
Password strength
Encyclopedia
Password strength is a measure of the effectiveness of a password
in resisting guessing and brute-force attacks. In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. The strength of a password is a function of length, complexity, and unpredictability.
Using strong passwords lowers overall risk
of a security breach, but strong passwords do not replace the need for other effective security controls
. The effectiveness of a password of a given strength is strongly determined by the design and implementation of the authentication system software, particularly how frequently password guesses can be tested by an attacker and how securely information on user passwords is stored and transmitted. Risks are also posed by several means of breaching computer security which are unrelated to password strength. Such means include wiretapping
, phishing
, keystroke logging
, social engineering
, dumpster diving
, side-channel attacks, and software vulnerabilities
.
.)
In 2010, the Georgia Tech Research Institute
developed a method of using GPGPU
to crack passwords much faster. As of 2011, commercial products are available that claim the ability to test up to 2,800,000,000 passwords per second on a standard desktop computer using a high-end graphics processor. Such a device can crack a 10 letter single-case password in one day. Note that the work can be distributed over many computers for an additional speedup proportional to the number of available computers with comparable GPUs. Special key stretching hashes are available that take a relatively long time to compute, reducing the rate at which guessing can take place. Although it is considered best practice to use key stretching, many common systems do not.
Another situation where quick guessing is possible is when the password is used to form a cryptographic key. In such cases, an attacker can quickly check to see if a guessed password successfully decodes encrypted data. For example, one commercial product claims to test 103,000 WPA
PSK passwords per second.
If a cryptographic salt is not used in the password system, the attacker can pre-compute hash values for common passwords variants and for all passwords shorter than a certain length, allowing very rapid recovery. Long lists of pre-computed password hashes can be efficiently stored using rainbow tables. Such tables are available on the Internet for several common password authentication systems.
Commonly, passwords are initially created by asking a human to choose a password, sometimes guided by suggestions or restricted by a set of rules. This typically happens at the time of account creation for computer systems or Internet Web sites. In this case, only estimates of strength are possible, since humans tend to follow patterns in such tasks, and those patterns will always assist an attacker. In addition, lists of commonly chosen passwords are widely available for use by password guessing programs. Any of the numerous online dictionaries for various languages is such a list. All items in such lists are considered weak, as are passwords that are simple modifications of them. Either can be quickly tried. For some decades, investigations of passwords on multi-user computer systems have shown that 40% or more are readily guessed using only computer programs, and more can be found when information about a particular user is taken into account during the attack.
Automatic password generation, if properly done, can avoid any connection between a password and its user. For example, one's pet's name is quite unlikely to be generated by such a system. For a password chosen from a sufficiently large 'password space', brute force search time can be made so long as to be infeasible. However, truly random passwords can be tricky to generate and they tend to be difficult for the user to remember.
, measured in bits, a concept from information theory
. Instead of the number of guesses needed to find the password with certainty, the base-2 logarithm
of that number is given, which is the number of "entropy bits" in a password. A password with, say, 42 bits of strength calculated in this way would be as strong as a string of 42 bits chosen randomly, say by a fair coin toss. Put another way, a password with 42 bits of strength would require 242 attempts to exhaust all possibilities during a brute force search. Thus, adding one bit of entropy to a password doubles the number of guesses required, which makes an attacker's task twice as difficult. On average, an attacker will have to try half the possible passwords before finding the correct one. (see Law of large numbers
)
character set), syllables designed to form pronounceable passwords, or even words from a word list (thus forming a passphrase
).
The strength of random passwords depends on the actual entropy of the underlying number generator; these are often not truly random, but pseudo random. Many publicly available password generators use random number generators found in programming libraries that offer limited entropy. However most modern operating systems offer cryptographically strong random number generators that are suitable for password generation. It is also possible to use ordinary dice
to generate random passwords. See Random password generator#Stronger methods. Random password programs often have the ability to ensure that the resulting password complies with a local password policy
; for instance, by always producing a mix of letters, numbers and special characters.
For passwords generated by a process that randomly selects a string of symbols of length, L, from a set of N possible symbols, the number of possible passwords can be found by raising the number of symbols to the power L, i.e. NL. The strength of a random password as measured by the information entropy
is just the base-2 logarithm
or log2 of the number of possible passwords, assuming each symbol in the password is produced independently. Thus a random password's information entropy, H, is given by the formula
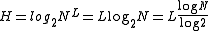
where N is the number of possible symbols and L is the number of symbols in the password. H is measured in bit
s.
character set (roughly those on a standard U.S. English keyboard) include 26 letters (in two case
variants), 10 digits, and 32 non-alphanumeric symbols (i.e., punctuation, grouping, etc.), for a total of 94 symbols (95 if space is included). However the same strength can always be achieved with a smaller symbol set by choosing a longer password. In the extreme, binary passwords can be very secure, even though only two possible symbols are used. See table below. Thus a 14 character password consisting of only random lowercase letters has the same strength (4.7×14 = 65.8 bits) as a ten character password chosen at random from all printable ASCII characters (65.55 bits).
Note that the full strength associated with using the entire ASCII character set (numerals, mixed case letters and special characters) is only achieved if each character in the password is chosen randomly from that set. Capitalizing a letter and adding a couple of numbers and a special character to a password will not achieve the same strength. If the numbers and special character are added in predictable ways, say at the beginning and end of the password, they could even lower password strength compared to an all letter random password of the same length.
Because national keyboard implementations vary, not all 94 ASCII printable characters can be used everywhere. This can present a problem to an international traveler who wished to log into remote system using a keyboard on a local computer. See keyboard layout
.
