
Peer-to-peer
Encyclopedia


Peers make a portion of their resources, such as processing power, disk storage or network bandwidth, directly available to other network participants, without the need for central coordination by servers or stable hosts. Peers are both suppliers and consumers of resources, in contrast to the traditional client–server model where only servers supply (send), and clients consume (receive).
The peer-to-peer application structure was popularized by file sharing systems like Napster
Napster
Napster is an online music store and a Best Buy company. It was originally founded as a pioneering peer-to-peer file sharing Internet service that emphasized sharing audio files that were typically digitally encoded music as MP3 format files...
. The concept has inspired new structures and philosophies
Philosophy
Philosophy is the study of general and fundamental problems, such as those connected with existence, knowledge, values, reason, mind, and language. Philosophy is distinguished from other ways of addressing such problems by its critical, generally systematic approach and its reliance on rational...
in many areas of human interaction
Interaction
Interaction is a kind of action that occurs as two or more objects have an effect upon one another. The idea of a two-way effect is essential in the concept of interaction, as opposed to a one-way causal effect...
. Peer-to-peer networking is not restricted to technology, but covers also social
Social
The term social refers to a characteristic of living organisms...
processes with a peer-to-peer dynamic. In such context, social peer-to-peer processes are currently emerging throughout society
Society
A society, or a human society, is a group of people related to each other through persistent relations, or a large social grouping sharing the same geographical or virtual territory, subject to the same political authority and dominant cultural expectations...
.
Architecture of P2P systems
Peer-to-peer systems often implement an abstract overlay networkOverlay network
An overlay network is a computer network which is built on the top of another network. Nodes in the overlay can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network...
, built at Application Layer
Application layer
The Internet protocol suite and the Open Systems Interconnection model of computer networking each specify a group of protocols and methods identified by the name application layer....
, on top of the native or physical network topology. Such overlays are used for indexing and peer discovery and make the P2P system independent from the physical network topology. Content is typically exchanged directly over the underlying Internet Protocol
Internet Protocol
The Internet Protocol is the principal communications protocol used for relaying datagrams across an internetwork using the Internet Protocol Suite...
(IP) network. Anonymous peer-to-peer
Anonymous P2P
An anonymous P2P communication system is a peer-to-peer distributed application in which the nodes or participants are anonymous or pseudonymous...
systems are an exception, and implement extra routing layers to obscure the identity of the source or destination of queries.
In structured peer-to-peer networks, peers (and, sometimes, resources) are organized following specific criteria and algorithms, which lead to overlays with specific topologies and properties. They typically use distributed hash table
Distributed hash table
A distributed hash table is a class of a decentralized distributed system that provides a lookup service similar to a hash table; pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key...
-based (DHT) indexing, such as in the Chord system (MIT
Massachusetts Institute of Technology
The Massachusetts Institute of Technology is a private research university located in Cambridge, Massachusetts. MIT has five schools and one college, containing a total of 32 academic departments, with a strong emphasis on scientific and technological education and research.Founded in 1861 in...
).
Unstructured peer-to-peer networks do not impose any structure on the overlay networks. Peers in these networks connect in an ad-hoc fashion. Ideally, unstructured P2P systems would have absolutely no centralized system, but in practice there are several types of unstructured systems with various degrees of centralization. Three categories can easily be seen.
- In pure peer-to-peer systems the entire network consists solely of equipotent peers. There is only one routing layer, as there are no preferred nodes with any special infrastructure function.
- Hybrid peer-to-peer systems allow such infrastructure nodes to exist, often called supernodes.
- In centralized peer-to-peer systems, a central server is used for indexing functions and to bootstrap the entire system. Although this has similarities with a structured architecture, the connections between peers are not determined by any algorithm.
The first prominent and popular peer-to-peer file sharing
Peer-to-peer file sharing
P2P or Peer-to-peer file sharing allows users to download files such as music, movies, and games using a P2P software client that searches for other connected computers. The "peers" are computer systems connected to each other through internet. Thus, the only requirements for a computer to join...
system, Napster, was an example of the centralized model. Freenet
Freenet
Freenet is a decentralized, censorship-resistant distributed data store originally designed by Ian Clarke. According to Clarke, Freenet aims to provide freedom of speech through a peer-to-peer network with strong protection of anonymity; as part of supporting its users' freedom, Freenet is free and...
and early implementations of the gnutella
Gnutella
Gnutella is a large peer-to-peer network which, at the time of its creation, was the first decentralized peer-to-peer network of its kind, leading to other, later networks adopting the model...
protocol, on the other hand, are examples of the decentralized model. Modern gnutella
Gnutella
Gnutella is a large peer-to-peer network which, at the time of its creation, was the first decentralized peer-to-peer network of its kind, leading to other, later networks adopting the model...
implementations, Gnutella2
Gnutella2
Gnutella2, often referred to as G2, is a peer-to-peer protocol developed mainly by Michael Stokes and released in 2002. While inspired by the gnutella protocol, G2 shares little of its design with the exception of its connection handshake and download mechanics. It adopts an extensible binary...
, as well as the now deprecated Kazaa
Kazaa
Kazaa Media Desktop started as a peer-to-peer file sharing application using the FastTrack protocol licensed by Joltid Ltd. and operated as Kazaa by Sharman Networks...
network are examples of the hybrid model.
A pure P2P network does not have the notion of clients
Client (computing)
A client is an application or system that accesses a service made available by a server. The server is often on another computer system, in which case the client accesses the service by way of a network....
or servers but only equal peer
Peer group (computer networking)
In computer networking, a peer group is a group of functional units in the same layer of a network, by analogy with peer group. See also peer-to-peer networking which is a specific type of networking relying on basically equal end hosts rather than on a hierarchy of devices....
nodes that simultaneously function as both "clients" and "servers" to the other nodes on the network. This model of network arrangement differs from the client–server model where communication is usually to and from a central server. A typical example of a file transfer that does not use the P2P model is the File Transfer Protocol
File Transfer Protocol
File Transfer Protocol is a standard network protocol used to transfer files from one host to another host over a TCP-based network, such as the Internet. FTP is built on a client-server architecture and utilizes separate control and data connections between the client and server...
