Security and Emergency Preparedness"
- Infracritical
- Centre for the Protection of National Infrastructure (United Kingdom)
- "Water Infrastructure Security Enhancements" draft national standards
- Terrorism & Public Utility Infrastructure Protection
- DoD IA Policy Chart - Build & Operate a Trusted GIG