Authentication programs (e.g., those which determines access to a computer system) vary in which characters they allow in passwords. Some do not recognize case differences (e.g., the upper-case "E" is considered equivalent to the lower-case "e"), others prohibit some of the other symbols. In the past few decades, systems have permitted more characters in passwords, but limitations still exist. Many hand held devices, such as PDA
s and smart phones, require complex shift sequences to enter special characters. Systems also vary in the maximum length of passwords allowed, with some older systems limited to eight characters.
Thus, in one analysis of over 3 million eight-character passwords, the letter "e" was used over 1.5 million times, while the letter "f" was only used 250,000 times. A uniform distribution would have had each character being used about 900,000 times. The most common number used is "1", whereas the most common letters are a, e, o, and r.
NIST suggests the following scheme to estimate the entropy of human-generated passwords:
This would imply that an eight-character human-selected password without upper case letters and non-alphabetic characters has about 18 bits of entropy. However the scheme is based on the basic assumption that users select passwords with the same entropy as ordinary English text.
Users rarely make full use of larger characters sets in forming passwords. For example, hacking results obtained from a MySpace phishing scheme in 2006 revealed 34,000 passwords, of which only 8.3% used mixed case, numbers, and symbols.
, most people are good at securing their wallets or purses, which is a "great place" to store a written password.
Some basic benchmarks have been established for brute force searches in the context of attempting to find keys used in encryption. The problem is not the same since these approaches involve astronomical numbers of trials, but the results are suggestive for password choice. In 1999, an Electronic Frontier Foundation project
broke 56-bit DES
encryption in less than a day using specially designed hardware. In 2002, distributed.net
cracked a 64-bit key in 4 years, 9 months, and 23 days. As of October 12, 2011, distributed.net estimates that cracking a 72-bit key using current hardware will take about 45,579 days or 124.8 years. Due to currently understood limitations from fundamental physics, there is no expectation that any digital computer (or combination) will be capable of breaking 256-bit encryption via a brute-force attack. Whether or not quantum computers will be able to do so in practice is still unknown, though theoretical analysis suggests such possibilities.
As a result, there can be no exact answer to the somewhat different problem of the password strength required to resist brute force attack in practice. NIST recommends 80-bits for the most secure passwords, which can nearly be achieved with a 95-character choice (e.g., the original ASCII character set) with a 12-character random password (12 x 6.5 bits = 78). A 2010 Georgia Tech Research Institute
study also recommended a 12-character random password, but as a minimum length requirement.
Some guidelines advise against writing passwords down, while others, noting the large numbers of password protected systems users must access, encourage writing down passwords as long as the written password lists are kept in a safe place, such as a wallet or safe, not attached to a monitor or in an unlocked desk drawer.
The possible character set for a password can be constrained by different web sites or by the range of keyboards on which the password must be entered.
There are many other ways a password can be weak, corresponding to the strengths of various attack schemes; the core principle is that a password should have high entropy (usually taken to be equivalent to randomness) and not be readily derivable by any "clever" pattern, nor should passwords be mixed with information identifying the user. On-line services often provide a restore password function that a hacker can figure out and by doing so bypass a password. Choosing hard to guess restore password questions can further secure the password.
For example, password expiration is often covered by password policies. Password expiration serves two purposes:
Some argue that password expirations have become obsolete, since:
The following measures may increase acceptance of strong password requirements, if carefully used:
A Microsoft
expert was quoted as saying at a 2005 security conference: "I claim that password policy should say you should write down your password. I have 68 different passwords. If I am not allowed to write any of them down, guess what I am going to do? I am going to use the same password on every one of them."
If passwords are written down, they should never be kept in obvious places such as address books, Rolodex
files, under drawers or keyboards, or behind pictures. Perhaps the worst, but all too common, location is a Post-It note on the computer monitor. Better locations are a safe deposit box
or a locked file approved for information of sensitivity comparable to that protected by the password. Most locks on office file cabinets are far from adequate. Software is available for popular hand-held computers that can store passwords for numerous accounts in encrypted form. Another approach is to encrypt
by hand on paper and remember the encryption method and key. And another approach is to use a single password or slightly-varying passwords for low-security accounts and select distinctly separate strong passwords for a smaller number of high-value applications such as for online banking
.
, as well as calculating the entropy of the generated password. A good password manager will provide resistance against attacks such as key logging, clipboard logging and various other memory spying techniques.
Even when run on local machines, without network involvement, there are potential problems. Implementational problems (e.g., errors in programming or algorithm choice) are always possible, of course, and many of these exhibit no discernible clues for a user or administrator. And, such programs are limited to estimates of brute force attack vulnerability regardless of where they are run. Passwords which are vulnerable to guessing attacks cannot be checked automatically, as not everyone's pet is named Rover or Fluffy, nor do all children or relatives have common names, readily found in lists.
As a result, use of such checking facilities cannot be recommended. The tests they can apply are easy for users to perform, if they understand some basic principles. And the increased attack opportunities should be avoided as well, on the general principle of not making an attacker's task easier.
Password
A password is a secret word or string of characters that is used for authentication, to prove identity or gain access to a resource . The password should be kept secret from those not allowed access....
in resisting guessing and brute-force attacks. In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. The strength of a password is a function of length, complexity, and unpredictability.
Using strong passwords lowers overall risk
Risk
Risk is the potential that a chosen action or activity will lead to a loss . The notion implies that a choice having an influence on the outcome exists . Potential losses themselves may also be called "risks"...
of a security breach, but strong passwords do not replace the need for other effective security controls
Security controls
Security controls are safeguards or countermeasures to avoid, counteract or minimize security risks.To help review or design security controls, they can be classified by several criteria, for example according to the time that they act, relative to a security incident:*Before the event, preventive...