(FTP) service in which the client and server programs are distinct: the clients initiate the transfer, and the servers satisfy these requests.
The P2P overlay network
Overlay network
An overlay network is a computer network which is built on the top of another network. Nodes in the overlay can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network...
consists of all the participating peers as network nodes. There are links between any two nodes that know each other: i.e. if a participating peer knows the location of another peer in the P2P network, then there is a directed edge from the former node to the latter in the overlay network. Based on how the nodes in the overlay network are linked to each other, we can classify the P2P networks as unstructured or structured.
Structured systems
Structured P2P networks employ a globally consistent protocol to ensure that any node can efficiently route a search to some peer that has the desired file, even if the file is extremely rare. Such a guarantee necessitates a more structured pattern of overlay links. By far the most common type of structured P2P network is the distributed hash tableDistributed hash table
A distributed hash table is a class of a decentralized distributed system that provides a lookup service similar to a hash table; pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key...
(DHT), in which a variant of consistent hashing
Consistent hashing
Consistent hashing is a special kind of hashing. In contrast, in most traditional hash tables, a change in the number of array slots causes nearly all keys to be remapped...
is used to assign ownership of each file to a particular peer, in a way analogous to a traditional hash table
Hash table
In computer science, a hash table or hash map is a data structure that uses a hash function to map identifying values, known as keys , to their associated values . Thus, a hash table implements an associative array...
's assignment of each key to a particular array slot.
Distributed hash tables
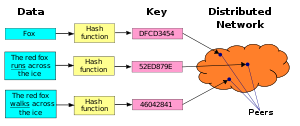
Distributed hash table
A distributed hash table is a class of a decentralized distributed system that provides a lookup service similar to a hash table; pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key...
s (DHTs) are a class of decentralized distributed systems
Distributed computing
Distributed computing is a field of computer science that studies distributed systems. A distributed system consists of multiple autonomous computers that communicate through a computer network. The computers interact with each other in order to achieve a common goal...
that provide a lookup service similar to a hash table
Hash table
In computer science, a hash table or hash map is a data structure that uses a hash function to map identifying values, known as keys , to their associated values . Thus, a hash table implements an associative array...
: (key, value) pairs are stored in the DHT, and any participating node
Node (networking)
In communication networks, a node is a connection point, either a redistribution point or a communication endpoint . The definition of a node depends on the network and protocol layer referred to...
can efficiently retrieve the value associated with a given key. Responsibility for maintaining the mapping from keys to values is distributed among the nodes, in such a way that a change in the set of participants causes a minimal amount of disruption. This allows DHTs to scale
Scalability
In electronics scalability is the ability of a system, network, or process, to handle growing amount of work in a graceful manner or its ability to be enlarged to accommodate that growth...
to extremely large numbers of nodes and to handle continual node arrivals, departures, and failures.
DHTs form an infrastructure that can be used to build peer-to-peer networks. Notable distributed networks that use DHTs include BitTorrent's distributed tracker, the Kad network
Kad Network
The Kad network is a peer-to-peer network which implements the Kademlia P2P overlay protocol. The majority of users on the Kad Network are also connected to servers on the eDonkey network, and Kad Network clients typically query known nodes on the eDonkey network in order to find an initial node...
, the Storm botnet
Storm botnet
The Storm botnet or Storm worm botnet is a remotely controlled network of "zombie" computers that have been linked by the Storm Worm, a Trojan horse spread through e-mail spam...
, YaCy
YaCy
YaCy is a free distributed search engine, built on principles of peer-to-peer networks. Its core is a computer program written in Java distributed on several hundred computers, , so-called YaCy-peers...
, and the Coral Content Distribution Network
Coral Content Distribution Network
The Coral Content Distribution Network, sometimes called Coral Cache or Coral, is a free peer-to-peer content distribution network designed and operated by Michael Freedman...
.
Some prominent research projects include the Chord project, the PAST storage utility
PAST storage utility
PAST is a large-scale, distributed, persistent storage system based on the Pastry peer-to-peer overlay network.-External links:* A. Rowstron and P. Druschel. . 18th ACM SOSP'01, Lake Louise, Alberta, Canada, October 2001.* PAST homepages: , * *...
, the P-Grid
P-Grid
P-Grid is a self-organizing structured peer-to-peer system, which can accommodate arbitrary key distributions , still providing storage load-balancing and efficient search by using randomized routing.- Salient features :* Good storage load-balancing despite arbitrary load-distribution over the...
, a self-organized and emerging overlay network and the CoopNet content distribution system
CoopNet content distribution system
CoopNet , a system for off-loading serving to peers who have recently downloaded content, is described in the paper “The Case for Cooperative Networking”, presented at the First in 2002....
(see below for external links related to these projects).
DHT-based networks have been widely utilized for accomplishing efficient resource discovery for grid computing
Grid computing
Grid computing is a term referring to the combination of computer resources from multiple administrative domains to reach a common goal. The grid can be thought of as a distributed system with non-interactive workloads that involve a large number of files...
systems, as it aids in resource management and scheduling of applications. Resource discovery activity involves searching for the appropriate resource types that match the user’s application requirements. Recent advances in the domain of decentralized resource discovery have been based on extending the existing DHTs with the capability of multi-dimensional data organization and query routing. Majority of the efforts have looked at embedding spatial database indices such as the Space Filling Curves (SFCs) including the Hilbert curves, Z-curves, k-d tree, MX-CIF Quad tree and R*-tree for managing, routing, and indexing of complex Grid resource query objects over DHT networks. Spatial indices are well suited for handling the complexity of Grid resource queries. Although some spatial indices can have issues as regards to routing load-balance in case of a skewed data set, all the spatial indices are more scalable in terms of the number of hops traversed and messages generated while searching and routing Grid resource queries.
