Files-11
Encyclopedia
Files-11, also known as on-disk structure, is the file system
used by Hewlett-Packard
's OpenVMS
operating system
, and also (in a simpler form) by the older RSX-11
. It is a hierarchical file system, with support for access control list
s, record
-oriented I/O
, remote network
access, and file versioning.
Files-11 is similar to, but significantly more advanced than, the filesystems used in previous Digital Equipment Corporation
operating systems such as TOPS-20
and RSTS/E
. It is also a clear predecessor of NTFS
. Many of the concepts used in Files-11 appear in NTFS.
While this was suitable for PDP-11
systems, which possessed limited permanent storage capacity, VAX
systems with much larger hard drives required a more flexible method of file storage: hierarchical directory layout in particular, the most notable improvement in ODS-2.
ODS-1 is the flat filesystem used by the RSX-11 OS, supported by older VMS
systems for RSX compatibility, but never used to support VMS itself; it has been largely superseded by ODS-2 and ODS-5.
ODS-2 is the standard VMS filesystem, and remains the most common filesystem for system disks (the disk on which the operating system is installed).
Although seldom referred to by their ODS level designations, ODS-3 and ODS-4 are the Files-11 support for the CD-ROM ISO 9660
and High Sierra Format filesystems, respectively.
ODS-5 is an extended version of ODS-2 available on Alpha
and IA-64 platforms which adds support for case-preserving filenames with non-ASCII
characters and improvements to the hierarchical directory support. It was originally intended for file serving to Microsoft Windows
or other non-VMS systems as part of the "NT affinity" project, but is also used on user disks and Internet
servers.
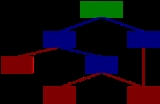
 All files and directories in a Files-11 filesystem are contained inside one or more parent directories, and eventually under the root directory, the master file directory (see below). The filesystem is therefore organised in a tree-like structure.
All files and directories in a Files-11 filesystem are contained inside one or more parent directories, and eventually under the root directory, the master file directory (see below). The filesystem is therefore organised in a tree-like structure.
In this example (see right), File 2 has a directory entry under both Dir 2 and Dir 3; it is "in" both directories simultaneously. Even if removed from one, it would still exist in the other directory until removed from there also. This is similar to the concept of hard links in UNIX
, although care must be taken that the file is not actually deleted on disks that are not set up for hard links (only available on ODS-5 disks, and then only if the disk has hard links enabled).
 In an OpenVMS cluster configuration, non-private disks are shared between all nodes in the cluster (see figure 1). In this configuration, the two system disks are accessible to both nodes via the network, but the private disk is not shared: it is mounted for use only by a particular user or process on that machine. Access to files across a cluster is managed by the OpenVMS Distributed Lock Manager, an integral part of the filesystem.
In an OpenVMS cluster configuration, non-private disks are shared between all nodes in the cluster (see figure 1). In this configuration, the two system disks are accessible to both nodes via the network, but the private disk is not shared: it is mounted for use only by a particular user or process on that machine. Access to files across a cluster is managed by the OpenVMS Distributed Lock Manager, an integral part of the filesystem.
Multiple disks can be combined to form a single large logical disk, or volume set. Disks can also be automatically replicated into shadow sets for data security or faster read performance.
A disk is identified by either its physical name or (more often) by a user-defined logical name. For example, the boot device (system disk) may have the physical name $3$DKA100, but it is generally referred to by the logical name SYS$SYSDEVICE.
Filesystems on each disk (with the exception of ODS-1) are hierarchical. A fully specified filename
consists of a nodename, a username and password, a device name, directory, filename, file type, and a version number, in the format:
NODE"accountname password"::device:[directory.subdirectory]filename.type;ver
For example, [DIR1.DIR2.DIR3]FILE.EXT refers to the latest version of FILE.EXT, on the current default disk, in directory [DIR1.DIR2.DIR3].
DIR1 is a subdirectory of the master file directory (MFD), or root directory, and DIR2 is a subdirectory of DIR1. A disk's MFD is identified by [000000].
Most parts of the filename can be omitted, in which case they are taken from the current default file specification. The default file specification replaces the concept of "current directory" in other operating systems by providing a set of defaults for node, device name and directory. All processes have a default file specification which includes disk name and directory, and most VMS filesystem routine
s accept a default file specification which can also include the file type; the TYPE command, for example, defaults to ".LIS" as the file type, so the command TYPE F, with no extension, attempts to open the file F.LIS.
Every file has a version number, which defaults to 1 if no other versions of the same filename are present (otherwise one higher than the greatest version). Every time a file is saved, rather than overwriting the existing version, a new file with the same name but an incremented version number is created. Old versions can be deleted explicitly, with the DELETE or the PURGE command, or optionally, older versions of a file can be deleted automatically when the file's version limit is reached (set by SET FILE/VERSION_LIMIT). Old versions are thus not overwritten, but are kept on disk and may be retrieved at any time. The architectural limit on version numbers is 32767. The versioning behavior is easily overridden if it is unwanted. In particular, files which are directly updated, such as databases, do not create new versions unless explicitly programmed.
