
X Window core protocol
Encyclopedia

X Window System
The X window system is a computer software system and network protocol that provides a basis for graphical user interfaces and rich input device capability for networked computers...
, which is a networked
Computer network
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information....
windowing system
Windowing system
A windowing system is a component of a graphical user interface , and more specifically of a desktop environment, which supports the implementation of window managers, and provides basic support for graphics hardware, pointing devices such as mice, and keyboards...
for bitmap
Bitmap
In computer graphics, a bitmap or pixmap is a type of memory organization or image file format used to store digital images. The term bitmap comes from the computer programming terminology, meaning just a map of bits, a spatially mapped array of bits. Now, along with pixmap, it commonly refers to...
displays used to build graphical user interface
Graphical user interface
In computing, a graphical user interface is a type of user interface that allows users to interact with electronic devices with images rather than text commands. GUIs can be used in computers, hand-held devices such as MP3 players, portable media players or gaming devices, household appliances and...
s on Unix
Unix
Unix is a multitasking, multi-user computer operating system originally developed in 1969 by a group of AT&T employees at Bell Labs, including Ken Thompson, Dennis Ritchie, Brian Kernighan, Douglas McIlroy, and Joe Ossanna...
, Unix-like
Unix-like
A Unix-like operating system is one that behaves in a manner similar to a Unix system, while not necessarily conforming to or being certified to any version of the Single UNIX Specification....
, and other operating system
Operating system
An operating system is a set of programs that manage computer hardware resources and provide common services for application software. The operating system is the most important type of system software in a computer system...
s. The X Window System is based on a client–server model: a single server
Server (computing)
In the context of client-server architecture, a server is a computer program running to serve the requests of other programs, the "clients". Thus, the "server" performs some computational task on behalf of "clients"...
controls the input/output
Input/output
In computing, input/output, or I/O, refers to the communication between an information processing system , and the outside world, possibly a human, or another information processing system. Inputs are the signals or data received by the system, and outputs are the signals or data sent from it...
hardware
Hardware
Hardware is a general term for equipment such as keys, locks, hinges, latches, handles, wire, chains, plumbing supplies, tools, utensils, cutlery and machine parts. Household hardware is typically sold in hardware stores....
, such as the screen, the keyboard
Computer keyboard
In computing, a keyboard is a typewriter-style keyboard, which uses an arrangement of buttons or keys, to act as mechanical levers or electronic switches...
, and the mouse; all application program
Computer program
A computer program is a sequence of instructions written to perform a specified task with a computer. A computer requires programs to function, typically executing the program's instructions in a central processor. The program has an executable form that the computer can use directly to execute...
s act as client
Client (computing)
A client is an application or system that accesses a service made available by a server. The server is often on another computer system, in which case the client accesses the service by way of a network....
s, interacting with the user
User (computing)
A user is an agent, either a human agent or software agent, who uses a computer or network service. A user often has a user account and is identified by a username , screen name , nickname , or handle, which is derived from the identical Citizen's Band radio term.Users are...
and with the other clients via the server. This interaction is regulated by the X Window System core protocol. Other protocols related to the X Window System exist, both built at the top of the X Window System core protocol or as separate protocols.
In the X Window System core protocol, only four kinds of packets are sent, asynchronously
Asynchrony
Asynchrony, in the general meaning, is the state of not being synchronized.* Asynchronous learning* Collaborative editing systemsIn specific terms of digital logic and physical layer of communication, an asynchronous process does not require a clock signal, in contrast with synchronous and...
, over the network: requests, replies, events, and errors. Requests are sent by a client to the server to ask it to perform some operation (for example, create a new window) and to send back data it holds. Replies are sent by the server to provide such data. Events are sent by the server to notify clients of user activity or other occurrences they are interested in. Errors are packet sent by the server to notify a client of errors occurred during processing of its requests. Requests may generate replies, events, and errors; other than this, the protocol does not mandate over a specific order in which packets are sent over the network. Some extensions to the core protocol exist, each one having its own requests, replies, events, and errors.
X originated at MIT
Massachusetts Institute of Technology
The Massachusetts Institute of Technology is a private research university located in Cambridge, Massachusetts. MIT has five schools and one college, containing a total of 32 academic departments, with a strong emphasis on scientific and technological education and research.Founded in 1861 in...
in 1984 (its release X11 appeared in September 1987). Its designers Bob Scheifler
Bob Scheifler
Robert William Scheifler is an American computer scientist. He is most notable for leading the development of the X Window System from the project's inception in 1984 until the closure of the MIT X Consortium in 1996...
and Jim Gettys
Jim Gettys
Jim Gettys is an American computer programmer at Alcatel-Lucent Bell Labs, USA. Until January 2009, he was the Vice President of Software at the One Laptop per Child project, working on the software for the OLPC XO-1. He is one of the original developers of the X Window System at MIT and worked on...
set as an early principle that its core protocol was to "create mechanism, not policy". As a result, the core protocol does not specify the interaction between clients and between a client and the user. These interactions are the subject of separate specifications, such as the ICCCM and the freedesktop.org
Freedesktop.org
freedesktop.org is a project to work on interoperability and shared base technology for free software desktop environments for the X Window System on Linux and other Unix-like operating systems. It was founded by Havoc Pennington from Red Hat in March 2000.The organisation focuses on the user....
specifications, and are typically enforced automatically by using a given widget set.