Unstructured systems
An unstructured P2P network is formed when the overlay links are established arbitrarily. Such networks can be easily constructed as a new peer that wants to join the network can copy existing links of another node and then form its own links over time. In an unstructured P2P network, if a peer wants to find a desired piece of data in the network, the query has to be floodFlood
A flood is an overflow of an expanse of water that submerges land. The EU Floods directive defines a flood as a temporary covering by water of land not normally covered by water...
ed through the network to find as many peers as possible that share the data. The main disadvantage with such networks is that the queries may not always be resolved. Popular content is likely to be available at several peers and any peer searching for it is likely to find the same thing. But if a peer is looking for rare data shared by only a few other peers, then it is highly unlikely that search will be successful. Since there is no correlation
Correlation
In statistics, dependence refers to any statistical relationship between two random variables or two sets of data. Correlation refers to any of a broad class of statistical relationships involving dependence....
between a peer and the content managed by it, there is no guarantee that flooding will find a peer that has the desired data. Flooding also causes a high amount of signaling traffic in the network and hence such networks typically have very poor search efficiency. Many of the popular P2P networks are unstructured.
In pure P2P networks: Peers act as equals, merging the roles of clients and server. In such networks, there is no central server managing the network, neither is there a central router. Some examples of pure P2P Application Layer
Application layer
The Internet protocol suite and the Open Systems Interconnection model of computer networking each specify a group of protocols and methods identified by the name application layer....
networks designed for peer-to-peer file sharing
Peer-to-peer file sharing
P2P or Peer-to-peer file sharing allows users to download files such as music, movies, and games using a P2P software client that searches for other connected computers. The "peers" are computer systems connected to each other through internet. Thus, the only requirements for a computer to join...
are gnutella (pre v0.4) and Freenet.
There also exist hybrid P2P systems, which distribute their clients into two groups: client nodes and overlay nodes. Typically, each client is able to act according to the momentary need of the network and can become part of the respective overlay network
Overlay network
An overlay network is a computer network which is built on the top of another network. Nodes in the overlay can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network...
used to coordinate the P2P structure. This division between normal and 'better' nodes is done in order to address the scaling problems on early pure P2P networks. As examples for such networks can be named modern implementations of gnutella (after v0.4) and Gnutella2
Gnutella2
Gnutella2, often referred to as G2, is a peer-to-peer protocol developed mainly by Michael Stokes and released in 2002. While inspired by the gnutella protocol, G2 shares little of its design with the exception of its connection handshake and download mechanics. It adopts an extensible binary...
.
Another type of hybrid P2P network are networks using on the one hand central server(s) or bootstrapping mechanisms, on the other hand P2P for their data transfers. These networks are in general called 'centralized networks' because of their lack of ability to work without their central server(s). An example for such a network is the eDonkey network
EDonkey network
The eDonkey network is a decentralized, mostly server-based, peer-to-peer file sharing network best suited to share big files among users, and to provide long term availability of files...
(often also called eD2k).
Indexing and resource discovery
Older peer-to-peer networks duplicate resources across each node in the network configured to carry that type of information. This allows local searching, but requires much traffic.Modern networks use central coordinating servers and directed search requests. Central servers are typically used for listing potential peers (Tor
Tor (anonymity network)
Tor is a system intended to enable online anonymity. Tor client software routes Internet traffic through a worldwide volunteer network of servers in order to conceal a user's location or usage from someone conducting network surveillance or traffic analysis...
), coordinating their activities (Folding@home
Folding@home
Folding@home is a distributed computing project designed to use spare processing power on personal computers to perform simulations of disease-relevant protein folding and other molecular dynamics, and to improve on the methods of doing so...
), and searching (Napster
Napster
Napster is an online music store and a Best Buy company. It was originally founded as a pioneering peer-to-peer file sharing Internet service that emphasized sharing audio files that were typically digitally encoded music as MP3 format files...
, eMule
EMule
eMule is a free peer-to-peer file sharing application for Microsoft Windows. Started in May 2002 as an alternative to eDonkey2000, eMule now connects to both the eDonkey network and the Kad network...
). Decentralized searching was first done by flooding search requests out across peers. More efficient directed search strategies, including supernodes and distributed hash tables, are now used.
Many P2P systems use stronger peers (super-peers, super-nodes) as servers and client-peers are connected in a star-like fashion to a single super-peer.
Peer-to-peer-like systems
In modern definitions of peer-to-peer technology, the term implies the general architectural concepts outlined in this article. However, the basic concept of peer-to-peer computing was envisioned in earlier software systems and networking discussions, reaching back to principles stated in the first Request for CommentsRequest for Comments
In computer network engineering, a Request for Comments is a memorandum published by the Internet Engineering Task Force describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems.Through the Internet Society, engineers and...
, RFC 1.
A distributed messaging system that is often likened as an early peer-to-peer architecture is the USENET
Usenet
Usenet is a worldwide distributed Internet discussion system. It developed from the general purpose UUCP architecture of the same name.Duke University graduate students Tom Truscott and Jim Ellis conceived the idea in 1979 and it was established in 1980...
network news system that is in principle a client–server model from the user or client perspective, when they read or post news articles. However, news server
News server
A news server is a set of computer software used to handle Usenet articles. It may also refer to a computer itself which is primarily or solely used for handling Usenet. A reader server provides an interface to read and post articles, generally with the assistance of a news client. A transit...
s communicate with one another as peers to propagate Usenet news
Usenet
Usenet is a worldwide distributed Internet discussion system. It developed from the general purpose UUCP architecture of the same name.Duke University graduate students Tom Truscott and Jim Ellis conceived the idea in 1979 and it was established in 1980...
articles over the entire group of network servers. The same consideration applies to SMTP
Simple Mail Transfer Protocol
Simple Mail Transfer Protocol is an Internet standard for electronic mail transmission across Internet Protocol networks. SMTP was first defined by RFC 821 , and last updated by RFC 5321 which includes the extended SMTP additions, and is the protocol in widespread use today...
email in the sense that the core email relaying network of Mail transfer agent
Mail transfer agent
Within Internet message handling services , a message transfer agent or mail transfer agent or mail relay is software that transfers electronic mail messages from one computer to another using a client–server application architecture...
s has a peer-to-peer character, while the periphery of e-mail client
E-mail client
An email client, email reader, or more formally mail user agent , is a computer program used to manage a user's email.The term can refer to any system capable of accessing the user's email mailbox, regardless of it being a mail user agent, a relaying server, or a human typing on a terminal...
s and their direct connections is strictly a client–server relationship. Tim Berners-Lee
Tim Berners-Lee
Sir Timothy John "Tim" Berners-Lee, , also known as "TimBL", is a British computer scientist, MIT professor and the inventor of the World Wide Web...