ODS-2 is limited to eight levels of subdirectories, and only uppercase, alphanumeric names (plus the underscore, dash, and dollar sign) up to 39.39 characters (39 for the filename and another 39 for the extension). ODS-5 expands the character set to lowercase letters and most other printable ASCII characters, as well as ISO
Latin-1 and Unicode
characters, increases the maximum filename length and allows unlimited levels of subdirectories. When constructing a pathname for an ODS-5 file which uses characters not allowed under ODS-2, a special "^" syntax is used to preserve backwards compatibility; the file "file.tar.gz;1" on an ODS-5 disk, for example, would be referred to as "file^.tar.gz"—the file's name is "file.tar", and the extension is ".gz".
-based access control. UIC access control is based on the owner of the file and the UIC, or user, accessing the file. Access is determined by four groups of permissions:
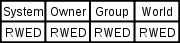
And four permission bits:
The "system" access applies to any user whose UIC group code is less than or equal to the SYSGEN parameter MAXSYSGROUP (typically 8, or 10 octal
) (for example the SYSTEM user); "owner" and "group" apply to the owner of the file and that user's user group, and "world" applies to any other user. There is also a fifth permission bit, "Control", which is used to determine access to change file metadata such as protection. This group cannot be set explicitly; it is always set for System and Owner, and never for Group or World.
UIC-based access control is also affected by four system privileges, which allow users holding them to override access controls:
ACLs allow additional privileges to be assigned on a user– or group–specific basis; for example, a web server's UIC could be granted read access to all files in a particular directory. ACLs can be marked as inherited, where a directory file's ACL applies to all files underneath it. ACLs are modified using the EDIT/ACL command, and take the form of identifier/access pairs. For example, the ACL entry
(IDENTIFIER=HTTP$SERVER,ACCESS=READ+EXECUTE)
would allow the user HTTP$SERVER to read and execute the file.
$ DEFINE/TRANS=CONCEAL HOME DISK$USERS:[username.]
would allow HOME:[DIR]FILE to be used. More common are simple logicals which point to specific directories associated with some application software which may be located in on any disk or any directory. Hence logical ABC_EXE may point to a directory of executable programs for application ABC and ABC_TEMP may point to a directory of temporary files for that same application and this directory may be on the same disk and in the same directory tree as ABC_EXE or could be somewhere on another disk (and in a different directory tree).
Logical names do not have a close equivalent in POSIX operating systems. They resemble Unix environment variable
s, except they are expanded by the filesystem, instead of the command shell or application program. They must be defined before use, so it is common for many logical names to be defined in the system startup command file, as well as user login command files.
The closest non-DEC operating system to support the concept of logical names is AmigaOS
, through the ASSIGN command. AmigaOS's disk operating system, AmigaDOS
, which is a port of TRIPOS
, bears some resemblance to DEC operating systems. For example, physical device names follow a pattern like DF0: for the first floppy disk, CDROM2: for the 3rd CD-ROM drive, etc. However, since the system can boot from any attached drive, the operating system creates the SYS: assignment to automatically reference the boot device used. Other assignments, LIBS:, PREFS:, C:, S:, et al. are also made, themselves referenced off SYS:. Users are, of course, allowed to create and destroy their own assignments too.
In VMS, logical names may reference other logical names (up to a predefined nesting limit of 10), and may contain lists of names to search for an existing filename. Some frequently referenced logical names are:
is the structured I/O
layer of the VMS operating system. RMS provides comprehensive program support for managing structured file
s, such as record-based and indexed database
files. The VMS filesystem, in conjunction with RMS, extends files access past simple byte
-streams and allows OS-level support for a variety of rich files types. Each file in the VMS filesystem may be thought of as a database
, containing a series of records
, each of which has one of more individual fields
. A text file, for example, is a list of records (lines) separated by a newline character. RMS is an example of a record-oriented filesystem
.
There are four record formats defined by RMS:
There are four record access methods, or methods to retrieve extant records from files:
Every file on a Files-11 disk (or volume set) has a unique file identification (FID), composed of three numbers: the file number (NUM), the file sequence number (SEQ), and the relative volume number (RVN). The NUM indicates where in the INDEXF.SYS file (see below) the metadata for the file is located; the SEQ is a generation number which incremented when the file is deleted and another file is created reusing the same INDEXF.SYS entry (so any dangling references to the old file do not accidentally point to the new one); and the RVN indicates the volume number on which the file is stored when using a volume set.
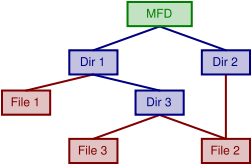
. At the root of the directory structure is the master file directory (MFD), the root directory which contains (directly or indirectly) every file on the volume.
This diagram shows an example directory containing 3 files, and the way each filename is mapped to the INDEXF.SYS entry (each INDEXF entry contains more information; only the first few items are shown here).