Overview
Communication between server and clients is done by exchanging packets over a channelChannel (communications)
In telecommunications and computer networking, a communication channel, or channel, refers either to a physical transmission medium such as a wire, or to a logical connection over a multiplexed medium such as a radio channel...
. The connection is established by the client (how the client is started is not specified in the protocol). The client also sends the first packet, containing the byte order to be used and information about the version of the protocol and the kind of authentication the client expects the server to use. The server answers by sending back a packet stating the acceptance or refusal of the connection, or with a request for a further authentication
Authentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
. If the connection is accepted, the acceptance packet contains data for the client to use in the subsequent interaction with the server.
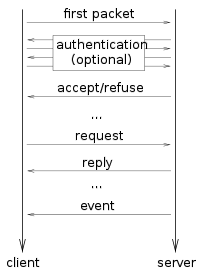
- Request: The client requests information from the server or requests it to perform an action.
- Reply: The server responds to a request. Not all requests generate replies.
- Event: The server informs the client of an event, such as keyboard or mouse input, a window being moved, resized or exposed, etc.
- Error: The server sends an error packet if a request is invalid. Since requests are queued, error packets generated by a request may not be sent immediately.
Request and reply packets have varying length, while event and error packets have a fixed length of 32 byte
Byte
The byte is a unit of digital information in computing and telecommunications that most commonly consists of eight bits. Historically, a byte was the number of bits used to encode a single character of text in a computer and for this reason it is the basic addressable element in many computer...
s.
Request packets are numbered sequentially by the server as soon as it receives them: the first request from a client is numbered 1, the second 2, etc. The least significant 16 bits of the sequential number of a request is included in the reply and error packets generated by the request, if any. They are also included in event packets to indicate the sequential number of the request that the server is currently processing or has just finished processing.
Windows
What is usually called a window in most graphical user interfaceGraphical user interface
In computing, a graphical user interface is a type of user interface that allows users to interact with electronic devices with images rather than text commands. GUIs can be used in computers, hand-held devices such as MP3 players, portable media players or gaming devices, household appliances and...
s is called a top-level window in the X Window System. The term window is also used to denote windows that lie within another window, that is, the subwindows of a parent window. Graphical elements such as button
Button (computing)
In computing, a button is a user interface element that provides the user a simple way to trigger an event, like searching for a query at a search engine, or to interact with dialog boxes, like confirming an action.-Description:A typical button is a rectangle or rounded rectangle, wider than it is...
s, menu
Menu (computing)
In computing and telecommunications, a menu is a list of commands presented to an operator by a computer or communications system. A menu is used in contrast to a command-line interface, where instructions to the computer are given in the form of commands .Choices given from a menu may be selected...
s, icon
Icon (computing)
A computer icon is a pictogram displayed on a computer screen and used to navigate a computer system or mobile device. The icon itself is a small picture or symbol serving as a quick, intuitive representation of a software tool, function or a data file accessible on the system. It functions as an...
s, etc. can be realized using subwindows.
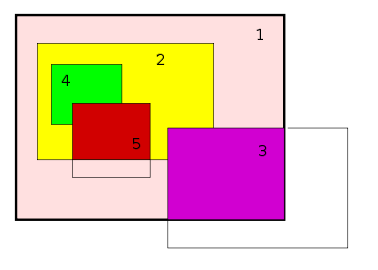
Tree (graph theory)
In mathematics, more specifically graph theory, a tree is an undirected graph in which any two vertices are connected by exactly one simple path. In other words, any connected graph without cycles is a tree...
(a hierarchy). The root of this tree is the root window
Root window
In the X Window System, every window is contained within another window, called its parent. This makes the windows form a hierarchy. The root window is the root of this hierarchy...
, which is a special window created automatically by the server at startup. All other windows are directly or indirectly subwindows of the root window. The top-level windows are the direct subwindows of the root window. Visibly, the root window is as large as the virtual desktop, and lies behind all other windows.
The content of a window is not always guaranteed to be preserved over time. In particular, the window content may be destroyed when the window is moved, resized, covered by other windows, and in general made totally or partly non-visible. In particular, content is lost if the X server is not maintaining a backing store of the window content. The client can request backing store for a window to be maintained, but there is no obligation for the server to do so. Therefore, clients cannot assume that backing store is maintained. If a visible part of a window has an unspecified content, an event is sent to notify the client that the window content has to be drawn again.
Every window has an associated set of attributes, such as the geometry of the window (size and position), the background image, whether backing store has been requested for it, etc. The protocol includes requests for a client to inspect and change the attributes of a window.
Windows can be
InputOutput or InputOnly. InputOutput windows can be shown on the screen and are used for drawing. InputOnly windows are never shown on the screen and are used only to receive input.The decorative frame and title bar
Title bar
In computing, the title bar consists of that part of a window where the title of the window appears. Most graphical operating systems and window managers position the title bar at the top of the application window as a horizontal bar....
(possibly including buttons) that is usually seen around windows are created by the window manager
Window manager
A window manager is system software that controls the placement and appearance of windows within a windowing system in a graphical user interface. Most window managers are designed to help provide a desktop environment...
, not by the client that creates the window. The window manager also handles input related to these elements, such as resizing the window when the user clicks and drags the window frame. Clients usually operate on the window they created disregarding the changes operated by the window manager. A change it has to take into account is that re-parenting window manager
Re-parenting window manager
A stacking window manager is a window manager that draws all windows in a specific order, allowing them to overlap, using a technique called painter's algorithm...
s, which almost all modern window managers are, change the parent of top-level windows to a window that is not the root. From the point of view of the core protocol, the window manager is a client, not different from the other applications.