's vision for the World Wide Web
World Wide Web
The World Wide Web is a system of interlinked hypertext documents accessed via the Internet...
, as evidenced by his WorldWideWeb
WorldWideWeb
WorldWideWeb, later renamed to Nexus to avoid confusion between the software and the World Wide Web, was the first web browser and editor. When it was written, WorldWideWeb was the only way to view the Web....
editor/browser, was close to a peer-to-peer design in that it assumed each user of the web would be an active editor and contributor creating and linking content to form an interlinked web of links. This contrasts to the broadcasting
Broadcasting
Broadcasting is the distribution of audio and video content to a dispersed audience via any audio visual medium. Receiving parties may include the general public or a relatively large subset of thereof...
-like structure of the web as it has developed over the years.
Advantages and weaknesses
In P2P networks, clients provide resources, which may include bandwidthBandwidth (computing)
In computer networking and computer science, bandwidth, network bandwidth, data bandwidth, or digital bandwidth is a measure of available or consumed data communication resources expressed in bits/second or multiples of it .Note that in textbooks on wireless communications, modem data transmission,...
, storage space, and computing power. This property is one of the major advantages of using P2P networks because it makes the setup and running costs very small for the original content distributor. As nodes arrive and demand on the system increases, the total capacity of the system also increases, and the likelihood of failure decreases. If one peer on the network fails to function properly, the whole network is not compromised or damaged. In contrast, in a typical client–server architecture, clients share only their demands with the system, but not their resources. In this case, as more clients join the system, fewer resources are available to serve each client, and if the central server fails, the entire network is taken down.
The decentralized nature of P2P networks increases robustness because it removes the single point of failure
Reliability engineering
Reliability engineering is an engineering field, that deals with the study, evaluation, and life-cycle management of reliability: the ability of a system or component to perform its required functions under stated conditions for a specified period of time. It is often measured as a probability of...
that can be inherent in a client-server based system.
Another important property of peer-to-peer systems is the lack of a system administrator. This leads to a network that is easier and faster to setup and keep running because a full staff is not required to ensure efficiency and stability. Decentralized networks introduce new security issues because they are designed so that each user is responsible for controlling their data and resources. Peer-to-peer networks, along with almost all network systems, are vulnerable to unsecure and unsigned codes that may allow remote access to files on a victim's computer or even compromise the entire network. A user may encounter harmful data by downloading a file that was originally uploaded as a virus disguised in an .exe, .mp3, .avi, or any other filetype. This type of security issue is due to the lack of an administrator that maintains the list of files being distributed.
Harmful data can also be distributed on P2P networks by modifying files that are already being distributed on the network. This type of security breach is created by the fact that users are connecting to untrusted sources, as opposed to a maintained server. In the past this has happened to the FastTrack network when the RIAA managed to introduce faked chunks into downloads and downloaded files (mostly MP3
MP3
MPEG-1 or MPEG-2 Audio Layer III, more commonly referred to as MP3, is a patented digital audio encoding format using a form of lossy data compression...
files). Files infected with the RIAA virus were unusable afterwards or even contained malicious code. The RIAA is also known to have uploaded fake music and movies to P2P networks in order to deter illegal file sharing. Consequently, the P2P networks of today have seen an enormous increase of their security and file verification mechanisms. Modern hashing
Hash chain
A hash chain is the successive application of a cryptographic hash function to a piece of data. In computer security, a hash chain is a method to produce many one-time keys from a single key or password...
, chunk verification
File verification
File verification is the process of using an algorithm for verifying the integrity or authenticity of a computer file. This can be done by comparing two files bit-by-bit, but requires two copies of the same file, and may miss systematic corruptions which might occur to both files...
and different encryption methods have made most networks resistant to almost any type of attack, even when major parts of the respective network have been replaced by faked or nonfunctional hosts.
There are both advantages and disadvantages in P2P networks related to the topic of data backup, recovery, and availability. In a centralized network, the system administrators are the only forces controlling the availability of files being shared. If the administrators decide to no longer distribute a file, they simply have to remove it from their servers, and it will no longer be available to users. Along with leaving the users powerless in deciding what is distributed throughout the community, this makes the entire system vulnerable to threats and requests from the government and other large forces. For example, YouTube has been pressured by the RIAA, MPAA, and entertainment industry to filter out copyrighted content. Although server-client networks are able to monitor and manage content availability, they can have more stability in the availability of the content they choose to host. A client should not have trouble accessing obscure content that is being shared on a stable centralized network. P2P networks, however, are more unreliable in sharing unpopular files because sharing files in a P2P network requires that at least one node in the network has the requested data, and that node must be able to connect to the node requesting the data. This requirement is occasionally hard to meet because users may delete or stop sharing data at any point.
In this sense, the community of users in a P2P network is completely responsible for deciding what content is available. Unpopular files will eventually disappear and become unavailable as more people stop sharing them. Popular files, however, will be highly and easily distributed. Popular files on a P2P network actually have more stability and availability than files on central networks. In a centralized network, only the loss of connection between the clients and server is simple enough to cause a failure, but in P2P networks, the connections between every node must be lost in order to fail to share data. In a centralized system, the administrators are responsible for all data recovery and backups, while in P2P systems, each node requires its own backup system. Because of the lack of central authority in P2P networks, forces such as the recording industry, RIAA, MPAA, and the government are unable to delete or stop the sharing of content on P2P systems.