. The effectiveness of a password of a given strength is strongly determined by the design and implementation of the authentication system software, particularly how frequently password guesses can be tested by an attacker and how securely information on user passwords is stored and transmitted. Risks are also posed by several means of breaching computer security which are unrelated to password strength. Such means include wiretapping
Telephone tapping
Telephone tapping is the monitoring of telephone and Internet conversations by a third party, often by covert means. The wire tap received its name because, historically, the monitoring connection was an actual electrical tap on the telephone line...
, phishing
Phishing
Phishing is a way of attempting to acquire information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT...
, keystroke logging
Keystroke logging
Keystroke logging is the action of tracking the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored...
, social engineering
Social engineering (security)
Social engineering is commonly understood to mean the art of manipulating people into performing actions or divulging confidential information...
, dumpster diving
Dumpster diving
Dumpster diving is the practice of sifting through commercial or residential trash to find items that have been discarded by their owners, but that may be useful to the dumpster diver.-Etymology and alternate names:...
, side-channel attacks, and software vulnerabilities
Vulnerability (computing)
In computer security, a vulnerability is a weakness which allows an attacker to reduce a system's information assurance.Vulnerability is the intersection of three elements: a system susceptibility or flaw, attacker access to the flaw, and attacker capability to exploit the flaw...
.
Determining password strength
There are 2 factors to consider in determining password strength: the ease with which an attacker can check the validity of a guessed password, and the average number of guesses the attacker must make to find the correct password. The first factor is determined by how the password is stored and what it is used for, while the second factor is determined by how long the password is, what set of symbols it is drawn from and how it is created.Password guess validation
The most obvious way to test a guessed password is to attempt to use it to access the resource the password was meant to protect. However, this can be slow and many systems will delay or block access to an account after several wrong passwords are entered. On the other hand, systems that use passwords for authentication must store them in some form to check against entered values. Usually only a cryptographic hash of a password is stored instead of the password itself. If the hash is strong enough, it is very hard to reverse it, so an attacker that gets hold of the hash value cannot directly recover the password. However, if the cryptographic hash data files have been stolen, knowledge of the hash value lets the attacker quickly test guesses. (See Password crackingPassword cracking
Password cracking is the process of recovering passwords from data that has been stored in or transmitted by a computer system. A common approach is to repeatedly try guesses for the password...
.)
In 2010, the Georgia Tech Research Institute
Georgia Tech Research Institute
The Georgia Tech Research Institute is the nonprofit applied research arm of the Georgia Institute of Technology in Atlanta, Georgia, United States...
developed a method of using GPGPU
GPGPU
General-purpose computing on graphics processing units is the technique of using a GPU, which typically handles computation only for computer graphics, to perform computation in applications traditionally handled by the CPU...
to crack passwords much faster. As of 2011, commercial products are available that claim the ability to test up to 2,800,000,000 passwords per second on a standard desktop computer using a high-end graphics processor. Such a device can crack a 10 letter single-case password in one day. Note that the work can be distributed over many computers for an additional speedup proportional to the number of available computers with comparable GPUs. Special key stretching hashes are available that take a relatively long time to compute, reducing the rate at which guessing can take place. Although it is considered best practice to use key stretching, many common systems do not.
Another situation where quick guessing is possible is when the password is used to form a cryptographic key. In such cases, an attacker can quickly check to see if a guessed password successfully decodes encrypted data. For example, one commercial product claims to test 103,000 WPA
WPA
- Agencies and organizations :*World Pool-Billiard Association*World Psychiatric Association- United States :*Washington Project for the Arts*Women's Prison Association...
PSK passwords per second.
If a cryptographic salt is not used in the password system, the attacker can pre-compute hash values for common passwords variants and for all passwords shorter than a certain length, allowing very rapid recovery. Long lists of pre-computed password hashes can be efficiently stored using rainbow tables. Such tables are available on the Internet for several common password authentication systems.
Password creation
Passwords are created either automatically (using randomizing equipment) or by a human. The strength of randomly chosen passwords against a brute force attack can be calculated with precision.Commonly, passwords are initially created by asking a human to choose a password, sometimes guided by suggestions or restricted by a set of rules. This typically happens at the time of account creation for computer systems or Internet Web sites. In this case, only estimates of strength are possible, since humans tend to follow patterns in such tasks, and those patterns will always assist an attacker. In addition, lists of commonly chosen passwords are widely available for use by password guessing programs. Any of the numerous online dictionaries for various languages is such a list. All items in such lists are considered weak, as are passwords that are simple modifications of them. Either can be quickly tried. For some decades, investigations of passwords on multi-user computer systems have shown that 40% or more are readily guessed using only computer programs, and more can be found when information about a particular user is taken into account during the attack.
Automatic password generation, if properly done, can avoid any connection between a password and its user. For example, one's pet's name is quite unlikely to be generated by such a system. For a password chosen from a sufficiently large 'password space', brute force search time can be made so long as to be infeasible. However, truly random passwords can be tricky to generate and they tend to be difficult for the user to remember.
Entropy as a measure of password strength
It is usual in the computer industry to estimate password strength in terms of information entropyInformation entropy
In information theory, entropy is a measure of the uncertainty associated with a random variable. In this context, the term usually refers to the Shannon entropy, which quantifies the expected value of the information contained in a message, usually in units such as bits...
, measured in bits, a concept from information theory
Information theory
Information theory is a branch of applied mathematics and electrical engineering involving the quantification of information. Information theory was developed by Claude E. Shannon to find fundamental limits on signal processing operations such as compressing data and on reliably storing and...
