SAFER
Encyclopedia
In cryptography
, SAFER (Secure And Fast Encryption Routine) is the name of a family of block cipher
s designed primarily by James Massey
(one of the designers of IDEA) on behalf of Cylink Corporation. The early SAFER K and SAFER SK designs share the same encryption
function, but differ in the number of rounds and the key schedule
. More recent versions — SAFER+ and SAFER++ — were submitted as candidates to the AES process and the NESSIE
project respectively. All of the algorithms in the SAFER family are unpatented and available for unrestricted use.
 The first SAFER cipher was SAFER K-64, published by Massey in 1993, with a 64-bit block size
The first SAFER cipher was SAFER K-64, published by Massey in 1993, with a 64-bit block size
. The "K-64" denotes a key size
of 64 bits. There was some demand for a version with a larger 128-bit key
, and the following year Massey published such a variant incorporating new key schedule designed by the Singapore
Ministry for Home affairs: SAFER K-128. However, both Lars Knudsen
and Sean Murphy
found minor weaknesses in this version, prompting a redesign of the key schedule to one suggested by Knudsen; these variants were named SAFER SK-64 and SAFER SK-128 respectively — the "SK" standing for "Strengthened Key schedule", though the RSA
FAQ reports that, "one joke has it that SK really stands for 'Stop Knudsen', a wise precaution in the design of any block cipher". Another variant with a reduced key size was published, SAFER SK-40, to comply with 40-bit export restrictions.
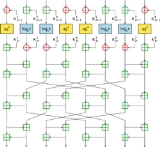
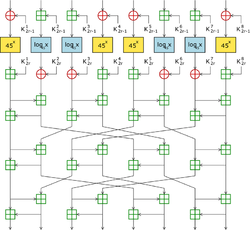
All of these ciphers use the same round function consisting of four stages, as shown in the diagram: a key-mixing stage, a substitution layer, another key-mixing stage, and finally a diffusion layer. In the first key-mixing stage, the plaintext block is divided into eight 8-bit segments, and subkeys are added using either addition modulo 256 (denoted by a "+" in a square) or XOR (denoted by a "+" in a circle). The substitution layer consists of two S-boxes, each the inverse of each other, derived from discrete exponentiation
(45x) and logarithm
(log45x) functions. After a second key-mixing stage there is the diffusion layer: a novel cryptographic component termed a pseudo-Hadamard transform
(PHT). (The PHT was also later used in the Twofish
cipher.)
Cryptography
Cryptography is the practice and study of techniques for secure communication in the presence of third parties...
, SAFER (Secure And Fast Encryption Routine) is the name of a family of block cipher
Block cipher
In cryptography, a block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks, with an unvarying transformation. A block cipher encryption algorithm might take a 128-bit block of plaintext as input, and output a corresponding 128-bit block of ciphertext...
s designed primarily by James Massey
James Massey
James Lee Massey is an information theorist andcryptographer, Professor Emeritus of Digital Technology at ETH Zurich. His notable work...
(one of the designers of IDEA) on behalf of Cylink Corporation. The early SAFER K and SAFER SK designs share the same encryption
Encryption
In cryptography, encryption is the process of transforming information using an algorithm to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. The result of the process is encrypted information...
function, but differ in the number of rounds and the key schedule
Key schedule
[[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES [[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES [[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES ("[[Image:DES-key-schedule.png|thumbnail|220px|The key schedule of DES ("...
. More recent versions — SAFER+ and SAFER++ — were submitted as candidates to the AES process and the NESSIE
NESSIE
NESSIE was a European research project funded from 2000–2003 to identify secure cryptographic primitives. The project was comparable to the NIST AES process and the Japanese Government-sponsored CRYPTREC project, but with notable differences from both...
project respectively. All of the algorithms in the SAFER family are unpatented and available for unrestricted use.
SAFER K and SAFER SK

Block size (cryptography)
In modern cryptography, symmetric key ciphers are generally divided into stream ciphers and block ciphers. Block ciphers operate on a fixed length string of bits. The length of this bit string is the block size...
. The "K-64" denotes a key size
Key size
In cryptography, key size or key length is the size measured in bits of the key used in a cryptographic algorithm . An algorithm's key length is distinct from its cryptographic security, which is a logarithmic measure of the fastest known computational attack on the algorithm, also measured in bits...
of 64 bits. There was some demand for a version with a larger 128-bit key
Key (cryptography)
In cryptography, a key is a piece of information that determines the functional output of a cryptographic algorithm or cipher. Without a key, the algorithm would produce no useful result. In encryption, a key specifies the particular transformation of plaintext into ciphertext, or vice versa...