Social and economic impact
The concept of P2P is increasingly evolving to an expanded usage as the relational dynamic active in distributed networks, i.e., not just computer to computer, but human to human. Yochai BenklerYochai Benkler
Yochai Benkler is an Israeli-American professor of Law and author. Since 2007, he has been the Berkman Professor of Entrepreneurial Legal Studies at Harvard Law School. He is also a faculty co-director of the Berkman Center for Internet & Society at Harvard University.- Biography :In 1984, Benkler...
has coined the term commons-based peer production
Commons-based peer production
Commons-based peer production is a term coined by Harvard Law School professor Yochai Benkler to describe a new model of socio-economic production in which the creative energy of large numbers of people is coordinated into large, meaningful projects mostly without traditional hierarchical...
to denote collaborative projects such as free and open source software
Free and open source software
Free and open-source software or free/libre/open-source software is software that is liberally licensed to grant users the right to use, study, change, and improve its design through the availability of its source code...
and Wikipedia
Wikipedia
Wikipedia is a free, web-based, collaborative, multilingual encyclopedia project supported by the non-profit Wikimedia Foundation. Its 20 million articles have been written collaboratively by volunteers around the world. Almost all of its articles can be edited by anyone with access to the site,...
. Associated with peer production are the concepts of:
- peer governance (referring to the manner in which peer production projects are managed)
- peer property (referring to the new type of licenses which recognize individual authorship but not exclusive property rights, such as the GNU General Public LicenseGNU General Public LicenseThe GNU General Public License is the most widely used free software license, originally written by Richard Stallman for the GNU Project....
and the Creative CommonsCreative CommonsCreative Commons is a non-profit organization headquartered in Mountain View, California, United States devoted to expanding the range of creative works available for others to build upon legally and to share. The organization has released several copyright-licenses known as Creative Commons...
licenses) - peer distribution (or the manner in which products, particularly peer-produced products, are distributed)
Some researchers have explored the benefits of enabling virtual communities to self-organize and introduce incentives for resource sharing and cooperation, arguing that the social aspect missing from today's peer-to-peer systems should be seen both as a goal and a means for self-organized virtual communities to be built and fostered. Ongoing research efforts for designing effective incentive mechanisms in P2P systems, based on principles from game theory are beginning to take on a more psychological and information-processing direction.
Applications
There are numerous applications of peer-to-peer networks. The most commonly known is for content distributionContent delivery
- Many file sharing networks, such as gnutellaGnutellaGnutella is a large peer-to-peer network which, at the time of its creation, was the first decentralized peer-to-peer network of its kind, leading to other, later networks adopting the model...
, G2Gnutella2Gnutella2, often referred to as G2, is a peer-to-peer protocol developed mainly by Michael Stokes and released in 2002. While inspired by the gnutella protocol, G2 shares little of its design with the exception of its connection handshake and download mechanics. It adopts an extensible binary...
and the eDonkey networkEDonkey networkThe eDonkey network is a decentralized, mostly server-based, peer-to-peer file sharing network best suited to share big files among users, and to provide long term availability of files...
popularized peer-to-peer technologies. From 2004 on, such networks form the largest contributor of network traffic on the Internet. - Peer-to-peer content delivery networks (P2P-CDN). See : Giraffic, KontikiKontikiKontiki is a peer-assisted content delivery technology company, founded in November 2000. It was acquired by VeriSign in March 2006. VeriSign, as part of a major divestiture, sold Kontiki to MK Capital in May 2008....
, IgniteIgniteIgnite is a program for gifted and talented young people in South Australia, created in 1998 and formerly known as SHIP . It is administered by the South Australian Department of Education and Children's Services....
, RedSwooshRedSwooshRed Swoosh was a peer-to-peer content delivery company founded by Travis Kalanick and Michael Todd in 2001 and acquired by Akamai Technologies in 2007. The Red Swoosh technology included a centralized directory that indexed online clients and caches...
. - Peer-to-peer content services, e.g. caches for improved performance such as Correli Caches
- Software publication and distribution (Linux, several games); via file sharingFile sharingFile sharing is the practice of distributing or providing access to digitally stored information, such as computer programs, multimedia , documents, or electronic books. It may be implemented through a variety of ways...
networks. - Streaming mediaStreaming mediaStreaming media is multimedia that is constantly received by and presented to an end-user while being delivered by a streaming provider.The term "presented" is used in this article in a general sense that includes audio or video playback. The name refers to the delivery method of the medium rather...
. P2PTVP2PTVThe term P2PTV refers to peer-to-peer software applications designed to redistribute video streams in real time on a P2P network; the distributed video streams are typically TV channels from all over the world but may also come from other sources...
and PDTPPeer Distributed Transfer ProtocolThe Peer Distributed Transfer Protocol is an Internet file transfer protocol for distributing files from a central server across a peer-to-peer network. It is conceptually similar to BitTorrent but allows for streaming media. The protocol has been assigned port 6086 by the Internet Assigned...
. Applications include TVUPlayerTVUnetworksTVU Networks Corporation is a company that manufactures live mobile television broadcasting equipment and offers an Internet television broadcasting platform that uses P2PTV technology. Founded in 2005, the company is based in Mountain View, California.....
, JoostJoostJoost is an Internet TV service, created by Niklas Zennström and Janus Friis . During 2007-8 Joost used peer-to-peer TV technology to distribute content to their Mozilla-based desktop player; in late 2008 this was migrated to use a Flash-based Web player instead.Joost began development in 2006...
, CoolStreamingCoolStreamingCoolStreaming is a P2PTV technology that enables users to share television content with each other over the Internet. The technology behind CoolStreaming is similar to that of BitTorrent. The viewers upload content at the same time the programs are downloaded and viewed...
, Cybersky-TVCybersky-TVCybersky-TV is a free software application for sharing television signals using a P2PTV technology. It allows users with a broadband internet connection to share the TV channels they are able to receive...
, PPLivePPLivePPTV, developed by PPLive, is a leading online TV service offering both live streaming and video-on-demand of TV programs/shows, movies, drama, sports, news and entertainment video contents. The service is accessible either from its website or from client software installation...
, LiveStationLiveStationLivestation is a platform for distributing live television and radio broadcasts over a data network. It has been developed by Skinkers Ltd and is now a new company called Livestation Ltd...
, Giraffic and DidiomDidiomDidiom was a mobile media company that specialized in the development of streaming media applications and wireless content delivery platforms. Built on peer-to-peer placeshifting technology, the company’s flagship product allowed customers to stream their home computer’s audio collection to their...