Data about a window can be obtained by running the
xwininfo program. Passing it the -tree command-line argument, this program shows the tree of subwindows of a window, along with their identifiers and geometry data.Pixmaps and drawables
A pixmap is a region of memory that can be used for drawing. Unlike windows, pixmaps are not automatically shown on the screen. However, the content of a pixmap (or a part of it) can be transferred to a window and vice versa. This allows for techniques such as double bufferingDouble buffering
In computer science, multiple buffering is the use of more than one buffer to hold a block of data, so that a "reader" will see a complete version of the data, rather than a partially-updated version of the data being created by a "writer"...
. Most of the graphical operations that can be done on windows can also be done on pixmaps.
Windows and pixmaps are collectively named drawables, and their content data resides on the server. A client can however request the content of a drawable to be transferred from the server to the client or vice versa.
Graphic contexts and fonts
The client can request a number of graphic operations, such as clearing an area, copying an area into another, drawing points, lines, rectangles, and text. Beside clearing, all operations are possible on all drawables, both windows and pixmaps.Most requests for graphic operations include a graphic context, which is a structure that contains the parameters of the graphic operations. A graphic context includes the foreground color, the background color, the font of text, and other graphic parameters. When requesting a graphic operation, the client includes a graphic context. Not all parameters of the graphic context affect the operation: for example, the font does not affect drawing a line.
The core protocol specifies the use of server-side fonts. Such fonts are stored as file
Computer file
A computer file is a block of arbitrary information, or resource for storing information, which is available to a computer program and is usually based on some kind of durable storage. A file is durable in the sense that it remains available for programs to use after the current program has finished...
s, and the server accesses them either directly via the local filesystem or via the network from another program called font server. Clients can request the list of fonts available to the server and can request a font to be loaded (if not already) or unloaded (if not used by other clients) by the server. A client can request general information about a font (for example, the font ascent) and the space a specific string takes when drawn with a specific font.
X logical font description
X logical font description is a font standard used by the X Window System. It is intended to support:* unique, descriptive font names that support simple pattern matching* multiple font vendors, arbitrary character sets, and encodings...
conventions specify how fonts should be named according to their attributes. These conventions also specify the values of optional properties that can be attached to fonts.
The
xlsfonts program prints the list of fonts stored in the server. The xfontsel program shows the glyphs of fonts, and allow the user to select the name of a font for pasting it in another window.The use of server-side fonts is currently considered deprecated in favour of client-side fonts. Such fonts are rendered by the client, not by the server, with the support of the Xft
Xft
Xft, the X FreeType interface library, is a free computer program library written by Keith Packard. As of version 2.1, it is licensed under a quasi-BSD license....
or cairo
Cairo (graphics)
cairo is a software library used to provide a vector graphics-based, device-independent API for software developers. It is designed to provide primitives for 2-dimensional drawing across a number of different backends...
libraries and the XRender
XRender
The X Rendering Extension is an X Window System extension to implement Porter-Duff image compositing in the X server, to allow efficient display of transparent images.- History :...
extension. No specification on client-side fonts is given in the core protocol.
Resources and identifiers
All data about windows, pixmaps, fonts, etc. are stored in the server. The client knows identifierIdentifier
An identifier is a name that identifies either a unique object or a unique class of objects, where the "object" or class may be an idea, physical [countable] object , or physical [noncountable] substance...
s of these objects—integers it uses as names for them when interacting with the server. For example, if a client wishes a window to be created, it requests the server to create a window with a given identifier. The identifier can be later used by the client to request, for example, a string to be drawn in the window. The following objects reside in the server and are known by the client via a numerical identifier:
-
Window -
Pixmap -
Font -
Colormap(a table of colors, described below) -
Graphic context
These objects are called resources. When a client requests the creation of one such resource, it also specifies an identifier for it. For example, for creating a new window, the client specifies both the attributes of the window (parent, width, height, etc.) and the identifier to associate with the window.
Identifiers are 32-bit integer
Integer
The integers are formed by the natural numbers together with the negatives of the non-zero natural numbers .They are known as Positive and Negative Integers respectively...
s with their three most significant bits equal to zero. Every client has its own set of identifiers it can use for creating new resources. This set is specified by the server as two integers included in the acceptance packet (the packet it sends to the client to inform it that the connection is accepted). Clients choose identifiers that are in this set in such a way they do not clash: two objects among windows, pixmaps, fonts, colormaps, and graphic contexts cannot have the same identifier.
Once a resource has been created, its identifier is used by the client to request operations about it to the server. Some operations affect the given resource (for example, requests to move windows); others ask for resource data stored from the server (for example, requests for the attributes of windows).
Identifiers are unique to the server, not only to the client; for example, no two windows have the same identifier, even if created by two different clients. A client can access any object given its identifier. In particular, it can also access resources created by any other client, even if their identifiers are outside the set of identifiers it can create.
As a result, two clients connected to the same server can use the same identifier to refer to the same resource. For example, if a client creates a window of identifier
0x1e00021 and passes this number 0x1e00021 to another application (via any available means, for example by storing this number in a file that is also accessible to the other application), this other application is able to operate on the very same window. This possibility is for example exploited by the X Window version of Ghostview: this program creates a subwindow, storing its identifier in an environment variableEnvironment variable
Environment variables are a set of dynamic named values that can affect the way running processes will behave on a computer.They can be said in some sense to create the operating environment in which a process runs...