File system
A file system is a means to organize data expected to be retained after a program terminates by providing procedures to store, retrieve and update data, as well as manage the available space on the device which contain it. A file system organizes data in an efficient manner and is tuned to the...
used by Hewlett-Packard
Hewlett-Packard
Hewlett-Packard Company or HP is an American multinational information technology corporation headquartered in Palo Alto, California, USA that provides products, technologies, softwares, solutions and services to consumers, small- and medium-sized businesses and large enterprises, including...
's OpenVMS
OpenVMS
OpenVMS , previously known as VAX-11/VMS, VAX/VMS or VMS, is a computer server operating system that runs on VAX, Alpha and Itanium-based families of computers. Contrary to what its name suggests, OpenVMS is not open source software; however, the source listings are available for purchase...
operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
, and also (in a simpler form) by the older RSX-11
RSX-11
RSX-11 is a family of real-time operating systems mainly for PDP-11 computers created by Digital Equipment Corporation , common in the late 1970s and early 1980s. RSX-11D first appeared on the PDP-11/40 in 1972...
. It is a hierarchical file system, with support for access control list
Access control list
An access control list , with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject...
s, record
Record (computer science)
In computer science, a record is an instance of a product of primitive data types called a tuple. In C it is the compound data in a struct. Records are among the simplest data structures. A record is a value that contains other values, typically in fixed number and sequence and typically indexed...
-oriented I/O
Input/output
In computing, input/output, or I/O, refers to the communication between an information processing system , and the outside world, possibly a human, or another information processing system. Inputs are the signals or data received by the system, and outputs are the signals or data sent from it...
, remote network
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
access, and file versioning.
Files-11 is similar to, but significantly more advanced than, the filesystems used in previous Digital Equipment Corporation
Digital Equipment Corporation
Digital Equipment Corporation was a major American company in the computer industry and a leading vendor of computer systems, software and peripherals from the 1960s to the 1990s...
operating systems such as TOPS-20
TOPS-20
The TOPS-20 operating system by Digital Equipment Corporation was the second proprietary OS for the PDP-10 mainframe computer. TOPS-20 began in 1969 as the TENEX operating system of Bolt, Beranek and Newman...
and RSTS/E
RSTS/E
RSTS is a multi-user time-sharing operating system, developed by Digital Equipment Corporation , for the PDP-11 series of 16-bit minicomputers. The first version of RSTS was implemented in 1970 by DEC software engineers that developed the TSS-8 time-sharing operating system for the PDP-8...
. It is also a clear predecessor of NTFS
NTFS
NTFS is the standard file system of Windows NT, including its later versions Windows 2000, Windows XP, Windows Server 2003, Windows Server 2008, Windows Vista, and Windows 7....
. Many of the concepts used in Files-11 appear in NTFS.
History
The native OpenVMS file system is descended from older DEC operating systems, and is similar in many ways. A major difference is the layout of directories. These file systems all provided some form of rudimentary non-hierarchical directory structure, typically based on assigning one directory per user account. Under RSTS/E, each user account was represented by two numbers, a [project,programmer] pair, and had one associated directory. Special system files, such as program executables and the OS itself, were stored in the directory of a reserved system account.While this was suitable for PDP-11
PDP-11
The PDP-11 was a series of 16-bit minicomputers sold by Digital Equipment Corporation from 1970 into the 1990s, one of a succession of products in the PDP series. The PDP-11 replaced the PDP-8 in many real-time applications, although both product lines lived in parallel for more than 10 years...
systems, which possessed limited permanent storage capacity, VAX
VAX
VAX was an instruction set architecture developed by Digital Equipment Corporation in the mid-1970s. A 32-bit complex instruction set computer ISA, it was designed to extend or replace DEC's various Programmed Data Processor ISAs...
systems with much larger hard drives required a more flexible method of file storage: hierarchical directory layout in particular, the most notable improvement in ODS-2.
Overview
"Files-11" is the general term for five separate filesystems, known as on-disk structure (ODS) levels 1 through 5.ODS-1 is the flat filesystem used by the RSX-11 OS, supported by older VMS
OpenVMS
OpenVMS , previously known as VAX-11/VMS, VAX/VMS or VMS, is a computer server operating system that runs on VAX, Alpha and Itanium-based families of computers. Contrary to what its name suggests, OpenVMS is not open source software; however, the source listings are available for purchase...
systems for RSX compatibility, but never used to support VMS itself; it has been largely superseded by ODS-2 and ODS-5.
ODS-2 is the standard VMS filesystem, and remains the most common filesystem for system disks (the disk on which the operating system is installed).
Although seldom referred to by their ODS level designations, ODS-3 and ODS-4 are the Files-11 support for the CD-ROM ISO 9660
ISO 9660
ISO 9660, also referred to as CDFS by some hardware and software providers, is a file system standard published by the International Organization for Standardization for optical disc media....
and High Sierra Format filesystems, respectively.