. - SpotifySpotifySpotify is a Swedish-founded, UK-headquartered DRM-based music streaming service offering streaming of selected music from a range of major and independent record labels, including Sony, EMI, Warner Music Group, and Universal. Launched in October 2008 by Swedish startup Spotify AB, the service had...
uses a peer-to-peer network along with streaming servers to stream music to its desktop music player. - PeercastingPeercastingPeercasting is a method of multicasting streams, usually audio and/or video, to the Internet via peer-to-peer technology. It can be used for commercial, independent, and amateur multicasts. Unlike traditional IP Multicast, peercasting can facilitate on-demand content delivery.-Operation:It usually...
for multicasting streams. See PeerCastPeerCastPeerCast is an open source streaming media multicast tool. PeerCast uses peer-to-peer technology to minimize the necessary upload bandwidth for the original multicaster.The website of PeerCast appears to be abandoned since December 2007...
, IceShare, FreeCastFreeCastFreeCast is a free software application which allows peer-to-peer streaming, sometimes called peercasting. It makes possible an audio or video stream broadcast to a large number of listeners from a simple DSL connection....
, RawflowRawflowRawFlow is a provider of live p2p streaming technology that enables internet broadcasting of audio and video. Rawflow was incorporated in 2002 by Mikkel Dissing, Daniel Franklin and Stephen Dicks. Its main office is in London, UK... - Pennsylvania State University, MIT and Simon Fraser University are carrying on a project called LionShareLionShareLionShare is a software project designed to facilitate file sharing among educational institutions around the world. It is based on the free and open-source LimeWire file sharing program written in Java....
designed for facilitating file sharing among educational institutions globally. - Osiris (Serverless Portal System)Osiris (Serverless Portal System)Osiris Serverless Portal System is a freeware program used to create web portals distributed via peer-to-peer networking and autonomous from centralized servers...
allows its users to create anonymous and autonomous web portals distributed via P2P network.
Exchange of physical goods, services, or space
- Peer-to-peer renting web platforms enable people to find and reserve goods, services, or space on the virtual platform, but carry out the actual P2P transaction in the physical world (for example: emailing a local footwear vendor to reserve for you that comfy pair of slippers which you've always had your eyes on, or contacting a neighbor who has listed their weedwacker for rent).
Networking
- Domain Name SystemDomain name systemThe Domain Name System is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities...
, for InternetInternetThe Internet is a global system of interconnected computer networks that use the standard Internet protocol suite to serve billions of users worldwide...
information retrieval. See Comparison of DNS server softwareComparison of DNS server softwareThis article presents a comparison of the features, platform support, and packaging of independent implementations of Domain Name System name server software.- Servers compared :... - cloud computingCloud computingCloud computing is the delivery of computing as a service rather than a product, whereby shared resources, software, and information are provided to computers and other devices as a utility over a network ....
- DalesaDalesaDalesa is a peer-to-peer web cache designed for Local Area Networks . Dalesa is a free and opensource software developed by Lanka Software Foundation under GPL license.-Introduction:...
a peer-to-peer web cache for LANs (based on IP multicasting).
Science
- In bioinformatics, drug candidate identification. The first such program was begun in 2001 the Centre for Computational Drug Discovery at the University of OxfordUniversity of OxfordThe University of Oxford is a university located in Oxford, United Kingdom. It is the second-oldest surviving university in the world and the oldest in the English-speaking world. Although its exact date of foundation is unclear, there is evidence of teaching as far back as 1096...
in cooperation with the National Foundation for Cancer Research. There are now several similar programs running under the United Devices Cancer Research ProjectGrid.orggrid.org was a website and online community established in 2001 that focuses on cluster computing and grid computing software for users. For the first 6 years of its history it operated several different volunteer computing projects that allowed members to donate their spare computer cycles to...
. - The sciencenetSciencenetSciencenet is a distributed search engine at KIT – Liebel-Lab for scientific knowledge.The Sciencenet software is based on p2p technology developed by Michael Christen in collaboration with Liebel-lab at KIT.- Background :...
P2P search engine. - BOINC
Search
- YaCyYaCyYaCy is a free distributed search engine, built on principles of peer-to-peer networks. Its core is a computer program written in Java distributed on several hundred computers, , so-called YaCy-peers...
, a free distributed search engine, built on principles of peer-to-peer networks.
Communications networks
- SkypeSkypeSkype is a software application that allows users to make voice and video calls and chat over the Internet. Calls to other users within the Skype service are free, while calls to both traditional landline telephones and mobile phones can be made for a fee using a debit-based user account system...
, one of the most widely used internet phone applications is using P2P technology. - VoIP (using application layer protocols such as SIPSession Initiation ProtocolThe Session Initiation Protocol is an IETF-defined signaling protocol widely used for controlling communication sessions such as voice and video calls over Internet Protocol . The protocol can be used for creating, modifying and terminating two-party or multiparty sessions...
) - Instant messagingInstant messagingInstant Messaging is a form of real-time direct text-based chatting communication in push mode between two or more people using personal computers or other devices, along with shared clients. The user's text is conveyed over a network, such as the Internet...
and online chatOnline chatOnline chat may refer to any kind of communication over the Internet, that offers an instantaneous transmission of text-based messages from sender to receiver, hence the delay for visual access to the sent message shall not hamper the flow of communications in any of the directions... - Completely decentralized networks of peers: UsenetUsenetUsenet is a worldwide distributed Internet discussion system. It developed from the general purpose UUCP architecture of the same name.Duke University graduate students Tom Truscott and Jim Ellis conceived the idea in 1979 and it was established in 1980...
(1979) and WWIVnetWWIVnetWWIVnet was a Bulletin board system network for WWIV-based BBSes. It was created by Wayne Bell on December 1, 1987.-Network layout:WWIVnet consisted of several participating BBSes, each referenced by a unique number called a node number. Originally, WWIVnet nodes were numbered by area code...
(1987).
General
- Research like the Chord project, the PAST storage utilityPAST storage utilityPAST is a large-scale, distributed, persistent storage system based on the Pastry peer-to-peer overlay network.-External links:* A. Rowstron and P. Druschel. . 18th ACM SOSP'01, Lake Louise, Alberta, Canada, October 2001.* PAST homepages: , * *...