. Instead of the number of guesses needed to find the password with certainty, the base-2 logarithm
Binary logarithm
In mathematics, the binary logarithm is the logarithm to the base 2. It is the inverse function of n ↦ 2n. The binary logarithm of n is the power to which the number 2 must be raised to obtain the value n. This makes the binary logarithm useful for anything involving powers of 2,...
of that number is given, which is the number of "entropy bits" in a password. A password with, say, 42 bits of strength calculated in this way would be as strong as a string of 42 bits chosen randomly, say by a fair coin toss. Put another way, a password with 42 bits of strength would require 242 attempts to exhaust all possibilities during a brute force search. Thus, adding one bit of entropy to a password doubles the number of guesses required, which makes an attacker's task twice as difficult. On average, an attacker will have to try half the possible passwords before finding the correct one. (see Law of large numbers
Law of large numbers
In probability theory, the law of large numbers is a theorem that describes the result of performing the same experiment a large number of times...
)
Random passwords
Random passwords consist of a string of symbols of specified length taken from some set of symbols using a random selection process in which each symbol is equally likely to be selected. The symbols can be individual characters from a character set (e.g., the ASCIIASCII
The American Standard Code for Information Interchange is a character-encoding scheme based on the ordering of the English alphabet. ASCII codes represent text in computers, communications equipment, and other devices that use text...
character set), syllables designed to form pronounceable passwords, or even words from a word list (thus forming a passphrase
Passphrase
A passphrase is a sequence of words or other text used to control access to a computer system, program or data. A passphrase is similar to a password in usage, but is generally longer for added security. Passphrases are often used to control both access to, and operation of, cryptographic programs...
).
The strength of random passwords depends on the actual entropy of the underlying number generator; these are often not truly random, but pseudo random. Many publicly available password generators use random number generators found in programming libraries that offer limited entropy. However most modern operating systems offer cryptographically strong random number generators that are suitable for password generation. It is also possible to use ordinary dice
Dice
A die is a small throwable object with multiple resting positions, used for generating random numbers...
to generate random passwords. See Random password generator#Stronger methods. Random password programs often have the ability to ensure that the resulting password complies with a local password policy
Password policy
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organization's official regulations and may be taught as part of security awareness training...
; for instance, by always producing a mix of letters, numbers and special characters.
For passwords generated by a process that randomly selects a string of symbols of length, L, from a set of N possible symbols, the number of possible passwords can be found by raising the number of symbols to the power L, i.e. NL. The strength of a random password as measured by the information entropy
Information entropy
In information theory, entropy is a measure of the uncertainty associated with a random variable. In this context, the term usually refers to the Shannon entropy, which quantifies the expected value of the information contained in a message, usually in units such as bits...
is just the base-2 logarithm
Binary logarithm
In mathematics, the binary logarithm is the logarithm to the base 2. It is the inverse function of n ↦ 2n. The binary logarithm of n is the power to which the number 2 must be raised to obtain the value n. This makes the binary logarithm useful for anything involving powers of 2,...
or log2 of the number of possible passwords, assuming each symbol in the password is produced independently. Thus a random password's information entropy, H, is given by the formula
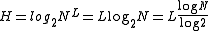
where N is the number of possible symbols and L is the number of symbols in the password. H is measured in bit
Bit
A bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
s.
| Symbol set | Symbol count N | Entropy per symbol H |
|---|---|---|
| Arabic numerals Arabic numerals Arabic numerals or Hindu numerals or Hindu-Arabic numerals or Indo-Arabic numerals are the ten digits . They are descended from the Hindu-Arabic numeral system developed by Indian mathematicians, in which a sequence of digits such as "975" is read as a numeral... (0–9) (e.g. PIN Personal identification number A personal identification number is a secret numeric password shared between a user and a system that can be used to authenticate the user to the system. Typically, the user is required to provide a non-confidential user identifier or token and a confidential PIN to gain access to the system... ) |
10 | bits |
| hexadecimal Hexadecimal In mathematics and computer science, hexadecimal is a positional numeral system with a radix, or base, of 16. It uses sixteen distinct symbols, most often the symbols 0–9 to represent values zero to nine, and A, B, C, D, E, F to represent values ten to fifteen... numerals (0–9, A-F) (e.g. WEP Wired Equivalent Privacy Wired Equivalent Privacy is a weak security algorithm for IEEE 802.11 wireless networks. Introduced as part of the original 802.11 standard ratified in September 1999, its intention was to provide data confidentiality comparable to that of a traditional wired network... keys) |
16 | 4.0000 bits |
| Case insensitive Case sensitivity Text sometimes exhibits case sensitivity; that is, words can differ in meaning based on differing use of uppercase and lowercase letters. Words with capital letters do not always have the same meaning when written with lowercase letters.... Latin alphabet Latin alphabet The Latin alphabet, also called the Roman alphabet, is the most recognized alphabet used in the world today. It evolved from a western variety of the Greek alphabet called the Cumaean alphabet, which was adopted and modified by the Etruscans who ruled early Rome... (a-z or A-Z) |
26 | bits |
| Case insensitive alphanumeric Alphanumeric Alphanumeric is a combination of alphabetic and numeric characters, and is used to describe the collection of Latin letters and Arabic digits or a text constructed from this collection. There are either 36 or 62 alphanumeric characters. The alphanumeric character set consists of the numbers 0 to... (a-z or A-Z, 0–9) |
36 | bits |
| Case sensitive Case sensitivity Text sometimes exhibits case sensitivity; that is, words can differ in meaning based on differing use of uppercase and lowercase letters. Words with capital letters do not always have the same meaning when written with lowercase letters.... Latin alphabet (a-z, A-Z) |
52 | bits |
| Case sensitive alphanumeric (a-z, A-Z, 0–9) | 62 | bits |
| All ASCII printable characters | 95 | bits |
| All extended ASCII printable characters Extended ASCII The term extended ASCII describes eight-bit or larger character encodings that include the standard seven-bit ASCII characters as well as others... |
218 | bits |
| Diceware Diceware Diceware is a method for creating passphrases, passwords, and other cryptographic variables using ordinary dice as a hardware random number generator. For each word in the passphrase, five dice rolls are required. The numbers that come up in the rolls are assembled as a five digit number, e.g.... word list |
7776 | bits |
Password strength depends on symbol set and length
Increasing the number of possible symbols from which random passwords are chosen will increase the strength of generated passwords of any given length. For example, the printable characters in the ASCIIASCII
The American Standard Code for Information Interchange is a character-encoding scheme based on the ordering of the English alphabet. ASCII codes represent text in computers, communications equipment, and other devices that use text...