ODS-5 is an extended version of ODS-2 available on Alpha
DEC Alpha
Alpha, originally known as Alpha AXP, is a 64-bit reduced instruction set computer instruction set architecture developed by Digital Equipment Corporation , designed to replace the 32-bit VAX complex instruction set computer ISA and its implementations. Alpha was implemented in microprocessors...
and IA-64 platforms which adds support for case-preserving filenames with non-ASCII
ASCII
The American Standard Code for Information Interchange is a character-encoding scheme based on the ordering of the English alphabet. ASCII codes represent text in computers, communications equipment, and other devices that use text...
characters and improvements to the hierarchical directory support. It was originally intended for file serving to Microsoft Windows
Microsoft Windows
Microsoft Windows is a series of operating systems produced by Microsoft.Microsoft introduced an operating environment named Windows on November 20, 1985 as an add-on to MS-DOS in response to the growing interest in graphical user interfaces . Microsoft Windows came to dominate the world's personal...
or other non-VMS systems as part of the "NT affinity" project, but is also used on user disks and Internet
Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
servers.
Directory layout

In this example (see right), File 2 has a directory entry under both Dir 2 and Dir 3; it is "in" both directories simultaneously. Even if removed from one, it would still exist in the other directory until removed from there also. This is similar to the concept of hard links in UNIX
Unix
Unix is a multitasking, multi-user computer operating system originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Brian Kernighan, Douglas McIlroy, and Joe Ossanna...
, although care must be taken that the file is not actually deleted on disks that are not set up for hard links (only available on ODS-5 disks, and then only if the disk has hard links enabled).
Disk organization and naming
An operational VMS system has access to one or more online disks, each of which contains a complete, independent filesystem. These are either local storage or, in the case of a cluster, storage shared with remote systems.
Multiple disks can be combined to form a single large logical disk, or volume set. Disks can also be automatically replicated into shadow sets for data security or faster read performance.
A disk is identified by either its physical name or (more often) by a user-defined logical name. For example, the boot device (system disk) may have the physical name $3$DKA100, but it is generally referred to by the logical name SYS$SYSDEVICE.
Filesystems on each disk (with the exception of ODS-1) are hierarchical. A fully specified filename
Filename
The filename is metadata about a file; a string used to uniquely identify a file stored on the file system. Different file systems impose different restrictions on length and allowed characters on filenames.A filename includes one or more of these components:...
consists of a nodename, a username and password, a device name, directory, filename, file type, and a version number, in the format:
NODE"accountname password"::device:[directory.subdirectory]filename.type;ver
For example, [DIR1.DIR2.DIR3]FILE.EXT refers to the latest version of FILE.EXT, on the current default disk, in directory [DIR1.DIR2.DIR3].
DIR1 is a subdirectory of the master file directory (MFD), or root directory, and DIR2 is a subdirectory of DIR1. A disk's MFD is identified by [000000].
Most parts of the filename can be omitted, in which case they are taken from the current default file specification. The default file specification replaces the concept of "current directory" in other operating systems by providing a set of defaults for node, device name and directory. All processes have a default file specification which includes disk name and directory, and most VMS filesystem routine
Routine
Routine may refer to:*Subroutine in computer science*Choreographed routine, orchestrated dance involving several performers*Comedy routine, comedic act or part of an act*Visual routine, visual cognitive means of extracting information from a scene...
s accept a default file specification which can also include the file type; the TYPE command, for example, defaults to ".LIS" as the file type, so the command TYPE F, with no extension, attempts to open the file F.LIS.
Every file has a version number, which defaults to 1 if no other versions of the same filename are present (otherwise one higher than the greatest version). Every time a file is saved, rather than overwriting the existing version, a new file with the same name but an incremented version number is created. Old versions can be deleted explicitly, with the DELETE or the PURGE command, or optionally, older versions of a file can be deleted automatically when the file's version limit is reached (set by SET FILE/VERSION_LIMIT). Old versions are thus not overwritten, but are kept on disk and may be retrieved at any time. The architectural limit on version numbers is 32767. The versioning behavior is easily overridden if it is unwanted. In particular, files which are directly updated, such as databases, do not create new versions unless explicitly programmed.
ODS-2 is limited to eight levels of subdirectories, and only uppercase, alphanumeric names (plus the underscore, dash, and dollar sign) up to 39.39 characters (39 for the filename and another 39 for the extension). ODS-5 expands the character set to lowercase letters and most other printable ASCII characters, as well as ISO
International Organization for Standardization
The International Organization for Standardization , widely known as ISO, is an international standard-setting body composed of representatives from various national standards organizations. Founded on February 23, 1947, the organization promulgates worldwide proprietary, industrial and commercial...
Latin-1 and Unicode
Unicode
Unicode is a computing industry standard for the consistent encoding, representation and handling of text expressed in most of the world's writing systems...
characters, increases the maximum filename length and allows unlimited levels of subdirectories. When constructing a pathname for an ODS-5 file which uses characters not allowed under ODS-2, a special "^" syntax is used to preserve backwards compatibility; the file "file.tar.gz;1" on an ODS-5 disk, for example, would be referred to as "file^.tar.gz"—the file's name is "file.tar", and the extension is ".gz".
File security: protection and ACLs
VMS file security is defined by two mechanisms, UIC-based access control and ACLAccess control list
An access control list , with respect to a computer file system, is a list of permissions attached to an object. An ACL specifies which users or system processes are granted access to objects, as well as what operations are allowed on given objects. Each entry in a typical ACL specifies a subject...