, and calls Ghostscript
Ghostscript
Ghostscript is a suite of software based on an interpreter for Adobe Systems' PostScript and Portable Document Format page description languages.- Features :...
; this program draws the content of the PostScript
PostScript
PostScript is a dynamically typed concatenative programming language created by John Warnock and Charles Geschke in 1982. It is best known for its use as a page description language in the electronic and desktop publishing areas. Adobe PostScript 3 is also the worldwide printing and imaging...
file to show in this window.
Resources are normally destroyed when the client that created them closes the connection with the server. However, before closing connection, a client can request the server not to destroy them.
Events
Events are packets sent by the server to a client to communicate that something the client may be interested in has happened. For example, an event is sent when the user presses a key or clicks a mouse button. Events are not only used for input: for example, events are sent to indicate the creation of new subwindows of a given window.Every event is relative to a window. For example, if the user clicks when the pointer is in a window, the event will be relative to that window. The event packet contains the identifier of that window.
A client can request the server to send an event to another client; this is used for communication between clients. Such an event is for example generated when a client requests the text that is currently selected: this event is sent to the client that is currently handling the window that holds the selection.
The
Expose event is sent when an area of a window of destroyed content is made visible. The content of a window may be destroyed in some conditions, for example, if the window is covered and the server is not maintaining a backing store. The server generates an Expose event to notify the client that a part of the window has to be drawn.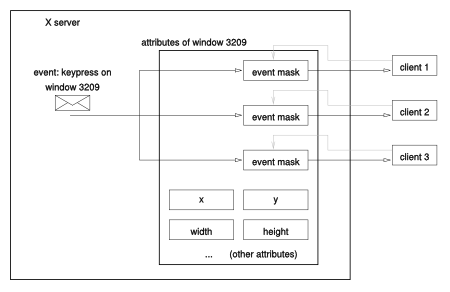
Clients specify which kinds of events they want to be sent by setting an attribute of a window. For example, in order to redraw a window when its content has been destroyed, a client must receive the
Expose events, which inform it that the window needs to be drawn again. The client will however be sent Expose events only if the client has previously stated its interest in these events, which is done by appropriately setting the event maskMask (computing)
In computer science, a mask is data that is used for bitwise operations.Using a mask, multiple bits in a byte, nibble, word can be set either on, off or inverted from on to off in a single bitwise operation.-Masking bits to 1:...
attribute of the window.
Different clients can request events on the same window. They can even set different event masks on the same window. For example, a client may request only keyboard events on a window while another client requests only mouse events on the same window. This is possible because the server, for each window, maintains a separate event mask for each client. However, there are some kinds of events that can only be selected by one client at time for each window. In particular, these events report mouse button clicks and some changes related to window management.
The
xev program shows the events relative to a window. In particular, xev -id WID requests all possible events relative to the window of identifier WID and prints them.Example
The following is a possible example of interaction between a server and a program that creates a window with a black box in it and exits on a keypress. In this example, the server does not send any reply because the client requests do not generate replies. These requests could generate errors.- The client opens the connection with the server and sends the initial packet specifying the byte order it is using.
- The server accepts the connection (no authorization is involved in this example) by sending an appropriate packet, which contains other information such as the identifier of the root window (e.g.,
0x0000002b) and which identifiers the client can create. - The client requests the creation of a default graphic context with identifier
0x00200000(this request, like the other requests of this example, does not generate replies from the server) - The client requests the server to create a top-level window (that is, it specifies the parent to be the root window
0x0000002b) with identifier0x00200001, size 200x200, position (10,10), etc. - The client requests a change in the attributes of the window
0x00200001, specifying it is interested in receivingExposeandKeyPressevents. - The client requests the window
0x00200001to be mapped (shown on the screen) - When the window is made visible and its content has to be drawn, the server sends the client an
Exposeevent - In response to this event, the client requests a box to be drawn by sending a
PolyFillRectanglerequest with window0x00200001and graphic context0x00200000
If the window is covered by another window and uncovered again, assuming that backing store is not maintained:
- The server sends another
Exposeevent to tell the client that the window has to be drawn again - The client redraws the window by sending a
PolyFillRectanglerequest
If a key is pressed:
- The server sends a
KeyPressevent to the client to notify it that the user has pressed a key - The client reacts appropriately (in this case, it terminates)
Colors
At the protocol level, a color is represented by a 32-bit unsigned integer, called a pixelvalue. The following elements affect the representation of colors:- the color depthColor depthIn computer graphics, color depth or bit depth is the number of bits used to represent the color of a single pixel in a bitmapped image or video frame buffer. This concept is also known as bits per pixel , particularly when specified along with the number of bits used...
- the colormap, which is a table containing red, green, and blue intensity values
- the visual type, which specifies how the table is used to represent colors
In the easiest case, the colormap is a table containing a RGB triple in each row. A pixelvalue
x represents the color contained in the x-th row of the table. If the client can change the entries in the colormap, this representation is identified by the PseudoColor visual class. The visual class StaticColor is similar, but the client cannot change the entries in the colormap.There are a total of six possible visual classes, each one identifying a different way for representing an RGB triple with a pixelvalue.