character set (roughly those on a standard U.S. English keyboard) include 26 letters (in two case
Letter case
In orthography and typography, letter case is the distinction between the larger majuscule and smaller minuscule letters...
variants), 10 digits, and 32 non-alphanumeric symbols (i.e., punctuation, grouping, etc.), for a total of 94 symbols (95 if space is included). However the same strength can always be achieved with a smaller symbol set by choosing a longer password. In the extreme, binary passwords can be very secure, even though only two possible symbols are used. See table below. Thus a 14 character password consisting of only random lowercase letters has the same strength (4.7×14 = 65.8 bits) as a ten character password chosen at random from all printable ASCII characters (65.55 bits).
| Desired password entropy H | Arabic numerals Arabic numerals Arabic numerals or Hindu numerals or Hindu-Arabic numerals or Indo-Arabic numerals are the ten digits . They are descended from the Hindu-Arabic numeral system developed by Indian mathematicians, in which a sequence of digits such as "975" is read as a numeral... | Case insensitive Case sensitivity Text sometimes exhibits case sensitivity; that is, words can differ in meaning based on differing use of uppercase and lowercase letters. Words with capital letters do not always have the same meaning when written with lowercase letters.... Latin alphabet Latin alphabet The Latin alphabet, also called the Roman alphabet, is the most recognized alphabet used in the world today. It evolved from a western variety of the Greek alphabet called the Cumaean alphabet, which was adopted and modified by the Etruscans who ruled early Rome... | Case insensitive alphanumeric Alphanumeric Alphanumeric is a combination of alphabetic and numeric characters, and is used to describe the collection of Latin letters and Arabic digits or a text constructed from this collection. There are either 36 or 62 alphanumeric characters. The alphanumeric character set consists of the numbers 0 to... | Case sensitive Case sensitivity Text sometimes exhibits case sensitivity; that is, words can differ in meaning based on differing use of uppercase and lowercase letters. Words with capital letters do not always have the same meaning when written with lowercase letters.... Latin alphabet | Case sensitive alphanumeric | All ASCII printable characters |
|---|---|---|---|---|---|---|
| 32 bits | 10 | 7 | 7 | 6 | 6 | 5 |
| 40 bits | 13 | 9 | 8 | 8 | 7 | 7 |
| 64 bits | 20 | 14 | 13 | 12 | 11 | 10 |
| 80 bits | 25 | 18 | 16 | 15 | 14 | 13 |
| 96 bits | 29 | 21 | 19 | 17 | 17 | 15 |
| 128 bits | 39 | 28 | 25 | 23 | 22 | 20 |
| 160 bits | 49 | 35 | 31 | 29 | 27 | 25 |
| 192 bits | 58 | 41 | 38 | 34 | 33 | 30 |
| 224 bits | 68 | 48 | 44 | 40 | 38 | 35 |
| 256 bits | 78 | 55 | 50 | 45 | 43 | 40 |
| 384 bits | 116 | 82 | 75 | 68 | 65 | 59 |
| 512 bits | 155 | 109 | 100 | 90 | 86 | 79 |
| 1024 bits | 309 | 218 | 199 | 180 | 172 | 157 |
Note that the full strength associated with using the entire ASCII character set (numerals, mixed case letters and special characters) is only achieved if each character in the password is chosen randomly from that set. Capitalizing a letter and adding a couple of numbers and a special character to a password will not achieve the same strength. If the numbers and special character are added in predictable ways, say at the beginning and end of the password, they could even lower password strength compared to an all letter random password of the same length.
Because national keyboard implementations vary, not all 94 ASCII printable characters can be used everywhere. This can present a problem to an international traveler who wished to log into remote system using a keyboard on a local computer. See keyboard layout
Keyboard layout
A keyboard layout is any specific mechanical, visual, or functional arrangement of the keys, legends, or key–meaning associations of a computer, typewriter, or other typographic keyboard....
.
Authentication programs (e.g., those which determines access to a computer system) vary in which characters they allow in passwords. Some do not recognize case differences (e.g., the upper-case "E" is considered equivalent to the lower-case "e"), others prohibit some of the other symbols. In the past few decades, systems have permitted more characters in passwords, but limitations still exist. Many hand held devices, such as PDA
PDA
A PDA is most commonly a Personal digital assistant, also known as a Personal data assistant, a mobile electronic device.PDA may also refer to:In science, medicine and technology:...
s and smart phones, require complex shift sequences to enter special characters. Systems also vary in the maximum length of passwords allowed, with some older systems limited to eight characters.