-based access control. UIC access control is based on the owner of the file and the UIC, or user, accessing the file. Access is determined by four groups of permissions:

- System
- Owner
- Group
- World
And four permission bits:
- Read
- Write
- Execute
- Delete
The "system" access applies to any user whose UIC group code is less than or equal to the SYSGEN parameter MAXSYSGROUP (typically 8, or 10 octal
Octal
The octal numeral system, or oct for short, is the base-8 number system, and uses the digits 0 to 7. Numerals can be made from binary numerals by grouping consecutive binary digits into groups of three...
) (for example the SYSTEM user); "owner" and "group" apply to the owner of the file and that user's user group, and "world" applies to any other user. There is also a fifth permission bit, "Control", which is used to determine access to change file metadata such as protection. This group cannot be set explicitly; it is always set for System and Owner, and never for Group or World.
UIC-based access control is also affected by four system privileges, which allow users holding them to override access controls:
- BYPASS: user implicitly has RWED access to all files, regardless of file protection;
- READALL: user implicitly has R access to all files;
- SYSPRV: user may access files based on System protection;
- GRPPRV: user may access files based on System protection if their UIC group matches the file's group.
ACLs allow additional privileges to be assigned on a user– or group–specific basis; for example, a web server's UIC could be granted read access to all files in a particular directory. ACLs can be marked as inherited, where a directory file's ACL applies to all files underneath it. ACLs are modified using the EDIT/ACL command, and take the form of identifier/access pairs. For example, the ACL entry
(IDENTIFIER=HTTP$SERVER,ACCESS=READ+EXECUTE)
would allow the user HTTP$SERVER to read and execute the file.
Logical names
A logical name is a system variable which may reference a disk, directory or file, or contain other program-specific information. For example, the logical SYS$SYSDEVICE contains the system's boot device. A logical name normally refers to a single directory or disk, e.g. SYS$LOGIN: which is the user's login (home) directory (or directories); these logicals cannot be used as true disk names—SYS$LOGIN:[DIR]FILE is not a valid file specification. However, concealed logical names, defined by DEFINE/TRANSLATION=CONCEALED, can be used in that way; these rooted directories are defined with a trailing "." on the directory specification, hence$ DEFINE/TRANS=CONCEAL HOME DISK$USERS:[username.]
would allow HOME:[DIR]FILE to be used. More common are simple logicals which point to specific directories associated with some application software which may be located in on any disk or any directory. Hence logical ABC_EXE may point to a directory of executable programs for application ABC and ABC_TEMP may point to a directory of temporary files for that same application and this directory may be on the same disk and in the same directory tree as ABC_EXE or could be somewhere on another disk (and in a different directory tree).
Logical names do not have a close equivalent in POSIX operating systems. They resemble Unix environment variable
Environment variable
Environment variables are a set of dynamic named values that can affect the way running processes will behave on a computer.They can be said in some sense to create the operating environment in which a process runs...
s, except they are expanded by the filesystem, instead of the command shell or application program. They must be defined before use, so it is common for many logical names to be defined in the system startup command file, as well as user login command files.
The closest non-DEC operating system to support the concept of logical names is AmigaOS
AmigaOS
AmigaOS is the default native operating system of the Amiga personal computer. It was developed first by Commodore International, and initially introduced in 1985 with the Amiga 1000...
, through the ASSIGN command. AmigaOS's disk operating system, AmigaDOS
AmigaDOS
AmigaDOS is the disk operating system of the AmigaOS, which includes file systems, file and directory manipulation, the command-line interface, and file redirection....
, which is a port of TRIPOS
TRIPOS
TRIPOS is a computer operating system. Development started in 1976 at the Computer Laboratory of Cambridge University and it was headed by Dr. Martin Richards. The first version appeared in January 1978 and it originally ran on a PDP-11. Later it was ported to the Computer Automation LSI4 and the...
, bears some resemblance to DEC operating systems. For example, physical device names follow a pattern like DF0: for the first floppy disk, CDROM2: for the 3rd CD-ROM drive, etc. However, since the system can boot from any attached drive, the operating system creates the SYS: assignment to automatically reference the boot device used. Other assignments, LIBS:, PREFS:, C:, S:, et al. are also made, themselves referenced off SYS:. Users are, of course, allowed to create and destroy their own assignments too.