, the P-GridP-GridP-Grid is a self-organizing structured peer-to-peer system, which can accommodate arbitrary key distributions , still providing storage load-balancing and efficient search by using randomized routing.- Salient features :* Good storage load-balancing despite arbitrary load-distribution over the...
, and the CoopNet content distribution systemCoopNet content distribution systemCoopNet , a system for off-loading serving to peers who have recently downloaded content, is described in the paper “The Case for Cooperative Networking”, presented at the First in 2002....
. - JXTAJXTAJXTA is an open source peer-to-peer protocol specification begun by Sun Microsystems in 2001. The JXTA protocols are defined as a set of XML messages which allow any device connected to a network to exchange messages and collaborate independently of the underlying network topology.As JXTA is based...
, for Peer applications. See Collanos WorkplaceCollanosCollanos Workplace is a proprietary teamwork software that ceased development in 2010.Installed on each team member’s computer, it builds a team environment and transparent knowledge store that allows to define and organize the content of project teams...
(Teamwork softwareCollaborative softwareCollaborative software is computer software designed to help people involved in a common task achieve goals...
), Sixearch
Miscellaneous
- The U.S. Department of Defense has started research on P2P networks as part of its modern network warfare strategy. In May, 2003 Dr. Tether. Director of Defense Advanced Research Project Agency testified that U.S. Military is using P2P networks.
- Kato et al.’s studies indicate over 200 companies with approximately $400 million USD are investing in P2P network. Besides File Sharing, companies are also interested in Distributing Computing, Content Distribution.
- Wireless community networkWireless community networkWireless community networks or wireless community projects are the organizations that attempt to take a grassroots approach to providing a viable alternative to municipal wireless networks for consumers....
, NetsukukuNetsukukuNetsukuku is the name of an experimental peer-to-peer routing system, developed by the in 2006, created to build up a distributed network, anonymous and censorship-free, fully independent but not necessarily separated from the Internet, without the support of any server, ISP and no central... - An earlier generation of peer-to-peer systems were called "metacomputing" or were classed as "middleware". These include: LegionLegion (software)Legion is a computer software system variously classified as a distributed operating system, a peer-to-peer system, metacomputing software, or middleware...
, GlobusGlobus ToolkitThe Globus Toolkit, currently at version 5, is an open source toolkit for building computing grids developed and provided by the Globus Alliance.-Standards implementation:The Globus Toolkit is an implementation of the following standards:... - BitcoinBitcoinBitcoin is a decentralized, peer-to-peer network over which users make transactions that are tracked and verified through this network. The word Bitcoin also refers to the digital currency implemented as the currency medium for user transactions over this network...
is a peer-to-peer based digital currency.
Historical perspective
Tim Berners-LeeTim Berners-Lee
Sir Timothy John "Tim" Berners-Lee, , also known as "TimBL", is a British computer scientist, MIT professor and the inventor of the World Wide Web...
's vision for the World Wide Web
World Wide Web
The World Wide Web is a system of interlinked hypertext documents accessed via the Internet...
was close to a P2P network in that it assumed each user of the web would be an active editor and contributor, creating and linking content to form an interlinked "web" of links. This contrasts to the current broadcasting
Broadcasting
Broadcasting is the distribution of audio and video content to a dispersed audience via any audio visual medium. Receiving parties may include the general public or a relatively large subset of thereof...
-like structure of the web.
Some networks and channels such as Napster
Napster
Napster is an online music store and a Best Buy company. It was originally founded as a pioneering peer-to-peer file sharing Internet service that emphasized sharing audio files that were typically digitally encoded music as MP3 format files...
, OpenNAP
Opennap
OpenNap is a peer-to-peer service server software. It was created as an open source Napster server, extending the Napster protocol to allow sharing of any media type, and adding the ability to link servers together.-History:...
and IRC
Internet Relay Chat
Internet Relay Chat is a protocol for real-time Internet text messaging or synchronous conferencing. It is mainly designed for group communication in discussion forums, called channels, but also allows one-to-one communication via private message as well as chat and data transfer, including file...
serving channel
Serving channel
A serving channel is a slang term for a file sharing channel found on an IRC network. Here, users can share and download files including photos, videos, audio files, books, programs, etc...
s use a client–server structure for some tasks (e.g., searching) and a P2P structure for others. Networks such as gnutella
Gnutella
Gnutella is a large peer-to-peer network which, at the time of its creation, was the first decentralized peer-to-peer network of its kind, leading to other, later networks adopting the model...
or Freenet
Freenet
Freenet is a decentralized, censorship-resistant distributed data store originally designed by Ian Clarke. According to Clarke, Freenet aims to provide freedom of speech through a peer-to-peer network with strong protection of anonymity; as part of supporting its users' freedom, Freenet is free and...
use a P2P structure for nearly all tasks, with the exception of finding peers to connect to when first setting up.
P2P architecture embodies one of the key technical concepts of the Internet, described in the first Internet Request for Comments
Request for Comments
In computer network engineering, a Request for Comments is a memorandum published by the Internet Engineering Task Force describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems.Through the Internet Society, engineers and...
, RFC 1, "Host Software" dated April 7, 1969. More recently, the concept has achieved recognition in the general public in the context of the absence of central indexing servers
Server (computing)
In the context of client-server architecture, a server is a computer program running to serve the requests of other programs, the "clients". Thus, the "server" performs some computational task on behalf of "clients"...
in architectures used for exchanging multimedia files.
Network neutrality controversy
Peer-to-peer applications present one of the core issues in the network neutralityNetwork neutrality
Network neutrality is a principle that advocates no restrictions by Internet service providers or governments on consumers' access to networks that participate in the Internet...
controversy. Internet service providers (ISP
Internet service provider
An Internet service provider is a company that provides access to the Internet. Access ISPs directly connect customers to the Internet using copper wires, wireless or fiber-optic connections. Hosting ISPs lease server space for smaller businesses and host other people servers...
s) have been known to throttle P2P file-sharing traffic due to its high-bandwidth usage. Compared to Web browsing, e-mail or many other uses of the internet, where data is only transferred in short intervals and relative small quantities, P2P file-sharing often consists of relatively heavy bandwidth usage due to ongoing file transfers and swarm/network coordination packets. In October 2007, Comcast
Comcast
Comcast Corporation is the largest cable operator, home Internet service provider, and fourth largest home telephone service provider in the United States, providing cable television, broadband Internet, and telephone service to both residential and commercial customers in 39 states and the...