PseudoColor and StaticColor are two. Another two are GrayScale and StaticGray, which differ in that they only display shades of grey.The two remaining visual classes differ from the ones above because they break pixelvalues in three parts and use three separate tables for the red, green, and blue intensity. According to this color representation, a pixelvalue is converted into an RGB triple as follows:
- the pixelvalue is seen as a sequence of bitBitA bit is the basic unit of information in computing and telecommunications; it is the amount of information stored by a digital device or other physical system that exists in one of two possible distinct states...
s - this sequence is broken in three parts
- each of these three chunks of bits is seen as an integer and used as an index to find a value in each of three separate tables
This mechanism requires the colormap to be composed of three separate tables, one for each primary color
Primary color
Primary colors are sets of colors that can be combined to make a useful range of colors. For human applications, three primary colors are usually used, since human color vision is trichromatic....
. The result of the conversion is still a triple of intensity values. The visual classes using this representation are the
DirectColor and TrueColor ones, differing on whether the client can change colormaps or not.These six mechanisms for representing colors with pixelvalues all require some additional parameters to work. These parameters are collected into a visual type, which contains a visual class and other parameters of the representation of colors. Each server has a fixed set of visualtypes, each one associated with a numerical identifier. These identifiers are 32-bit unsigned integers, but are not necessarily different from identifiers of resources or atoms.
When the connection from a client is accepted, the acceptance packet sent by the server contains a sequence of blocks, each one containing information about a single screen. For each screen, the relative block contains a list of other blocks, each one relative to a specific color depth that is supported by the screen. For each supported depth, this list contains a list of visualtypes. As a result, each screen is associated a number of possible depths, and each depth of each screen is associated a number of possible visual types. A given visual type can be used for more screens and for different depths.
For each visual type, the acceptance packet contains both its identifier and the actual parameters it contains (visual class, etc.) The client stores this information, as it cannot request it afterwards. Moreover, clients cannot change or create new visual types. Requests for creation of a new window include the depth and the identifier of the visual type to use for representing colors of this window.
Colormaps are used regardless of whether the hardware controlling the screen (e.g., a graphic card) uses a palette
Palette (computing)
In computer graphics, a palette is either a given, finite set of colors for the management of digital images , or a small on-screen graphical element for choosing from a limited set of choices, not necessarily colors .Depending on the context In computer graphics, a palette is either a given,...
, which is a table that is also used for representing colors. Servers use colormaps even if the hardware is not using a palette. Whenever the hardware uses palettes, only a limited number of colormaps can be installed. In particular, a colormap is installed when the hardware shows colors according to it. A client can request the server to install a colormap. However, this may require the uninstalling of another colormap: the effect is that windows using the uninstalled colormap are not shown with the correct color, an effect dubbed color flashing or technicolor. This problem can be solved using standard colormaps, which are colormaps with a predictable association between pixelvalues and colors. Thanks to this property, standard colormaps can be used by different applications.
The creation of colormaps is regulated by the ICCCM convention. Standard colormaps are regulated by the ICCCM and by the Xlib
Xlib
Xlib is an X Window System protocol client library written in the C programming language. It contains functions for interacting with an X server. These functions allow programmers to write programs without knowing the details of the protocol...
specification.
A part of the X colour system is the X Color Management System (xcms). This system was introduced with X11R6 Release 5 in 1991. This system consists of several additional features in xlib, found in the Xcms* series of functions. This system defines device independent color schemes which can be converted into device dependent RGB systems. The system consists of the xlib Xcms* functions and as well the X Device Color Characterization Convention (XDCCC) which describes how to convert the various device independent colour systems into device dependent RGB colour systems. This system supports the CIEXYZ, xyY, CIELUV and CIELAB and as well the TekHVC colour systems.
http://insar.stanford.edu/~lharcke/programming/Xcms/, http://tronche.com/gui/x/xlib/color/
Atoms
Atoms are 32-bit integers representing strings. The protocol designers introduced atoms because they represent strings in a short and fixed size: while a string may be arbitrarily long, an atom is always a 32-bit integer. Atom brevity was exploited by mandating their use in the kinds of packets that are likely to be sent many times with the same strings; this results in a more efficient use of the network. The fixed size of atoms was exploited by specifying a fixed size for events, namely 32 bytes: fixed-size packets can contain atoms, while they cannot contain long strings.Precisely, atoms are identifiers of strings stored in the server. They are similar to the identifiers of resources (Windows, Pixmaps, etc.) but differ from them in two ways. First, the identifiers of atoms are chosen by the server, not by the client. In other words, when a client requests the creation of a new atom, it only sends the server the string to be stored, not its identifier; this identifier is chosen by the server and sent back as a reply to the client. The second important difference between resources and atoms is that atoms are not associated with clients. Once created, an atom survives until the server quits or resets (this is not the default behavior of resources).
Atoms are identifiers and are therefore unique. However, an atom and a resource identifier can coincide. The string associated with an atom is called the atom name. The name of an atom cannot be changed after creation, and no two atoms can have the same name. As a result, the name of an atom is commonly used to indicate the atom: “the atom
ABCD” means, more precisely, “the atom whose associated string is ABCD.” or “the atom whose name is ABCD.” A client can request the creation of a new atom and can request for the atom (the identifier) of a given string. Some atoms are predefined (created by the server with given identifier and string).Atoms are used for a number of purposes, mostly related to communication between different clients connected to the same server. In particular, they are used in association with the properties of windows, which are described below.