In VMS, logical names may reference other logical names (up to a predefined nesting limit of 10), and may contain lists of names to search for an existing filename. Some frequently referenced logical names are:
| logical name | meaning |
|---|---|
| SYS$INPUT | equivalent of standard input, program data source |
| SYS$OUTPUT | equivalent of standard output, program data destination |
| SYS$ERROR | equivalent of standard error Standard error Standard error can refer to:* Standard error , the estimated standard deviation or error of a series of measurements* Standard error stream, one of the standard streams in Unix-like operating systems... , program error message destination |
| SYS$COMMAND | source of batch file (that is, .COM command file) commands |
| TT | the terminal associated with the process |
| SYS$PRINT | the default printer or print queue |
| SYS$LOGIN | home directory for each user |
| SYS$SCRATCH | temporary folder Temporary folder In computing, a temporary folder or temporary directory is a directory used to hold temporary files. Many operating systems and some software automatically delete the contents of this directory at bootup or at regular intervals.... , directory for temporary files |
| SYS$SYSTEM | directory containing most system programs and a few vital data files, such as the system authorization file (accounts and passwords) |
| SYS$SHARE | shared runtime libraries, executables, etc. |
| SYS$LIBRARY | system and added libraries |
Record-oriented I/O: Record Management Services
Record Management ServicesRecord Management Services
Record Management Services are procedures in the VMS, RSTS/E, RT-11 and high-end RSX-11 operating systems that programs may call to process files and records within files. VMS RMS is an integral part of the system software; its procedures run in executive mode...
is the structured I/O
Input/output
In computing, input/output, or I/O, refers to the communication between an information processing system , and the outside world, possibly a human, or another information processing system. Inputs are the signals or data received by the system, and outputs are the signals or data sent from it...
layer of the VMS operating system. RMS provides comprehensive program support for managing structured file
Computer file
A computer file is a block of arbitrary information, or resource for storing information, which is available to a computer program and is usually based on some kind of durable storage. A file is durable in the sense that it remains available for programs to use after the current program has finished...
s, such as record-based and indexed database
Database
A database is an organized collection of data for one or more purposes, usually in digital form. The data are typically organized to model relevant aspects of reality , in a way that supports processes requiring this information...
files. The VMS filesystem, in conjunction with RMS, extends files access past simple byte
Byte
The byte is a unit of digital information in computing and telecommunications that most commonly consists of eight bits. Historically, a byte was the number of bits used to encode a single character of text in a computer and for this reason it is the basic addressable element in many computer...
-streams and allows OS-level support for a variety of rich files types. Each file in the VMS filesystem may be thought of as a database
Database
A database is an organized collection of data for one or more purposes, usually in digital form. The data are typically organized to model relevant aspects of reality , in a way that supports processes requiring this information...
, containing a series of records
Record (computer science)
In computer science, a record is an instance of a product of primitive data types called a tuple. In C it is the compound data in a struct. Records are among the simplest data structures. A record is a value that contains other values, typically in fixed number and sequence and typically indexed...
, each of which has one of more individual fields
Field (computer science)
In computer science, data that has several parts can be divided into fields. Relational databases arrange data as sets of database records, also called rows. Each record consists of several fields; the fields of all records form the columns....
. A text file, for example, is a list of records (lines) separated by a newline character. RMS is an example of a record-oriented filesystem
Record-oriented filesystem
In computer science, a record-oriented filesystem is a file system where files are stored as collections of records. There are several different record formats; the details vary depending on the particular system...
.
There are four record formats defined by RMS:
- Fixed length - all records in the file have the same length.
- Variable length - records vary in length, and every record is prefixed by a count byte giving its length.
- Variable record length with fixed-length control - records vary in length, but are preceded by a fixed-length control block.
- Stream - record vary in length, and every record is separated from the next one by a termination character. A text file is an example of a stream-format file using line feed or carriage returnCarriage returnCarriage return, often shortened to return, refers to a control character or mechanism used to start a new line of text.Originally, the term "carriage return" referred to a mechanism or lever on a typewriter...
to separate records.
There are four record access methods, or methods to retrieve extant records from files:
- Sequential Access - starting with a particular records, subsequent records are retrieved in order until the end of the file.
- Relative Record Number Access - records are retrieved via a record number relative to the beginning of the file.
- Record File Address Access - records are retrieved directly by their location in the file (RFA, or Record File Address).
- Indexed Access - records are retrieved via a key, in a form of key-value mappingAssociative arrayIn computer science, an associative array is an abstract data type composed of a collection of pairs, such that each possible key appears at most once in the collection....
.
Physical layout: the On-Disk Structure
At the disk level, ODS represents the filesystem as an array of blocks, a block being 512 contiguous bytes on one physical disk (volume). Disk blocks are assigned in clusters (originally 3 contiguous blocks but later increased with larger disk sizes). A file on the disk will ideally be entirely contiguous, i.e. the blocks which contain the file will be sequential, but disk fragmentation will sometimes require the file to located in discontiguous clusters in which case the fragments are called 'extents'. Disks may be combined with other disks to form a volume set and files stored anywhere across that set of disks, but larger disk sizes have reduced the use of volume sets because management of a single physical disk is simpler.Every file on a Files-11 disk (or volume set) has a unique file identification (FID), composed of three numbers: the file number (NUM), the file sequence number (SEQ), and the relative volume number (RVN). The NUM indicates where in the INDEXF.SYS file (see below) the metadata for the file is located; the SEQ is a generation number which incremented when the file is deleted and another file is created reusing the same INDEXF.SYS entry (so any dangling references to the old file do not accidentally point to the new one); and the RVN indicates the volume number on which the file is stored when using a volume set.