Human-generated passwords
People are notoriously remiss at achieving sufficient entropy to produce satisfactory passwords. Some stage magicians exploit this inability for amusement, in a minor way, by divining supposed random choices (of numbers, say) made by audience members.Thus, in one analysis of over 3 million eight-character passwords, the letter "e" was used over 1.5 million times, while the letter "f" was only used 250,000 times. A uniform distribution would have had each character being used about 900,000 times. The most common number used is "1", whereas the most common letters are a, e, o, and r.
NIST suggests the following scheme to estimate the entropy of human-generated passwords:
- the entropy of the first character is four bits;
- the entropy of the next seven characters are two bits per character;
- the ninth through the twentieth character has 1.5 bits of entropy per character;
- characters 21 and above have one bit of entropy per character.
- a "bonus" of six bits is added if both upper case letters and non-alphabetic characters are used.
This would imply that an eight-character human-selected password without upper case letters and non-alphabetic characters has about 18 bits of entropy. However the scheme is based on the basic assumption that users select passwords with the same entropy as ordinary English text.
Users rarely make full use of larger characters sets in forming passwords. For example, hacking results obtained from a MySpace phishing scheme in 2006 revealed 34,000 passwords, of which only 8.3% used mixed case, numbers, and symbols.
Bit strength threshold
As a practical matter, passwords must be both reasonable and functional for the end user as well as strong enough for the intended purpose. Passwords that are too difficult to remember may be forgotten and so are more likely to be written on paper, which some consider a security risk. In contrast, others argue that forcing users to remember passwords without assistance can only accommodate weak passwords, and thus poses a greater security risk. According to Bruce SchneierBruce Schneier
Bruce Schneier is an American cryptographer, computer security specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, and is the founder and chief technology officer of BT Managed Security Solutions, formerly Counterpane Internet...
, most people are good at securing their wallets or purses, which is a "great place" to store a written password.
Some basic benchmarks have been established for brute force searches in the context of attempting to find keys used in encryption. The problem is not the same since these approaches involve astronomical numbers of trials, but the results are suggestive for password choice. In 1999, an Electronic Frontier Foundation project
EFF DES cracker
In cryptography, the EFF DES cracker is a machine built by the Electronic Frontier Foundation in 1998 to perform a brute force search of DES cipher's key space — that is, to decrypt an encrypted message by trying every possible key...
broke 56-bit DES
DES
-Computing:* Data Encryption Standard* DirectShow Editing Services, an Application Programming Interface-Medical:* Diethylstilbestrol, a synthetic estrogen and the origin of the phrase "DES daughter"* DES gene, which encodes the Desmin protein...
encryption in less than a day using specially designed hardware. In 2002, distributed.net
Distributed.net
distributed.net is a worldwide distributed computing effort that is attempting to solve large scale problems using otherwise idle CPU or GPU time. It is officially recognized as a non-profit organization under U.S...
cracked a 64-bit key in 4 years, 9 months, and 23 days. As of October 12, 2011, distributed.net estimates that cracking a 72-bit key using current hardware will take about 45,579 days or 124.8 years. Due to currently understood limitations from fundamental physics, there is no expectation that any digital computer (or combination) will be capable of breaking 256-bit encryption via a brute-force attack. Whether or not quantum computers will be able to do so in practice is still unknown, though theoretical analysis suggests such possibilities.
As a result, there can be no exact answer to the somewhat different problem of the password strength required to resist brute force attack in practice. NIST recommends 80-bits for the most secure passwords, which can nearly be achieved with a 95-character choice (e.g., the original ASCII character set) with a 12-character random password (12 x 6.5 bits = 78). A 2010 Georgia Tech Research Institute
Georgia Tech Research Institute
The Georgia Tech Research Institute is the nonprofit applied research arm of the Georgia Institute of Technology in Atlanta, Georgia, United States...
study also recommended a 12-character random password, but as a minimum length requirement.
Common guidelines
Guidelines for choosing good passwords are designed to make passwords less easily discovered by intelligent guessing. Common guidelines include:- A minimum password length of 12 to 14 characters if permitted
- Generating passwords randomly where feasible
- Avoiding passwords based on repetition, dictionary words, letter or number sequences, usernames, relative or pet names, romantic links (current or past), or biographical information (e.g., ID numbers, ancestors' names or dates).
- Including numbers, and symbols in passwords if allowed by the system
- If the system recognizes case as significant, using capital and lower-case letters
- Avoiding using the same password for multiple sites or purposes
Some guidelines advise against writing passwords down, while others, noting the large numbers of password protected systems users must access, encourage writing down passwords as long as the written password lists are kept in a safe place, such as a wallet or safe, not attached to a monitor or in an unlocked desk drawer.
The possible character set for a password can be constrained by different web sites or by the range of keyboards on which the password must be entered.
Examples of weak passwords
As with any security measure, passwords vary in effectiveness (i.e., strength); some are weaker than others. For example, the difference in weakness between a dictionary word and a word with obfuscation (i.e., letters in the password are substituted by, say, numbers— a common approach) may cost a password cracking device a few more seconds– this adds little strength. The examples below illustrate various ways weak passwords might be constructed, all of which are based on simple patterns which result in extremely low entropy, allowing them to be tested automatically at high speeds:- Default passwordDefault passwordWhere a device needs a username and/or password to login, a default password is usually provided that allows the device to be accessed during its initial setup...
s (as supplied by the system vendor and meant to be changed at installation time): password, default, admin, guest, etc. Lists of default passwords are widely available on the internet. - Dictionary words: chameleon, RedSox, sandbags, bunnyhop!, IntenseCrabtree, etc., including words in non-English dictionaries.
- Words with numbers appended: password1, deer2000, john1234, etc., can be easily tested automatically with little lost time.