The list of all atoms residing in a server can be printed out using the program
xlsatoms. In particular, this program prints each atom (the identifier, that is, a number) with its name (its associated string).Properties
Every window has a predefined set of attributes and a set of properties, all stored in the server and accessible to the clients via appropriate requests. Attributes are data about the window, such as its size, position, background color, etc. Properties are arbitrary pieces of data attached to a window. Unlike attributes, properties have no meaning at the level of the X Window core protocol. A client can store arbitrary data in a property of a window.A property is characterized by a name, a type, and a value. Properties are similar to variables
Variable (programming)
In computer programming, a variable is a symbolic name given to some known or unknown quantity or information, for the purpose of allowing the name to be used independently of the information it represents...
in imperative programming languages, in that a client can create a new property with a given name and type and store a value in it. Properties are associated to windows: two properties with the same name can exist on two different windows while having different types and values.
The name, type, and value of a property are strings; more precisely, they are atoms, that is, strings stored in the server and accessible to the clients via identifiers. A client application can access a given property by using the identifier of the atom containing the name of the property.
Properties are mostly used for inter-client communication. For example, the property named
WM_NAME (the property named by the atom whose associated string is "WM_NAME") is used for storing the name of windows. Window managerWindow manager
A window manager is system software that controls the placement and appearance of windows within a windowing system in a graphical user interface. Most window managers are designed to help provide a desktop environment...
s typically read this property to display the name of windows in their title bar.
Some types of inter-client communication use properties of the root window. For example, according to the freedesktop window manager specification, window managers should store the identifier of the currently active window
Active window
An active window is the currently focused window in the current window manager or explorer. Different window managers indicate the currently-active window in different ways and allow the user to switch between windows in different ways. For example, in Microsoft Windows, if both Notepad and...
in the property named
_NET_ACTIVE_WINDOW of the root window. The X resourcesX resources
In the X Window System, the X resources are parameters of computer programs such as the name of the font used in the buttons, the background color of menus, etc. They are used in conjunction with or as an alternative to command line parameters and configuration files.- Format :At the X protocol...
, which contain parameter
Parameter (computer science)
In computer programming, a parameter is a special kind of variable, used in a subroutine to refer to one of the pieces of data provided as input to the subroutine. These pieces of data are called arguments...
s of programs, are also stored in properties of the root window; this way, all clients can access them, even if running on different computers.
The
xprop program prints the properties of a given window; xprop -root prints the name, type, and value of each property of the root window.Mappings

Modifier key
In computing, a modifier key is a special key on a computer keyboard that modifies the normal action of another key when the two are pressed in combination....
was also pressed.
When a key is pressed or released, the server sends events of type
KeyPress or KeyRelease to the appropriate clients. These events contain:- the keycode of the pressed key
- the current state of the modifiers (Shift, Control, etc.) and mouse buttons
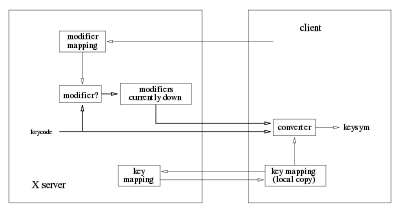
While the translation from keycodes to keysyms is done by the client, the table that represents this association is maintained by the server. Storing this table in a centralized place makes it accessible to all clients. Typical clients only request this mapping and use it for decoding the keycode and modifiers field of a key event into a keysym. However, clients can also change this mapping at will.
A modifier is a key that, when pressed, changes the interpretation of other keys. A common modifier is the Shift key
Shift key
The shift key is a modifier key on a keyboard, used to type capital letters and other alternate "upper" characters. There are typically two shift keys, on the left and right sides of the row below the home row...
: when the key that normally produces a lowercase "a" is pressed together with Shift, it produces an uppercase "A". Other common modifiers are "Control", "Alt", and "Meta".
The X server works with at most eight modifiers. However, each modifier can be associated with more than one key. This is necessary because many keyboards have duplicated keys for some modifiers. For example, many keyboards have two "Shift" keys (one on the left and one on the right). These two keys produce two different keycodes when pressed, but the X server associates both with the "Shift" modifier.
For each of the eight modifiers, the X server maintains a list of the keycodes that it consider to be that modifier. As an example, if the list of the first modifier (the "Shift" modifier) contains the keycode
0x37, then the key that produces the keycode 0x37 is considered a shift key by the X server.The lists of modifier mappings is maintained by the X server but can be changed by every client. For example, a client can request the "F1 key" to be added to the list of "Shift" modifiers. From this point on, this key behaves like another shift modifier. However, the keycode corresponding to F1 is still generated when this key is pressed. As a result, F1 operates as it did before (for example, a help window may be opened when it is pressed), but also operates like the shift key (pressing "a" in a text editor while F1 is down adds "A" to the current text).
The X server maintains and uses a modifier mapping for the mouse buttons. However, the buttons can only be permuted
Permutation
In mathematics, the notion of permutation is used with several slightly different meanings, all related to the act of permuting objects or values. Informally, a permutation of a set of objects is an arrangement of those objects into a particular order...
. This is mostly useful for exchanging the leftmost and rightmost button for left-handed
Left-handed
Left-handedness is the preference for the left hand over the right for everyday activities such as writing. In ancient times it was seen as a sign of the devil, and was abhorred in many cultures...
users.