Directories
The structural support of an ODS volume is provided by a directory file—a special file containing a list of file names, file version numbers and their associated FIDs, similar to VSAM catalogs on MVSMVS
Multiple Virtual Storage, more commonly called MVS, was the most commonly used operating system on the System/370 and System/390 IBM mainframe computers...
. At the root of the directory structure is the master file directory (MFD), the root directory which contains (directly or indirectly) every file on the volume.
This diagram shows an example directory containing 3 files, and the way each filename is mapped to the INDEXF.SYS entry (each INDEXF entry contains more information; only the first few items are shown here).
The Master File Directory
At the top level of an ODS filesystem is the master file directory (MFD), which contains all top-level directory files (including itself), and several system files used to store filesystem information. On ODS-1 volumes, a two-level directory structure is used: each user identification code (UIC) has an associated user file directory (UFD), of the form [GROUP.USER]. On ODS-2 and later volumes, the layout of directories under the MFD is free-form, subject to a limit on the nesting of directories (8 levels on ODS-2 and unlimited on ODS-5). On multi-volume sets, the MFD is always stored on the first volume, and contains the subdirectories of all volumes.The following system files are present in the ODS MFD:
- INDEXF.SYS;1—Index file
- BITMAP.SYS;1—Storage bitmap file
- BADBLK.SYS;1—Bad block file
- 000000.DIR;1—The MFD directory file itself
- CORIMG.SYS;1—Core image file
- VOLSET.SYS;1—Volume set list file (ODS-2/5 only)
- CONTIN.SYS;1—Continuation file (ODS-2/5 only)
- BACKUP.SYS;1—Backup log file (ODS-2/5 only)
- BADLOG.SYS;1—Pending bad block (ODS-2/5 only)
- SECURITY.SYS;1—Volume security profile (ODS-2/5 only)
- QUOTA.SYS;1—Quota file (optional and available under ODS-2/5 only)
- GPT.SYS;1—GUID Partitioning Table (GPT) (OpenVMS I64 EFI boot structures, optional on OpenVMS Alpha)
Note that the filesystem implementation itself does not refer to these files by name, but by their file IDs, which always have the same values. Thus, INDEXF.SYS is always the file with NUM = 1 and SEQ = 1.
Index file: INDEXF.SYS
The index file contains the most basic information about a Files-11 volume set.There are two organizations of INDEXF.SYS, the traditional organization and the organization used on disks with GPT.SYS; with the GUID Partition Table (GPT) structures.
With the traditional organization, block 1 is the boot block, which contains the location of the primary bootstrap image, used to load the VMS operating system. This is always located at logical block 0 on the disk, so that the hardware firmware can read it. This block is always present, even on non-system (non-bootable) volumes.
After the boot block is the primary home block. This contains the volume name, the location of the extents comprising the remainder of the index file, the volume owner's UIC, and the volume protection information. There are normally several additional copies of the home block, known as the secondary home blocks, to allow recovery of the volume if it is lost or damaged.
On disks with GPT.SYS, GPT.SYS contains the equivalent of the boot block (known as the Master Boot Record (MBR)), and there is no primary home block. All home blocks present on a GPT-based disk are alternate home blocks. These structures are not included in INDEXF.SYS, and the blocks of the INDEXF.SYS file are unused.
The rest of the index file is composed of file headers, which describe the extents allocated to the files residing on the volume, and file metadata such as the owner UIC, ACLs and protection information. Each file is described by one or more file headers—more than one can be required when a file has a large number of extents. The file header is a fixed-length block, but contains both fixed– and variable–length sections:
- The header contains the NUM and SEQ, the protection (security) information, and the location(s) of the rest of the file header.
- The ident section contains the accounting metadata: the filename, creation and modification times, and the time of the last backup.
- The map describes which physical disk blocks (extents) map to each virtual block of the file.
- The access control list contains the ACL information for the file.
- The reserved area is space at the end of the file header which is not used by the operating system. This can be used by for customer- or vendor-specific information.
- The last two bytes of the header are a checksumChecksumA checksum or hash sum is a fixed-size datum computed from an arbitrary block of digital data for the purpose of detecting accidental errors that may have been introduced during its transmission or storage. The integrity of the data can be checked at any later time by recomputing the checksum and...
of the previous 255 words, to verify the validity of the header.
If possible, the map and ACL sections of the header are contained completely in the primary header. However, if the ACL is too long, or the file contains too many extents, there will not be enough space in the primary header to store them. In this case, an extension header is allocated to store the overflow information.
Layout of the INDEXF.SYS header.
The file header begins with 4 offsets (IDOFFSET, MPOFFSET, ACOFFSET and ROFFSET). Since the size of the areas after the fixed-length header may vary (such as the map and ACL areas), the offsets are required to locate these additional areas. Each offset is the number of 16-bit words from the beginning of the file header to the beginning of that area.
If the file requires multiple headers, the extension segment number (SEGNUM) contains the sequence number of this header, beginning at 0 in the first entry in INDEXF.SYS.
STRUCLEV contains the current structure level (in the high byte) and version (in the low byte) of the filesystem; ODS-2 being structure level 2. An increase in the version number indicates a backwards-compatible change that older software may ignore; changes in the structure level itself are incompatible.
