
Encryption software
Encyclopedia
Encryption software is software whose main task is encryption
and decryption of data, usually in the form of files on (or sectors of) hard drives and removable media
, email
messages, or in the form of packets sent over computer network
s.
that is designed to encrypt computer data in such a way that it cannot be recovered without access to the key. Software encryption is a fundamental part of all aspects of modern computer communication and file protection and may include features like file shredding.
The purpose of encryption is to prevent third parties from recovering the original information. This is particularly important for sensitive data like credit card numbers.
) competition. The winner, Rijndael, got 86 votes while Serpent
got 59 votes, Twofish
31 votes, RC6
23 votes and MARS 13 votes. NIST chose Rijndael as its standard. Serpent and Rijndael are in fact somewhat similar; the main difference is that Rijndael is faster (having fewer rounds) but Serpent is more secure.
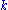 , of each byte of plain text
, of each byte of plain text 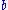 , to produce a cipher value
, to produce a cipher value  .
.

Ciphers can be categorized into two general types: public key
ciphers and symmetric key ciphers.
Public key systems are based upon algorithms that are at least strongly believed to be "one-way" operations. That is, encryption with one member of a key pair is only easily reversed (decrypted) using the other member of the pair. Further, one member of the pair (the public key) cannot be easily used to determine the other (the private key). Provided the problems posed by the system to cryptanalyst are effectively unsolvable, the system is effectively secure. Such systems are used for key exchanges (for subsequent use of symmetric key ciphers), digital signatures and the like.
Symmetric key ciphers (also referred to as secret key ciphers) are called such because the same key is used for both encryption and decryption. Thus, in order for messages encrypted with a symmetric key cipher to remain secure, the key used must remain secret. Symmetric key ciphers can be further subdivided into stream ciphers
and block ciphers
.
Stream ciphers typically encrypt plaintext a bit or byte at a time, and are most commonly used to encipher real-time communications, such as audio and video information. The key is used to establish the initial state of a key-stream generator, and the output of that generator is used to encrypt the plaintext.
Block cipher algorithms encrypt blocks of bytes of plaintext a block at a time. The Advanced Encryption Standard algorithm (AES - derived from the Rijndael cipher algorithm) is a block cipher that processes 16 bytes at a time, while its predecessor, the Data Encryption Standard algorithm (DES) encrypted blocks of eight bytes.
A common mistake made by amateur cryptographers is the assumption that because the method is secret, the cipher is secure. This is not usually true. Many "home grown" encryption algorithms reveal the key quite easily when fed a string of identical bytes (e.g., null
s).
The purpose of disseminating an encryption method is to allow the community to evaluate it. If it is indeed secure, then its power lies in the fact that its method has been subjected to scrutiny and found to be sound, not that it is secret.
Network traffic encryption tools
Each of these categories define the range and location of the data to be encrypted, but the process is the same for each.
Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
and decryption of data, usually in the form of files on (or sectors of) hard drives and removable media
Removable media
In computer storage, removable media refers to storage media which is designed to be removed from the computer without powering the computer off.Some types of removable media are designed to be read by removable readers and drives...
Email
Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the...
messages, or in the form of packets sent over computer network
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
s.
Security
Encryption software executes an algorithmAlgorithm
In mathematics and computer science, an algorithm is an effective method expressed as a finite list of well-defined instructions for calculating a function. Algorithms are used for calculation, data processing, and automated reasoning...
that is designed to encrypt computer data in such a way that it cannot be recovered without access to the key. Software encryption is a fundamental part of all aspects of modern computer communication and file protection and may include features like file shredding.
The purpose of encryption is to prevent third parties from recovering the original information. This is particularly important for sensitive data like credit card numbers.
Encryption choices
Many encryption algorithms exist. The more popular options were submitted to the National Institute of Standards and Technology or NIST for the Advanced Encryption Standard (AESAdvanced Encryption Standard
Advanced Encryption Standard is a specification for the encryption of electronic data. It has been adopted by the U.S. government and is now used worldwide. It supersedes DES...
) competition. The winner, Rijndael, got 86 votes while Serpent
Serpent (cipher)
Serpent is a symmetric key block cipher which was a finalist in the Advanced Encryption Standard contest, where it came second to Rijndael. Serpent was designed by Ross Anderson, Eli Biham, and Lars Knudsen....
got 59 votes, Twofish
Twofish
In cryptography, Twofish is a symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists of the Advanced Encryption Standard contest, but was not selected for standardisation...