The
xmodmap program shows and changes the key, modifier, and mouse button mappings.Grabs
A grab is a condition in which all keyboard or mouse events are sent to a single client. A client can request a grab of the keyboard, the mouse, or both: if the request is fulfilled by the server, all keyboard/mouse events are sent to the grabbing client until the grab is released. The other clients will not receive these events.When requesting a grab, a client specifies a grab window: all events are sent to the grabbing client as if they were relative to the grab window. However, the other clients do not receive events even if they have selected them in the grab window. There are two kinds of grabs:
active : the grab takes place immediately
passive : the grab takes place only when a previously specified key or mouse button is pressed and terminates when it is released
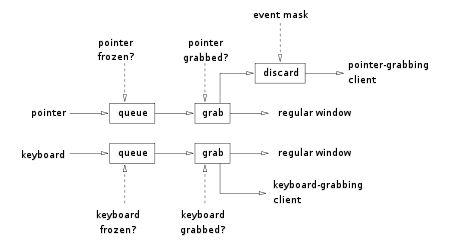
For pointer events, an additional parameter affects the delivery of events: an event mask, which specifies which types of events are to be delivered and which ones are to be discarded.
The requests for grabbing include a field for specifying what happens to events that would be sent to the grabbing client even if it had not established the grab. In particular, the client can request them to be sent as usual or according to the grab. These two conditions are not the same as they may appear. For example, a client that would normally receive the keyboard events on a first window may request the keyboard to be grabbed by a second window. Events that would normally be sent to the first window may or may not be redirected to the grab window depending on the parameter in the grab request.
A client can also request the grab of the entire server. In this case, no request will be processed by the server except the ones coming from the grabbing client.
Other
Other requests and events in the core protocol exist. The first kind of requests is relative to the parent relationship between windows: a client can request to change the parent of a window, or can request information about the parenthood of windows. Other requests are relative to the selectionX Window selection
Selections, cut buffers, and drag-and-drop are the mechanisms used in the X Window System to allow a user to transfer data from a window to another. Selections and cut buffer are typically used when a user selects text or some other data in a window and pastes in another one...
, which is however mostly governed by other protocols. Other requests are about the input focus
Focus (computing)
In computing, the focus indicates the component of the graphical user interface which is currently selected to receive input. Text entered at the keyboard or pasted from a clipboard is sent to the component which currently has the focus. Moving the focus away from a specific user interface element...
and the shape of the cursor
Cursor (computers)
In computing, a cursor is an indicator used to show the position on a computer monitor or other display device that will respond to input from a text input or pointing device. The flashing text cursor may be referred to as a caret in some cases...
. A client can also request the owner of a resource (window, pixmap, etc.) to be killed, which causes the server to terminate the connection with it. Finally, a client can send a no-operation
NOP
In computer science, NOP or NOOP is an assembly language instruction, sequence of programming language statements, or computer protocol command that effectively does nothing at all....
request to the server.
Extensions
In particular, a client can request the list of all available extensions for data relative to a specific extension. The packets of extensions are similar to the packets of the core protocol. The core protocol specifies that request, event, and error packets contain an integer indicating its type (for example, the request for creating a new window is numbered 1). A range of these integers are reserved for extensions.
Authorization
When the client initially establishes a connection with the server, the server can reply by either accepting the connection, refusing it, or requesting authenticationAuthentication
Authentication is the act of confirming the truth of an attribute of a datum or entity...
. An authentication request contains the name of the authentication method to use. The core protocol does not specify the authentication process, which depends on the kind of authentication used, other than it ends with the server either sending an acceptance or a refusal packet.
During the regular interaction between a client and a server, the only requests related to authentication are about the host-based access method. In particular, a client can request this method to be enabled and can request reading and changing the list of hosts (clients
Client (computing)
A client is an application or system that accesses a service made available by a server. The server is often on another computer system, in which case the client accesses the service by way of a network....
) that are authorized to connect. Typical applications do not use these requests; they are used by the
xhost program to give a user or a scriptShell script
A shell script is a script written for the shell, or command line interpreter, of an operating system. It is often considered a simple domain-specific programming language...
access to the host access list. The host-based access method is considered insecure.
Xlib and other client libraries
Most client programs communicate with the server via the XlibXlib
Xlib is an X Window System protocol client library written in the C programming language. It contains functions for interacting with an X server. These functions allow programmers to write programs without knowing the details of the protocol...
client library. In particular, most clients use libraries such as Xaw
Xaw
Xaw is short for the X Window System Athena widget set, which is a set of widgets to implement simple user interfaces based upon the X Toolkit Intrinsics...
, Motif
Motif (widget toolkit)
In computing, Motif refers to both a graphical user interface specification and the widget toolkit for building applications that follow that specification under the X Window System on Unix and other POSIX-compliant systems. It emerged in the 1980s as Unix workstations were on the rise, as a...
, GTK+
GTK+
GTK+ is a cross-platform widget toolkit for creating graphical user interfaces. It is licensed under the terms of the GNU LGPL, allowing both free and proprietary software to use it. It is one of the most popular toolkits for the X Window System, along with Qt.The name GTK+ originates from GTK;...
, or Qt
Qt (toolkit)
Qt is a cross-platform application framework that is widely used for developing application software with a graphical user interface , and also used for developing non-GUI programs such as command-line tools and consoles for servers...
which in turn use Xlib for interacting with the server. The use of Xlib has the following effects:
- Xlib makes the client synchronous with respect to replies and events:
- the Xlib functions that send requests block until the appropriate replies, if any is expected, are received; in other words, an X Window client not using Xlib can send a request to the server and then do other operations while waiting for the reply, but a client using Xlib can only call an Xlib function that sends the request and wait for the reply, thus blocking the client while waiting for the reply (unless the client starts a new thread before calling the function);
- while the server sends events asynchronously, Xlib stores events received by the client in a queue; the client program can only access them by explicitly calling functions of the X11 library; in other words, the client is forced to block or busy-waitBusy waitingIn software engineering, busy-waiting or spinning is a technique in which a process repeatedly checks to see if a condition is true, such as whether keyboard input is available, or if a lock is available. Spinning can also be used to generate an arbitrary time delay, a technique that was necessary...
if expecting an event.