- Words with simple obfuscation: p@ssw0rd, l33th4x0r, g0ldf1sh, etc., can be tested automatically with little additional effort. For example a domain administrator password compromised in the DigiNotarDigiNotarDigiNotar was a Dutch certificate authority owned by VASCO Data Security International. On September 3, 2011, after it had become clear that a security breach had resulted in the fraudulent issuing of certificates, the Dutch government took over operational management of DigiNotar's systems...
attack was reportedly Pr0d@dm1n. - Doubled words: crabcrab, stopstop, treetree, passpass, etc.
- Common sequences from a keyboard row: qwerty, 12345, asdfgh, fred, etc.
- Numeric sequences based on well known numbers such as 911 (9-1-19-1-19-1-1 is the emergency telephone number for the North American Numbering Plan .It is one of eight N11 codes.The use of this number is for emergency circumstances only, and to use it for any other purpose can be a crime.-History:In the earliest days of telephone technology, prior to the...
, 9/11), 314159... (piPi' is a mathematical constant that is the ratio of any circle's circumference to its diameter. is approximately equal to 3.14. Many formulae in mathematics, science, and engineering involve , which makes it one of the most important mathematical constants...
), or 27182... (eE (mathematical constant)The mathematical constant ' is the unique real number such that the value of the derivative of the function at the point is equal to 1. The function so defined is called the exponential function, and its inverse is the natural logarithm, or logarithm to base...
), etc. - Identifiers: jsmith123, 1/1/1970, 555–1234, "your username", etc.
- Anything personally related to an individual: license plate number, Social Security number, current or past telephone number, student ID, address, birthday, sports team, relative's or pet's names/nicknames/birthdays/initials, etc., can easily be tested automatically after a simple investigation of person's details.
There are many other ways a password can be weak, corresponding to the strengths of various attack schemes; the core principle is that a password should have high entropy (usually taken to be equivalent to randomness) and not be readily derivable by any "clever" pattern, nor should passwords be mixed with information identifying the user. On-line services often provide a restore password function that a hacker can figure out and by doing so bypass a password. Choosing hard to guess restore password questions can further secure the password.
Password policy
A password policy is a guide to choosing satisfactory passwords. Some are controversial. They are usually intended to:- assist users in choosing strong passwords
- ensure the passwords are suited to the target population
- recommendations to users with regard to the handling of their passwords
- a requirement to change any password which has been lost or compromised, and perhaps that no password be used longer than a limited time
- some policies prescribe the pattern of characters which passwords must contain
For example, password expiration is often covered by password policies. Password expiration serves two purposes:
- if the time to crack a password is estimated to be 100 days, password expiration times fewer than 100 days may help ensure insufficient time for an attacker.
- if a password has been compromised, requiring it to be changed regularly should limit the access time for the attacker
Some argue that password expirations have become obsolete, since:
- asking users to change passwords frequently encourages simple, weak passwords.
- if one has a truly strong password, there is little point in changing it. Changing passwords which are already strong introduces risk that the new password may be less strong.
- A compromised password is likely to be used immediately by an attacker to install a backdoor, often via privilege escalationPrivilege escalationPrivilege escalation is the act of exploiting a bug, design flaw or configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user...
. Once this is accomplished, password changes won't prevent future attacker access.
Creating and handling passwords
The hardest passwords to crack, for a given length and character set, are random character strings; if long enough they resist brute force attacks (because there are many characters) and guessing attacks (due to high entropy). However, such passwords are typically the hardest to remember. The imposition of a requirement for such passwords in a password policy may encourage users to write them down, store them in PDAs or cellphones, or share them with others as a safeguard against memory failure. Some people consider each of these user resorts to increase security risks. Others suggest the absurdity of expecting users to remember distinct complex passwords for each of the dozens of accounts they access. For example, security expert Bruce Schneier recommends writing down your password:The following measures may increase acceptance of strong password requirements, if carefully used:
- a training program. Also, updated training for those who fail to follow the password policy (lost passwords, inadequate passwords, etc.).
- rewarding strong password users by reducing the rate, or eliminating altogether, the need for password changes (password expiration). The strength of user-chosen passwords can be estimated by automatic programs which inspect and evaluate proposed passwords, when setting or changing a password.
- displaying to each user the last login date and time in the hope that the user may notice unauthorized access, suggesting a compromised password.
- allowing users to reset their passwords via an automatic system, which reduces help desk call volume. However, some systems are themselves insecure; for instance, easily guessed or researched answers to password reset questions bypass the advantages of a strong password system.
- using randomly generated passwords that do not allow users to choose their own passwords, or at least offering randomly generated passwords as an option.
Memory techniques
Password policies sometimes suggest memory techniques to assist remembering passwords:- mnemonic passwords: Some users develop mnemonicMnemonicA mnemonic , or mnemonic device, is any learning technique that aids memory. To improve long term memory, mnemonic systems are used to make memorization easier. Commonly encountered mnemonics are often verbal, such as a very short poem or a special word used to help a person remember something,...
phrases and use them to generate high-entropy (more or less random) passwords which are nevertheless relatively easy for the user to remember. For instance, the first letter of each word in a memorable phrase. Silly ones are possibly more memorable. Another way to make random-appearing passwords more memorable is to use random words (see dicewareDicewareDiceware is a method for creating passphrases, passwords, and other cryptographic variables using ordinary dice as a hardware random number generator. For each word in the passphrase, five dice rolls are required. The numbers that come up in the rolls are assembled as a five digit number, e.g....
) or syllables instead of randomly-chosen letters. - after-the-fact mnemonics: After the password has been established, invent a mnemonic that fits. It does not have to be reasonable or sensible, only memorable. This allows passwords to be random.
- password patterns: Any pattern in a password makes guessing (automated or not) easier and reduces an attacker's work factor.