31 votes, RC6
RC6
In cryptography, RC6 is a symmetric key block cipher derived from RC5. It was designed by Ron Rivest, Matt Robshaw, Ray Sidney, and Yiqun Lisa Yin to meet the requirements of the Advanced Encryption Standard competition. The algorithm was one of the five finalists, and was also submitted to the...
23 votes and MARS 13 votes. NIST chose Rijndael as its standard. Serpent and Rijndael are in fact somewhat similar; the main difference is that Rijndael is faster (having fewer rounds) but Serpent is more secure.
Choosing encryption
There are several factors that affect the choice of an encryption algorithm including speed and security. The simplest method would be an XOR operation, with a constant value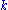 , of each byte of plain text
, of each byte of plain text 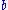 , to produce a cipher value
, to produce a cipher value  .
.
Ciphers can be categorized into two general types: public key
Public-key cryptography
Public-key cryptography refers to a cryptographic system requiring two separate keys, one to lock or encrypt the plaintext, and one to unlock or decrypt the cyphertext. Neither key will do both functions. One of these keys is published or public and the other is kept private...
ciphers and symmetric key ciphers.
Public key systems are based upon algorithms that are at least strongly believed to be "one-way" operations. That is, encryption with one member of a key pair is only easily reversed (decrypted) using the other member of the pair. Further, one member of the pair (the public key) cannot be easily used to determine the other (the private key). Provided the problems posed by the system to cryptanalyst are effectively unsolvable, the system is effectively secure. Such systems are used for key exchanges (for subsequent use of symmetric key ciphers), digital signatures and the like.
Symmetric key ciphers (also referred to as secret key ciphers) are called such because the same key is used for both encryption and decryption. Thus, in order for messages encrypted with a symmetric key cipher to remain secure, the key used must remain secret. Symmetric key ciphers can be further subdivided into stream ciphers
Stream cipher
In cryptography, a stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream . In a stream cipher the plaintext digits are encrypted one at a time, and the transformation of successive digits varies during the encryption...
and block ciphers
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
.
Stream ciphers typically encrypt plaintext a bit or byte at a time, and are most commonly used to encipher real-time communications, such as audio and video information. The key is used to establish the initial state of a key-stream generator, and the output of that generator is used to encrypt the plaintext.
Block cipher algorithms encrypt blocks of bytes of plaintext a block at a time. The Advanced Encryption Standard algorithm (AES - derived from the Rijndael cipher algorithm) is a block cipher that processes 16 bytes at a time, while its predecessor, the Data Encryption Standard algorithm (DES) encrypted blocks of eight bytes.
A common mistake made by amateur cryptographers is the assumption that because the method is secret, the cipher is secure. This is not usually true. Many "home grown" encryption algorithms reveal the key quite easily when fed a string of identical bytes (e.g., null
Null
-In computing:* Null , a special marker and keyword in SQL* Null character, the zero-valued ASCII character, also designated by NUL, often used as a terminator, separator or filler* Null device, a special computer file that discards all data written to it...
s).
The purpose of disseminating an encryption method is to allow the community to evaluate it. If it is indeed secure, then its power lies in the fact that its method has been subjected to scrutiny and found to be sound, not that it is secret.
Applications
Encryption can be applied to data in many ways. Common categories are:- Disk encryption softwareDisk encryption softwareTo protect confidentiality of the data stored on a computer disk a computer security technique called disk encryption is used. This article discusses software that is used to implement the technique...
(also known as OTFEOTFEOn-the-fly encryption , also known as Real-time Encryption, is a method used by some encryption programs, for example, disk encryption software...
software) - File/folder encryption
- Database encryption
- Communication encryption software
Network traffic encryption tools
Each of these categories define the range and location of the data to be encrypted, but the process is the same for each.
See also
- Cold boot attackCold boot attackIn cryptography, a cold boot attack is a type of side channel attack in which an attacker with physical access to a computer is able to retrieve encryption keys from a running operating system after using a cold reboot to restart the machine from a completely "off" state...
- Disk encryptionDisk encryptionDisk encryption is a special case of data at rest protection when the storage media is a sector-addressable device . This article presents cryptographic aspects of the problem...
- Password managerPassword managerA password manager is software that helps a user organize passwords and PIN codes. The software typically has a local database or a file that holds the encrypted password data for secure logon onto computers, networks, web sites and application data files. Many password managers also work as a form...
- Single sign-onSingle sign-onSingle sign-on is a property of access control of multiple related, but independent software systems. With this property a user logs in once and gains access to all systems without being prompted to log in again at each of them...