, one of the largest broadband Internet providers in the USA, started blocking P2P applications such as BitTorrent. Their rationale was that P2P is mostly used to share illegal content, and their infrastructure is not designed for continuous, high-bandwidth traffic. Critics point out that P2P networking has legitimate uses, and that this is another way that large providers are trying to control use and content on the Internet, and direct people towards a client-server
Client-server
The client–server model of computing is a distributed application that partitions tasks or workloads between the providers of a resource or service, called servers, and service requesters, called clients. Often clients and servers communicate over a computer network on separate hardware, but both...
-based application architecture. The client-server model provides financial barriers-to-entry to small publishers and individuals, and can be less efficient for sharing large files. As a reaction to this bandwidth throttling, several P2P applications started implementing protocol obfuscation, such as the BitTorrent protocol encryption
BitTorrent protocol encryption
Protocol encryption , message stream encryption , or protocol header encrypt are related features of some peer-to-peer file-sharing clients, including BitTorrent clients. They attempt to enhance privacy and confidentiality...
. Techniques for achieving "protocol obfuscation" involves removing otherwise easily identifiable properties of protocols, such as deterministic byte sequences and packet sizes, by making the data look as if it were random. The ISP's solution to the high bandwidth is P2P caching
P2P caching
Peer-to-peer caching is a computer network traffic management technology used by Internet Service Providers to accelerate content delivered over peer-to-peer networks while reducing related bandwidth costs....
, where a ISP stores the part of files most accessed by P2P clients in order to save access to the Internet.
See also
- Client–server model
- Decentralized computingDecentralized computingDecentralized computing is the allocation of resources, both hardware and software, to each individual workstation, or office location. In contrast, centralized computing exists when the majority of functions are carried out, or obtained from a remote centralized location. Decentralized computing...
- Friend-to-friendFriend-to-friendA friend-to-friend computer network is a type of peer-to-peer network in which users only make direct connections with people they know. Passwords or digital signatures can be used for authentication....
- PeercastingPeercastingPeercasting is a method of multicasting streams, usually audio and/or video, to the Internet via peer-to-peer technology. It can be used for commercial, independent, and amateur multicasts. Unlike traditional IP Multicast, peercasting can facilitate on-demand content delivery.-Operation:It usually...
- Segmented downloadingSegmented downloadingSegmented downloading can be a more efficient way of downloading files from many peers at once. The one single file is downloaded, in parallel, from several distinct sources or uploaders of the file...
- Semantic P2P networksSemantic p2p networksSemantic P2P networks is a new type of P2P networks. It combines the advantages of unstructured P2P networks and structural P2P networks, and avoids the disadvantages of theirs....
- Wireless ad hoc network
- Dead Drop (USB)
External links
- Glossary of P2P terminology
- Foundation of Peer-to-Peer Computing, Special Issue, Elsevier Journal of Computer Communication, (Ed) Javed I. Khan and Adam Wierzbicki, Volume 31, Issue 2, February 2008
- Ross J. Anderson. The eternity service. In Pragocrypt 1996, 1996.
- Marling Engle & J. I. Khan. Vulnerabilities of P2P systems and a critical look at their solutions, May 2006
- Stephanos Androutsellis-Theotokis and Diomidis Spinellis. A survey of peer-to-peer content distribution technologies. ACM Computing Surveys, 36(4):335–371, December 2004.
- Biddle, Peter, Paul England, Marcus Peinado, and Bryan Willman, The Darknet and the Future of Content Distribution. In 2002 ACM Workshop on Digital Rights Management, November 2002.
- John F. Buford, Heather Yu, Eng Keong Lua P2P Networking and Applications. ISBN 30-12374-214-5, Morgan Kaufmann, December 2008
- Djamal-Eddine Meddour, Mubashar Mushtaq, and Toufik Ahmed, “Open Issues in P2P Multimedia Streaming”, in the proceedings of the 1st Multimedia Communications Workshop MULTICOMM 2006 held in conjunction with IEEE ICC 2006 pp 43–48, June 2006, Istanbul, Turkey.
- Detlef Schoder and Kai Fischbach, Core Concepts in Peer-to-Peer (P2P) Networking. In: Subramanian, R.; Goodman, B. (eds.): P2P Computing: The Evolution of a Disruptive Technology, Idea Group Inc, Hershey. 2005
- Ralf Steinmetz, Klaus Wehrle (Eds). Peer-to-Peer Systems and Applications. ISBN 3-540-29192-X, Lecture Notes in Computer Science, Volume 3485, September 2005.
- Ramesh Subramanian and Brian Goodman (eds), Peer-to-Peer Computing: Evolution of a Disruptive Technology, ISBN 1-59140-429-0, Idea Group Inc., Hershey, PA, USA, 2005.
- Shuman GhosemajumderShuman GhosemajumderShuman Ghosemajumder is a Canadian technologist, entrepreneur, and author. He is the former click fraud czar at Google, the author of works on digital distribution including the Open Music Model, and co-founder of TeachAIDS.-Early life:...
. Advanced Peer-Based Technology Business Models. MIT Sloan School of ManagementMIT Sloan School of ManagementThe MIT Sloan School of Management is the business school of the Massachusetts Institute of Technology, in Cambridge, Massachusetts....
, 2002. - Silverthorne, Sean. Music Downloads: Pirates- or Customers?. Harvard Business School Working KnowledgeHarvard Business SchoolHarvard Business School is the graduate business school of Harvard University in Boston, Massachusetts, United States and is widely recognized as one of the top business schools in the world. The school offers the world's largest full-time MBA program, doctoral programs, and many executive...
, 2004.