- In an example from the UK in October 2005, employees of the British governmentDepartments of the United Kingdom GovernmentHer Majesty's Government of the United Kingdom contains a number of Cabinet ministers who are usually called secretaries of state when they are in charge of Government departments called ministerial departments...
were advised to use passwords of the following form: consonant, vowel, consonant, consonant, vowel, consonant, number, number (for example pinray45). This pattern is called an Environ password and is case-insensitive. The pattern of alternating vowel and consonant characters was intended to make passwords more likely to be pronounceable and thus more memorable. Unfortunately, such patterns severely reduce the password's information entropyInformation entropyIn information theory, entropy is a measure of the uncertainty associated with a random variable. In this context, the term usually refers to the Shannon entropy, which quantifies the expected value of the information contained in a message, usually in units such as bits...
, making brute forceBrute force attackIn cryptography, a brute-force attack, or exhaustive key search, is a strategy that can, in theory, be used against any encrypted data. Such an attack might be utilized when it is not possible to take advantage of other weaknesses in an encryption system that would make the task easier...
password attacks considerably more efficient.
- In an example from the UK in October 2005, employees of the British government
Protecting passwords
Computer users are generally advised to "never write down a password anywhere, no matter what" and "never use the same password for more than one account." However, an ordinary computer user may have dozens of password-protected accounts. Users with multiple accounts needing passwords often give up and use the same password for every account. When varied password complexity requirements prevent use of the same (memorable) scheme for producing high-strength passwords, overly simplified passwords will often be created to satisfy irritating and conflicting password requirements.A Microsoft
Microsoft
Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions...
expert was quoted as saying at a 2005 security conference: "I claim that password policy should say you should write down your password. I have 68 different passwords. If I am not allowed to write any of them down, guess what I am going to do? I am going to use the same password on every one of them."
If passwords are written down, they should never be kept in obvious places such as address books, Rolodex
Rolodex
A Rolodex is a rotating file device used to store business contact information currently manufactured by Newell Rubbermaid. The Rolodex holds specially shaped index cards; the user writes the contact information for one person or company on each card...
files, under drawers or keyboards, or behind pictures. Perhaps the worst, but all too common, location is a Post-It note on the computer monitor. Better locations are a safe deposit box
Safe deposit box
A safe deposit box or wrongly referred to as a safety deposit box is an individually-secured container, usually held within a larger safe or bank vault. Safe deposit boxes are generally located in banks, post offices or other institutions...
or a locked file approved for information of sensitivity comparable to that protected by the password. Most locks on office file cabinets are far from adequate. Software is available for popular hand-held computers that can store passwords for numerous accounts in encrypted form. Another approach is to encrypt
Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
by hand on paper and remember the encryption method and key. And another approach is to use a single password or slightly-varying passwords for low-security accounts and select distinctly separate strong passwords for a smaller number of high-value applications such as for online banking
Online banking
Online banking allows customers to conduct financial transactions on a secure website operated by their retail or virtual bank, credit union or building society.-Features:...
.
Password managers
A reasonable compromise for using large numbers of passwords is to record them in a password manager, which include stand-alone applications, web browser extensions, or a manager built into the operating system. A password manager allows the user to use hundreds of different passwords, and only have to remember a single password, the one which opens the encrypted password database. Needless to say, this single password should be strong and well-protected (not recorded anywhere). Most password managers can automatically create strong passwords using a cryptographically secure random password generatorRandom password generator
A random password generator is software program or hardware device that takes input from a random or pseudo-random number generator and automatically generates a password...
, as well as calculating the entropy of the generated password. A good password manager will provide resistance against attacks such as key logging, clipboard logging and various other memory spying techniques.
Password strength advisers
Several web sites, and some standalone programs meant to be run without a network connection on a local machine, offer automated tests of password strength adequacy. They are problematic. Any network based checking necessarily involves submitting one's password to a purpose declared system somewhere. Doing so eases an attacker's problem very considerably; the relevant network traffic is identifiable as passwords saving much sifting effort, authentication of network connection problems permit authentication problems (e.g., site spoofing) which are lessened for equivalent programs running on local computers.Even when run on local machines, without network involvement, there are potential problems. Implementational problems (e.g., errors in programming or algorithm choice) are always possible, of course, and many of these exhibit no discernible clues for a user or administrator. And, such programs are limited to estimates of brute force attack vulnerability regardless of where they are run. Passwords which are vulnerable to guessing attacks cannot be checked automatically, as not everyone's pet is named Rover or Fluffy, nor do all children or relatives have common names, readily found in lists.
As a result, use of such checking facilities cannot be recommended. The tests they can apply are easy for users to perform, if they understand some basic principles. And the increased attack opportunities should be avoided as well, on the general principle of not making an attacker's task easier.
See also
- Keystroke loggingKeystroke loggingKeystroke logging is the action of tracking the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored...
- PhishingPhishingPhishing is a way of attempting to acquire information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT...
- Vulnerability (computing)Vulnerability (computing)In computer security, a vulnerability is a weakness which allows an attacker to reduce a system's information assurance.Vulnerability is the intersection of three elements: a system susceptibility or flaw, attacker access to the flaw, and attacker capability to exploit the flaw...
External links
- Choosing Good Passwords — A User Guide.
- Password Policy Guidelines.
- Bruce Schneier (December 14, 2006). MySpace Passwords Aren't So Dumb.
- How to Write Better Passwords
- RFC 4086: Randomness Requirements for Security
- Frequently used passwords to avoid
- Steve Gibson (June 2011). GRC's | Password Haystacks: How well Hidden is Your Needle?
- Microsoft's Password Strength Checker