- Xlib does not send requests to the server immediately, but stores them in a queue, called the output buffer; the requests in the output buffer are actually sent when:
- the program explicitly requests so by calling a library function such as
XFlush; - the program calls a function that gives as a result something that involve a reply from the server, such as
XGetWindowAttributes; - the program asks for an event in the event queue (for example, by calling
XNextEvent) and the call blocks (for example,XNextEventblocks if the queue is empty.)
- the program explicitly requests so by calling a library function such as
Higher-level libraries such as Xt
Intrinsics
X Toolkit Intrinsics is a library used in the X Window System. More precisely, it is a library that uses the low-level Xlib library and provides a friendly API to develop X11 software with graphical widgets...
(which is in turn used by Xaw
Xaw
Xaw is short for the X Window System Athena widget set, which is a set of widgets to implement simple user interfaces based upon the X Toolkit Intrinsics...
and Motif
Motif (widget toolkit)
In computing, Motif refers to both a graphical user interface specification and the widget toolkit for building applications that follow that specification under the X Window System on Unix and other POSIX-compliant systems. It emerged in the 1980s as Unix workstations were on the rise, as a...
) allow the client program to specify the callback function
Callback (computer science)
In computer programming, a callback is a reference to executable code, or a piece of executable code, that is passed as an argument to other code. This allows a lower-level software layer to call a subroutine defined in a higher-level layer....
s associated with some events; the library takes care of polling the event queue and calling the appropriate function when required; some events such as those indicating the need of redrawing a window are handled internally by Xt.
Lower-level libraries, such as XCB
XCB
In computing, XCB is a C language binding for the X Window System. It is implemented as free software and aims to replace Xlib. The project was started in 2001 by Bart Massey....
, provide asynchronous access to the protocol, allowing better latency hiding.
What the X Window System core protocol does not specify
The X Window System core protocol does not mandate over inter-client communication and does not specify how windows are used to form the visual elements that are common in graphical user interfaces (buttonButton (computing)
In computing, a button is a user interface element that provides the user a simple way to trigger an event, like searching for a query at a search engine, or to interact with dialog boxes, like confirming an action.-Description:A typical button is a rectangle or rounded rectangle, wider than it is...
s, menu
Menu (computing)
In computing and telecommunications, a menu is a list of commands presented to an operator by a computer or communications system. A menu is used in contrast to a command-line interface, where instructions to the computer are given in the form of commands .Choices given from a menu may be selected...
s, etc.) Graphical user interface elements are defined by client libraries realizing widget toolkit
Widget toolkit
In computing, a widget toolkit, widget library, or GUI toolkit is a set of widgets for use in designing applications with graphical user interfaces...
s. Inter-client communication is covered by other standards such as the ICCCM and freedesktop specifications.
Inter-client communication is relevant to selections, cut buffers, and drag-and-drop
X Window selection
Selections, cut buffers, and drag-and-drop are the mechanisms used in the X Window System to allow a user to transfer data from a window to another. Selections and cut buffer are typically used when a user selects text or some other data in a window and pastes in another one...
, which are the methods used by a user to transfer data from a window to another. Since the windows may be controlled by different programs, a protocol for exchanging this data is necessary. Inter-client communication is also relevant to X window manager
X window manager
An X window manager is a window manager which runs on top of the X Window System, a windowing system mainly used on Unix-like systems.Unlike the Mac OS and Microsoft Windows platforms which have historically provided a vendor-controlled, fixed set of ways to control how windows and panes display...
s, which are programs that control the appearance of the windows and the general look-and-feel of the graphical user interface. Yet another issue where inter-client communication is to some extent relevant is that of session management
X session manager
In the X Window System, an X session manager is a session management program, a program that can save and restore the current state of a set of running applications.- Overview:...
.
How a user session starts is another issue that is not covered by the core protocol. Usually, this is done automatically by the X display manager. The user can however also start a session manually running the xinit
Xinit
The xinit program allows a user to manually start an X server. The startx script is a front-end for xinit.By default, xinit and startx start an X server on display :0 and then start an xterm on it. When the xterm terminates, xinit and startx kill the X server. In general, xinit and startx can start...
or startx programs.
See also
- X Window System protocols and architectureX Window System protocols and architectureIn computing, the X Window System is a network-transparent windowing system for bitmap displays. This article details the protocols and technical structure of X11.-Client–server model and network transparency:...
- XlibXlibXlib is an X Window System protocol client library written in the C programming language. It contains functions for interacting with an X server. These functions allow programmers to write programs without knowing the details of the protocol...
- IntrinsicsIntrinsicsX Toolkit Intrinsics is a library used in the X Window System. More precisely, it is a library that uses the low-level Xlib library and provides a friendly API to develop X11 software with graphical widgets...
- XneeXneeGNU Xnee is a suite of programs that can record, replay and distribute user actions under the X11 environment. It can be used for testing and demonstrating X11 applications....
can be used to sniff the X Window System protocol
External links
- X.Org Foundation (official home page) - Mirror with the domain name 'freedesktop.org'.
- X Window System Internals
- Kenton Lee's pages on X Window and Motif
- X Window System Protocol, Version 11, Release 6.8