W_FID (containing three values: FID_NUM, FID_SEQ and FID_RVN, corresponding to the file, sequence, and relative volume number) contains the ID of this file; EXT_FID (again composed of three values) holds the location of the next extension header, if any. In both of these values, the RVN is specified as 0 to represent the "current" volume (0 is not normally a valid RVN).
FILECHAR contains several flags which affect how the file is handled or organised:
- NOBACKUP causes this file to be ignored when a backupBackupIn information technology, a backup or the process of backing up is making copies of data which may be used to restore the original after a data loss event. The verb form is back up in two words, whereas the noun is backup....
is run. - WRITEBACK enables cached (delayed) writes to the file.
- READCHECK causes all reads of the file to be done twice, and compared to ensure data integrity.
- WRITCHECK results in all writes being verified by a subsequent read and compare.
- CONTIGB causes the OS to attempt to allocate storage for the file in as contiguous a manner as possible.
- LOCKED is set if the file is deaccess-locked. If set, this indicates that the file was not properly closed after its last use, and the contents may be inconsistent.
- CONTIG indicates that the file is stored contiguously on disk; that is, each virtual block
 is mapped to the logical (physical) block
is mapped to the logical (physical) block  , for some constant
, for some constant  .
. - BADACL is set if the file has an invalid access control list.
- SPOOL is set if the file is a spool file, such as an intermediate file used during printing.
- DIRECTORY is set if the file is a directory.
- BADBLOCK is set if the file contains bad blocks.
- MARKDEL is set if the file has been marked for deletion, but is still in use; it will be deleted once closed by the last user.
- NOCHARGE, if set, causes space used by the file to not be taken from the owner's storage quota.
- ERASE causes the file's contents to be overwritten when it is deleted.
ACCMODE describes the privilege level at which a process must be running in order to access the file. VMS defines four privilege levels: user, supervisor, exec, and kernel. Each type of access - read, write, execute and delete - is encoded as a 2-bit integer.
FILEPROT contains the discretionary access control
Discretionary access control
In computer security, discretionary access control is a kind of access control defined by the Trusted Computer System Evaluation Criteria "as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong...
information for the file. It is divided into 4 groups of 4 bits each: system, owner, group and world. Bit 0 corresponds to read access, 1 to write, 2 to execute and 3 to delete. Setting a bit denies a particular access to a group; clearing it allows it.
If the file header is an extension header, BACKLINK contains the file ID of the primary header; otherwise, it contains the file ID of the directory file containing the primary entry for the file.
Other files
- Storage bitmap file: BITMAP.SYS
- The bitmap file is responsible for storing information regarding used and available space on a volume. It contains the storage control block (SCB), which includes summary information detailing ???, and the bitmap, an array of bits to indicate if a cluster of blocks on the disk is free or allocated. In early versions of VMS the cluster comprised 3 blocks but as disk sizes have increased, so has the cluster size.
- Bad block file: BADBLK.SYS
- The bad block file contains all of the known bad blocks on the physical volume. The purpose is to prevent the system from allocating them to files. This file was used more in the early days when disks were typically manufactured with more bad patches on the surface.
- Volume set list file: VOLSET.SYS
- The volume set list is located on volume 1 of a volume set, and contains a list of labels of all volumes in the set, and the set's volume name.
- Continuation file: CONTIN.SYS
- When a file on a multi-volume set crosses the boundary of two constituent volumes, the continuation file is used as its extension header and describes the volume where the rest of the file can be found.
- Quota file: QUOTA.SYS
- The quota file contains information of each UIC's disk space usage on a volume. It contains a record for each UIC with space allocated to it on a volume, along with information on how much space is being used by that UIC. NOTE: The DISK QUOTA feature is optional and the file will only exist if the feature was ever enabled.
- Volume security profile: SECURITY.SYS
- The volume security profile contains the volume's owner UIC, the volume protection mask, and its access control list.
- GUID Partitioning Table: GPT.SYS
- This file overlays and protects the MBR (Master Boot Record) and GPT (GUID Partitioning Table) disk structures utilized for and by the Extensible Firmware InterfaceExtensible Firmware InterfaceThe Unified Extensible Firmware Interface is a specification that defines a software interface between an operating system and platform firmware...
-compliant firmware. This file is created by default during OpenVMS I64 disk initialization, and is optionally created (with INITIALIZE/GPT) on OpenVMS Alpha.
See also
- Comparison of file systemsComparison of file systems-General information:-Limits:-Metadata:-Features:-Allocation and layout policies:-Supporting operating systems:-See also:* Comparison of archive formats* Comparison of file archivers* List of archive formats* List of file archivers...
- NTFSNTFSNTFS is the standard file system of Windows NT, including its later versions Windows 2000, Windows XP, Windows Server 2003, Windows Server 2008, Windows Vista, and Windows 7....
- Has many structural and metadata similarities with Files-11 and is almost certainly derived from it.
External links
- OpenVMS documentation: Guide to OpenVMS File Applications
- http://www.vms2linux.de