, and the following year Massey published such a variant incorporating new key schedule designed by the Singapore
Singapore
Singapore , officially the Republic of Singapore, is a Southeast Asian city-state off the southern tip of the Malay Peninsula, north of the equator. An island country made up of 63 islands, it is separated from Malaysia by the Straits of Johor to its north and from Indonesia's Riau Islands by the...
Ministry for Home affairs: SAFER K-128. However, both Lars Knudsen
Lars Knudsen
Lars Ramkilde Knudsen is a Danish researcher in cryptography, particularly interested in the design and analysis of block ciphers, hash functions and message authentication codes .-Academic:...
and Sean Murphy
Sean Murphy (cryptographer)
Sean Murphy is a cryptographer, currently a professor at Royal Holloway, University of London. He worked on the NESSIE and ECRYPT projects. His notable research includes the cryptanalysis of FEAL and the Advanced Encryption Standard, and the use of stochastic and statistical techniques in...
found minor weaknesses in this version, prompting a redesign of the key schedule to one suggested by Knudsen; these variants were named SAFER SK-64 and SAFER SK-128 respectively — the "SK" standing for "Strengthened Key schedule", though the RSA
RSA Security
RSA, the security division of EMC Corporation, is headquartered in Bedford, Massachusetts, United States, and maintains offices in Australia, Ireland, Israel, the United Kingdom, Singapore, India, China, Hong Kong and Japan....
FAQ reports that, "one joke has it that SK really stands for 'Stop Knudsen', a wise precaution in the design of any block cipher". Another variant with a reduced key size was published, SAFER SK-40, to comply with 40-bit export restrictions.
All of these ciphers use the same round function consisting of four stages, as shown in the diagram: a key-mixing stage, a substitution layer, another key-mixing stage, and finally a diffusion layer. In the first key-mixing stage, the plaintext block is divided into eight 8-bit segments, and subkeys are added using either addition modulo 256 (denoted by a "+" in a square) or XOR (denoted by a "+" in a circle). The substitution layer consists of two S-boxes, each the inverse of each other, derived from discrete exponentiation
Exponentiation
Exponentiation is a mathematical operation, written as an, involving two numbers, the base a and the exponent n...
(45x) and logarithm
Logarithm
The logarithm of a number is the exponent by which another fixed value, the base, has to be raised to produce that number. For example, the logarithm of 1000 to base 10 is 3, because 1000 is 10 to the power 3: More generally, if x = by, then y is the logarithm of x to base b, and is written...
(log45x) functions. After a second key-mixing stage there is the diffusion layer: a novel cryptographic component termed a pseudo-Hadamard transform
Pseudo-Hadamard transform
The pseudo-Hadamard transform is a reversible transformation of a bit string that provides cryptographic diffusion. See Hadamard transform.The bit string must be of even length, so it can be split into two bit strings a and b of equal lengths, each of n bits...
(PHT). (The PHT was also later used in the Twofish
Twofish
In cryptography, Twofish is a symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists of the Advanced Encryption Standard contest, but was not selected for standardisation...
cipher.)
SAFER+ and SAFER++
There are two more-recent members of the SAFER family that have made changes to the main encryption routine, designed by the Armenian cryptographers Gurgen Khachatrian (American University of Armenia) and Melsik Kuregian in conjunction with Massey.- SAFER+ (Massey et al., 1998) was submitted as a candidate for the Advanced Encryption Standard and has a block size of 128 bits. The cipher was not selected as a finalist. BluetoothBluetoothBluetooth is a proprietary open wireless technology standard for exchanging data over short distances from fixed and mobile devices, creating personal area networks with high levels of security...
uses custom algorithms based on SAFER+ for key derivation (called E21 and E22) and authentication as message authentication codeMessage authentication codeIn cryptography, a message authentication code is a short piece of information used to authenticate a message.A MAC algorithm, sometimes called a keyed hash function, accepts as input a secret key and an arbitrary-length message to be authenticated, and outputs a MAC...
s (called E1). Encryption in Bluetooth does not use SAFER+. - SAFER++ (Massey et al., 2000) was submitted to the NESSIENESSIENESSIE was a European research project funded from 2000–2003 to identify secure cryptographic primitives. The project was comparable to the NIST AES process and the Japanese Government-sponsored CRYPTREC project, but with notable differences from both...
project in two versions, one with 64 bits, and the other with 128 bits.

